
What Is Website Penetration Testing?
February 16, 2023
What Is Cloud Penetration Testing? A Complete Guide
February 22, 2023
APIs (Application Programming Interfaces) are an integral part of modern software architecture, allowing varied software systems to interact and communicate with one another. But despite their widespread use and importance, APIs are still a super-vulnerable asset, garnering a lot of attention from people with malicious intent.
Organizations need to ensure the security of the APIs they deploy to avoid operational delays and monetary losses.
That’s where API penetration testing comes in.
In this article, we cover API pen testing in detail, addressing why you should conduct an API pentest, the common API vulnerabilities out there, and what goes into the API pen-testing process. Let’s get into it!
What is API Penetration Testing?
An API penetration test is a security evaluation conducted by an external pentester to detect vulnerabilities that may exist in API integrations due to incorrect business logic, core programming issues etc, often by using the same techniques and methodology as a real-world attacker.
This is done to identify vulnerabilities that endanger the confidentiality, integrity, or availability of an organization’s data or infrastructure, and to give actionable solutions to mitigate identified risks.
The tester implements the same strategies, tools, and procedures as an actual attacker. By simulating a real-world attack, the tester gets a better understanding of the vulnerabilities that exist from a hacker’s perspective.
This helps them to secure those critical points of vulnerability effectively.
Why Conduct API Pen Tests?
APIs have enabled businesses to improve efficiency by connecting various apps and building custom workflows. However, this increased usage also implies that hackers have more avenues to attack from. It is therefore vital for businesses to ensure the security of the APIs they deploy to avoid unwanted data breaches and monetary loss.
At the start of the API development process, companies are required to add security. They do this by adding security testing to their CI/CD pipelines.
To find and fix design problems in APIs, they need to do Static Analysis Security Testing (also called “SAST”).
While insightful, such an evaluation is limited and not capable of detecting deep-rooted flaws such as those that exist in business logic. To resolve these issues and truly secure your APIs and your org from every possible attack scenario, it is vital to conduct a comprehensive API penetration test.
What are Common Vulnerabilities in APIs?
Here are some common vulnerabilities in APIs that can lead to a massive data breach.
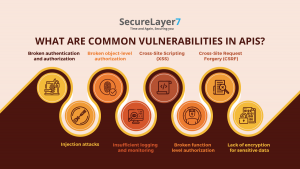
- Broken authentication and authorization – This refers to weak authentication and authorization mechanisms, that lead to unauthorized users accessing sensitive data. This can even go as far as performing actions on behalf of the user.
- Injection attacks – This is when an attacker injects malicious data into the API request, allowing them to change or retrieve sensitive data from the system. Common types of injection attacks include SQL injection and script injection.
- Broken object-level authorization – This occurs when the API does not confirm the access rights of the user for specific objects. An attacker can exploit this vulnerability to access or change data they should not be able to access.
- Insufficient logging and monitoring – APIs that do not log and monitor access and actions can make it difficult to detect and respond to security incidents.
- Cross-Site Scripting (XSS) – This is a type of injection attack where an attacker injects malicious script into the API response, which is then executed in the client’s browser.
- Broken function level authorization – This is when the API does not confirm the access rights of the user for specific functions. An attacker can exploit this vulnerability to perform actions they should not be able to perform.
- Cross-Site Request Forgery (CSRF) – This is an attack where an attacker tricks the user’s browser into sending a malicious request to the API, allowing the attacker to perform actions on behalf of the user.
- Lack of encryption for sensitive data – This is when sensitive data is transmitted over the network without proper encryption, making it vulnerable to eavesdropping and tampering.
It is essential to install appropriate security measures to mitigate these vulnerabilities and ensure the security of API systems.
The API Pen-testing Process
Like most penetration testing processes, API pentesting is conducted through an intensive, step-by-step methodology that ensures every possible vulnerability is rooted out. While every pentester has their own unique process, they are all variations of an overarching 5-step methodology.
