SecureLayer7 Launches Information Security Testing Services
January 31, 2015
Malware Cleanup: Analysis of an Undetectable web-shell code uploaded via RevSlider Vulnerability
March 9, 2015
Over last 3 years, I’ve participated in the Google Reward Program and found some relatively serious vulnerability. Google OAuth Target URL, Upload X.509 Cert and Domain Description Vulnerable to UI Redress Attack is my one of the oldest finding in Google Reward program. UI Redress Attack is basically a well known attack in the Info Sec community. Also, for those who are new to UI Redress Attack, find information here.
According to Wiki, OAuth is an open standard for the purpose of authorization, it provides client applications a secure access on behalf of a resource owner.
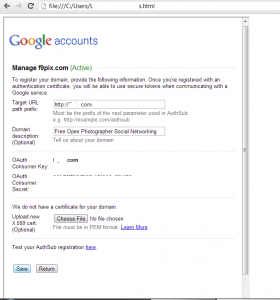
The following URL was vulnerable to UI Redress Attack :
https://accounts.google.com/ManageDomain?authsub_msd=anydomain.com
As a result of using this vulnerability, the attacker is able to update victim’s OAuth Information including Target URL, Upload X.509 Cert and Domain Description.
The following Header information was passing to Google server and you can identify XFO Header information is missing.
Host: accounts.google.com User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.3) Gecko/20100401 Firefox/3.6.3 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 115 Connection: keep-alive
Following is sample POC:
<iframe src = “https://accounts.google.com/ManageDomain?authsub_msd=anydomain.com” width=”600″ height=”600″>
In next blog post I’ll be posting another Relatively Critical Google Vulnerability.