
What Is Automated Penetration Testing? A Complete Guide
March 29, 2023
Journey to BugDazz 2.0 release
April 3, 2023
As cyber threats continue to evolve, it’s becoming increasingly important for organizations to regularly test the security of their systems and applications.
Penetration testing is one such approach to assess the security posture of your systems. It involves simulating an attack on your systems to identify vulnerabilities that could be exploited by hackers.
However, conducting a successful pen test requires the use of specialized tools that can help you efficiently and accurately identify and exploit vulnerabilities.
In this blog post, we will introduce you to free pen-testing tools that you can use to conduct your pen test. These tools range from network scanners to password crackers, and each one has its own unique strengths and capabilities.
Whether you’re new to pen testing or an experienced professional, this list is designed to help you get started and improve your security testing efforts with penetration testing tools that are free of cost.
We’ll cover each tool in detail, explaining its features and functionality and how it can be used to identify and exploit vulnerabilities.
By the end of this blog post, you should have a solid understanding of the different types of penetration testing tools available and be able to select the best tools for your own pen testing needs.
Free Pentest Tools To Get Started With
Here is the list of the 11 best penetration testing tools used by pen testers.
- Metasploit
- Wireshark
- NMap
- BurpSuite
- Karkinos
- Fiddler
- Sifter
- Nikto
- Commix
- Intruder
- Sqlmap
Let us deep delve into these best free pen-testing tools to have a better understanding of each of them.
1. Metasploit
Metasploit is an open-source penetration testing framework that allows users to develop, test, and execute exploits against a variety of target systems.
The tool provides an extensive library of pre-written exploits and payloads, making it easy for even novice users to get started with their pen testing efforts.
One of the key features of Metasploit is its modular architecture, which allows users to easily create and share their exploits and payloads.
The framework also includes a robust set of auxiliary modules, which can be used to perform tasks such as scanning for vulnerabilities and fingerprinting target systems.
Metasploit also includes features such as automatic exploitation and post-exploitation modules, which can help users quickly and easily gain access to target systems and maintain access once they have compromised them.
Additionally, the framework includes a powerful scripting language, allowing users to automate tasks and customize their testing process to their specific needs.
Overall, Metasploit is a powerful and versatile tool that can be used for a wide range of pen testing tasks. Its extensive library of pre-written exploits, as well as its modular architecture and scripting capabilities, make it an essential tool for many pen testing professionals.
However, it’s important to note that Metasploit should only be used on systems that you have permission to test and that all testing should be conducted ethically and professionally.
2. Wireshark
Wireshark is a popular open-source network protocol analyzer that allows users to capture, analyze, and display network traffic in real-time. The tool supports a wide range of protocols, including TCP/IP, HTTP, DNS, and many others, and can be used to identify security vulnerabilities, troubleshoot network issues, and monitor network activity.
One of the critical features of Wireshark is its ability to capture and display network packets in real time, providing users with detailed information about the contents of each packet, including the source and destination IP addresses, the type of protocol being used, and any data contained within the packet.
Wireshark also includes a range of powerful analysis features, such as packet filtering, deep packet inspection, and protocol decoding, which can be used to identify anomalies and potential security threats within the network traffic.
Additionally, the tool includes a range of customizable display options, allowing users to configure the tool to their specific needs and preferences.
Overall, Wireshark is a versatile and powerful network analysis tool that is widely used by network administrators and security professionals.
Its ability to capture and analyze network traffic in real-time, combined with its advanced analysis features and customizable display options, make it an essential tool for anyone working with network security.
However, it’s important to note that Wireshark should only be used on networks that you have permission to monitor and that all monitoring should be conducted ethically and professionally.
3. NMap
Nmap (Network Mapper) is a free and open-source network scanning and mapping tool that is widely used by network administrators and security professionals.
The tool can be used to discover hosts and services on a network, as well as to identify potential security vulnerabilities and misconfigurations.
Nmap uses a range of scanning techniques, including TCP SYN scans, UDP scans, and OS fingerprinting, to gather information about target hosts and services.
The tool can also perform a range of other tasks, such as version detection, service enumeration, and network topology mapping.
