
Recon: an important part of penetration test for finding vulnerabilities
November 15, 2021
Websocket: common vulnerabilities plaguing it and managing them.
December 17, 2021
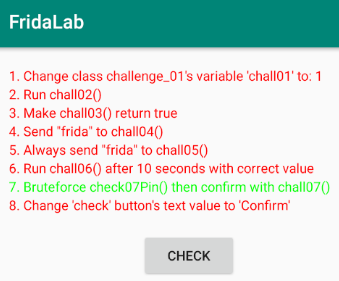
FridaLab Tool, an android application specially created to hone the Frida scripting skills on android.
These challenges include:
- Changing a hard-coded variable
- Modifying the return value from a function
- Running a function unused elsewhere
- Modifying arguments sent to functions
- Manipulating variables live
- Brute-forcing a PIN
- Modifying data on the screen.
In this article, I will explain each challenge step by step and the method to solve them.
Frida Tool is a dynamic code instrumentation toolkit.
It lets you inject snippets of JavaScript or your own library into native apps on Windows, macOS, Linux, iOS, Android, and QNX.
Run the Frida server and install the fridalab apk in the emulator.
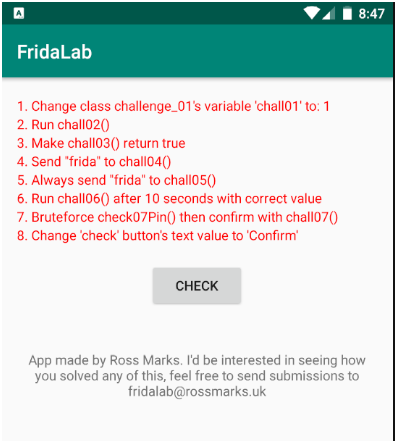
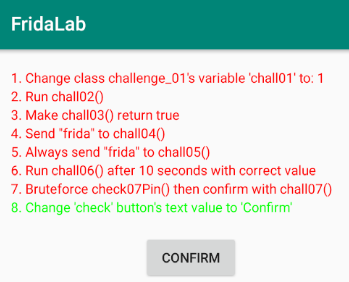
We can see a nice UI. In this application, there are 8 missions with minimal instructions provided. We can click on the check button after each attempt; if it changes to green, then it is solved.
Along with Frida Tool, we will use jadx for static code analysis and objection for runtime apk exploration.
Open the apk with jadx or just drag and drop.
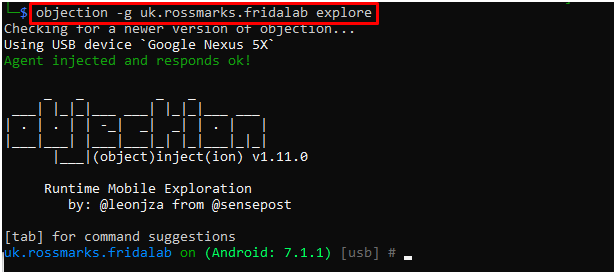
Explore the apk with objection. Also, the objection is powered by the Frida tool and will use the same Frida-server.
Just type the below command.
Let’s begin!
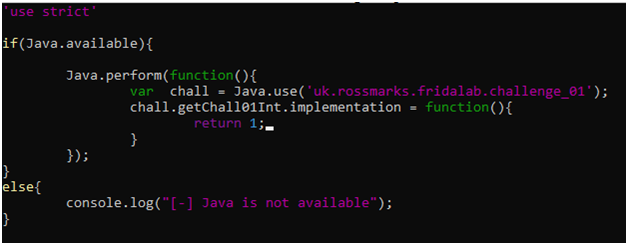
1 – Change class challenge_01’s variable ‘chall01’ to 1
The statement clearly says to change a variable chall01 to 1, which is of class challenge_01.
Let’s search for the challenge_01 class in jadx.
