Google OAuth Target URL and Domain Description Vulnerable to UI redress attack
March 7, 2015
Benefits of Outsourcing Vulnerability & Penetration Testing for Companies
March 13, 2015
I started my day with my regular Malware Cleanup activity when I came across an interesting backdoor web shell file on the server. The server is not specific to any particular environment, it was one of the regular update on WordPress package with the plugin RevSlider Plugin ver. 4.1.4 .
So I initiated the process to detect the backdoors and web malwares. During this process, I got a hit on a malicious .htaccess file which was redirecting hxxp://m.mobi-avto.ru as shown below:
In effect, I immediately started the mitigation process to remove and clean the malicious .htaccess file and in the process created backup of all files. Upon further investigation and some digging into other files from server, I ended up inspecting all files on the server using the the following method:find ./ \( -regex '.*\.php I also incorporated different techniques to detect any possible web shell and back-doors (for more techniques visit here) and at last, I got a hit on a web shell code.Interestingly, the beauty of this shell code is that it was completely undetectable to all the anti-viruses. If we dissect the total code we find that it was encoded with base64, with reverse compressed format by using the following snippet:
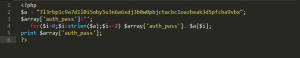
$Laz_ep=@gzinflate(strrev($L_qmfd));
Further on taking a closer look of it’s modus operandi ,we found that it was decoding entire encrypted web shellcode and in the next line it was sending commands to web-shell function for execution, as you can see in the code. This coded webshell was protected by authentication. Hence it was asking for a password for accessing webshell.
The code was completely encrypted. There was a static password stored in the script to access the webshell. So I started analyzing the script and tried to decrypt the web shellcode.
I found following statement suspicious :
$V_ibc("7l3rbp1c9a7d1l0i5oby5u3n6a6sdj3b0w0pbjctacbc1oazbeak3d5pfcba9vbx");
It could possibly be a snippet which is the password to the web shell authentication function.
After couple of minutes into my research I finally found that this is the only function which is responsible for the authentication and I wrote following code to decrypt it :
7l3rbp1c9a7d1l0i5oby5u3n6a6sdj3b0w0pbjctacbc1oazbeak3d5pfcba9vbx
So here actually the webshell (wso version 2.8) is storing Password in MD5 (73b197105b5366d300bcab1aba35fb9b) , if you just search md5 hash on Google you will find the plain text. For further reference, you can find php code here
Also, the details for the webshell, check out detection rate and analysis here :
MD5 : dba5a9a19f240a217b04003ac7084bb3 SHA1 : 28b399288497463f290e73bb8fca27be42de6095 SHA256 : 2ed92600c1e2baa9435a87fdf73807084242d0da2016362bcd0804bfa3f285a0 ssdeep 384:g7ECACT88nrR6og+cFz0ezXx0xSIZ3BLbMHMjRmgUR1RYsyOgDsephg4Hn8Wl:gBPokVfeFB7KAIZxf+fesyOks+hgOp File size 24.7 KB ( 25259 bytes )
The curious question here is that from where did the attacker uploaded the webshell and accessed the entire server?? I started checking all external plugins installations and after digging into the access.log and error.log, got the following findings:
134.249.53.85 - - [04/Mar/2015:00:44:22 +0530] "GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1" 200 3448 "-" "Mozilla/5.0 (Windows NT 6.1; rv:37.0) Gecko/20100101 Firefox/37.0" 134.249.53.85 - - [04/Mar/2015:00:44:23 +0530] "POST /wp-content/plugins/wp-symposium/server/php/index.php HTTP/1.1" 404 1417 "-" "Mozilla/5.0 (Windows NT 6.1; rv:37.0) Gecko/20100101 Firefox/37.0" 134.249.53.85 - - [04/Mar/2015:00:44:25 +0530] "GET /wp-content/plugins/wp-symposium/server/php/kcEgkjtkpykvzG.php HTTP/1.1" 404 1417 "-" "Mozilla/5.0 (Windows NT 6.1; rv:37.0) Gecko/20100101 Firefox/37.0"
The spotlight was on RevSlider Plugin ver. 4.1.4 which, as we can see, was a vulnerable plugin. Here, the attacker can read the files on the server. The Attacker managed to access the web config file of the wordpress and gained further access. So basically, this is how I saved the day and cleaned up malware, web mailers, backdoor and other malicious filefrom the website.