One of the key features of Nmap is its ability to detect potential security vulnerabilities and misconfigurations, such as open ports, unsecured services, and weak authentication mechanisms. The tool includes a wide range of scripts and plugins that can be used to detect these vulnerabilities, as well as to automate certain tasks, such as brute-force password cracking.
Nmap also includes a range of output formats, allowing users to view the results of their scans in a variety of ways, including plain text, XML, and HTML.
Additionally, the tool can be integrated with other security tools, such as Metasploit and Wireshark, to provide a more comprehensive security testing solution.
Overall, Nmap is a powerful and versatile network scanning and mapping tool that is widely used by security professionals. Its ability to detect potential vulnerabilities and misconfigurations, combined with its customizable output options and integration with other security tools, make it an essential tool for anyone working with network security.
However, it’s important to note that Nmap should only be used on networks that you have permission to scan and that all scanning should be conducted ethically and professionally.
4. BurpSuite
Burp Suite is a comprehensive platform for web application security testing. It is a set of tools developed by PortSwigger that can be used to perform security testing of web applications.
The suite comprises several modules, including a proxy server, scanner, and repeater, that can be used to intercept, manipulate, and test the traffic between a web browser and a web server.
Some of the features of Burp Suite include:
- Intercepting and modifying web traffic: Burp Suite’s proxy server allows users to intercept and modify web traffic between a web browser and a web server. This makes it possible to analyze and modify HTTP requests and responses and test the security of web applications.
- Vulnerability scanning: Burp Suite’s scanner module can automatically scan web applications for vulnerabilities, such as SQL injection and cross-site scripting (XSS), and provide detailed reports of any issues that are found.
- Repeater: This feature allows users to repeat specific HTTP requests to test how the server responds. This can be useful for testing the behavior of web applications under different conditions.
- Intruder: The intruder module allows users to automate the process of testing for vulnerabilities, by sending a large number of requests with different payloads to test for issues like SQL injection or XSS.
Burp Suite is widely used by security researchers, web application developers, and penetration testers to identify and exploit vulnerabilities in web applications.
However, it should be noted that using Burp Suite to test web applications without permission can be illegal and unethical, so it should only be used with the proper authorization and within a controlled testing environment.
5. Karkinos
Karkinos is a penetration testing tool that is known for being lightweight and efficient. It offers various security testing capabilities, such as encoding or decoding characters, encrypting or decrypting files and text, and conducting other security tests.
Karkinos is made up of multiple modules that can be combined to carry out a wide range of tests, earning it the nickname of “Swiss Army Knife” for penetration testing.
Some of its key features include the ability to encode or decode characters in different formats, cracking hashes using a built-in wordlist of over 15 million breached or common passwords, and generating popular hashes such as SHA1, SHA256, SHA512, and MD5.
Karkinos is compatible with both Linux and Windows, and it can interact and capture reverse shells, among other features.
6. Fiddler
Fiddler is a free web debugging proxy tool that allows users to monitor, manipulate and debug HTTP(S) traffic between their computer and the internet.
It can be used for a variety of purposes, such as analyzing network traffic, testing web applications, and debugging issues related to web traffic.
Fiddler intercepts web traffic and displays it in an easy-to-read format, allowing users to inspect and modify requests and responses.
It supports various debugging features such as breakpoints, automatic responses, and filters. Users can also create custom rules to modify traffic on the fly.
Fiddler is compatible with multiple platforms and browsers and can be used for desktop and mobile applications.
It is often used by developers, testers, and security professionals to test and debug web applications and APIs, as well as to identify and fix security vulnerabilities such as cross-site scripting (XSS) and SQL injection.
7. Sifter
Sifter is a free and open-source penetration testing and vulnerability scanning tool that is designed to simplify and automate common tasks performed during security assessments. It is written in Python and is compatible with Linux, macOS, and Windows.
Sifter combines a variety of other open-source tools and packages into a single, easy-to-use interface, including Nmap for network scanning,
Nikto for web server scanning and Metasploit for exploiting vulnerabilities. It also includes built-in scripts for common tasks such as password cracking, banner grabbing, and port scanning.
Sifter uses a modular approach, allowing users to select only the modules they need for their particular assessment. This helps to minimize the amount of time and effort required to set up and configure the tool.
Sifter is often used by security professionals, IT administrators, and penetration testers to identify and address vulnerabilities in systems, networks, and applications.
