
Web Services and API Penetration Testing Part #1
January 6, 2018
Web Services and API Penetration Testing Part #2
February 8, 2018
This blog is about a technique used by attackers to perform a phishing attack by using the Tabnabbing. Although, this was technique was invented a long time ago, but there are very few articles on this. Hence, I thought to write something on this topic.
What is tabnabbing?
Tabnabbing is a client side attack web based attack. It is not a vulnerability in the web application but a phishing technique. The attack takes advantage of users inattention in regards to tabs and the ability of javascript to rewrite a tab.
Demo on tabnabbing:
Following are the steps for demonstration:
1. Attacker sends a link of his website to the victim (using email, chat app, IM, redirection using a third party website). Link: http://127.0.0.1:1234/file.html
2. Victim clicks on that link. Attacker’s website opens:
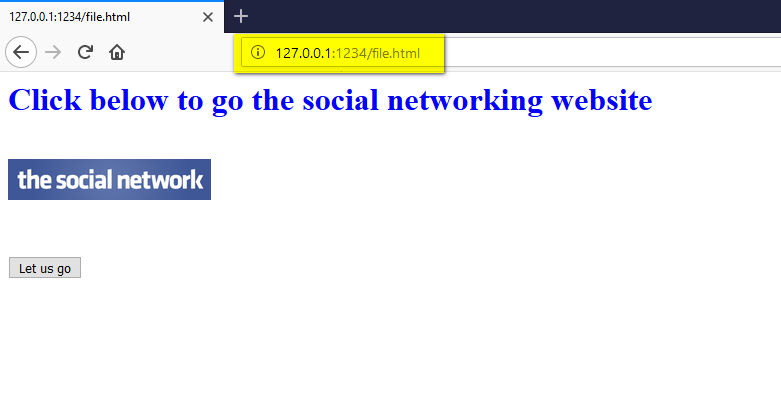
3. As per the directions on the website, the victim clicks on the ‘Let us go’ button to go to the social networking site.