Follow our blog via Twitter or email
-o -regex ‘.*\.incI also incorporated different techniques to detect any possible web shell and back-doors (for more techniques visit here) and at last, I got a hit on a web shell code.
Interestingly, the beauty of this shell code is that it was completely undetectable to all the anti-viruses. If we dissect the total code we find that it was encoded with base64, with reverse compressed format by using the following snippet:
Further on taking a closer look of it’s modus operandi ,we found that it was decoding entire encrypted web shellcode and in the next line it was sending commands to web-shell function for execution, as you can see in the code. This coded webshell was protected by authentication. Hence it was asking for a password for accessing webshell.
The code was completely encrypted. There was a static password stored in the script to access the webshell. So I started analyzing the script and tried to decrypt the web shellcode.
I found following statement suspicious :
It could possibly be a snippet which is the password to the web shell authentication function.
After couple of minutes into my research I finally found that this is the only function which is responsible for the authentication and I wrote following code to decrypt it :
So here actually the webshell (wso version 2.8) is storing Password in MD5 (73b197105b5366d300bcab1aba35fb9b) , if you just search md5 hash on Google you will find the plain text. For further reference, you can find php code here
Also, the details for the webshell, check out detection rate and analysis here :
The curious question here is that from where did the attacker uploaded the webshell and accessed the entire server?? I started checking all external plugins installations and after digging into the access.log and error.log, got the following findings:
The spotlight was on RevSlider Plugin ver. 4.1.4 which, as we can see, was a vulnerable plugin. Here, the attacker can read the files on the server. The Attacker managed to access the web config file of the wordpress and gained further access. So basically, this is how I saved the day and cleaned up malware, web mailers, backdoor and other malicious filefrom the website.
Follow our blog via Twitter or email
\) -print0 | xargs -0 egrep -il “$shellPaterns” | sort > shellPaterns.txt
I also incorporated different techniques to detect any possible web shell and back-doors (for more techniques visit here) and at last, I got a hit on a web shell code.
Interestingly, the beauty of this shell code is that it was completely undetectable to all the anti-viruses. If we dissect the total code we find that it was encoded with base64, with reverse compressed format by using the following snippet:
Further on taking a closer look of it’s modus operandi ,we found that it was decoding entire encrypted web shellcode and in the next line it was sending commands to web-shell function for execution, as you can see in the code. This coded webshell was protected by authentication. Hence it was asking for a password for accessing webshell.
The code was completely encrypted. There was a static password stored in the script to access the webshell. So I started analyzing the script and tried to decrypt the web shellcode.
I found following statement suspicious :
It could possibly be a snippet which is the password to the web shell authentication function.
After couple of minutes into my research I finally found that this is the only function which is responsible for the authentication and I wrote following code to decrypt it :
So here actually the webshell (wso version 2.8) is storing Password in MD5 (73b197105b5366d300bcab1aba35fb9b) , if you just search md5 hash on Google you will find the plain text. For further reference, you can find php code here
Also, the details for the webshell, check out detection rate and analysis here :
The curious question here is that from where did the attacker uploaded the webshell and accessed the entire server?? I started checking all external plugins installations and after digging into the access.log and error.log, got the following findings:
The spotlight was on RevSlider Plugin ver. 4.1.4 which, as we can see, was a vulnerable plugin. Here, the attacker can read the files on the server. The Attacker managed to access the web config file of the wordpress and gained further access. So basically, this is how I saved the day and cleaned up malware, web mailers, backdoor and other malicious filefrom the website.
![RewriteRule ^(.*)$ hxxp://m.mobi-avto.ru [L,R=302]](https://blog.securelayer7.net/wp-content/uploads/2015/03/1-300x88.png)