
Webinar Cyber Security CISO: Strategies of tomorrow’s cybersecurity
June 28, 2021
Cyber Security Webinar 2021 – The Emergence of CyberThreat Evaluation
July 13, 2021
Definition of ‘Cryptography’
“Cryptography is an information security tactic used to protect enterprise information and communication from cyber threats through the use of codes. This refers to secure information and communication techniques derived from algorithms, to convert messages in ways that are hard to decipher. “
Digitalization has led to the growth of digital communication and electronic data exchange, and many of us communicate without giving a second thought about security. Whether we agree or not, our digital footprints are captured and stored somewhere in cyberspace.
Whatever we communicate is often unprotected and open to cybercriminals for manipulation. There is hence a need for us to have a better understanding of cryptographic encryption to find ways to protect sensitive or confidential information. Effective encryption and decryption of data hold the key to security. As such, we need to convert information into an encrypted format so that it can be protected and accessed only by those authorized to do so.
Before beginning let’s have a short brief introduction to cryptography.
Cryptography achieves several information security-related objectives including confidentiality, integrity, authentication, and non-repudiation.
Cryptography, also known as cryptology, thus helps users to cipher and decipher hidden messages into codes, cipher, and numbers so information can be transmitted safely.
The process of coding and transforming plain text into an unreadable format is called encryption, while the process of decoding and converting the unreadable text to readable information using a special digital key is called decryption.
There are three major techniques used to convert the information into encrypted form. They are symmetric, asymmetric, and hashing.
Symmetric Algorithm:-
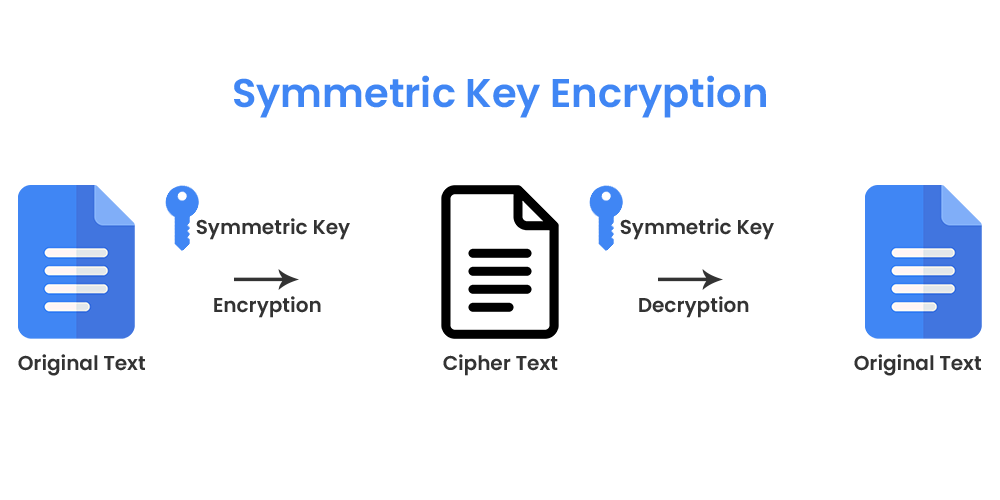
In the symmetric algorithm, both encryption and decryption keys are the same, so the same key must be used to enable secure communication. Symmetric algorithm encryptions are commonly used for bulk data encryption and are fast and easily implemented by hardware. The downside is that anyone with that decryption key can decrypt your data even if not intended.
