
How do you set up an Active Directory in Windows
October 28, 2021
Recon: an important part of penetration test for finding vulnerabilities
November 15, 2021
What is Android WebView?
Android WebView, an android system component, allows android apps to load or display content remotely.
Note: It isn’t a full fletched browser: It is just a part of the activity from the application.
For simple definition: WebView is like a simple browser in our application that we can use for browsing web content.
Example:
Facebook application
Verification:
In the Facebook application, we can browse the external web URL as well.
Browser supported protocols.
- http
- https
- ftp
- file
- smtp
What are the possible vulnerabilities that can occur on the WebView Functionality?
- WebView vulnerabilities
- Internal file access
- XSS
- API level attacks
- And more depends on application functionality.
Before diving into WebView we must understand some concepts.
What is Androidmanifest.xml file in the android application?
Every android app must have an AndroidManifest.xml file that describes essential information—components, package name, apps permissions, hardware and software requirement— about the application.
Android Application Components
1. Activities
2. Services
3. Content Provider
4. Broadcast Receiver
5. Intents
Activities:
An activity is a single, focused thing that the user can do. Almost all activities interact with the user.
Example: once you entered your credentials on login page it will redirect you into another activity(page)
<manifest … > <application … > <activity android:name=”.ExampleActivity” /> … </application … > … </manifest >
Services:
In the background, a service can perform long-running operations. It does not need any user interface.
- Foreground
- Background
<manifest … >
…
<application … >
<service android:name=”.ExampleService” />
…
</application>
</manifest>
Broadcast Receivers:
Android apps can send and receive, broadcast messages via the Android system and other Android apps.
Example: Downloaded notification. USB plugin and more.
<receiver android:name=".MyBroadcastReceiver" android:exported="true">
<intent-filter>
<action android:name="android.intent.action.BOOT_COMPLETED"/>
<action android:name="android.intent.action.INPUT_METHOD_CHANGED" />
</intent-filter>
</receiver>
Content Providers:
A provider as part of an Android application often provides its UI for working with the data (files, storage, and cloud)
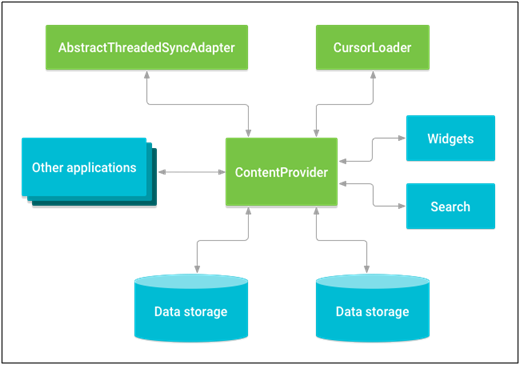
Intent:
Which is help to component interact with each other
- Explicit intent
- Implicit intent
How to find an Android Application is using WebView Functionality or not?
Let us dive into static code analysis.
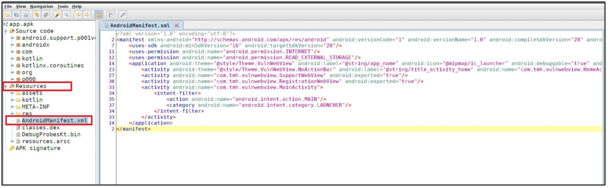
Decompile the app using jadx and Open the manifest.xml file. Then, check application activity.
Step 1: Open the application in jadx
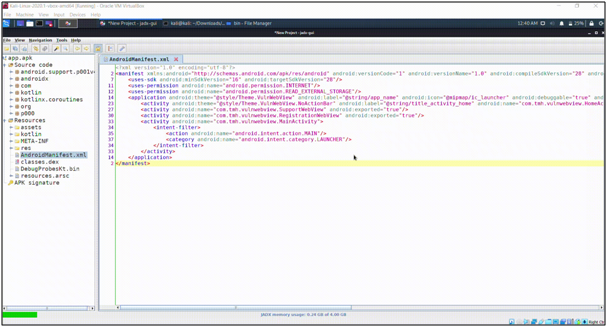
Step 2: Check the manifest.xml
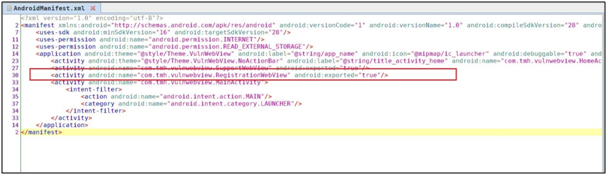
Just check for this Exported Flag is enabled for any activity or not.