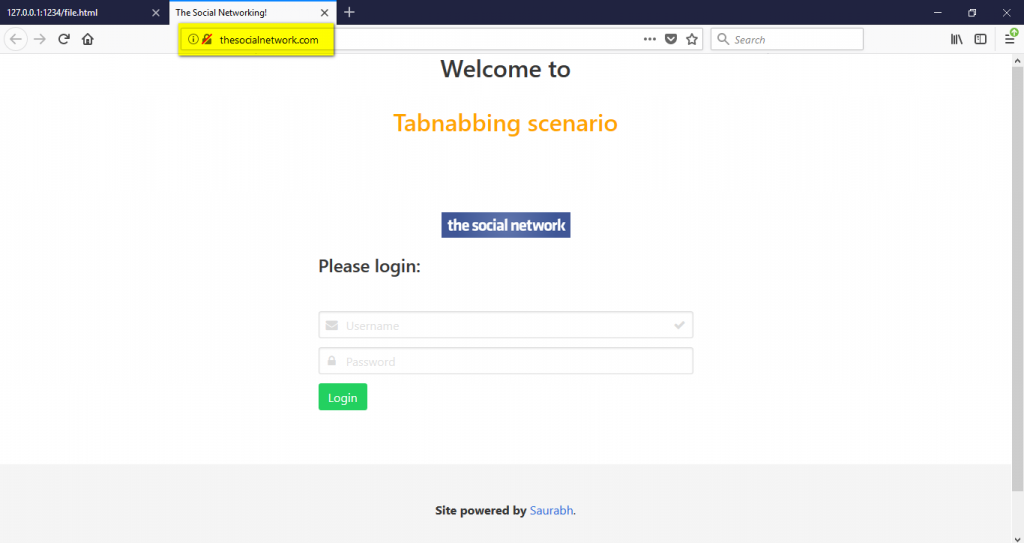
4. Victim sees the domain name in the address bar and firmly belive that it is a genuine website.
5. Victim waits for few seconds on the same page OR victim goes to some other tab in the same browser window.
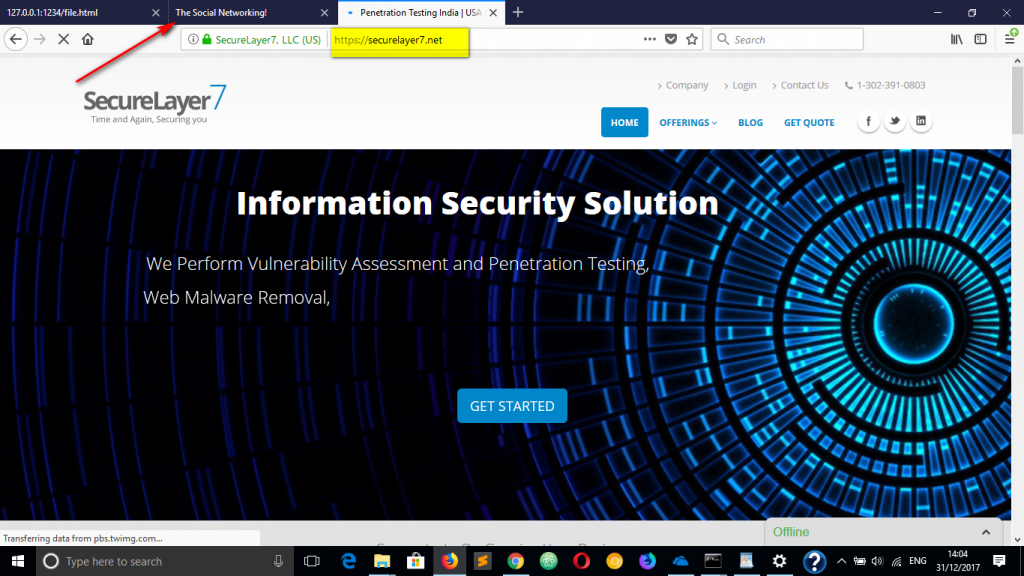
6. Victim returns back on the social networking site page.
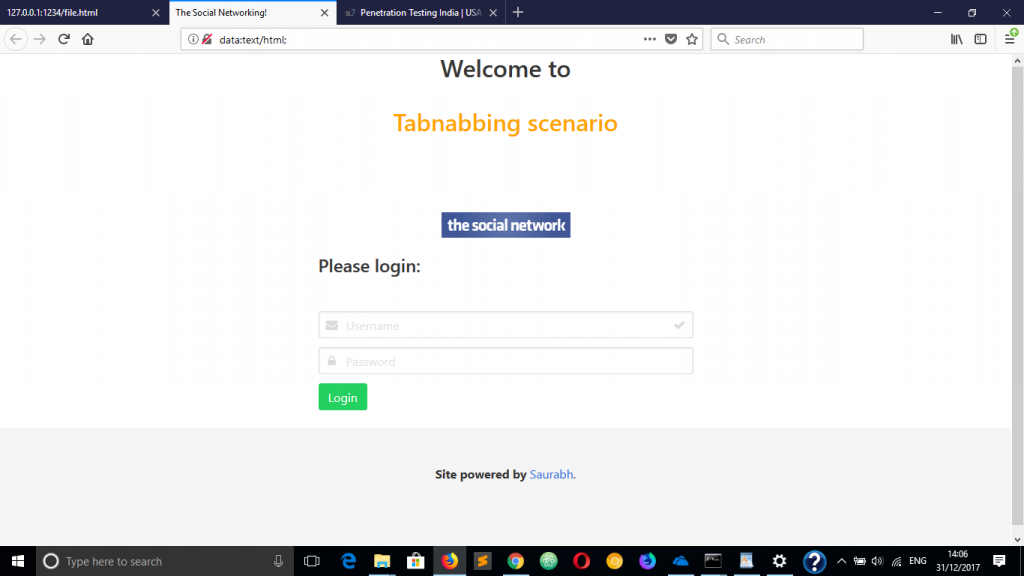
7. The victim enters the credentials believing it is a genuine site. But fails to observe the domain name which has changes from step 4 to 5.