Asymmetric Algorithm:-
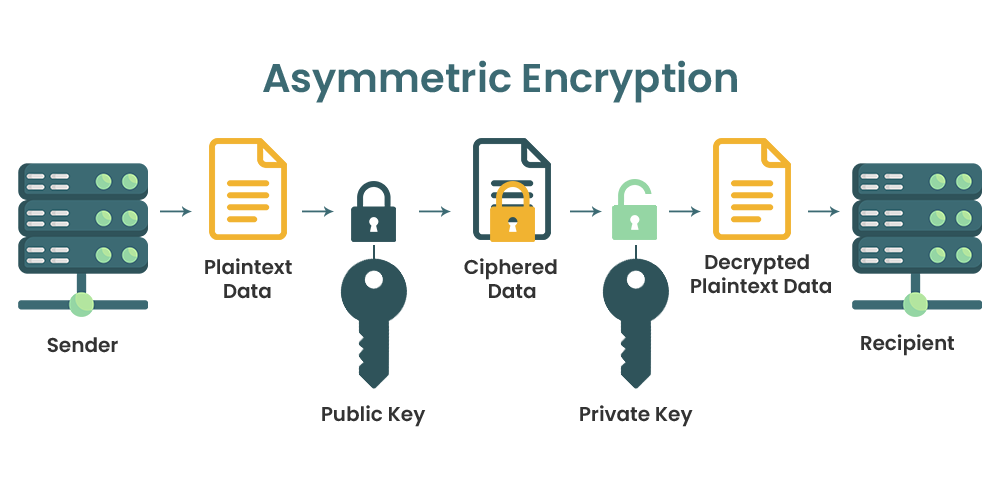
Asymmetric algorithm encryption consists of two separate but mathematically linked encryption keys. A public key is used to encrypt the data and can be distributed while the private key is used to decrypt the data and, therefore, is kept private.
Through the use of a private key, asymmetric encryption eliminates the preliminary exchange of secret keys, allows for public keys to be shared with anyone, and provides an underlying architecture for digital certificates, digital signatures, and a Public Key Infrastructure (PKI). The disadvantages are that it is slower than symmetric algorithm encryption and that it requires greater computation power.
Hashing:-
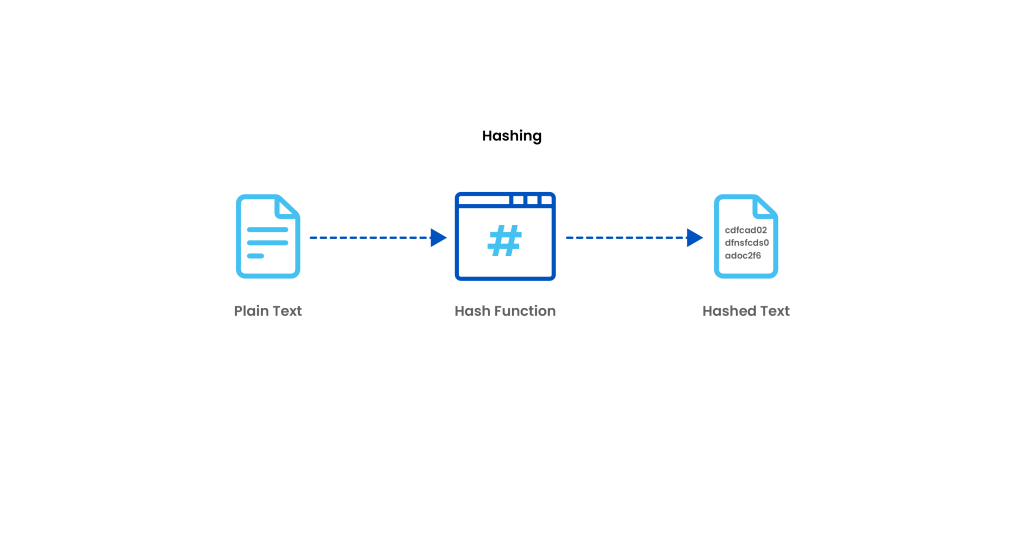
Hashing generates a unique signature of fixed length for a data set or message. Each specific message has its unique hash, making minor changes to the information easily trackable. Data encrypted with hashing cannot be deciphered or reversed back into its original form. That’s why hashing is used only as a method of verifying data.
So, after understanding the fundamentals of cryptography let’s have a look at a few latest cryptography encryption algorithms.
Now, let’s get familiar with some useful and strong algorithms to date.
They are
- Triple DES
- Twofish Encryption Algorithm
- Blowfish Encryption Algorithm
- AES and MD5 Encryption.
