My Six Months Journey in SecureLayer7
December 12, 2018Gratis Winter Pen Test 2019 Program
January 8, 2019Reading time: 8/10 minutes
Folks!!
In this blog, I will talk about Command and Control Servers (C&Cs) and diverse procedures utilized by “assailants” “attacker” to fabricate a powerful and dependable C&C foundation. The most well-known engineering utilized by aggressors for correspondence is the brought together design which depends on standard HTTP or IRC conventions. They have likewise developed with a decentralized engineering in view of P2P conventions.
Client–Server Model
In this model, there is a centralized server (C&Cs) and every one of the bots are associated with it. The programmer sends the summons to the C&Cs which thus advances the order to all bots and once the bot executes the charge it sends the outcome back to C&Cs, and later C&Cs transfers the outcome back to the programmer.
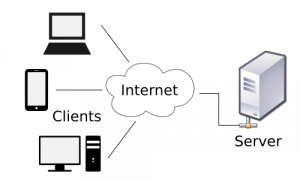
Figure 1: Image Reference from Wikipedia
Peer to Peer (P2P)
In this model, no “centralized” incorporated server is utilized and each associate (bot) goes about as a C&Cs and customer which gets a summons. This keeps away from a solitary purpose of disappointment which is an issue in C&Cs. In the event that the C&C server is brought down in the customer server model, at that point, the entire botnet will be disconnected. Which isn’t the situation in P2P engineering in light of the fact that, in the event that we bring down C&Cs then one of the bots in the system would go about as another C&Cs. Consequently, the system would be inline in any conditions.

Figure 2: Image Reference from Wikipedia
Attacker utilizes Internet Relay Chat convention, which is a content-based correspondence for continuous web informing. IRC is utilized on the grounds that it encourages low data transfer capacity correspondence and is basic in development. It is anything but difficult to recognize movement and close down the bot since associations barely utilize IRCs for interchanges. Hence, assailants are starting to utilize interpersonal organizations, for example, Twitter, Facebook, Telegram as the charge and control server for their bots. Assailants set up a phoney client profile and post encoded orders to the profile. The bot would then visit the profile to recover the order. Encoding the summon and posting it on Twitter or Facebook would be unpredictable and suspicious conduct. In this manner assailant additionally utilizes steganography to insert the charge into pictures. Informal communities are the simplest, least expensive and most solid foundation choice for charge and control servers.
Assailants additionally utilize Domain generation algorithms to create an expansive number of domain names that can be utilized with the command and control servers. Each bot in the botnet creates a deterministic space name list as the order and controller server. The bot at that point pings each area in the rundown to check if the area is up, regardless of whether space is closed down the bot at that point pings different areas to check in the event that it is live along these lines making it persevering. It is hard to imitate charges from the summon and control server in light of the utilization of open key cryptography usage in the bots. The bots will just acknowledge commands marked from the secret key of the malware controller.
The strategies utilized by assailants have advanced throughout the years and joining at least two techniques makes it more bothersome for associations or system overseers to distinguish and alleviate charge and control servers. Today all bots utilize encoded conventions, for example, TLS, HTTPS to make them unsusceptible. That is sufficient for the fundamental comprehension of charge and control servers and diverse systems utilized by aggressors to sidestep the noxious activity.
I hope you’ll enjoy the blog. 😉 Happy Hacking!


