Gratis Winter Pen Test 2019 Program
January 8, 2019
Setting up an Android Pentesting Environment
March 26, 2019
APIs (Application Programming Interfaces) are a crucial component of modern software systems, enabling different applications to interact with each other and share data seamlessly.
However, just like any other software component, APIs are also vulnerable to security threats that can lead to severe consequences, including data breaches, unauthorized access, and compromised systems.
In this blog, we will discuss
- The fundamentals of API penetration testing and how it helps in identifying and mitigating security risks,
- The OWASP 2017 Top 10 API Security Risks and how to use them to perform effective penetration testing, and
- The structure of API and the basics of API penetration testing along with API authentication and session management.
With this knowledge, you can better understand how to ensure your API is secure against potential attacks and safeguard your software systems and user data.
Let us get started!
Brief about API Penetration Testing:
API Penetration Testing is one of the favourite attack surfaces, where the attacker can use to gain into further access to the application or server. During the blog reading, I’ve described the OWASP 2017 Test Cases which is applicable for a general application pen test. I’m going to cover basics of the API penetration testing.
This blog all about API pen testing. Basically the blog is devided three diffeent senction as mentioned below.
- What is API pen testing?
- Structure of API request and response?
- Methodology, Tools and Test Case to perform Pen testing?
- Brief about API Penetration Testing
What is API Penetration Testing?
API Penetration Testing is the process of identifying vulnerabilities in an API (Application Programming Interface) to ensure that it is secure against potential attacks.
This type of testing involves simulating real-world attacks on the API by attempting to exploit known vulnerabilities or identifying new ones.
The goal of API Penetration Testing is to identify security weaknesses and provide recommendations to fix them.
Penetration testing involves a combination of manual and automated testing techniques to discover vulnerabilities that might be missed during standard testing procedures.
By performing API Penetration Testing, organizations can better understand the security posture of their APIs, safeguard against potential attacks, and ensure the protection of sensitive data.
To learn more about API Penetration Testing, you can read our blog here.
What is API Authentication and Session Management?
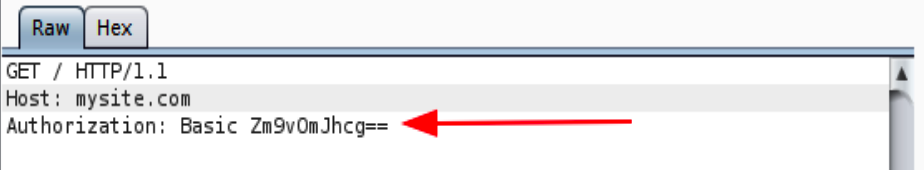
API Authentication and Session Management are critical components of securing APIs. Authentication is the process of verifying the identity of a user or application that is accessing the API.
The most common way to authenticate an API is by using tokens or API keys, which are issued to authorized users or applications. Session management, on the other hand, is the process of maintaining user sessions across multiple API requests.
API Authentication and Session Management are critical components of securing APIs. Authentication is the process of verifying the identity of a user or application that is accessing the API.
The most common way to authenticate an API is by using tokens or API keys, which are issued to authorized users or applications. Session management, on the other hand, is the process of maintaining user sessions across multiple API requests.
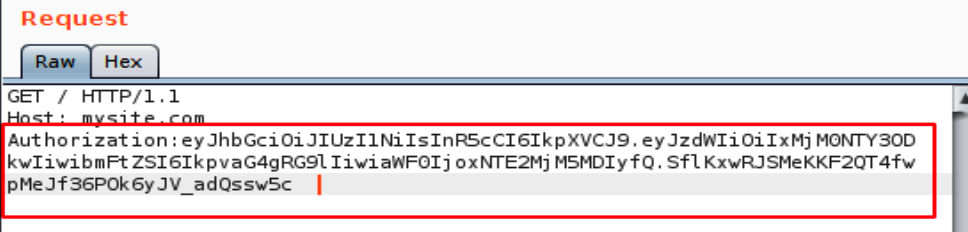
Proper authentication and session management can prevent unauthorized access to sensitive data, protect against attacks, and ensure the integrity of the API.
It’s essential to test API authentication and session management thoroughly during the penetration testing process to ensure that they are secure against potential threats.
Design or Structure of APIs
The design or structure of APIs is critical for their security and usability. APIs should be designed with a clear and intuitive structure that allows users to access data and functionality quickly and easily.
A well-designed API should have a simple and consistent interface, with well-defined endpoints that provide clear documentation on the API’s capabilities and limitations.
Additionally, APIs should use standard protocols and data formats, such as JSON or XML, to ensure interoperability and ease of use. By following these design principles, API developers can create APIs that are intuitive, efficient, and secure.
Another crucial aspect of API design is the implementation of security controls. APIs should be designed with security in mind, with authentication and authorization controls implemented at the API level to ensure that only authorized users or applications can access data or functionality.
Additionally, APIs should be protected from common attacks such as SQL injection and cross-site scripting (XSS) by using input validation and sanitization techniques. Proper error handling and logging mechanisms should also be implemented to ensure that any potential security incidents can be quickly detected and addressed.
Modern applications use API for calling the micro-services, performing actions, or monitoring user behavior. The design or the structure of the API is often exposed to the customers or the end user.
Due to the nature of the API, the attacker can understand the structure of the API and use this information to attack API further.