It’s not that only these algorithms should only be used but yes they should be preferred first. Let’s have a short and simple description of the Algorithms.
Triple DES
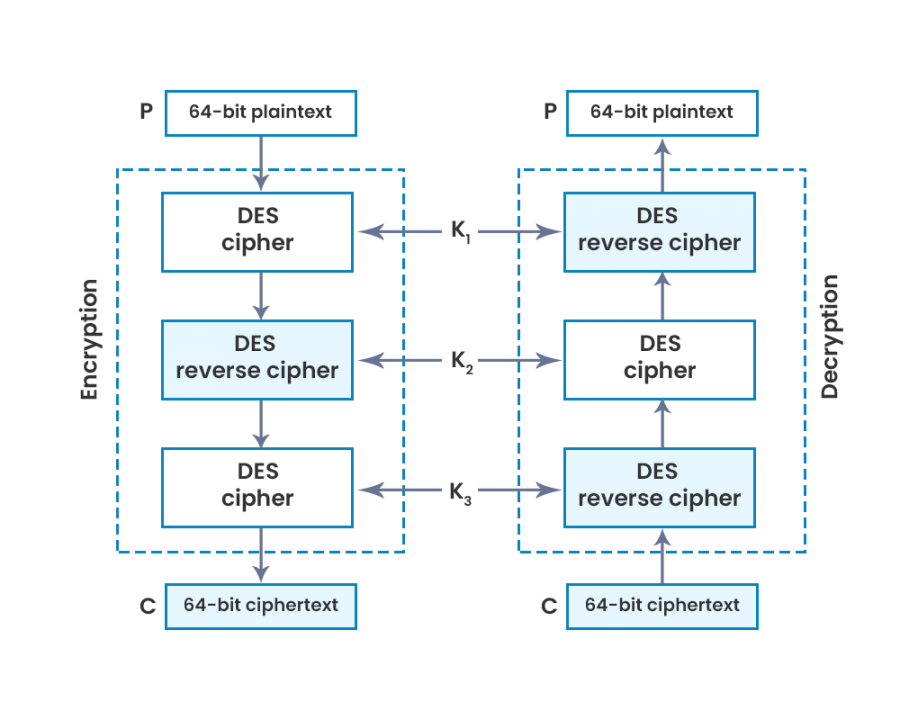
This form of data encryption algorithm applies block cipher algorithms thrice to all the data blocks individually, thrice to each data block. As a result, this process made 3DES much harder to crack than its DES predecessor.
DES converts 64-bit blocks of plaintext data into ciphertext by dividing the block into two separate 32-bit blocks and applying the encryption process to each independently. This involves 16 rounds of various processes — such as expansion, permutation, substitution, or an XOR operation with a round key —that the data will go through as it’s encrypted. Ultimately, 64-bit blocks of encrypted text are produced as the output.
TwoFish Encryption Algorithm
This form of the encryption algorithm is a symmetric key block cipher which is characterized by a 128-bit block size and whose keys’ size can run up to 256 bits. This protocol uses one key for encryption and decryption. It is a fast and flexible standard for eight-bit and thirty-two-bit CPUs, and small smart cards.
First, this cryptography protocol applies substitution boxes, S-boxes that are pre-computed and key-reliant. This implies that despite the provision of the S-box, it relies on the cipher key for the decryption of the encrypted data. The significance of the S-box is to conceal the key connection with the ciphertext. Secondly, the Twofish encryption standard is accepted as a substantially secure alternative.
Encryption protocols whose keys have 128 bits and above are regarded as safe from attacks: Twofish has a block size of 128 bits.