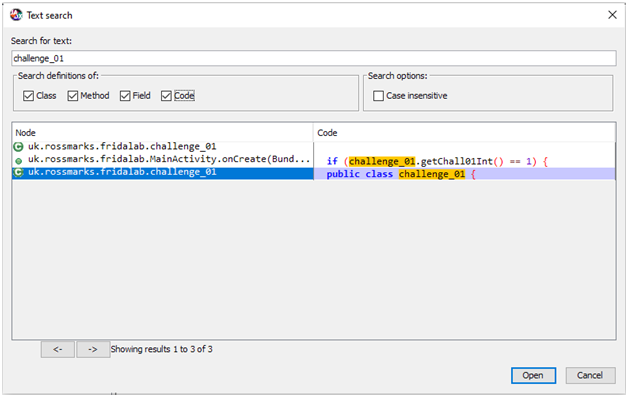
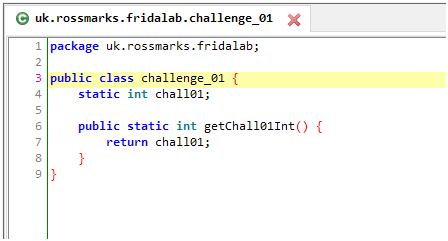
We can solve this by getting a javascript wrapper dynamically with Java.use() and changing the chall01 static variable to 1
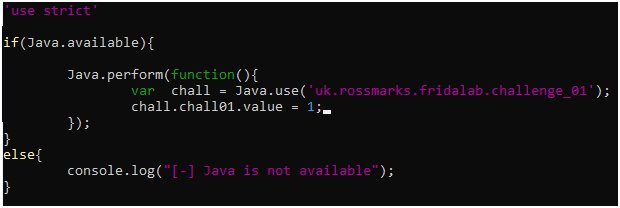
Run the above script with the following command.
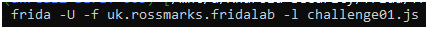
Now, %resume the apk and click on check for verifying the script.
Let’s explore this mission from objection to see the runtime actions.
Now, let’s hook and watch the class
Click on the check button from the apk.
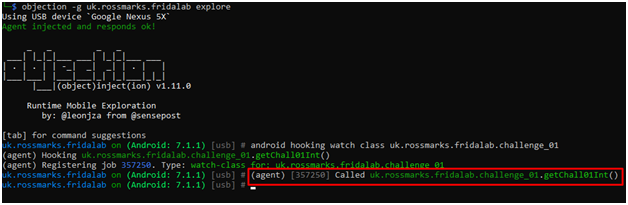
As we clicked the check button on the apk, uk.rossmarks.fridalab.challenge_01.getChall01Int() is invoked.
Another way of solving this challenge is to hook the function getChall01Int() and return 1 whenever it is called. It is because apk is verifying the challenge by calling the getChall01Int() and checking its return value.
2 – Run chall02()
In this challenge, we have to run a function chall02()
Let’s search for it in jadx.
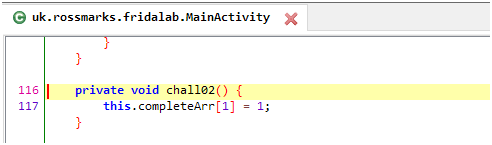
This method is a part of the MainActivity class and doesn’t return any value.
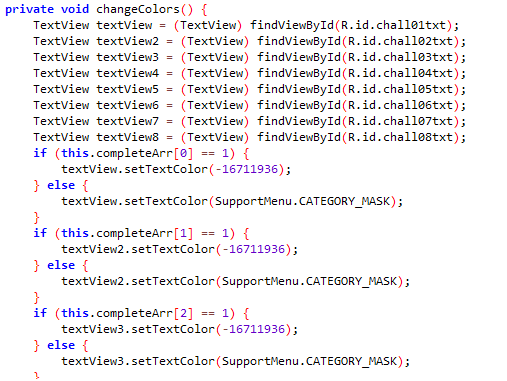
Also, I scrolled the MainActivity class and found the changeColors() method, which checks the indices of completeArr. If it is 1, then change the colour to green.
Let’s watch this MainActivity class with objection.
