
Breaking Down Data Lake Security
November 21, 2022
The Complete 2023 HIPAA Compliance Checklist
December 6, 2022
While the costs, uptime, customer support, and scalability are critical factors to consider when deploying your web service, placing its security on the back burner is a bad practice that can cause disastrous ramifications for the business.
As malicious actors exploit vulnerabilities in websites and applications to steal confidential information and lay waste to companies, it is essential to understand the importance of your data and what means you could employ to guard it.
Protecting your web service or application from hacks can ensure that you continue unhindered in your business’s roadmap to safely leverage your data to streamline operations, improve customer service, personalize marketing campaigns, and increase revenue and profits.
An integral part of web service hosting is knowing the fundamental security practices in protecting it. This article explores web services, how they work, their weaknesses, and how penetration testing could defend them.
What is a Web Service?
A web service is a software composed of a standardized XML messaging system that leverages the internet to facilitate interactions between web applications.
Since all web service communications are in XML, they are not restricted to any operating system or programming language, thus facilitating cross-platform communications between applications using Windows, Unix, Perl, Python, and Java.
Open standards such as TCP/IP, HTTP, Java, HTML, and XML are the foundation for web services.
The widespread adoption of web services in cloud-based, governmental, or service-oriented architectures has resulted in a broader scope of security challenges, such as injection attacks, phishing, Denial-of-Services (DoS) attacks, and more.
It is worth knowing that penetration testing is a practical approach to identifying and addressing vulnerabilities while reducing the overall attack surface of web services.
How do Web Services Work?
Web services depend on XML to tag the data, SOAP to transfer a message, and WSDL to describe service availability.
For a better understanding, take the SOAP-based Web Service Anatomy. Here, web services contain various components that maintain the standard of communication. When any service consumer wants to use a web service, they need to request from a service provider.
XML data in the SOAP format, the service receiver communicates requests with the service provider for any web services specified in the WSDL file.
Service providers then give the WSDL file to service consumers, which defines how the web services are accessed.
If the service consumer is unaware of any web service provider, it will look for the UDDI, which maintains the list of service providers for the particular web service.
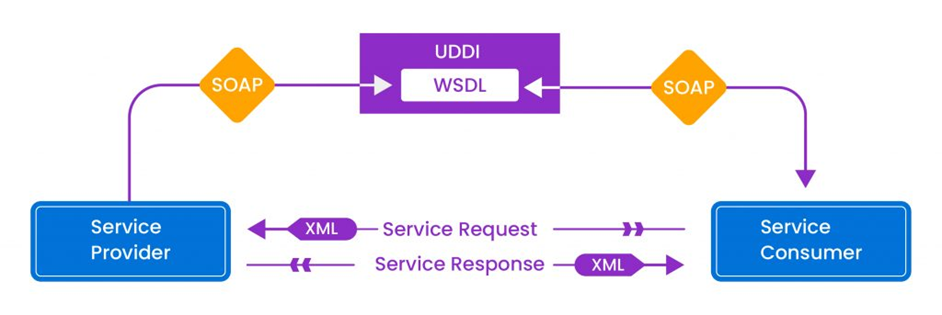
Component of web services
A web service primarily consists of two components:
- Service consumer – The service consumer is the client who requests particular web services.
- Service provider – The service provider is the server that receives the requests and responds to the client with the appropriate service.
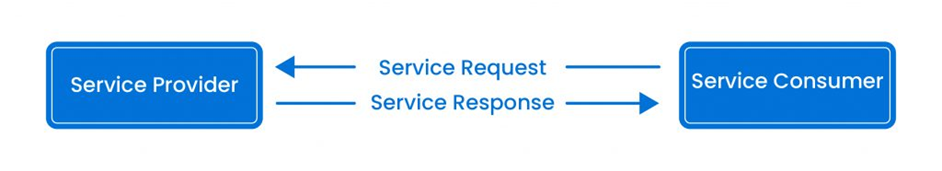
Anatomy of Web Services
Web service platforms are a combination of XML and HTTP. Their anatomy can consist of the following four elements:
XML
Extensible Markup Language (XML) is a language used to communicate in the form of SOAP messages.