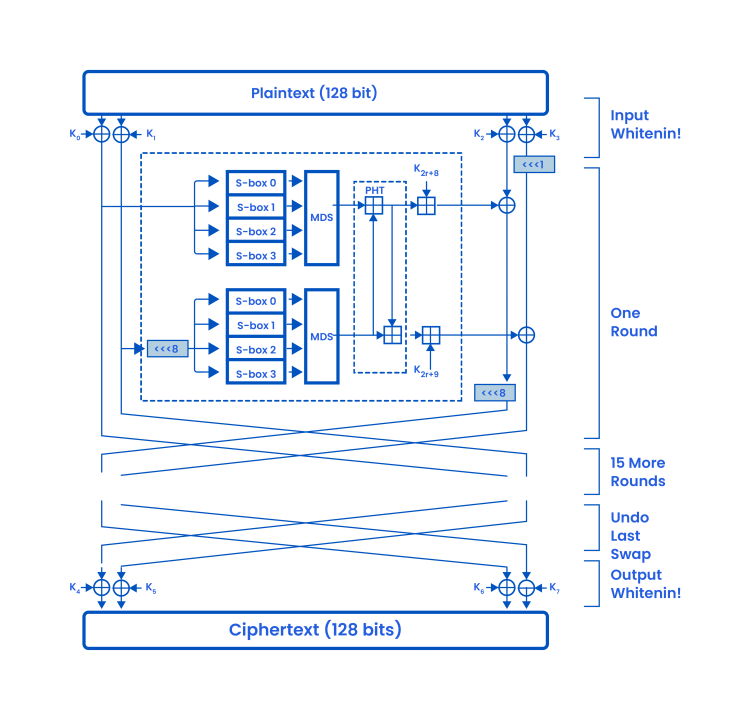
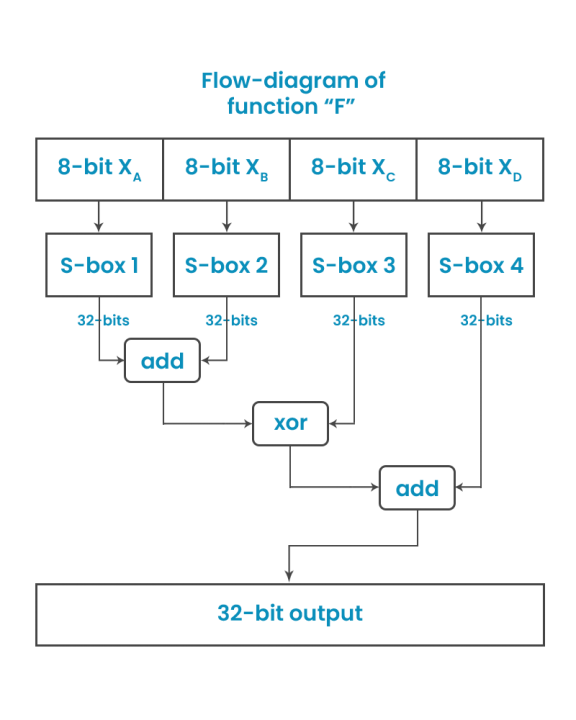
Blowfish Cryptography Encryption Algorithm:-
Blowfish is another algorithm designed to replace DES. This symmetric cipher splits messages into blocks of 64 bits and encrypts them individually.
Blowfish is known for both its tremendous speed and overall effectiveness as many claims that it has never been defeated. Compared to DES, it is substantially faster and offers better encryption security.
Now after looking at the algorithms let’s explore, the few vulnerabilities discovered in the past years. These vulnerabilities are an example of the points we need to take care of.
Starting from:-
- Amazon Music app is vulnerable to serious compromise of private key vulnerability.
Amazon music application used Security through the Obscurity approach by encrypting RSA Private key used to communicate and establish a communication with the amazon music application web server. The purpose of a private key is to keep it private always failing to which the CA needs to revoke the private key.
For more information visit here.
- Weakness in Random Number Generation issue in Yubikeys v4.4.2 -4.4.4
The YubiKey FIPS is FIPS 140-2 certified. The module implements five major functions -Yubico One Time Password (OTP), FIDO Universal 2nd Factor (U2F), PIV-compatible smart card, OpenPGP smart card, and OATH OTP authentication.
For more information visit here.
These are just a few from the bunch. If interested to go through the vulnerabilities then visit Documentation at master · null-open-security-community/Documentation
Summarizing the importance of cryptography encryption of the data is a must and should be encrypted with strong algorithms.


