
Conducting Comprehensive Security Scans With Nessus Explorer
May 2, 2023
7 Best Penetration Testing Service Companies In India
May 5, 2023
In recent years, web applications have become increasingly complex and dynamic, with JavaScript being a widely used language for creating dynamic web content. However, with the growing complexity of JavaScript applications, the risk of security vulnerabilities also increases.
One such vulnerability that has gained attention is “prototype pollution.” In this blog post, we will delve into the details of prototype pollution, how to detect it, its impact, and recommendations to mitigate the risks associated with this vulnerability.
What is Prototype Pollution Vulnerability?
Prototype pollution is a type of security vulnerability that occurs when an attacker can modify the prototype of an object in a JavaScript application, leading to unexpected behavior and potentially allowing the attacker to execute arbitrary code or gain unauthorized access. The prototype of an object is a shared object used as a blueprint to create new objects of the same type. Modifying the prototype allows an attacker to modify the behavior of all objects of that type, which can have far-reaching consequences.
How Prototype Pollution Occurs?
Prototype pollution typically occurs when an application fails to properly validate and sanitize user input used to modify an object’s prototype. This can happen in various ways, such as through user-controlled data that is directly or indirectly used in object creation, property assignment, or function invocation. When the application fails to properly validate and sanitize this user input, it can lead to unintended modifications to the prototype chain, resulting in prototype pollution vulnerabilities.
How to Detect Prototype Pollution?
Detecting prototype pollution vulnerabilities can be challenging, as they may not always manifest as direct errors or obvious behavior changes. However, several techniques can be used to detect prototype pollution vulnerabilities in JavaScript applications:
Code Review:
Review the application’s source code to identify potential areas where user input is used to modify an object’s prototype. Look for functions or methods that perform object creation, property assignment, or function invocation using user-controlled data. Check if proper validation and sanitation measures are in place.
Static Code Analysis:
Use static code analysis tools that can detect potential prototype pollution vulnerabilities by scanning the code for patterns or code constructs commonly associated with prototype pollution. These tools can help identify potential vulnerabilities by analyzing the code for unsafe object manipulation operations that can lead to prototype pollution.
Dynamic Analysis:
Conduct dynamic analysis of the application during runtime to monitor and analyze the behavior of objects and their prototypes. This can involve logging and analyzing object properties and methods during different stages of the application’s execution to identify any unexpected changes to the prototype chain.
Security Testing:
Include prototype pollution testing as part of your application’s security testing efforts, such as penetration testing or vulnerability scanning. Test the application using known attack vectors and payloads commonly associated with prototype pollution vulnerabilities to identify potential vulnerabilities.
Impact of Prototype Pollution
Prototype pollution vulnerability can allow an attacker to gain unauthorized access, execute arbitrary code, tamper with data, or disrupt the normal operation of an application. The impact of prototype pollution depends on the context and functionality of the affected JavaScript code, but it can result in severe security risks. Some of the main impacts of prototype pollution include:
Cross-Site Scripting (XSS):
An attacker can exploit prototype pollution to manipulate the prototype chain and inject malicious code into an object’s prototype. This can lead to the execution of arbitrary JavaScript code in the context of the victim’s browser, leading to XSS attacks.
Vulnerable Code:
Fix:
Exploit Request and Response:
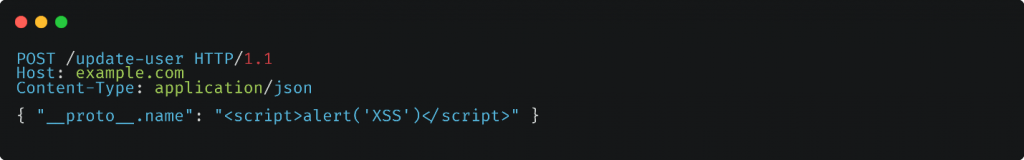
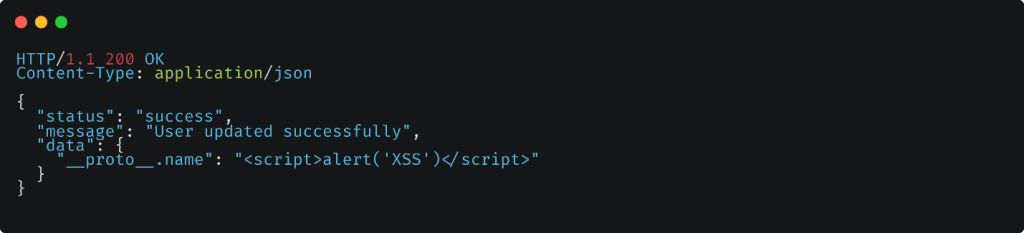
In this example, the attacker sends a POST request to the /update-user endpoint with a payload that includes the __proto__.name property with a value containing a malicious XSS payload. The server processes the request and updates the user with the provided data. As a result, the malicious code <script>alert(‘XSS’)</script> gets stored in the user’s data. It may be displayed or executed in the victim’s browser, leading to an XSS attack.