“Exported=True”
If the exported attribute has true value. It was exported else attribute had false value it’s not exported.
Support WebView and Registration WebView are explicitly exported; The Main activity is also exported as an intent filter.
Now Navigate to Registration activity.
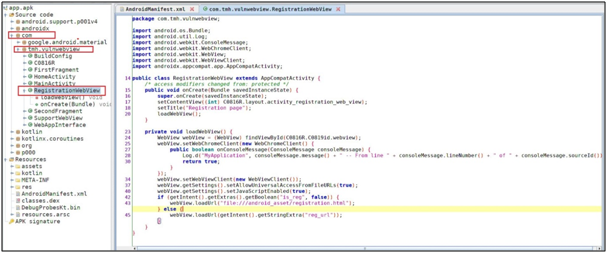
Webview activity – As you can see, the below POC explains how to analyze the code to identify the loadWebView and loadURL function.
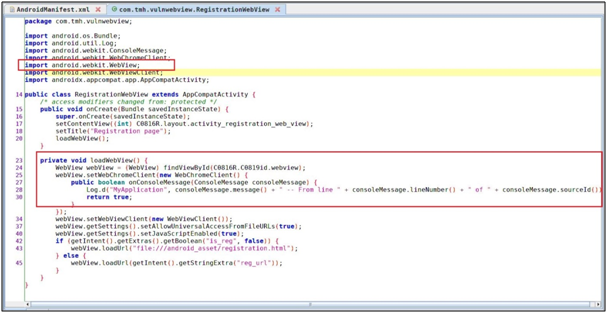
When we are looking to the WebView object closely
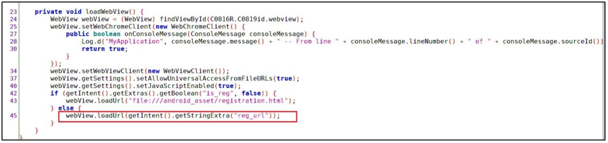
The String send to the intent to load the url(reg_url)
Exploitation Method 01: Exploitation using 3rd Party Apps
This functionality can be exploited by 3rd party applications by sending the intent to the component with a URL application that will accept any URL due to the component which was exported.
ADB is used for this activity, also we can use drozer tool.
Connect our android device using adb

Adb connect 192.168.1.6:5555
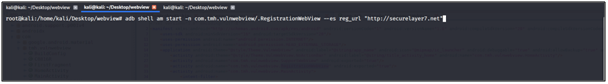
use following command for exploiting webview
adb shell am start –n com.tmh.vulwebview/.RegistrationWebView –es reg_url http://securelayer7.net
shell – will start unix shell on the device.
