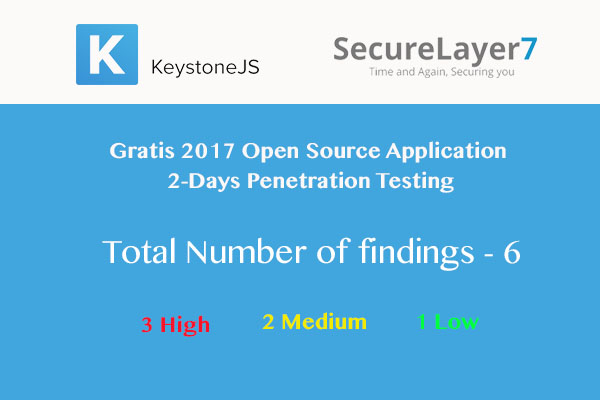
KeystoneJS Open Source Penetration Testing Report – Gratis 2017
October 24, 2017Gain Root without Password- macOS Sierra
December 1, 2017
Hi Readers, in the field of penetration testing, we all know attacks such as Clickjacking, Cross Site Scripting etc. These are attacks from most OWASP Top 10 test cases.
Today we will look into some advanced attack vectors which have been lately around sometime but not all are aware of.
Pastejacking. The art of changing what you copy from web pages.
What is pastejacking?
• Pastejacking is a method that malicious websites employ to take control of your computers’ clipboard and change its content to something harmful without your knowledge.
• This feature can allow malicious websites to take over your computers’ clipboard.
• When you copy something and paste it to your clipboard, the website can run one or more commands using your browser.
• The method can be used to change the Clipboard contents.
• If you paste something directly to the Terminals!? Result: Lethal Commands Executed
To avoid paste jacking:
• Windows users need to check what is placed into your computers’ clipboard.
• Paste the contents into the Notepad. It pastes clipboard as text only and lets you see what is there in the clipboard.
• Result: An additional step to prevent getting Pastejacked.
Attack scenario:
Here we have a sample page which shows a text: “who am i?” as bait for copying. Once this text is selected, it will automatically get replaced in the clipboard with echo ” I @// H4k3r” .
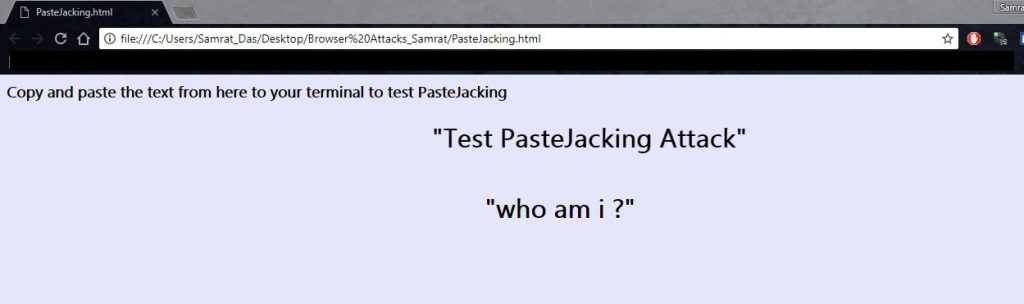
PasteJacking Page
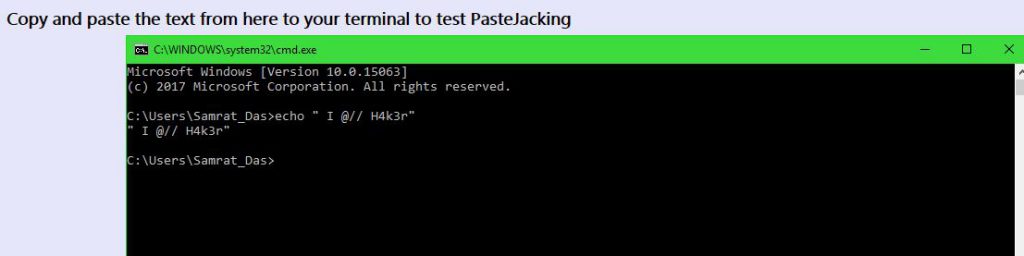
Output on console of pastejacking
What is XSSJacking
XSS jacking is yet another attack which chains together three different attacks: It combines Clickjacking, Pastejacking, and Self-XSS.
For those who may not be aware, here’s a quick intro :
- Self-XSS is a type of XSS that typically can only be triggered by a user typing in an XSS payload which triggers on themselves. This can be DOM based, or set in a field only settable and viewable by the one user.
- Clickjacking, is an attack that frames a website of a logged in user, typically sets the opacity of the frame to 0, and forces a victim to interact with their account, on a different website, unknown to them.