SOAP
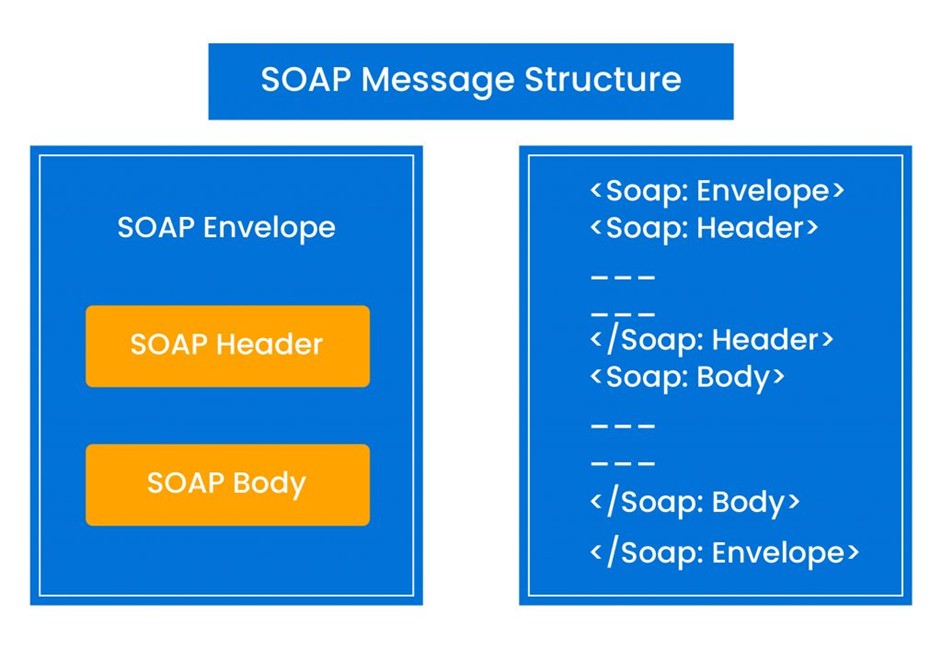
Simple Object Access Protocol (SOAP) is a format used to send XML requests. Here, using the SOAP protocol, a client can send a service request to the web service provider server that will then respond with the same protocol with the requested service.
SOAP messages consist of a Root Envelope element which indicates the header and body of the message. The optional SOAP header can contain metadata or application-specific information about SOAP messages, including the attributes for processing the directive.
The mandatory SOAP body holds the actual XML data, or SOAP Message stores the web service’s operations and parameters.
The concrete structure of the SOAP message is to communicate with a web service, and the Web Service Description Language (WSDL) describes the binding information.
UDDI
Universal Description, Discovery, and Integration (UDDI) contains a list of service providers who registered for a particular web service, so request consumers or clients can find all service providers for any web service in UDDI.
WSDL
A Web Services Description Language (WSDL) file consists of sections containing all the crucial information about the web service to be tested.
The first section describes the logical interface offered by the web service provider. The second provides clients with endpoint information like HTTP port numbers and instructions on composing web service requests, such as how the SOAP message should be represented and delivered.
Web Service Penetration Testing
Securing your web services is necessary to ensure that malicious attackers do not intercept any data transmitted between a user and the web service.
These attacks primarily occur because hackers can exploit your web service vulnerabilities and bypass its application controls.
Penetration testing is an excellent solution to identify problematic services and applications with potential vulnerabilities and misconfigurations.
Here are some of the common attack vectors malicious actors exploit to gain access to your web applications:
- SQL/OS command injection
- Authorizations issues
- WSDL Enumeration
- Broken Access Control
- Xpath Injection
- Session Tampering
- Bruteforce
- Directory Traversal
- Content Spoofing
- Information Disclosure
Prerequisites for web service penetration testing
Before you can conduct penetration on your web services, some of the prerequisites you require are a sample API file such as WSDL or SOAP, sample requests and responses to understand the values and data parsing, and entry points/URLs.
Here are the specific requirements for conducting black and grey box pen tests:
Prerequisites of Black box web services penetration testing:
A Web Service Description Language (WSDL) file would be required to perform a black box web service API penetration test.
Prerequisites of Grey box web Services penetration testing:
A grey box web service API penetration test requires sample requests and responses for methods along with the WSDL file.
Stages of penetration testing of web service
Our web service penetration tests typically consist of six stages:
- Information gathering
- Black box
- Google hacking using dorks to discover web services for websites hosted over a network
- UDDI
- Web service discovery when there is no WSDL provided
- Authentication type discovery
Web service pentest tools
Tools play an important role in performing practical penetration tests. We have two types of testing tools, automated and manual, to perform API security penetration testing.
Automated testing tools
- SoapUI Pro
- OWASP ZAP
- IBM AppScan
- HP Webinspect
- WSBang
- WSMap
- WSDigger
Manual tools
- Soap UI Free
- Burp Suite Pro
- Postman (with burp)
Extensions
- SAML Editor
- SAML Encoder / Decoder
- WSDL Wizard
- Wsdler
- SOA Client
Test cases to find in web services
The following are some attack vectors that penetration testing helps identify and mitigate.