Am – activity manager
Start – start the activity
-n – name of the compenent
–es – extra string
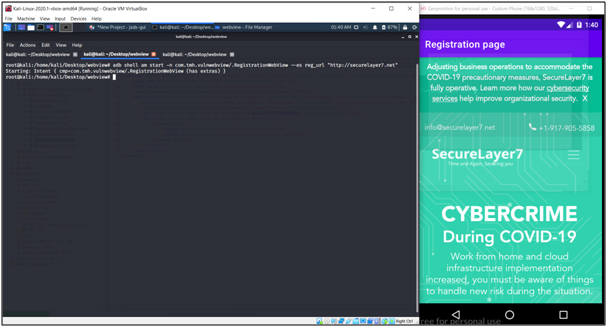
We have sent the intend with securelaye7.net within the context
adb shell am start -n com.tmh.vulnwebview/.RegistrationWebView –es reg_url https://google.com
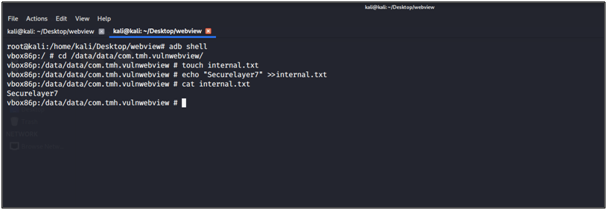
Exploitation Method 02: Read internal file
I have created file called internal.txt inside the directory
adb shell am start -n com.tmh.vulnwebview/.RegistrationWebView –es reg_url “file:///data/data/com.tmh.vulnwebview/internal.txt”
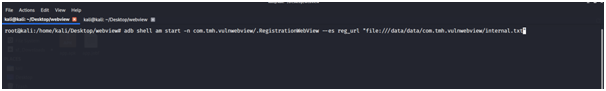
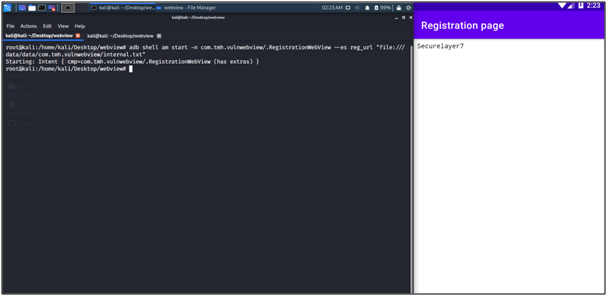
Exploitation Method 03: XSS through WebView
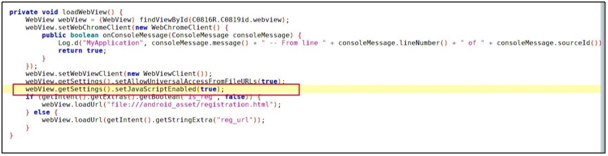
While reviewing the code, we observed that setJavaScriptEnabled(true) method was enabled, which means we can load JavaScript on this WebView.
An attacker might load execute arbitrary JavaScript code on WebView.
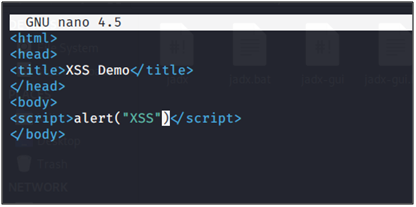
In the below image, we hosted a simple HTML file with an alert box on the python server.
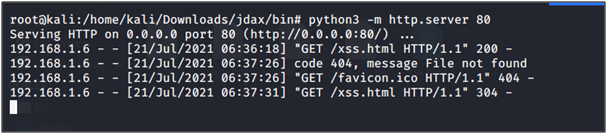
Load the below command over the adb shell.
adb shell am start -n com.tmh.vulnwebview/.RegistrationWebView –es reg_url “http://192.168.1.5/xss.html”
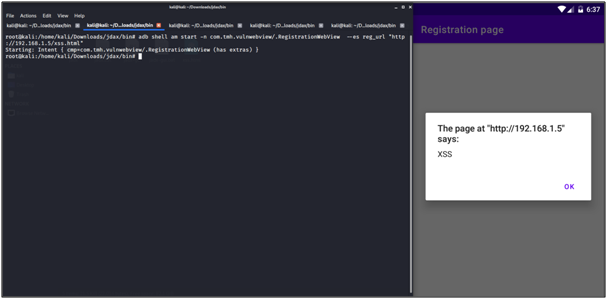
Mitigation:
Validating the origin of the content being loaded by the WebView is a good security precaution. It can be implemented by overriding the shouldOverrideUrlLoading and the shouldInterceptRequest methods.
Avoid following Vulnerable methods when WebView is in place:
- setAllowContentAccess()
- setAllowFileAccess()
- setAllowFileAccessFromFileURLs()
- setAllowUniversalAccessFromFileURLs()
- setJavaScriptEnabled()
- setPluginState()
Reading Local Resource Mitigation:
- WebView not to access sensitive local resources through file scheme:
- Any URI received via an intent from outside a trust boundary should be validated before rendering it with WebView
XSS Mitigation:
- Disable JavaScript if it is not necessary.
Android WebView is useful as it allows you to view links in the apps without leaving them. But you must keep it updated to prevent it from becoming a hacking pathway.


