
Webinar Cybersecurity CISO: Cybersecurity Trends for the digital ecosystem in 2021
December 27, 2020
Beginning for the search of cybersecurity jobs ended at SL7 leading my career a new start
January 6, 2021
Introduction
The year 2021 just had just started and we got struck with global pandemic COVID-19 caused by the novel coronavirus. With this global fear, one more unwanted danger came along but in the virtual world of cyberspace. And that is phishing attacks. From scam artists to blackhat hackers or threat actors started leveraging the situation and psychological fear to deceive the general public for sensitive personal information. This also impacts businesses relying on online presence and leakage of vital business information or trade secrets for example by an employee, which can cause huge disruptions in an ongoing operation.
Current time is so critical and the global market is already at the edge of facing recession, such attacks in cyberspace can completely shutdown Businesses in Information technology.
Identifying the Coronavirus phishing attempt
For protecting one from such a coronavirus phishing attack that can compromise the security of an organization we, fortunately, have solutions to identify such attacks in a much easy way these days, thanks to big tech corporations continuously reminding users before they fall for such a scam. Let’s take look at an example.
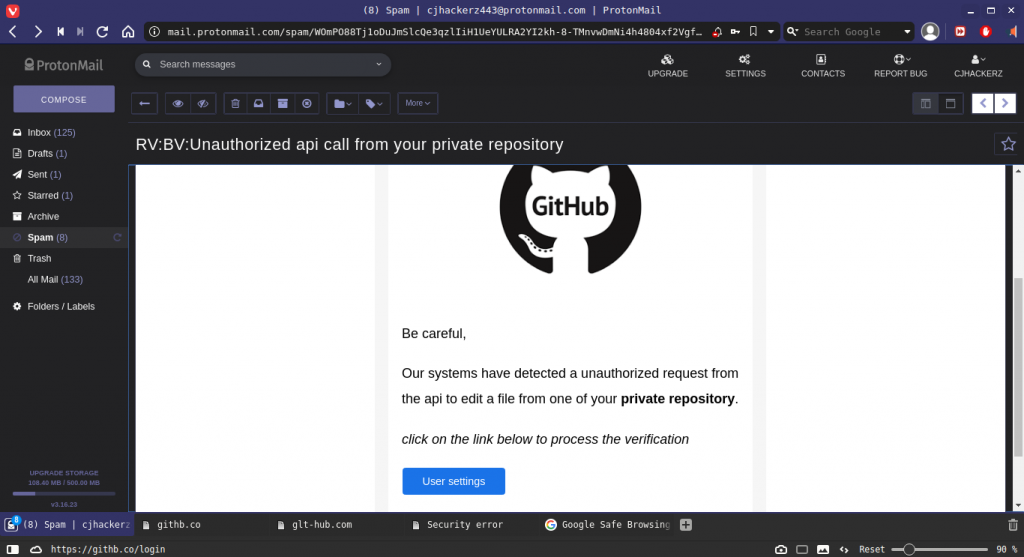
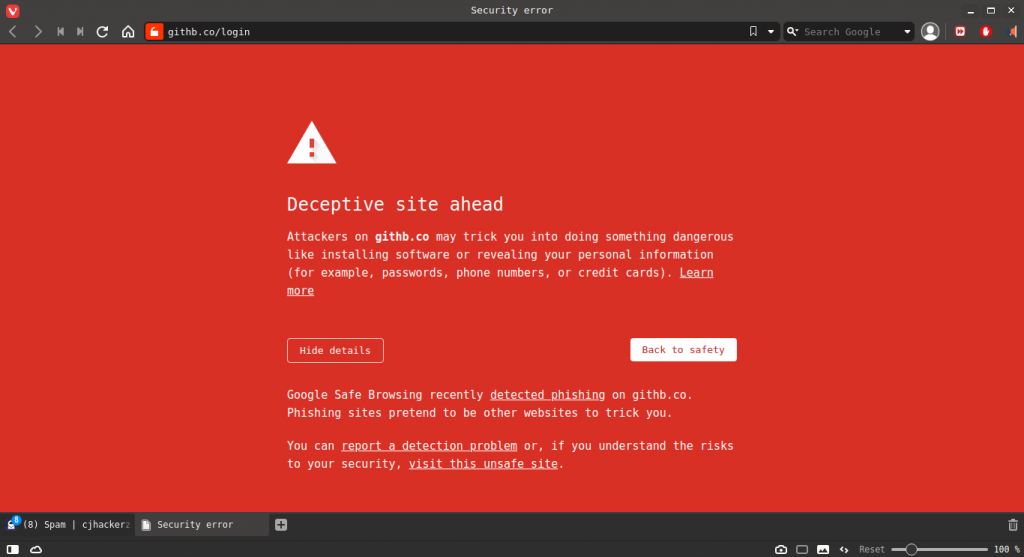
As you can see in the above screenshot this email tries to warn the user about unauthorized access to the private GitHub repository. GitHub is well known among the software development crowd for hosting open-source code via git version control system. Many startups and IT-related businesses maintain their open source products and services with continuous CI/CD DevOps pipeline. But wait it’s not a legitimate email, upon clicking on the user settings button which is supposed to lead you to the original GitHub domain it opens https://githb.co/login and my updated chrome engine based browser (Vivaldi) instantly stops opening it and displays a warning.