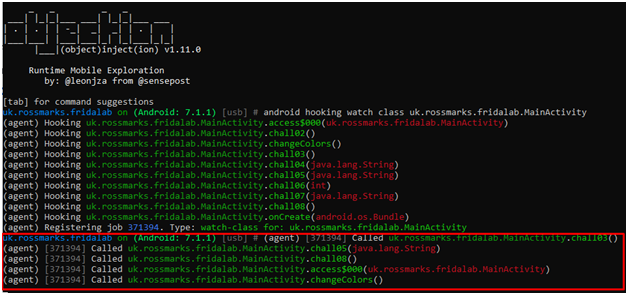
As we click the check button on apk, MainActivity class is invoked and but, chall02() method is not invoked.
Our job here is to run a function, which is unused in the apk.
Here, I used the java.choose() method to find the live instances of the MainActivity class and then on match, just call the chall02() method.
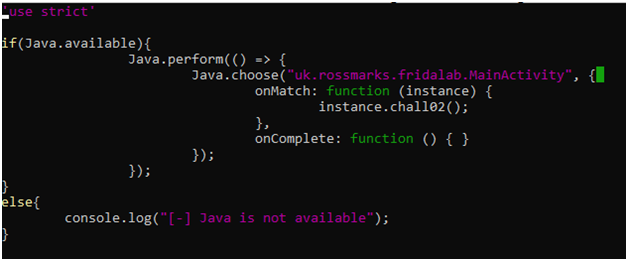
I ran the above script with Frida as we did on challenge01, but it failed to find the instance of MainActivity class.
Then, I came up with an idea. Why not first run the apk on the emulator and then invoke our script. So, I simply opened the apk on the emulator.
We need to find the process id of the apk to attach our script.
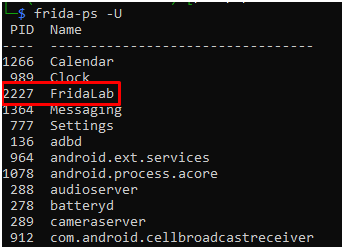
Got 2227 PID for FridaLab apk.
We will attach our script 2227 PID with frida.
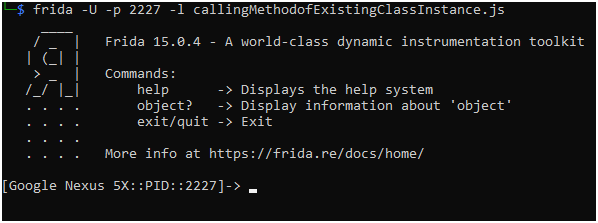
Now, click on the check button to verify it.
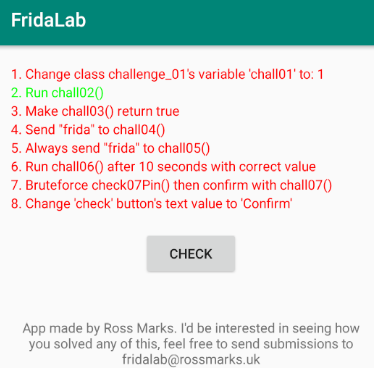
3 – Make chall03() return true
It is clear from the statement that we have to return true when chall03() is called.
Let’s search for it in jadx.
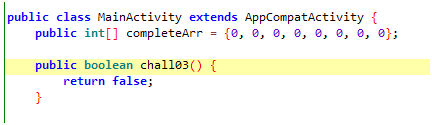
This method is under MainActivity class and is just returning false.
Now, let’s check with the objection, Is this method called while runtime?
We will hook and watch the MainActivity class.
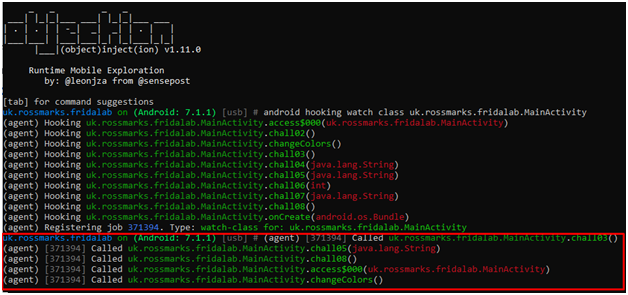
As we click the check button on apk, MainActivity class is invoked, and chall03() is called.
This challenge is similar to what we did on challenge01; the difference is that here we have to return a boolean value.