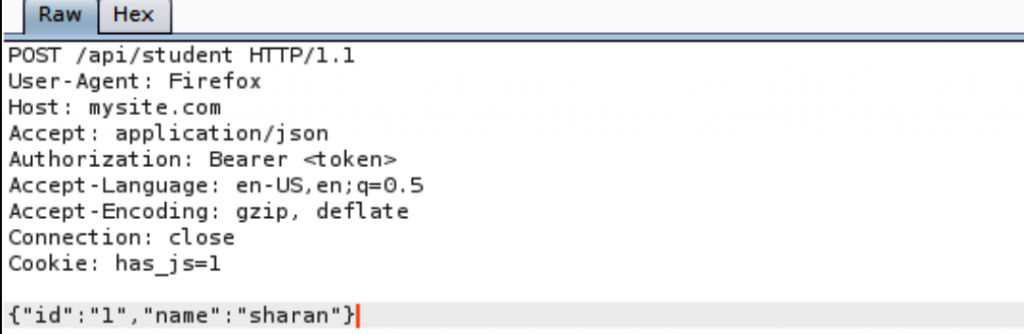
The REST API uses different processing requests such as GET, POST, PUT, DELETE, HEAD, and PATCH actions. The attacker can modify the request headers for understanding the API and use this understanding to craft an entirely working weaponized exploit.
The processing request can be altered, and as a best practice, the processing request must not be tampered with or modified. Below is an example of a processing request. Also keep an eye on the server’s responses for the made requests:
Overall, the design and structure of APIs should prioritize security and usability, with a focus on providing a clear and intuitive interface that is secure against potential threats.
Recommended Tools for API Penetration Testing
Here are some recommended tools for API Penetration Testing:
- Burp Suite: Burp Suite is a popular and comprehensive web application security testing tool that can be used for API Penetration Testing. It offers a wide range of features, including automated vulnerability scanning, request and response interception, manipulation, and advanced scripting capabilities.
- Postman: Postman is a powerful API development and testing tool that can be used for API Penetration Testing. It offers a user-friendly interface for sending and receiving API requests, testing authentication and authorization mechanisms, and debugging API issues.
- OWASP ZAP: OWASP ZAP is a free and open-source web application security scanner that can be used for API Penetration Testing. It offers a range of features, including automated vulnerability scanning, request and response interception and manipulation, and advanced scripting capabilities.
- Insomnia: Insomnia is a powerful REST API client that can be used for API Penetration Testing. It offers a user-friendly interface for sending and receiving API requests, testing authentication and authorization mechanisms, and debugging API issues.
- SoapUI: SoapUI is a widely used testing tool for SOAP and REST APIs that can be used for API Penetration Testing. It offers a range of features, including automated vulnerability scanning, request and response interception and manipulation, and advanced scripting capabilities.
It’s important to note that while these tools can be helpful for API Penetration Testing, they should not be the only method used. Manual testing and in-depth knowledge of API security risks are also crucial for identifying vulnerabilities and ensuring the security of APIs.
How to Find Vulnerabilities in API?
To find vulnerabilities in APIs, a combination of manual and automated testing techniques can be used.
Automated vulnerability scanners, such as Burp Suite, OWASP ZAP, or SoapUI, can be used to quickly identify common security issues such as injection flaws, broken authentication and session management, and insufficient input validation.
However, automated testing alone is not sufficient, and manual testing techniques such as fuzz testing and reverse engineering can be used to identify more complex vulnerabilities that may be missed by automated scanners.
A developer guide can give us more details about the inside of API. If documentation is not provided or API is deployed in a running server, then we need to capture all API requests using the proxy. Identify the POST/GET or other methods thoroughly in each API request. After completion of the understanding phase, write down the possible security test cases.
Additionally, testing different API endpoints with different user roles and permissions can help identify authorization issues. Thorough testing of input parameters, error handling mechanisms, and API responses can also help identify potential vulnerabilities.
Finally, it’s important to stay up-to-date on the latest API security trends and best practices, such as those provided by OWASP, to ensure that all potential vulnerabilities are identified and addressed.
Below are the basic test cases for the low-hanging vulnerabilities.
Hand-picked OWASP 2017 Test cases:
- Observe each parameter in every module of API, and understand how the data is transferred from the source to the destination. Try to play with the parameter by tampering with them.
- Identify if the API has any authorization token if it is having then remove that authorization token and see the application response. In some cases, if authorization is not implemented correctly then API might give you access to forbidden assets of the application.
- Analyze and check each module with a different access level of user ex: admin, moderator, normal user, etc.
- Check whether admin modules can be accessed via the restricted user.
- Identify the parameters which may be vulnerable to IDOR-type vulnerabilities such as id=1234 and also look at the cookies for manipulating the IDs.
- Check injection vulnerabilities by inserting special characters in all parameters in a request and check the response from the server. If you find any stack traces then use the information for further exploitation.
- Insert greater than, less than (<,>) characters in all parameters and see whether the application encodes them as > and <. If an application doesn’t escape any special characters then the application may be vulnerable to client-side attacks such as XSS (cross-site scripting).
- Modify the content-type server header for understanding the XML entity injection attack. Example: change content Application/JSON to application/XML and insert the XML entity payload to find the XML entity injection.
Strengthen the Security of your APIs with SecureLayer7
API security is a critical concern for any organization that deals with sensitive data. With the increasing prevalence of API-driven applications, securing APIs has become more important than ever.
At SecureLayer7, we specialize in API Penetration Testing, API Security Consulting, and API Security Training.
Our team of experienced professionals uses the latest techniques and tools to identify vulnerabilities in APIs and provide comprehensive solutions to strengthen their security. By partnering with SecureLayer7, you can ensure that your APIs are secure against potential threats and that your organization is protected against data breaches and other security incidents.
Don’t leave your APIs vulnerable to attacks. Contact SecureLayer7 today to schedule a consultation and learn how our API Security services can help you strengthen the security of your APIs.
Visit our website to learn more about our services and get in touch with us to discuss your API security needs.

1 Comment
Nice Info