How to Start IoT device Firmware Reverse Engineering?
August 5, 2019
Reading data from EEPROM without desoldering
August 12, 2019
A year ago, when I was fresher in the term of IoT security, I was very curious about the approaches for penetration testing on smart devices. I remember the day when I started approaching a device very first time for penetration testing and resulting in getting the device into pieces.
For any smart device, the Device Hardware and its firmware play a very important role hence here I decided to focus on reversing Hardware as well as It’s firmware parts. For this learning, I started with Sonoff Basic Wi-Fi Switch device.
Let’s understand interesting stuff about the targeted device;
What is Sonoff Wi-Fi Switch?
Sonoff Basic is a device which is mainly used in Home Automation. It is a wi-fi based wireless switch by which the user can control their smart devices. Sonoff transmitted the data over the cloud via Router, which enables the user to remotely control their home appliances

Basic Sonoff specifications :
Power Supply: 90V~250V A
Max. Current: 10A
Wireless Standard: Wi-Fi 2.4GHz b/g/
Security Mechanism: WEP/WPA-PSK/WPA2-PSK
Operating Temp.: 0℃~40℃
Operating Humidity: 5%-95%
Material: ABS
Connector: universal
Analyzing the Device :
When carrying out their security audits is the fact that it’s a necessity to open the device to analyze it and obtain information, such as the firmware or software embedded. So here below given the image which gives a brief of device internal structure:
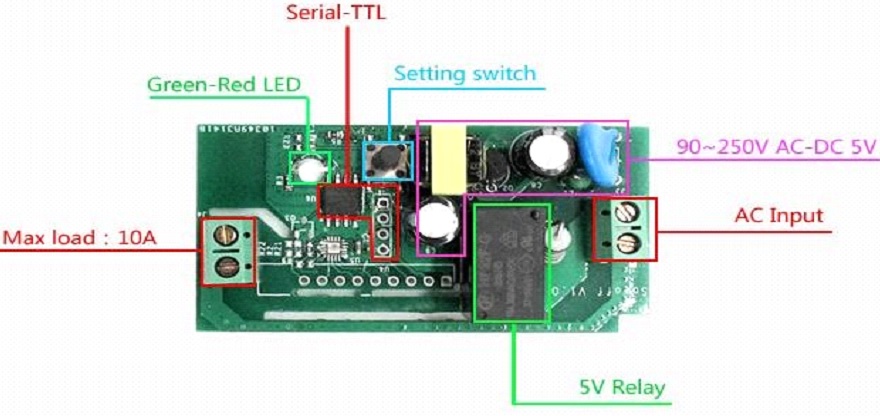
After enumerating the complete hardware parts of the device, including input/output switches, converters, setting switch, one flash chipset LED, etc., I found two interesting things among these other findings
- ESP8266
- UART Ports
ESP8266
ESP8266 offers a complete and self-contained Wi-Fi networking solution, allowing it to either host the application or to offload all Wi-Fi networking functions from another application processor.
Sonoff Basic device works on ESP8266 microchip. Then I decided to dump the memory
Open UART Port
UART stands for Universal Asynchronous Receiver/Transmitter. It’s not a
communication protocol like SPI and I2C, but a physical circuit in a microcontroller, or a standalone IC. A UART’s main purpose is to transmit and receive serial data.
During analysis, I came to know that, the hardware consists of OPEN UART ports which we can use to serially connect to the device.
You can find a brief understanding of the concept of UART pin identification here.
After Identification of UART pins, established the connection of the ports to the USB Converter as follows.
| Device | USB-TTL Converter |
| TX | RX |
| RX | TX |
| VCC | VCC |
| GND | GND |
Steps to be followed:-
For the activate the flash mode of the device
- Press the RESET button and connect the USB converter to Machin/laptop.

- For extracting the memory of the device use esp-tool, which is a very quiet handy tool for ESP8266 to perform the operations like reading, Write, Erase the data from/to the device.
- Use the following command for a dump the flash memory
esptool.py -p /dev/ttyUSB0 -b 115200 read_flash 0 0x400000 flash_contents.bin It will take some time to dump and when it will be done, memory present at the device with Baudrate 115200 will be dumped into flash_contents .bin file. The 0 0x400000 indicates the reading address of memory i.e. up to 4 MB. The address of the port might be change.(in my case it’s /dev/ttyUSB0)
Firmware analysis
So, after using the esptool with help of UART pinouts, I got the actual flash of our device. So here the time to take my very favorite move i.e. binwalk
Binwalk it is a tool to analyze and scan firmware images and binaries, and it quickly shows the different partitions, size, encryption, file system used.
binwalk -e flash_contents. bin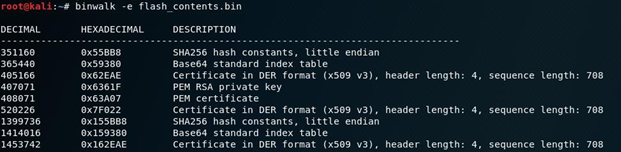
Here I got the above table. It included the columns of Memory addresses with the description.
I moved towards the next command and perform the strings on the binary and here I found the list of all SSID and plaintext Passwords of all previously connected networks.
strings flash_contents.bin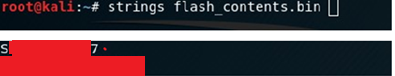
Conclusion:
Most important attack vectors we must consider is hardware vulnerabilities. We must know what critical information can be discovered through hardware penetration testing. Testing conducted on Soloff Wi-Fi-Switch, it concludes that the device does not use any encryption to stores the credentials like Username and passwords of all previously connected Routers.