- Pastejacking is the secret adding of malicious text at the end of copy-pasted data ( as seen above)
Practical scenario how it can be exploited:
- You’re a malicious hacker and you set up a messaging forum to interact with users.
- In the forum registration page, you place an “Enter your name” field and a “Reenter your name” field.
- You place a hidden iframe on top of the “Reenter your name” field, where you load a form field from a Innocent page.
- When a user wants to register on your forum, he’ll write his name, and most likely copy-paste it in the second field.
- The malicious website will append the malicious code after his copy-pasted text and insert it into his The innocent Website
- Attack possibilities:
- The innocent website being vulnerable to XSS flaws via its form fields, the attack code can perform malicious actions, and the victim account can get compromised.
- Impact: XSSJacking attacks can dump cookies, steal user data
Attack scenario:
Here in first screen shot we can see, a page with two simple text fields, enter your name and enter your name again.
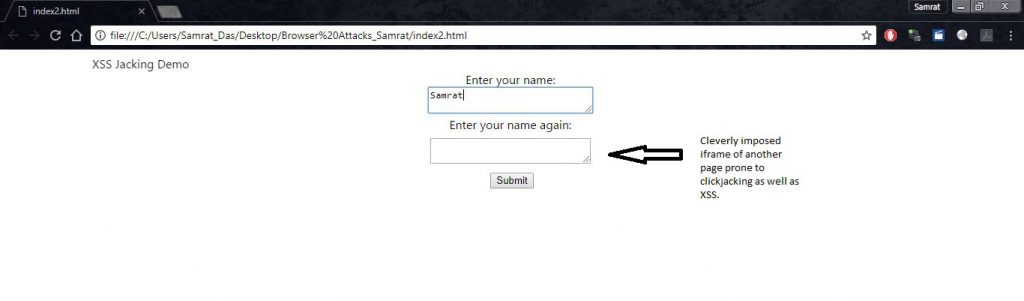
XSS Jacking Step 1
As to be expected a user will type his name first and then use the copy paste function for the second field. The moment he does so the xss alert will be triggered as an abuse of pastejacking method. The victim unknowingly ended up executing the self-XSS in the second field upon which the clickjacking exploit code was set.
So three attacks got executed in a jiffy!
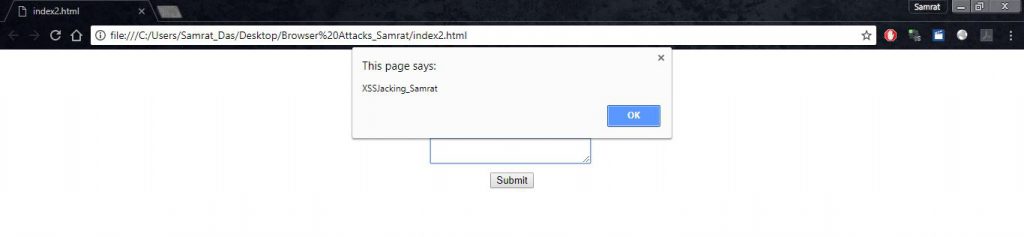
XSS Jacking Step 2
Output page.
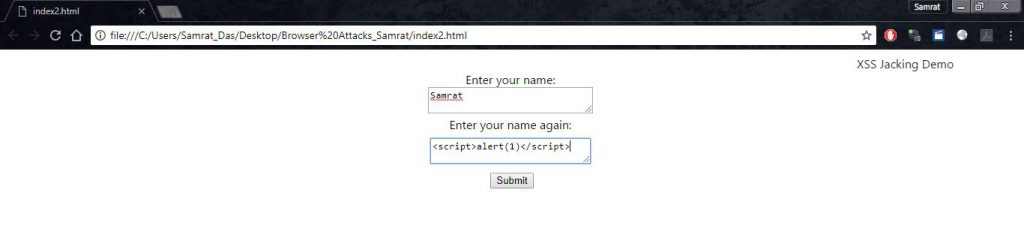
XSS Jacking 3
Result: The above two exploits are not really something having a patch!
Since it’s a mix of luck, feasibility and social engineering attacks, needing user intervention, make sure whenever you copy some content from unknown sites, its safe to first copy the content and paste it into a harmless place such as notepad to see what the content in the clipboard is.
References:
The above code for web pages is modified with a shortened form from the original sources of:
• https://github.com/dxa4481/Pastejacking
• https://github.com/dxa4481/XSSJacking
Note: The above article has also been published in Hakin9 https://hakin9.org/download/burp-suite-compendium/


