
What is penetration testing?
October 13, 2022
What are ransomware attacks & how to protect yourself from them
November 1, 2022
Enterprise security systems continue to be targeted by the meticulous and sophisticated modern-day cyber-criminal.
These attacks target and exploit areas of vulnerabilities such as cloud systems, third-party assets, Internet of Things (IoT) devices, Operational Technology (OT) environments, subsidiary networks, and remote workspaces.
Systematic exploits such as this are becoming a costly nuisance to businesses globally.
Luckily, attack surface management is an excellent methodology that works best with DevSecOps to mitigate these problems and reduce businesses’ cyber risk.
We aim to help readers understand all facets of attack surface management and how it can help CISOs mitigate all the weak spots that increase the organization’s attack surface area.
What is an attack surface?
An attack surface is the total number of potential entry points, including vulnerabilities and endpoints, that hackers can exploit to gain access to the system.
In other words, it’s the entire surface area of an enterprise exposed to hacks and security breaches.
With technologies such as IoT on the rise, the sheer volume of devices, network nodes, and web apps creates a substantially extensive attack surface area for most modern-age businesses.
This problem is precisely why organizations with a vast attack surface area need enhanced visibility through continuous attack surface monitoring that swiftly identifies and addresses all network vulnerabilities before any real damage can occur.
Components of an attack surface
The attack surface typically consists of four components that attackers can exploit and gain access to the company’s network. They are:
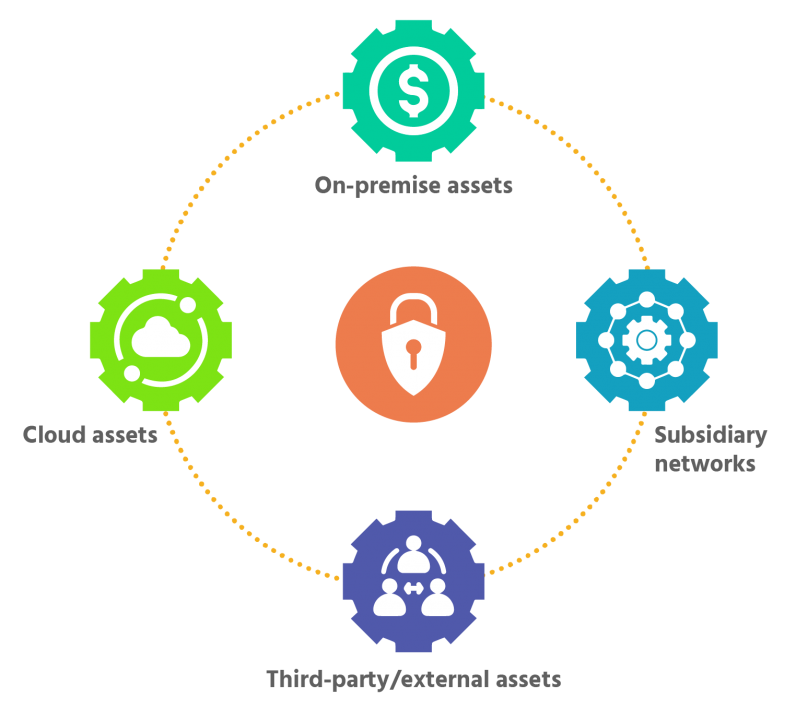
On-premise assets
This component consists of servers, hardware, and other on-site assets.
Cloud assets
Another critical component that bad actors frequently attack is cloud assets.
Cloud assets are all devices that rely upon the cloud to operate and store data. They may include SaaS programs, databases on the cloud, cloud servers, and more.
Third-party/external assets
External partners and vendors with limited access to the business network can also increase the attack surface area. This increase is because external partners sometimes access, store and process sensitive company data on insecure networks that are susceptible to attacks.
Subsidiary networks
Consider an instance where your business is a parent or holding company with multiple smaller subsidiaries.
Here, each subsidiary increases the surface attack area of the parent company as they typically share the same organizational network.
In such instances, attackers can gain access to the much more extensive network through overlooked vulnerabilities in the subsidiary’s network.
What is attack surface management?
Attack surface management (ASM) is the continuous discovery, inventory, classification, prioritization, and security monitoring of external digital assets that contain, transmit, or process sensitive data.
External attack surface management (EASM) is a more specialized capability of attack surface management that identifies and manages all threats from internet-facing assets.
EASM achieves this through penetration testing, vulnerability management, cloud security, and assessing subsidiary vulnerabilities and third-party partner businesses.
Is attack surface management critical?
A 2022 IBM report suggests that businesses that take a DevSecOps approach are more likely to incur reduced financial damage due to cyber attacks.
DevSecOps or Development, Security, and Operations designs organizational culture, platform design, and automation centered around building a robust IT infrastructure as a major priority during all phases of the IT lifecycle.
The DevSecOps approach maintains continuous integration and delivery of products by creating new IP addresses, public code repositories, and servers that remain dormant even after the project’s completion.
These abandoned potential attack vectors and other unknown and shadow assets left behind from DevSecOps can quickly be discovered, mapped out, reviewed, and resolved through automated ASM.
ASM also eliminates other vulnerabilities, such as weak passwords, outdated software, and misconfigurations. Addressing the attack vectors through attack surface management is integral to the continued success of DevSecOps.
Secure your enterprise with continuous penetration testing
The drawback behind attack surface management is that it requires a dedicated technical team. Additionally, the technical teams and other stakeholders will be subject to a significant learning curve.
It is worth noting that vulnerabilities can still fall through and compromise security when enterprises don’t practice best practices, including continuous monitoring and constant action.
A robust solution to this problem involves continuous penetration testing alongside attack surface management. Continuous penetration testing keeps the cyber security infrastructure one step ahead of cybercriminals.
If you need help with continuous penetration testing and attack surface management, consider taking the help of service providers, such as SecureLayer7, that can provide you with next-generation penetration testing and cyber security solutions.
SecureLayer7 helps customers spot high-risk business vulnerabilities such as authentication, authorization, and logic vulnerabilities that may result in data breaches.
Our PaaS services include application testing, mobile app penetration testing, thick client penetration testing, source code analysis, smart contract audit, and cloud penetration testing.
We are renowned amongst enterprises and SME organizations that use our continuous penetration testing and surface attack area management to enable businesses to address all four components of the business’s attack surface.
We help businesses address cloud security concerns by securely maintaining their cloud infrastructure. Any cloud-based vulnerabilities in your AWS, Azure, and Kubernetes systems are swiftly detected and quarantined by the SL7s platform.
SecureLayer7’s server hardening feature limits attacker entry points by preventing them from gaining access through unsecured ports. Server hardening is done by disabling unnecessary services and blocking unutilized protocols and ports.
SecureLayer7 provides full security service to your IoT ecosystem with lifecycle management, superficial testing, manual assessments, and endpoints to networks in the cloud. When deploying our systems, there will be fewer hindrances to IoT product delivery.
Contact us to find out more.