Remote Code Execution (RCE):
Prototype pollution can also be exploited to execute arbitrary code on the server-side, potentially leading to remote code execution vulnerabilities. For example, an attacker can manipulate the prototype chain to add a malicious function or modify an existing function, which can then be invoked with user-controlled data, leading to remote code execution.
Vulnerable Code:
Fix:
Exploit Request and Response:
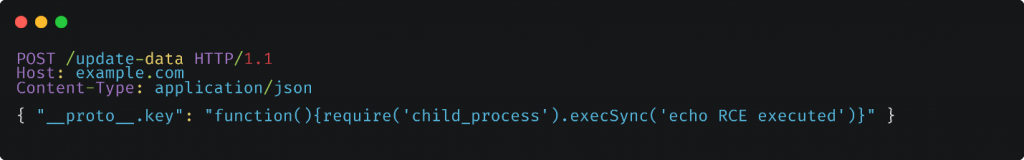
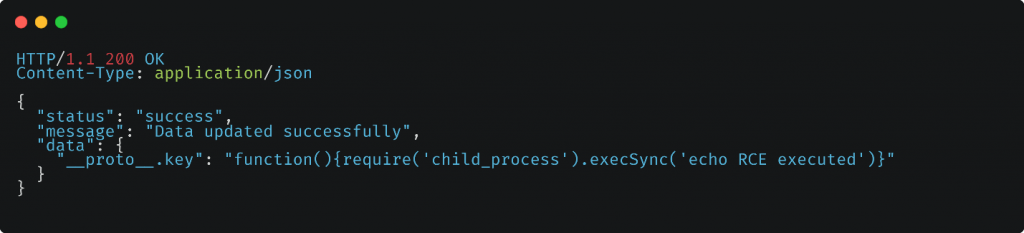
In this example, the attacker sends a POST request to the /update-data endpoint with a payload that includes the __proto__.key property with a value containing malicious code for remote code execution.
The malicious code uses the child_process module, a built-in module in Node.js, to execute the echo RCE executed command. As a result, the command gets executed on the server, leading to remote code execution.
It’s important to note that this is a simplistic example for illustrative purposes, and actual RCE payloads may be more sophisticated and dangerous.
Denial of Service (DoS):
Prototype pollution can be used to disrupt the normal operation of an application by manipulating the prototype chain in a way that leads to unexpected behavior or crashes.
For example, an attacker can create a cyclic prototype chain, causing the application to enter an infinite loop or consume excessive resources, resulting in a denial of service (DoS) attack.
For example, an attacker could manipulate the prototype chain of an object used for processing requests in a web application, causing the application to crash or become unresponsive, resulting in a DoS attack.
Vulnerable Code:
Fix:
Exploit Request and Response:
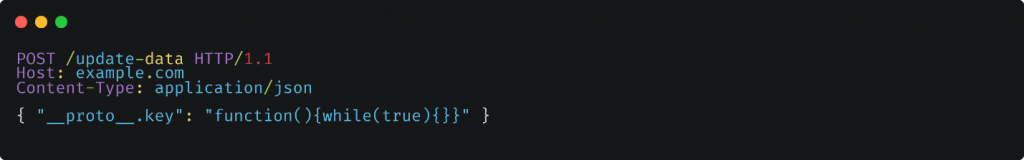
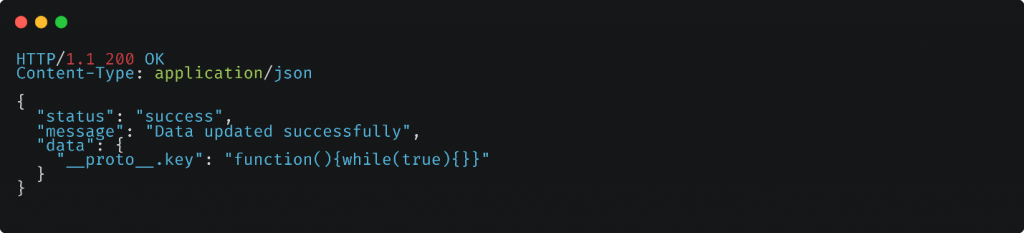
In this example, this example, the attacker sends a POST request to the /update-data endpoint with a payload that includes the __proto__.key property with a value containing an infinite loop while(true){}.
