An Overview: Red Team Vs Blue team – Securelayer7
April 24, 2023
Penetration Testing vs Vulnerability Scanning: A Comparison
April 26, 2023
DNS Rebinding is a technique that allows attackers to bypass the Same-Origin Policy (SOP) of web browsers. The Same-Origin Policy is a security feature that restricts web pages from making requests to a different domain than the one it originated from.
With DNS Rebinding, an attacker can bypass the SOP and make requests to an internal network, allowing them to exploit vulnerabilities on the server.
In this blog, we will explore the SSRF via DNS Rebinding attack, it’s impact, the remediation techniques available to prevent them, and conclude how to mitigate these attacks.
What is the SSRF DNS Rebinding attack?
Server-Side Request Forgery (SSRF) is a security vulnerability that occurs when an attacker can manipulate input processed by an application, causing it to make unintended requests to internal or external systems. (Read more about SSRF here)
The DNS rebinding attack is an SSRF attack involving an attacker changing the IP address that a domain name resolves to bypass same-origin policy restrictions and access resources on a victim’s internal network.
DNS Rebinding
This is the most popular type of SSRF. It is usually under the cover, and most developers don’t know about it.
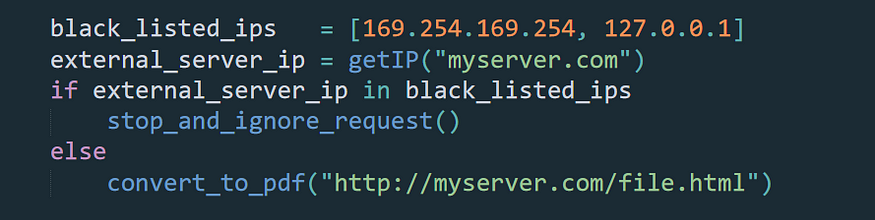
Let’s imagine that you’re building a website for HTML to PDF conversion. Here application server performs interaction on the external IP/server via the requested external server IP and blocked EC2 IP and localhost IP to perform the interaction.
Example
Take the following example that shows how the application DNS server works and looks for blacklisted IPs.
1) WEBSITE-DNS
WEBSITE: What is myserver.com IP Address?
DNS: myserver.com IP Address is 123.123.123.123
WEBSITE: OK2) WEBSITE-WEBSITE
WEBSITE: IS 123.123.123.123 Blacklisted?
WEBSITE: NO
WEBSITE: Send GET request to http://myserver.com/file.html3) WEBSITE-DNS
WEBSITE: What is myserver.com IP?
DNS: myserver.com IP Address is 123.123.123.123
WEBSITE: OK4) WEBSITE-USER
WEBSITE: Here is your PDF with the content of http://(123.123.123.123)/file.html
Looking at this code we found that the server checks the domain IP against the blacklist before continuing execution. At first glance, this seems to be secure but the truth is it’s not.
The Domain Name System (DNS) is a hierarchical and decentralized naming system for computers, services, or other resources connected to the Internet.
In order for the website server to know your server IP address, it has to perform a DNS request and parse the response which looks like this.
root@DESKTOP-R5P8K4U:~# dig myserver.com; <<>> DiG 9.11.3-1ubuntu1.7-Ubuntu <<>> myserver.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 2232
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1452
;; QUESTION SECTION:
;google.com. IN A;; ANSWER SECTION:
myserver.com. 85 IN A 123.123.123.123;; Query time: 124 msec
;; SERVER: 1.0.0.1#53(1.0.0.1)
;; WHEN: Wed Jan 15 16:23:49 EET 2020
;; MSG SIZE rcvd: 55
Now the website server knows that your server has the IP (123.123.123.123)
Back to our example. We know now that we need a way to trick the server into believing that our website IP is not blacklisted and fetch it.
This is important because if the server believes that the user’s IP is not blacklisted, it will fetch the user’s resources, allowing the attacker to gain access to the user’s sensitive information or control their system.
DNS rebinding works by exploiting the fact that DNS responses can include multiple IP addresses for a single domain name. An attacker can create a malicious website that includes JavaScript code that repeatedly sends DNS queries to their own server.
The first query returns an IP address that is not blacklisted, and the second query returns the IP address of the user’s server. The JavaScript code then sends a request to the user’s server using the IP address returned by the second DNS query.
Since the server now believes that the user’s IP is not blacklisted, it will fetch the resources from the user’s server, allowing the attacker to execute their attack.
If we set the IP address of myserver.com to a legitimate IP address (such as 123.123.123.123), and then change it to a non-routable IP address (like 169.254.169.254) after the server finishes, we could potentially circumvent certain security checks and access the EC2 IP. This technique is known as DNS rebinding
Remediation Techniques
There are several remediation techniques available to prevent DNS rebinding attacks. The following are some of the most effective techniques.
- Same-Origin Policy (SOP): The SOP is a security feature iin web browsers that prevent scripts running in one context from accessing resources in a different context. By default, the SOP prevents scripts running on a web page from accessing resources on a different domain. However, an attacker can bypass the SOP using DNS rebinding. To prevent this, developers can implement additional checks to ensure that the requested resource is on a trusted domain.
- DNS Pinning: DNS pinning is a technique that allows a website to “pin” a specific IP address to a domain name. This can prevent DNS rebinding attacks by ensuring that the browser only communicates with the expected IP address. DNS pinning can be implemented using HTTP headers or JavaScript.
- IP Address Whitelisting: Organizations can whitelist IP addresses allowed to access internal resources. This can prevent DNS rebinding attacks by ensuring that only trusted IP addresses can access sensitive data or systems.
- Firewall Rules: Firewall rules can help to prevent unauthorized access to internal resources. This can include blocking traffic from unknown or suspicious IP addresses, limiting access to specific ports or services, and implementing intrusion detection and prevention systems (IDPS).
Recap – SSRF via DNS Rebinding
SSRF via DNS rebinding attacks seriously threaten organizations that rely on web applications for their business operations.
These attacks can result in data theft, system compromise, network access, and reputation damage. To prevent DNS rebinding attacks, developers can implement techniques such as SOP, DNS pinning, IP address whitelisting, and firewall rules.
Organizations must stay up-to-date with the latest security trends and vulnerabilities to ensure their web applications remain secure. They can protect their sensitive data and systems from malicious attackers by taking proactive measures to prevent DNS rebinding attacks. Discover how to strengthen your web application’s security with SecureLayer7!
Our experts can provide solutions to prevent SSRF via DNS rebinding attacks and keep your data secure. Connect with us now to learn more and protect your business!