Threat actors have now leveled up their game by using HTML and CSS in emails to match with emails from original online service. Some times even they re-use HTML code by the legitimate service’s email notification and modifying some code. For our example, it was a blue-colored user settings button leading to the malicious GitHub domain. Check the snippet of the HTML source code below for a phishing email example.
<p style="-webkit-font-smoothing: antialiased;">
<span style="font-size:20px;">Be careful,</span>
</p>
<p style="-webkit-font-smoothing: antialiased;">
<span style="font-size:20px;">Our systems have detected a unauthorized request from the api to edit a file from one of your
<strong>private repository</strong>.
</span>
</p>
<p style="-webkit-font-smoothing: antialiased;">
<em>
<span style="font-size:20px;">click on the link below to process the verification</span>
</em>
</p>
<table>
<tbody>
<tr>
<td>
<a target="_blank" href="https://githb.co/login" dir="ltr" data- saferedirecturl="https://www.google.com/url? q=https://www.google.com/appserve/mkt/p/AMJ1mut- TokIGDmugcVFvmfjzrGckkSobnQf5YdkqKfe2_NmKBJtqyf6KYykRreJG- 7P0OY8NZ_9QvuiH0SjBiu0gBaTVdQqpdSnY2_-8DW_Nw7xgdMX37tI6I_RTCBjLIeTJOxTvM4Q Lgndmd_Ph-Yx8hWuTibiqgW-PgRAIXepXTVfHtx- 4PMFVxPOXBTPGvu73psH713a89eGjoWnFg&source=gmail&ust=15861444950190 00&usg=AFQjCNEq1D8ZLzHsLZOR5PhhBD1UaLX0OQ"> User settings
</a>
</td>
</tr>
</tbody>
</table>
<p>
<span>Thanks,</span>
<br>
<span>The GltHub Team</span>
</p>
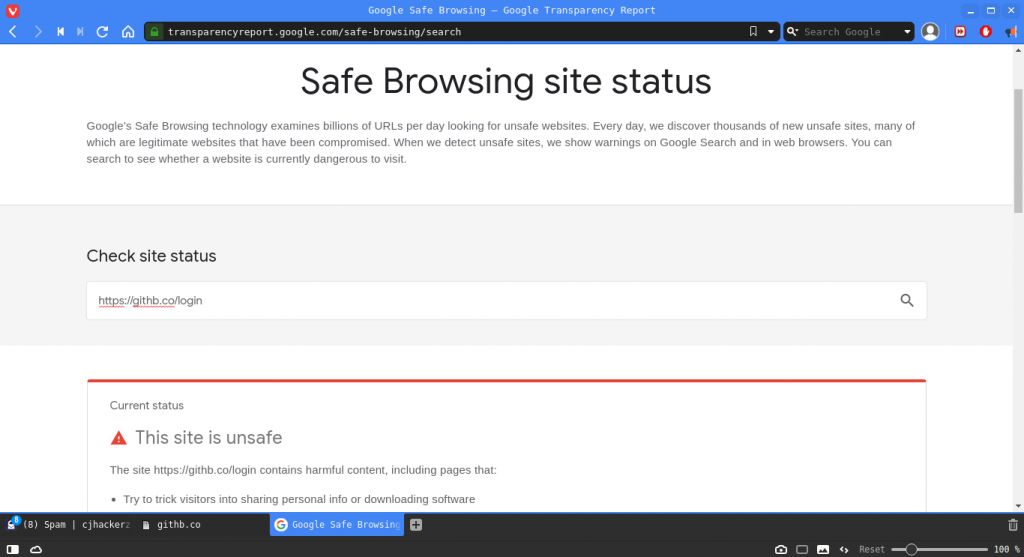
You may wonder how to identify such malicious domains or links in advance. Google is here to save again.
Visit this link: https://transparencyreport.google.com/safe-browsing/search
and in the search box enter the target URL that you are about to visit and wanna check whether it is malicious or not. Google’s Safe Browsing technology analyses millions and billions of URLs per day looking for unsafe websites. Every day, they discover thousands of new unsafe sites, many of which are legitimate websites that have been compromised. When they detect unsafe sites, they show warnings in google search results and also in web browsers.
Also, you can import the following phishing DNS blacklist inside your firewall configuration or use it to search your target domain manually.
https://phishing.army/download/phishing_army_blocklist_extended.txt
Phishing database: https://github.com/mitchellkrogza/Phishing.Database
Also, Gmail uses machine learning and Artificial intelligence to classify such malicious emails and warn users about it.