We can set the boolean return type of any function directly with objection.
Here, our command will be
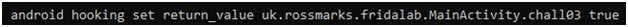
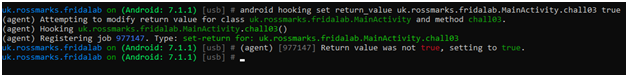
Now, click the check button on apk.
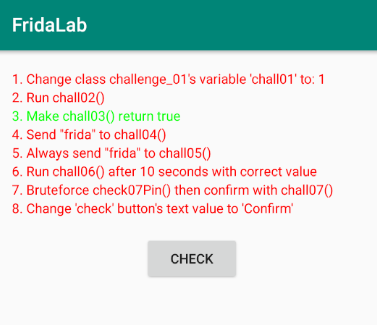
4 – Send “frida” to chall04()
This challenge is dealing with some kind of string. Let’s go to jadx for more clarity.
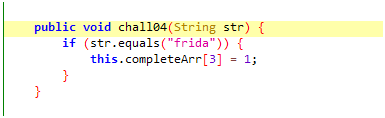
We have to pass the “frida” string to the chall04() function. But is this function being called on runtime or not?
Watching chall04() class with objection.
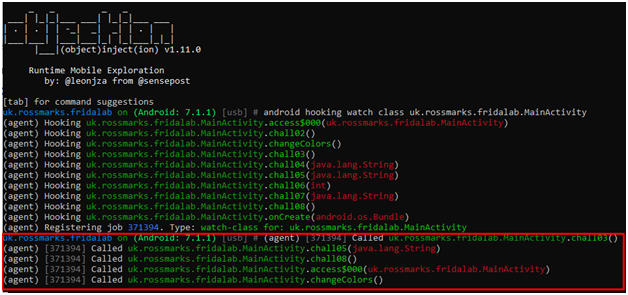
As we click the check button on apk, MainActivity class is invoked and but, chall04() method is not invoked.
Our job here is to modify arguments sent to function and run a function that is unused in the apk.
Similar to challenge02.
Again, I used java.choose() method to find the live instances of the MainActivity class and then on match, just call the chall04() method and pass “frida” as an argument.
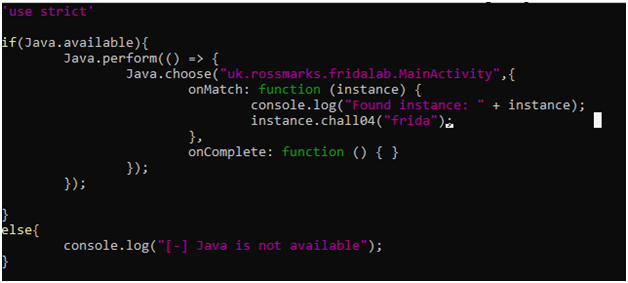
By running the above script with frida challenge04 is solved!
5 – Always send “frida” to chall05()
Looks the same as the previous challenge, but let’s see what the difference between jadx and objection is.
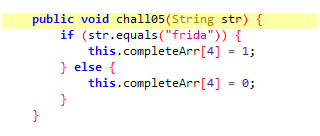
Didn’t find any difference with jdx. It’s time for runtime analysis with objection.
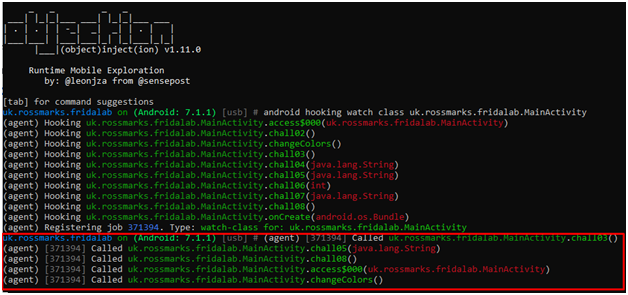
As we click the check button on apk, MainActivity class is invoked, and chall05() is called.
Our job here is to only modify arguments sent to function.
Similar to the previous challenge, but here the function is called while runtime.
So, we will overload the function and pass the “frida” argument in the original call.