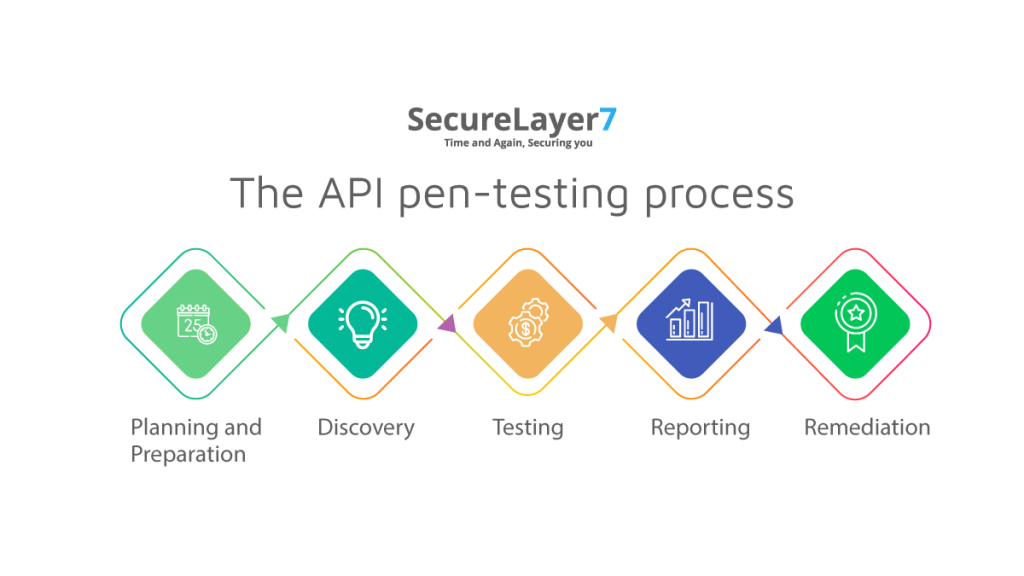
Step 1 – Planning and Preparation
This stage involves understanding the API, its functionalities, and defining the scope of the assessment. This includes gathering information about the API’s architecture, endpoints, authentication and authorization mechanisms, etc.
Step 2 – Discovery
In this stage, the tester identifies all the API endpoints and performs reconnaissance to gather information about the API’s functionality and security posture. This includes testing for common API vulnerabilities such as broken object-level authorization, injection attacks, and sensitive data exposure.
Step 3 – Testing
Here, the tester performs various types of tests to confirm the API’s security. This includes functional testing, penetration testing, and security testing.
During this stage, the tester uses various tools and techniques to test and override the API’s security, such as sending malicious payloads to the API and testing for vulnerabilities such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
Step 4 – Reporting
After completing the exploitation process, the tester will begin creating a report listing all the vulnerabilities and exploits that have been found. At SecureLayer7, we also provide in-depth recommendations to help our clients improve API security and make them impenetrable to real-world attacks.
These reports provide security teams with the data and the context they need to make informed decisions and improve API security.
They are also used as test cases that can be referred to in future tests.
Step 5 – Remediation
In this stage, the vulnerabilities identified by the pentesters are fixed, and the API is tested once again to ensure that the remediation was successful.
It’s important to note that API pen-testing should be performed by experienced security professionals who have a thorough understanding of API security and the various attacks that can be used to compromise it.
Additionally, it is a best practice to perform regular API security assessments to ensure the ongoing security of the API.
Conduct hassle-free API Pen-testing with SecureLayer7
SecureLayer7 is an experienced pentesting partner with over 12 years of experience in helping organizations worldwide secure their digital assets.
Our approach to API penetration testing has been modified and improved with years of learning and feedback to create the scientific, no-nonsense process that we have today.
Armed with an in-house team of expert pentesters and a custom-built platform that provides you with complete visibility into the status of your pentest request, SecureLayer7 is well-prepared to test APIs of any kind, detect the most minute vulnerabilities, and help you strategize redressals and prioritize fixes based on impact to business value.
Contact us today to learn more about how we can secure your entire API infrastructure.
FAQ
What is API penetration testing?
API penetration testing is a security testing process that identifies vulnerabilities and weaknesses in APIs, which are interfaces used by software applications to communicate with each other.
How to test API security testing?
API security testing can be conducted through a combination of manual and automated techniques, including security scans, fuzz testing, penetration testing, and validation of inputs/outputs, authentication, authorization, error handling, access controls, and SSL/TLS configurations.
What are the different types of API penetration testing?
Different types of API penetration testing include Black Box Testing (no prior knowledge of the system), White Box Testing (full knowledge of the system), and Gray Box Testing (partial knowledge of the system).
What tool for API tests?
There are several tools available for API testing, such as Postman, SoapUI, Burp Suite, OWASP ZAP, and Nmap, among others, that provide functionalities to test API security.
Why is API penetration testing important?
API penetration testing is important for identifying vulnerabilities, protecting sensitive data, meeting compliance requirements, enhancing trust and reputation, and reducing risk and financial impact from potential API-related security breaches


