The 6 Steps In The Penetration Testing Process
May 15, 2023
The Complete Cybersecurity Checklist For Startups And Small Businesses
May 24, 2023
Picture this: you’ve just launched your startup and are eager to hit the ground running. But with cyber threats on the rise, have you considered how secure your company’s systems truly are? Enter penetration testing: a critical security assessment that puts your company’s defenses to the ultimate test. As a startup, it’s important to understand what to expect during a pen test and how it can help you identify and address potential vulnerabilities.
In this blog post, we’ll explore the ins and outs of penetration testing for startups, from the initial scoping to the final report, and everything in between. So, buckle up and get ready to take your startup’s security to the next level!
What Should You Expect Throughout A Pentest
By having clear expectations for the pen testing process and actively engaging with the testing team, you can ensure that you get the most out of the assessment and improve the overall security posture of your startup.
As we progress further into the blog, we will learn about what to expect in different types of pen tests. We will also discover what to expect in each stage of the testing process.
Different types of Pentests
Different types of pen testing set different expectations and deliver the best results in very different ways. There are three types of pen tests we will discuss. Let us take a look at what to expect from each of them.

Black-box Pentest:
This is where the tester has no prior knowledge of the system or network being tested. The tester will simulate an attack from an external attacker, attempting to gain access to the system or network and identify vulnerabilities.
During a black-box pentest, you can expect the tester to conduct reconnaissance to gather information about the target, such as network topology and IP addresses. The tester will then attempt to exploit vulnerabilities using various tools and techniques, such as social engineering, port scanning and vulnerability scanning.
White-box Pentest
This is where the tester has full access to the system or network being tested, including detailed knowledge of the system architecture, source code, and other sensitive information.
During a white-box pentest, you can expect the tester to perform a thorough analysis of the system or network. The tester will review source code, perform network and system scans, and use advanced tools and techniques to identify vulnerabilities.
In all types of pen tests, you should expect the tester to provide a report detailing their findings and recommendations for improving the security of the system or network.
It’s important for you to note that the scope of the pentest should be clearly defined before the test begins to ensure that the tester is not inadvertently causing damage to the system or network.
Grey-box Pentest
This is where the tester has some knowledge of the system or network being tested. The tester may have access to limited information, such as network diagrams or login credentials, but will not have complete access to the system or network.
During a grey-box pentest, you can expect the tester to use a combination of black-box and white-box testing techniques. The tester will attempt to identify vulnerabilities based on the limited knowledge they have of the system or network.
What To Expect In Each Step Of The Pentest Process?
We now know what to expect during the process of pentesting and what to expect in terms of results. Let us now take a closer look at each phase of the pen test process.
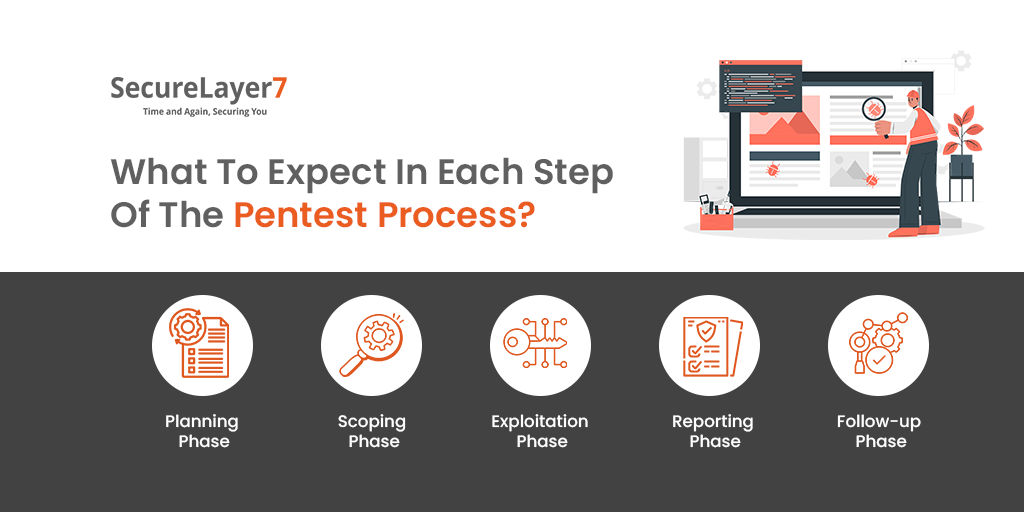
Planning Phase
During this phase, you’ll meet with the pentest provider to discuss your infrastructure and security objectives. The provider will ask questions to gain a better understanding of your organization’s environment and potential risks.