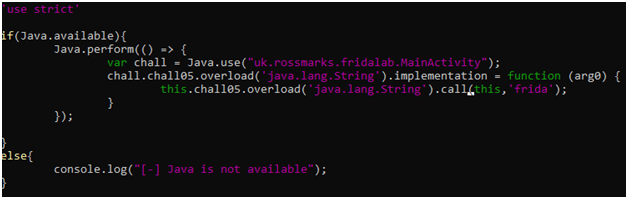
And ourlab gets solved by this simple script.
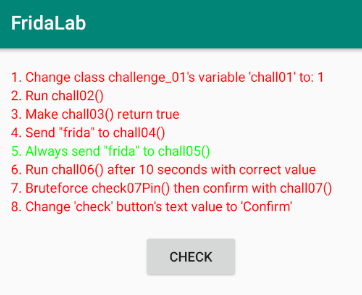
6 – Run chall06() after 10 seconds with correct value
Well, it looks like we have to run a certain function chall06() after 10 seconds.
Let’s look at its code.
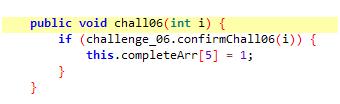
chall06() is calling confirmChall06() instead.
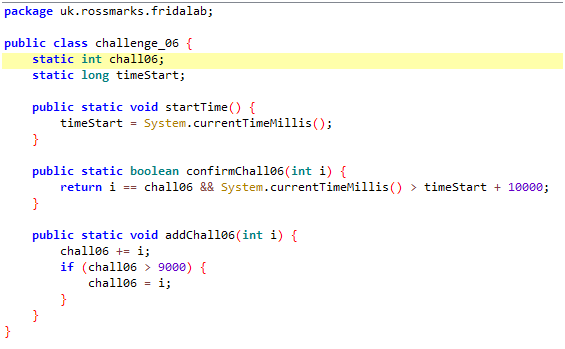
Here, confirmChall06() will return true:-
- If (input i is equal to chall06 variable) and ( current time > app start time + 10 second)
- Now, observe the addChall06() method :-
- chall06 variable is being set by addChall06() method and in turn this method is given a random value every 1 sec by the MainActivity class.
Also, by objection, we can confirm that chall06 is never called on runtime.
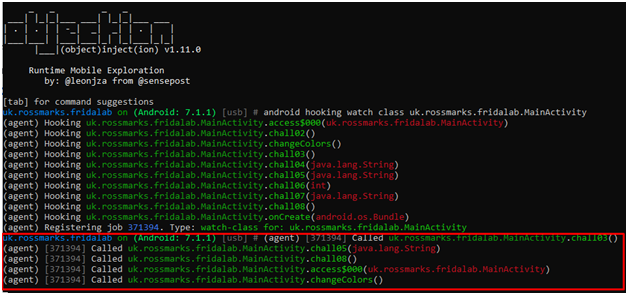
So our job here is to invoke an unused method after 10 seconds from the start of the application and give chall06() argument equal to challenge_06.chall06 variable from the challenge_06 class.
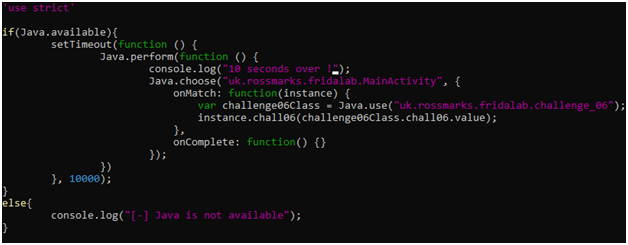
Run the script with Frida Tool and wait for 10 seconds. Then press “check” as usual.
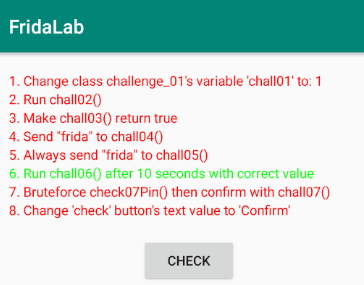
7 – Bruteforce check07Pin() then confirm with chall07()
This challenge says to bruteforce something. Let’s check with jadx.
