
Cryptocurrency Mining Scripts Harnessing your cpu memory via Browsers
December 1, 2017
Dark Web: Accessing the hidden content Part- 1
December 30, 2017
What are fileless malwares?
Fileless malware are not typical malwares that probe directly or indirectly to install software on a victim’s machine and then execute.
Instead, tools that are built-in to Windows are hijacked and used to carry out attacks.
Why is it more dangerous?
Due to the usage of only default windows tools, no signatures for antivirus can detect such attacks.
How does fileless malware work?
Fileless malware attacks relies on default Windows tools, particularly PowerShell and Windows Management Instrumentation (WMI) for malicious activity. Let’s take a look at both:
- PowerShell
PowerShell is a powerful scripting language that provides unprecedented access to a machine’s inner core, including unrestricted access to Windows APIs. PowerShell also offers the benefit of being an inherent part of Windows that’s completely trusted so the commands it executes are usually ignored by security software.
Powershell features enabled attackers to get through Windows Firewall, run PowerShell scripts remotely or simply drop into an interactive PowerShell session, providing complete admin control over an endpoint.
Relevance with Filess Malware:
PowerShell used in a fileless malware attack completely compromises a single machine and performs subsequent lateral movement.
Reason for it’s high threat level
Powershell as a trusted signature, loaded directly through system memory apart from unrestricted access to the OS.
- Windows Management Instrumentation (WMI)
WMI allows administrators to install software and updates or self-query the OS.Using WMI one can execute files, delete/copy apart from a host of other activities.
WMI also allows for persistence by auto-running programs stealthily on startup or based on specific events.
Examples of fileless malware attacks
One of the most widespread was Operation Cobalt Kitty, this attack was based on a very sophisticated obfuscated PowerShell payload consisting of Cobalt Strike’s Beacon payload on the victim’s computers as well as fetch payloads from the command-and-control server.
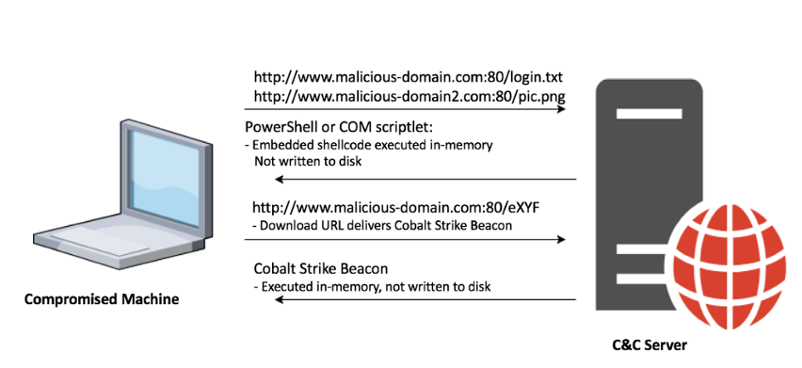
Filelessmalware Attack
Let’s take a brief look into it:
Operation Cobalt Kitty: A large-scale APT carried out by the OceanLotus Group
The attack went on around nearly six months without getting detected!
Phase one: Fileless operation (PowerShell and Cobalt Strike payloads)
This was the improved version of continuation of the original attack that began about a year prior to infection The threat actor operated a fileless PowerShell-based infrastructure, using customized PowerShell payloads taken from known offensive frameworks such as Cobalt Strike, PowerSploit and Nishang.
Phase two: Backdoors exploiting DLL-hijacking and using DNS tunneling
The attackers introduced two sophisticated backdoors that to deploy on selected targets. At the time of the attack, these backdoors were undetected and undocumented by any security vendor.
Phase three: Novel MS Outlook backdoor and lateral movement spree
Attackers harvested credentials stored on the compromised machines and performed lateral movement and infected new machines
Phase four: New arsenal and attempt to restore PowerShell infrastructure
Attackers returned to the scene and introduced new and improved tools aimed at bypassing the security mitigations that were implemented by the company’s IT team. These tools and methods mainly allowed them to bypass the PowerShell execution restrictions and password dumping mitigations.
Detection and prevention of fileless malware
These attacks reside almost completely in memory, and use legitimate system administration tools to execute and propagate, making determining what’s legitimate PowerShell use and what’s attacker activity very challenging.
Certain features in PowerShell also make it difficult to figure out when the tool is being used by attackers.
In such cases, Behavioral detection is the best way to tackle this challenge.
Behavioral Analysis and detection operates on the malware specimen’s interactions with its environment: File system,registry, network, as well as other processes and OS components.
The isolated system is then proved with monitoring tools observe the specimen’s execution.
More reading on: https://digital-forensics.sans.org/blog/2010/10/11/3-phases-malware-analysis-behavioral-code-memory-forensics/
https://www.cybereason.com/blog/operation-cobalt-kitty-apt