- Fuzzing
- XSS /SQLi/ Malformed XML
- File Upload
- Xpath Injection
- XML Bomb (DoS)
- Authentication-based attacks
- Replay attacks
- Session fixation
- XML Signature wrapping
- Session timeout
- Host Cipher Support/ Valid Certificate/ Protocol Support
- Hashing Algorithm Support
Leaving these web service test cases unattended can increase the attack surface of your websites and applications.
A critical practice is periodically conducting scans to weed out and mitigate such threats. SOAP UI Pro is a robust tool that can help quickly identify all exploits plaguing your systems.
How to conduct a scan with SOAP UI
Performing an automated scan using SOAP UI enables you to get a preliminary first-hand security report of the engaged web services. Let us explore the steps and approach that SOAP UI Pro takes to provide an accurate and comprehensive scan of your web service.
Step 1: Launch the SOAP UI application and create a functional test case.
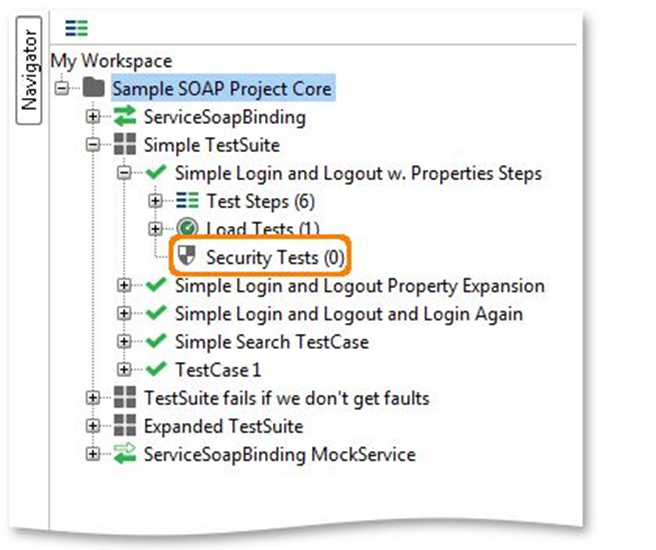
Step 2: Create a new security test from the simple TestSuite dropdown menu.
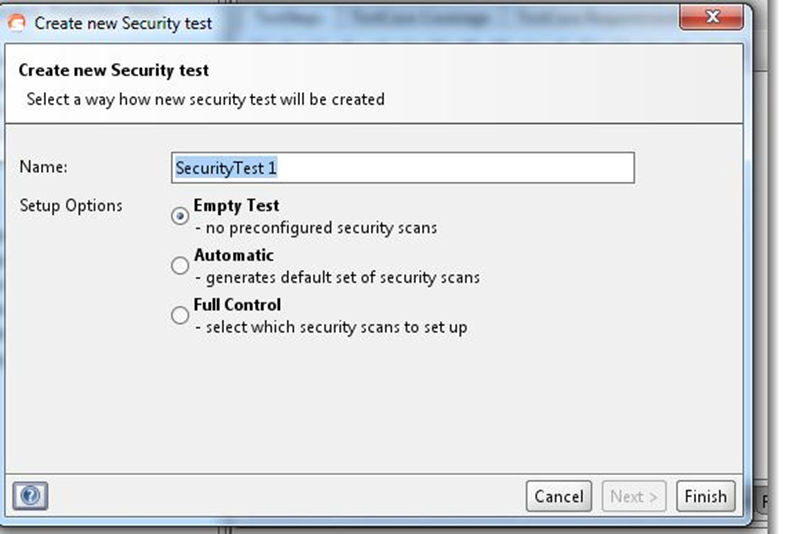
Step 3: Select the “Auto” mode to generate default security scans and assertions for the Test Steps in your TestCase and click on the “Next” button.