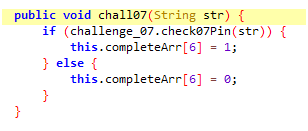
Our chall07 function takes an argument and again calls check07Pin().
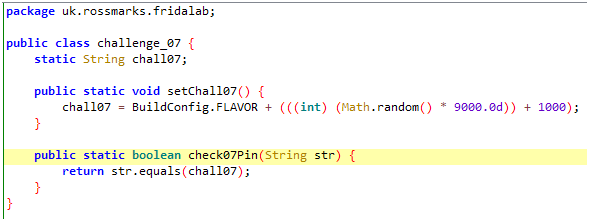
check07Pin returns true and our challenge is solved, if and only if our input argument is equal to chall07 variable of class challenge_07.
Again, after analysing the chall07, we can come to the conclusion that challenge_07.setChall07() is setting a random 4 digit number(stored as string).
Also, setChall07() is invoked by the MainActivity class at the runtime of the application.
There are many ways to solve this problem.
The easiest way is to use the check07Pin() function of challenge_07 class and compare it with every possible 4 digit number. We will stop when there is a match and will pass that number to chall07 function of MainActivity class.
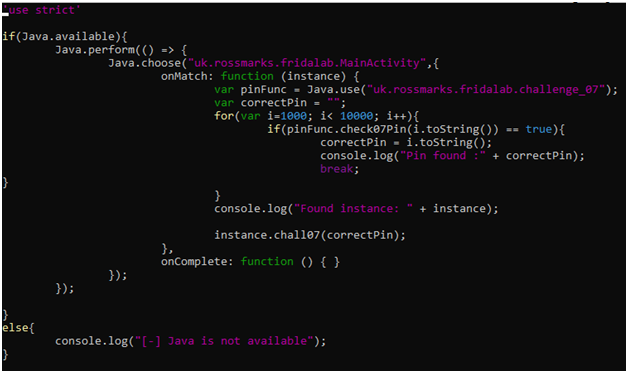
Run this beautiful script with Frida Tool.
8 – Change ‘check’ button’s text value to ‘Confirm’
Lastly, this challenge is about changing the ‘check’ button to the ‘confirm’ button (UI Manipulation).
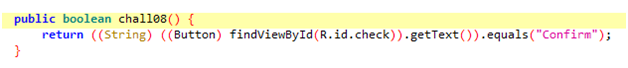
This function will return true if the button name (by default it is checked) is equal to “Confirm”.
findViewById connects our backend code with the User Interface elements, layouts, buttons, etc. Every component in the user interface has an ID associated with it, which allows you to control its actions from the backend. (from googling)
R is a Class in android that has the ids of all the views. findViewById is a method that finds the view from the layout resource file, that are attached with the current Activity.
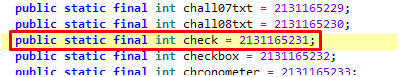
Our check variable has the following id.
Now, we will use android.widget.Button class to create our own button and then cast it on the checkid instance.
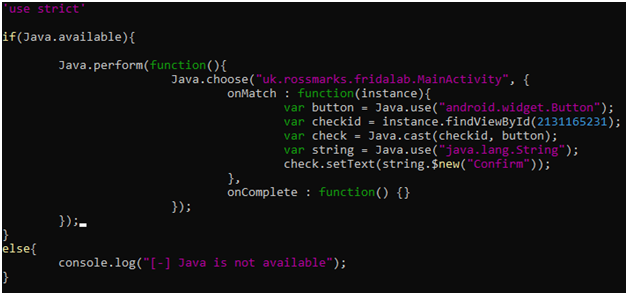
This is the simple script for the same.
Run it using Frida Tool, click on the button and observe the changes.
Conclusion
I hope you enjoyed solving the lab. I tried to explain everything logically; still, everything can’t be put down in a single blog.
Below are some references useful when writing Frida scripts.
https://frida.re/docs/javascript-api/#java
https://appsec-labs.com/portal/frida-cheatsheet-for-android/
You can contact me anytime for any questions, just shoot me an email at [email protected] .
Stay safe, wear a black hoodie and hack the world! 🙂