It can be used for both internal and external assessments and is designed to be easy to use, even for users with limited technical expertise.
8. Nikto
Nikto is a popular open-source web server scanner that helps security professionals and system administrators identify security vulnerabilities in web servers and applications.
It is written in Perl and is compatible with multiple operating systems such as Linux, macOS, and Windows.
Nikto conducts a comprehensive scan of the target web server and identifies potential vulnerabilities such as outdated software versions, misconfigured servers, and insecure files and scripts. It also checks for common web server misconfigurations and provides a detailed report of any identified vulnerabilities.
Nikto is highly configurable, allowing users to customize the scan settings according to their specific requirements.
It also supports multiple output formats, including HTML, CSV, and XML, which can be used to generate detailed reports.
Nikto is often used by penetration testers, security auditors, and system administrators to identify vulnerabilities and ensure that web servers and applications are properly secured.
It is a powerful tool that can help identify critical security flaws that could potentially be exploited by attackers.
However, it is important to use Nikto responsibly and only with the permission of the relevant system owners or stakeholders.
9. Commix
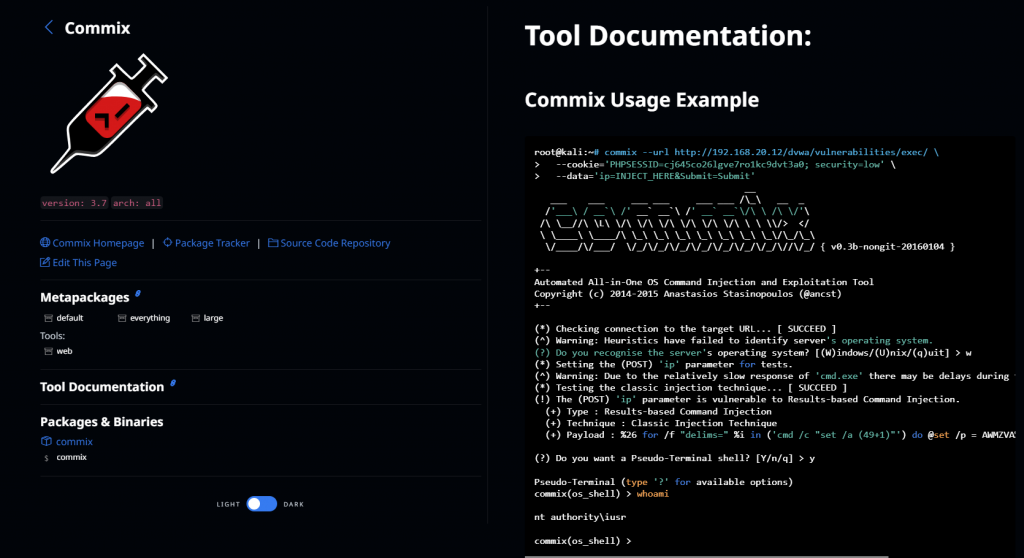
Commix is a command-line tool designed to identify and exploit web application vulnerabilities by performing various injection attacks. It is written in Python and is compatible with Linux and Windows operating systems.
Commix is capable of detecting and exploiting various injection vulnerabilities, such as SQL injection, cross-site scripting (XSS), and command injection. It can be used to test both GET and POST requests, as well as HTTP headers.
Commix is highly configurable, allowing users to customize the tool’s behavior based on their specific requirements. It supports various options and flags that can be used to specify injection points, payloads, and other parameters.
Commix is often used by penetration testers and security professionals to identify and exploit web application vulnerabilities.
However, it is important to use Commix responsibly and only with the permission of the relevant system owners or stakeholders. Improper use of the tool can result in serious security breaches and legal consequences.
10. Intruder
The intruder is a cloud-based vulnerability scanner and security testing platform designed for web applications and APIs.
It is designed to help security professionals identify and address vulnerabilities in their web applications quickly and efficiently.
Intruder offers a range of automated security tests, including web application scanning, vulnerability scanning, and penetration testing.
It also provides customizable security tests, allowing users to create their security tests based on their specific requirements.
The intruder is highly configurable, allowing users to customize the tool’s behavior based on their specific requirements.