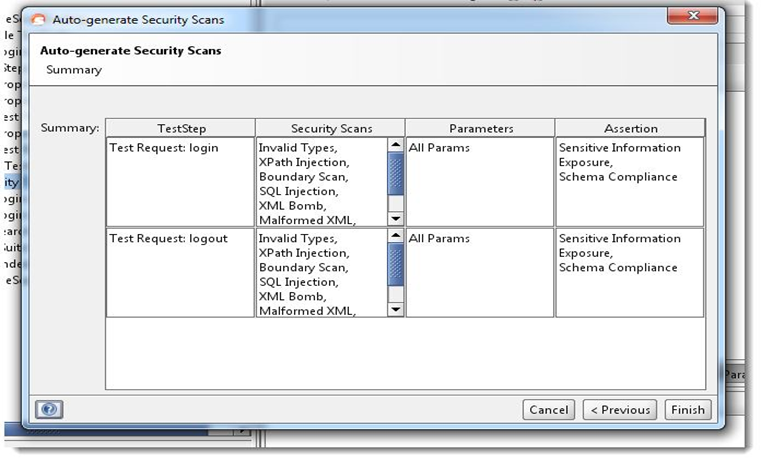
Step 4: Press “OK” to create the Security Test with the described configuration and open the Security Test window:
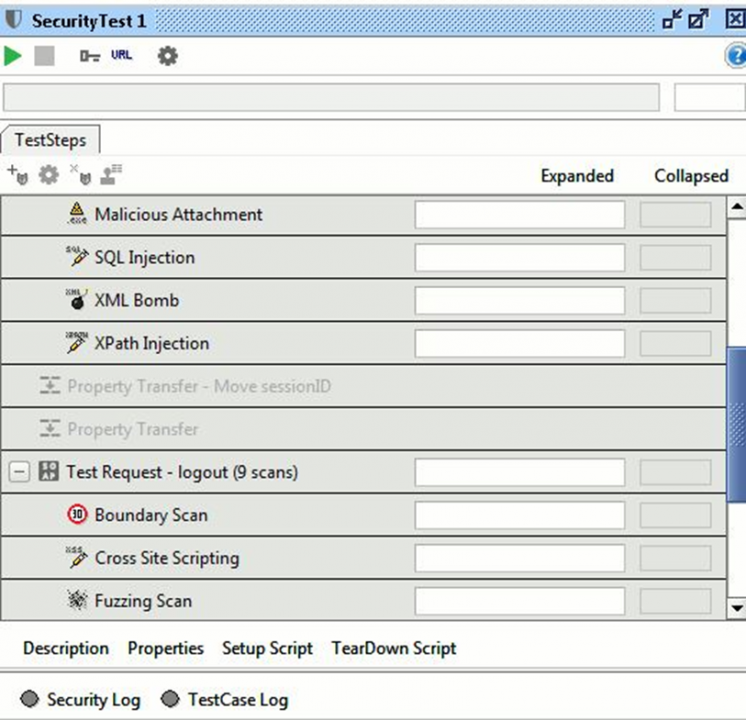
Step 5: Now run the security test.
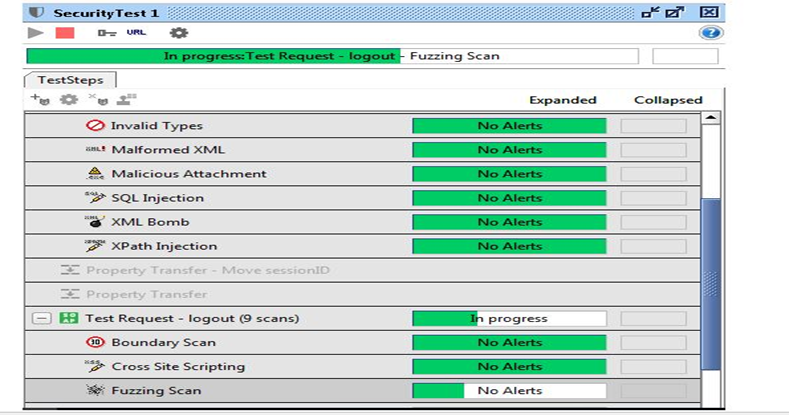
Step 6: Once the scan is complete, SOAP UI Pro will present a summary with a detailed overview of each test step, the security scans conducted on each of them, and the parameters and assertions. With this output, you can ascertain where you are vulnerable and generate assessment reports for your assessment.
You can practice penetration tests on VMS (virtual memory-based operating system) for vulnerabilities in web services using tools such as OWASP Mutillidae, OWASP WebGoat, DVWS, and PenTester Lab: Axis2 Web Service and Tomcat Manager.
Get a web service pentest done with SL7
Attackers can easily breach your systems and steal sensitive data without a robust line of defense for your web service infrastructure. So it is essential to choose the fitting service provider and implementation strategy to identify and mitigate vulnerabilities swiftly.
SecureLayer7 helps you scan and review your web services and configurations to stay optimally protected. Our pentest approach goes beyond the test cases mentioned in the OWASP top 10 SANS and NIST frameworks.
We help customers spot risky web service vulnerabilities such as authentication, authorization, and logic vulnerabilities which may result in data breaches. Our PaaS services include web application testing, mobile app penetration testing, thick client penetration testing, and VOIP penetration testing.
We are renowned amongst enterprises and SME organizations that use our penetration testing application to perform and act on continuous pen tests. Contact us now to find out more.