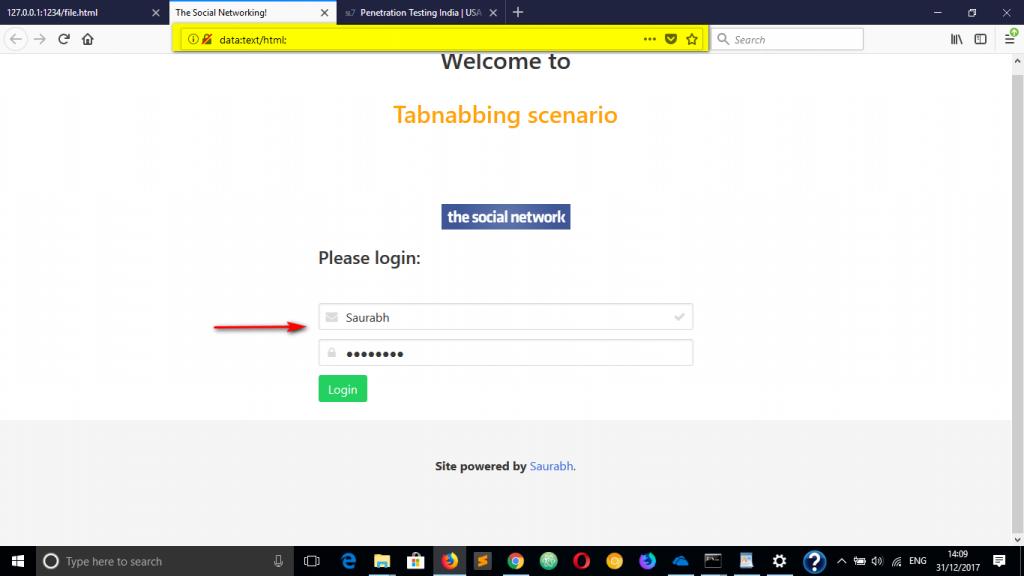
8. Victim clicks on Login button and the credentials get sent to attacker’s server because of phishing code that is hosted on new domain (data URI).
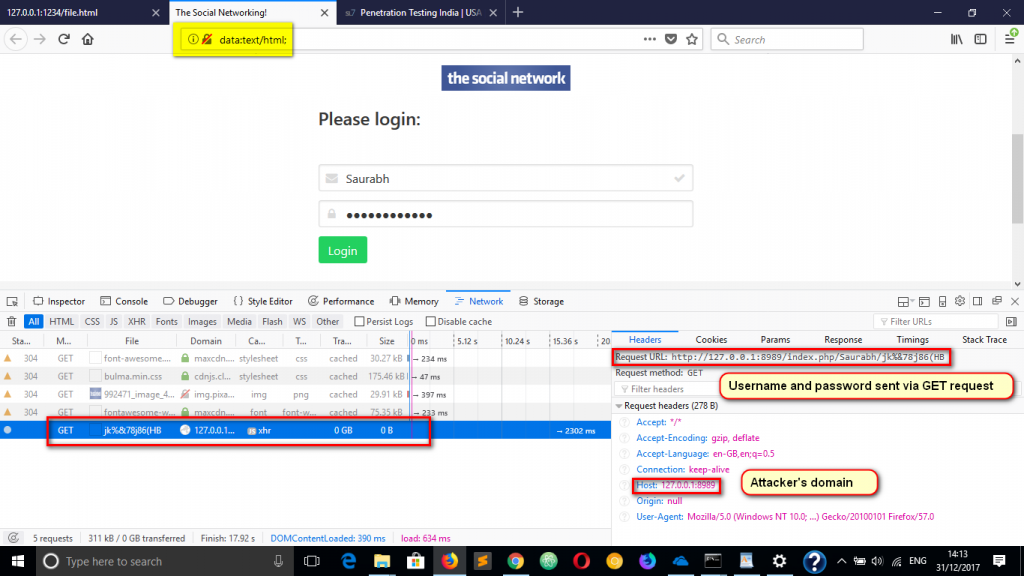
How did it happen?
The 3 lines of JS code made this:
var w; (A new variable is declared)
w = window.open(‘http://thesocialnetwork’, ‘target’); (It is assigned a value. That value is to perform action of opening a website in a new tab)
w.location.replace(‘data:text/html;,the duplicate html source code here’); (The address of the new tab is replaced with a data URI that contains the phishing code)
In the data URI, we deliberately add many empty spaces so that the victim fails to observe our code.
How to fix this issue?
As we have discussed before, this is not a vulnerability but a phishing technique. Hence, while entering their credentials, the users should confirm if the site is genuine or not by looking at the address bar.
You can find the phishing code here


1 Comment
Another good way to enhance this is by adding a “dummy” domain after the text/html, and then using the spaces to exceed the visible area. You can add HTML to cover up the fake domain text from showing up on the page.
This is a good explanation of the technique:
https://www.wordfence.com/blog/2017/01/gmail-phishing-data-uri/