You should be transparent and provide details about your infra setup, including any known vulnerabilities or issues. This will help the provider tailor the test based on your specific needs. You can also ask questions to clarify the process, understand the timeframe, and ensure that you get the most out of the testing.
Scoping Phase
In this phase, the pentest provider will gather information about your infrastructure, including network topology, web applications, and other systems. They will need access to your systems, so you should ensure that you provide them with the necessary permissions to do so.
The provider will conduct reconnaissance and map out the attack surface, identifying potential vulnerabilities and weaknesses.
Exploitation Phase
This is where the provider begins to simulate attacks on your systems. They will use various tools and techniques to identify vulnerabilities and attempt to gain unauthorized access to your systems. During this phase, you may notice some network or system performance issues as the provider runs their scans and tests. The provider will document all vulnerabilities and report them to you at the end of the testing.
Reporting Phase
Once the testing is complete, the provider will provide you with a comprehensive report that includes an overview of the testing methodology, findings, and recommendations. Each vulnerability will be listed and explained in detail, including the potential impact and likelihood of exploitation. You should review the report carefully and ask any questions you may have to ensure that you understand the findings and recommendations.
Follow-up Phase
After the vulnerabilities have been fixed, the provider can be tasked to recheck if the fixes have been made correctly and if security has been improved. The follow-up phase is optional but recommended, as it helps to ensure that the remediation efforts were successful and that your infrastructure is now more secure. The provider will retest the systems to verify that the vulnerabilities have been properly remediated, and provide you with a final report.
What does SecureLayer7 have to provide?
We, SecureLayer7, are a leading cybersecurity firm that specializes in providing advanced manual testing and other value-added services to our clients.
Our state-of-the-art pen tests are designed to provide as much value as possible to clients, going beyond the average checklist and scanner tools to provide a comprehensive manual pentest that is conducted by security experts.
Besides advanced manual testing, we also provide complete transparency through our very own BugDazz platform, detailed pentest reports that provide a deep-dive analysis of a client’s security posture, strategic mitigation that helps clients prioritize their remediation efforts, and easy retest capabilities to ensure that all vulnerabilities are properly remediated.
By leveraging these services, our clients can improve their security posture and better protect their critical assets from cyber threats.
Below are some of the additional services that we provide to ensure that our clients get the best possible results.
Advanced Manual Testing
Our pen tests go beyond the average checklist and scanner tools, offering a comprehensive manual pentest that is conducted by experienced security experts. This approach enables us to identify vulnerabilities that automated tools may miss and provide a more accurate assessment of a client’s security posture.
Complete Transparency:
Our BugDazz platform gives our clients complete visibility into each stage of their pentest, from planning and scoping to exploitation and reporting. This platform enables clients to track the progress of their pentest in real-time, view test results, and collaborate with our team of experts.
Detailed Pentest Reports
We provide detailed reports that offer a deep-dive analysis of a client’s security posture, including vulnerabilities discovered, recommendations for remediation, and potential impact on the organization’s overall security. These reports help our clients understand their risks and make informed decisions about prioritizing remediation efforts.
Strategic Mitigation
We go above and beyond by providing a strategy that helps clients understand which vulnerabilities are critical and need to be fixed first. This approach enables clients to prioritize remediation efforts and allocate resources more effectively to improve their overall security posture.
Easy Retest
The BugDazz platform ensures that clients can raise a ticket for a fix verification asynchronously and track progress while the pentest is happening on other areas of their infrastructure. This leads to faster, more seamless pentesting and ensures that all vulnerabilities are properly remediated.
Get in touch with our experts today to secure your startup today, and rest assured knowing the SecureLayer7 will help make your systems impermeable.