As a result, the server enters an infinite loop, consuming excessive resources and leading to a denial of service (DoS) attack, causing the application to become unresponsive or crash. It’s important to note that DoS attacks can cause disruption to legitimate users and result in loss of service availability, which can have severe consequences for the targeted application and its users.
Data Tampering:
Prototype pollution can also be used to modify data in the application in unintended ways. For example, an attacker can manipulate the prototype chain to modify data objects or change their behavior, leading to data tampering attacks.
This can result in unauthorized modifications to data, leading to data integrity or confidentiality breaches. For example, an attacker could manipulate the prototype chain of an object used for storing user data in a web application, allowing them to modify or delete the data, resulting in data tampering and potential data breaches.
Vulnerable Code:
Fix:
Exploit Request and Response:


In this example, the attacker sends a POST request to the /update-data endpoint with a payload that includes the __proto__.key property with a value of “newValue”. As a result, the value of the data.key property in the application’s data object gets tampered with the unauthorized new value “newValue”, leading to unauthorized modification of data. This can result in data integrity or confidentiality breaches, allowing the attacker to manipulate the data in unintended ways, leading to potential security and privacy risks.
Prototype Pollution Mitigation
To mitigate the risks associated with prototype pollution vulnerabilities, it is essential to follow secure coding practices and implement proper validation and sanitation measures for user input used to modify an object’s prototype. Here are some recommendations to fix prototype pollution vulnerabilities:
Validate and Sanitize User Input:
Always validate and sanitize user input used to modify an object’s prototype. This includes input used in object creation, property assignment, or function invocation. Implement strict validation checks to ensure that user input is of the expected type and does not contain any unexpected or malicious data.
Avoid Modifying Built-in Object Prototypes:
Avoid modifying the prototypes of built-in JavaScript objects, such as Object, Array, String, etc. Modifying these prototypes can have unintended consequences and introduce prototype pollution vulnerabilities. If customization is needed, consider extending these objects with a new object instead of modifying their prototypes directly.
Use Proper Object Creation Techniques:
Use safe object creation techniques, such as Object.create(), Object.assign(), or object literals, instead of using __proto__ to modify the prototype chain. These methods allow for controlled object creation without introducing prototype pollution vulnerabilities.
Sanitize User Input in Libraries and Frameworks:
If you use third-party libraries or frameworks that allow user input to be used in object creation, property assignment, or function invocation, make sure to validate and sanitize the user input according to the library’s documentation and best practices.
Regularly Update and Patch Dependencies:
Prototype pollution vulnerabilities can also arise from dependencies used in your application. Regularly update and patch all dependencies to their latest secure versions to minimize the risk of prototype pollution vulnerabilities.
Implement Content Security Policies (CSP):
Content Security Policies (CSP) can help mitigate the risks of prototype pollution by limiting the execution of JavaScript code from unauthorized sources. Implement CSP headers in your web application to restrict the sources from which JavaScript code can be loaded and executed.
Educate Developers and Testers:
Provide regular training and education to developers and security testers on secure coding practices, including awareness of prototype pollution vulnerabilities and mitigation techniques. Encourage the use of secure coding tools and practices, such as static code analysis, dynamic analysis, and security testing, to identify and fix prototype pollution vulnerabilities.
Conclusion
In conclusion, prototype pollution is a critical security concern in JavaScript applications. Proper measures should be taken to identify, mitigate, and fix these vulnerabilities to ensure the security and integrity of web applications. By following secure coding practices, validating and sanitizing user input, and staying vigilant with updates and patches, developers can effectively protect against prototype pollution attacks and safeguard their applications from potential exploits.