Benefits of Outsourcing Vulnerability & Penetration Testing for Companies
March 13, 2015CVE-2015-2652 – Unauthenticated File Upload in Oracle E-business Suite.
July 15, 2015Today was another day at work for SecureLayer7 to recover our client’s defaced website. And bang!! I think I hit upon a nasty vulnerability of a famous plugin. Although we successfully patched the vulnerability and we fixed the undoing of the blacklisting. On further research I stumbled upon its usage over the internet. As it turns out that it affects a large number of web users online, we put them to a greater risk if we do not mitigate it with a proper patch or an update.
Following URL is vulnerable to update CSS.
wp-admin/admin-ajax.php?action=revslider_ajax_action&client_action=get_captions_css
You can test your website by executing this python code.
Bug is triggered by sending POST request to admin-ajax.php?action=revslider_ajax_action&client_action=get_captions_css with following parameters
array(“action” => “revslider_ajax_action”,”client_action” => “update_captions_css”, “data” => “HTML-Update-Data”);
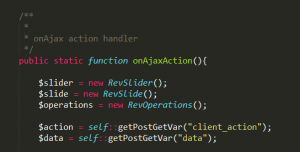
After I started digging for the root cause as to what is exactly triggering the bug, I figured out that there is a class file called as revslider_admin.php in the Revslider Plugin folder, where you can find onAjaxAction() function because of which the bug is actually being triggering.
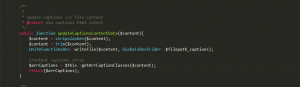
There is a switch function call where it is calling another function called as updateCaptionsContentData() as shown in the bellow image
The updateCaptionsContentData() function is located into the following location inc_php/revslider_operations.class.php. Here the actual trigger for the bug lies, as you can see writeFile function which is writing content in the file.
For fixing this bug, please update your revslider with latest version. I also found some interesting things in revslider_admin.php , which I’ll update in next blog post.
If you required any help to fix this bug you can find our services here . We provide various security Vulnerability & Penetration Testing Services
Follow to our blog via Twitter or email