Network Penetration Testing: The Complete Guide
March 14, 2023
What Is A Network Security Assessment?
March 27, 2023
In today’s digital age, cyber threats are becoming increasingly common and sophisticated, making it more important than ever for organizations to implement robust network security measures.
This blog will provide you with valuable insights into the best practices for network security that organizations can use to protect their networks and data from cyber threats.
We will discuss various techniques and strategies for network security, including implementing strong passwords and multi-factor authentication, keeping software and hardware up-to-date, using firewalls, conducting regular security audits, providing security awareness training, and implementing intrusion detection and prevention systems.
By the end of this blog, you will have a comprehensive understanding of the best practices for network security, and how they can be used to enhance the security of your organization’s networks and data with a complete well-researched checklist of the best practices for network security.
So, whether you’re a small business owner, an IT professional, or just interested in cybersecurity, this blog will provide you with valuable information that can help you stay safe online.
What exactly does Network Security Mean?
Network security is an essential component of any organization’s cybersecurity strategy. It involves implementing measures and policies to protect computer networks from unauthorized access, damage, or misuse.
Best practices for network security encompass a range of techniques and strategies that organizations can use to safeguard their networks and data from various cyber threats.
The layers of network security
Network security can be broken down into three main layers, each with its own set of practices and protocols. These layers are:
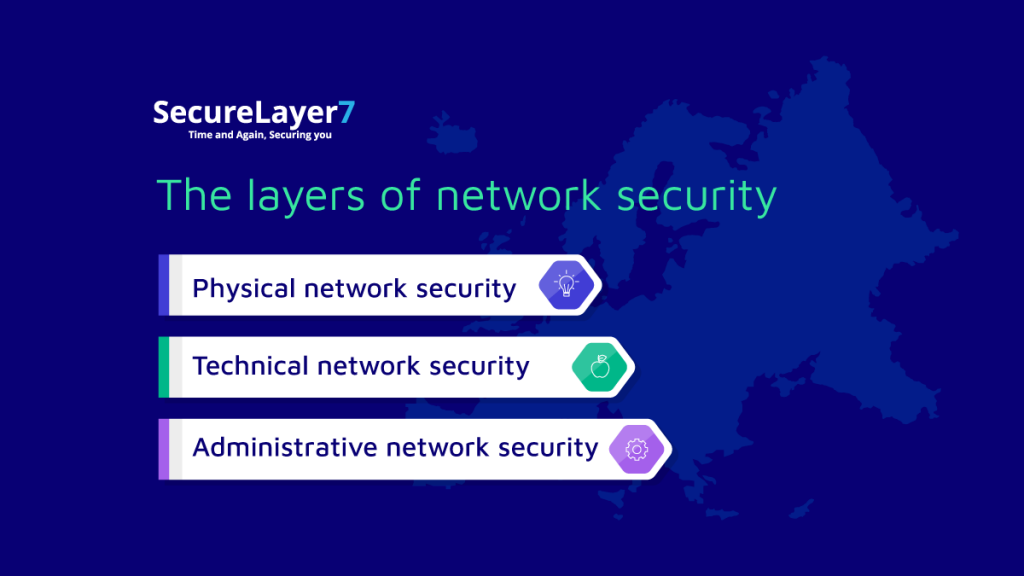
Physical network security
This layer involves securing the physical infrastructure of the network, such as the servers, routers, switches, and cabling. Physical security measures can include access controls, video surveillance, and alarm systems to protect against unauthorized physical access to the network.
Technical network security
This layer involves implementing technical security measures to protect the network from cyber threats, such as malware, viruses, and unauthorized access. Technical security measures can include firewalls, intrusion detection and prevention systems, encryption, and virtual private networks (VPNs).
Administrative network security
This layer involves implementing policies, procedures, and protocols to manage and control access to the network. Administrative security measures can include access controls, password policies, security awareness training, and regular security audits.
By implementing security measures across all three layers of network security, organizations can create a comprehensive network security strategy that addresses a wide range of cyber threats.
It’s important to note that network security is an ongoing process, and organizations must continually monitor and update their security measures to stay ahead of evolving threats.
Best practices for network security
Here is the checklist of 15 best practices that one can follow to enhance network security. Let us understand each one by one.