It provides a comprehensive dashboard that displays a summary of all identified vulnerabilities and their severity levels. It also supports integrations with various third-party tools, such as Jira and Slack, to help streamline the vulnerability management process.
The intruder is often used by security professionals and penetration testers to identify and address vulnerabilities in web applications and APIs.
It is designed to be easy to use, even for users with limited technical expertise, and provides a range of features to help streamline the vulnerability management process.
However, it is important to use Intruder responsibly and only with the permission of the relevant system owners or stakeholders.
11. Sqlmap
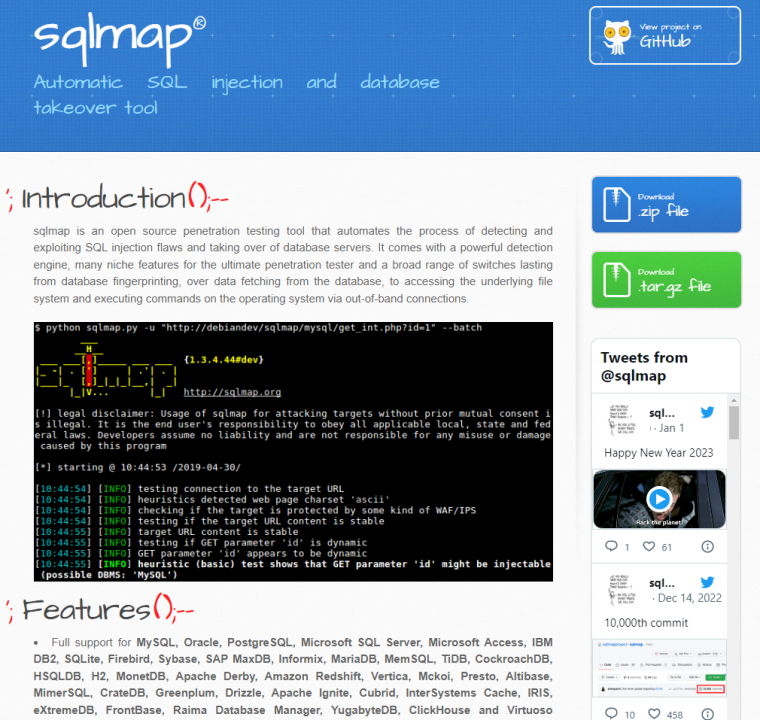
Sqlmap is an open-source penetration testing tool that automates the process of detecting and exploiting SQL injection vulnerabilities in web applications. It is written in Python and is compatible with Linux, macOS, and Windows operating systems.
Sqlmap is capable of identifying and exploiting various SQL injection vulnerabilities, including blind SQL injection, time-based SQL injection, and error-based SQL injection.
It also supports various database management systems, including MySQL, PostgreSQL, Microsoft SQL Server, and Oracle.
Sqlmap is highly configurable, allowing users to customize the tool’s behavior based on their specific requirements.
It provides a range of options and flags that can be used to specify the target URL, payload, and other parameters. It also supports various output formats, including HTML, XML, and JSON, which can be used to generate detailed reports.
Sqlmap is often used by penetration testers and security professionals to identify and exploit SQL injection vulnerabilities in web applications.
However, it is important to use Sqlmap responsibly and only with the permission of the relevant system owners or stakeholders. Improper use of the tool can result in serious security breaches and legal consequences.
Get Comprehensive Coverage With Proven Penetration Testing Services With SL7
Looking for comprehensive penetration testing services that provide proven results? Look no further than SL7, a leading provider of cutting-edge cybersecurity solutions.
Our penetration testing services are designed to identify vulnerabilities in your network, applications, and infrastructure, so you can take steps to strengthen your security posture and protect your assets from cyber threats.
Our team of experienced security professionals uses the latest tools and techniques to conduct comprehensive penetration testing that covers all aspects of your security environment.
We provide detailed reports that identify vulnerabilities and offer recommendations for remediation, helping you to prioritize your security efforts and maximize your investment in cybersecurity.
At SL7, we understand the importance of protecting your business from cyber threats, and we’re committed to providing the highest quality penetration testing services to help you achieve that goal.
Contact us today to learn more about how our services can help you enhance your security posture and protect your assets from cyber attacks.