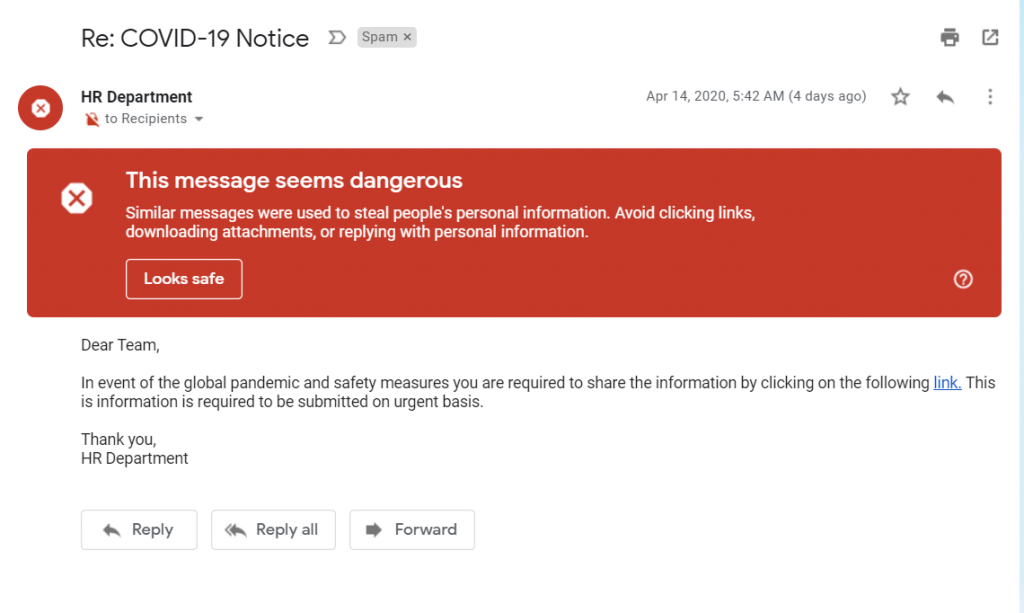
You should consider warnings from your email provider seriously and clicking links without verifying in your spam or junk folder is a slip for your account security. We will see some common patterns below that might be found in typical phishing emails.
- Phishing emails and text messages resemble they are from a company you know or trust.
- It May look like they’re from a bank, a credit card company, a social networking site, an online payment website or known application, or an online store.
- Phishing emails and text messages often tell a deceptive/fake story to trick you into clicking on a link or opening an attachment.
- Some may try to notify false suspicious activity or login attempts
- Claim there is a problem with your account or your payment information
- Saying you must confirm your personal information including a fake invoice and want you to click on a link to make a payment say you’re eligible to register for a government refund and offering a coupon for free stuff.
These are some examples according to the current COVID-19 situation:
- Fabricated notices from health organizations (e.g., The Ministry of Health and Family Welfare or the local health departments)
- Fake updates from an employer about policies or procedures to address the risk
- Websites containing COVID-19 infection maps and dashboards
- Information about protecting yourself, your children or your community that contains malicious links or attachments
- Charitable appeals to help victims of the virus, which are not legitimate
Prevention from Coronavirus phishing attacks
Just like masks, sanitizers and social distancing are solutions for COVID-19, in cyberspace, we have awareness, preparedness, and system software hygiene.
If you are a small company or startup you should focus more on investing individual employee’s education instead of a buying spree of firewalls and anti-virus solutions for internal network and IT infrastructure. Always remember human trust is very vulnerable to deceptive behavior.
Host educational sessions about how phishing works and harmlessly simulate such a scenario. For example, you can ask the project manager to send a fake policy change document, and explain to your employees that such emails can only come from the HR department and always check the source of the email address. Plan out anything that would simulate actual phishing scenario in such way your employee does not feel awkward of their understanding and learn new things from it so next time something similar is encountered they can make a rational decision.
For mid to large-capital companies spending those extra bucks for commercial-grade antivirus and ransomware protection solutions for most of the employee systems will work as an effective backup plan just like health insurance when something goes wrong and you will have enough time to act on it. Blocking advertisements and other irrelevant websites with the help of strong firewall configurations will also help protect up to a degree.
Always keep the operating system and work-related software up to date which reduces the chance for the exploitation of known vulnerabilities that can be leveraged by threat actors for a deeper level of system access. Educate employees to use more and more privacy-focused software in the work environment.
Implement good password management policies and periodically discard old ones.
Conclusion
End of the day it comes down to basic cybersecurity practices understood at a higher point of view by the people in your organization. I am not saying you will be 100% coronavirus phishing proof even after following all steps mentioned above, at least it will prevent you from the worst-case scenarios.