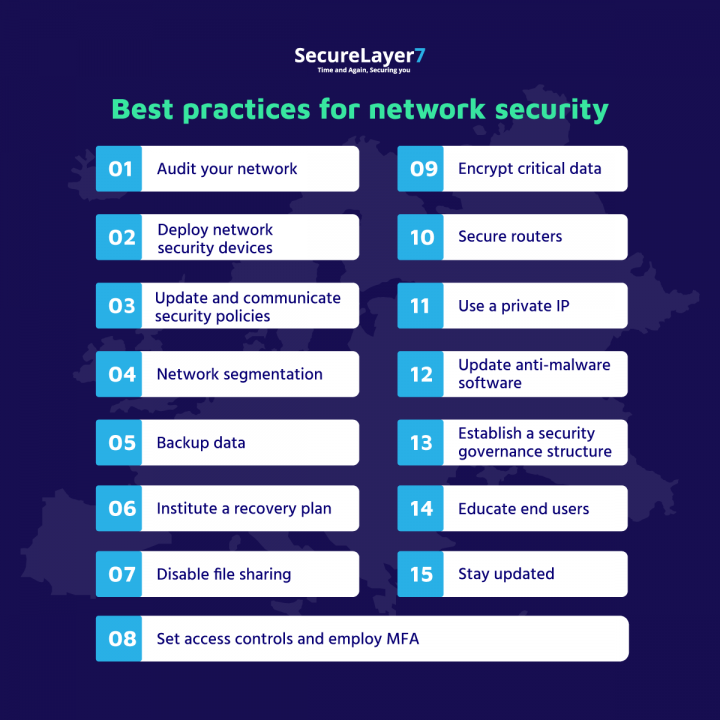
1. Audit your network
Conduct a thorough audit of your network to identify vulnerabilities and weaknesses that could be exploited by attackers. This includes identifying all devices and systems on your network, assessing the level of risk associated with each, and identifying areas where security measures could be improved.
2. Deploy network security devices
Implement network security devices, such as firewalls, intrusion detection and prevention systems, and VPNs, to protect your network from unauthorized access and attacks.
3. Update and communicate security policies
Regularly updating and communicating your organization’s security policies can help to ensure that all employees are aware of the best practices for network security and understand their roles and responsibilities in maintaining a secure network.
4. Network segmentation
Segmenting your network into smaller, more secure sub-networks can minimize the impact of a security breach and limit the spread of malware or other threats.
5. Backup data
Regularly backing up your data can help to minimize the impact of a data breach or other security incident.
6. Institute a recovery plan
Developing a recovery plan that outlines the steps to be taken in the event of a security incident can help to minimize the impact of the incident and facilitate a faster recovery.
7. Disable file sharing
Implementing access controls and multi-factor authentication can help to ensure that only authorized users have access to sensitive data and systems.
8. Set access controls and employ MFA
Ensuring that your routers are properly secured and configured can help to prevent unauthorized access to your network.
9. Encrypt critical data
Encrypting critical data can help to protect it from unauthorized access or theft.
10. Secure routers
Ensuring that your routers are properly secured and configured can help to prevent unauthorized access to your network.
11. Use a private IP
Using a private IP address for your network can help to prevent unauthorized access from outside the network.
12. Update anti-malware software
Regularly updating your anti-malware software can help to protect your network from new and emerging threats.
One of the most common areas for improvement in enterprise security is outdated antivirus or antimalware software. However, this is also one of the easiest to fix.
To address this issue, security professionals should conduct regular checks on their antimalware software and ensure that all devices are running the latest security software.
IT departments can also automate patch management wherever possible to keep the software up-to-date.
13. Establish a security governance structure
Establishing a security governance structure can help to ensure that network security is a priority throughout the organization.
To ensure network security, it is essential to establish a security governance structure. This involves setting up a framework that outlines the policies, procedures, and protocols for managing network security.
The structure should define the roles and responsibilities of individuals involved in managing security and responding to incidents. It should also include regular risk assessments and continuous monitoring to identify potential vulnerabilities and address them proactively.
Having a well-defined security governance structure helps organizations maintain a secure and compliant network environment.
14. Educate end users
Educating end-users on the best practices for network security can help to minimize the risk of security incidents caused by human error.
Given the prevalence of phishing attacks, it is crucial to raise end-user awareness. End-users are particularly susceptible to certain types of attacks that resemble regular communications.
As cybercriminals become more proficient at creating convincing emails and other forms of communication, the chances of a staff member falling victim to an attack increase.
To keep employees informed about the current threat landscape and associated security policies, ongoing end-user education should be integrated into a company’s culture.
15. Stay updated
Staying up-to-date with the latest security threats and best practices for network security can help to ensure that your network remains secure in the face of evolving threats.
Fortify your network with comprehensive penetration testing (SL7 pitch)
Cybersecurity threats are increasing at an alarming rate and it is crucial for businesses to fortify their networks against potential attacks.
Comprehensive penetration testing is a vital aspect of a cybersecurity strategy that can help businesses identify vulnerabilities in their network before they can be exploited by cybercriminals.
By simulating real-world attacks, penetration testing provides businesses with a realistic assessment of their security posture and enables them to address weaknesses proactively. At SecureLayer7, we offer comprehensive penetration testing services that provide a thorough evaluation of your network security, including the identification of potential liabilities and recommendations for remediation.
With our expert penetration testing services, you can rest assured that your network is fortified against potential cyber threats.”
Reach out to SecureLayer7 to start with your network protection.