How to fix CVE-2015-7547 glibc: getaddrinfo stack-based buffer overflow
February 25, 2016Backdoor PHP code WordPress
April 21, 2016
Presently, I am working on the Windows application for finding security flaws in the application. When I kick-started the application testing, I didn’t find any good resource for the Windows application penetration testing. So this is the blog for those who are looking for getting the right starting point in windows application penetration.
To begin with Windows application phone penetration testing, we first need to start with unlocking the windows phone.
Before getting started with Windows application penetration testing, let us have a look at the following prerequisites:
- Lumia 520 unlocked
- Windows VM or Primary Win OS
- DLL RE tools
- Windows Phone Internal
Lets get started with Lumia 520 phone unlock
Next, for unlocking windows phone we use Windows Phone Internals 1.2 tool from Windows Internals. This tool basically helps to unlock the phone and get root access enabling us to access the root file system. Kudos to XDA forum!!
The detailed steps have been given in the Getting Started section of the tool. You can also find your Windows mobile phone version in that section. Accordingly, it will be helpful to understand, whether we can unlock the phone.
Once the process starts with unlocking of the phone, the bootloader gets our direct access to the flash memory. This unlocks the bootloader, thus enabling the administrator access.
Woot! Once you have administrator access to the phone, the first step is to disable all ACL, capability and privilege checks.
It also allows the threads to escape the sandboxing and, most interestingly, it unlocks the device which allows side loading of homebrew applications.
Alright, now that you have your unlocked phone, what is the next step? Next, we need to have access to the complete file system of the phone, for the purpose of which, you will need to enter into the flash-mood. When you enter with flash-mood, this tool will help you to access the complete file system of the mobile.
Once you have complete access to the file system, all you need to do is to find the application data in the phone storage.
What is XAP ?
The Windows application files have an extension called XAP. As a matter of fact, this application is protected and stored on the Microsoft servers with digital right management, is what I believe.
There are two ways to download / access windows application files, as mentioned below:
- Download Windows Phone Apps from 3rd party (I would not recommend any 3rd part application downloader)
- Downloading Application data from the Phone
There is protection in the Windows phone for the application, one of the protection examples is Security Policy.
During my Windows Application penetration testing research, I recognized a trick which allows me to access the XAP file from Phone storage. Following is the process to dump the XAP file from the Windows Phone:
- Selecting Manual Mode
- Switching to Mass-Storage Mode
Once you perform the above steps, you will find the all the files in the Phone.
As a result of Switching to Mass-Storage mode, we get access to the file system.
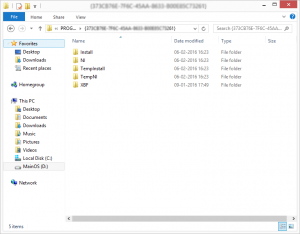
So now let’s try to find the target application folder. The Path Syntax is mentioned below:
So, now you will have to browse all the directories for finding the target application. I have written a script to find the application folder, WMAppManifest.xml. I will share it soon on the SecureLayer7 Github account.
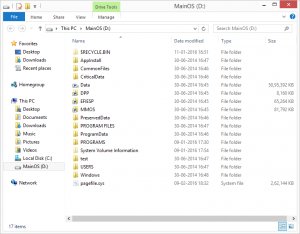
A brief overview of the directory structure:
- Temp
- PlatformData
- Roaming
- Framework Temp
- INetCache
- INetCookies
- INetHistory
- Local Storage
If you look at above directory structure as a pentester, the TEMP and Local Storage folders seem to be interesting. Mostly all the applications store their files in the temp and local storage, which might be important files of the application.
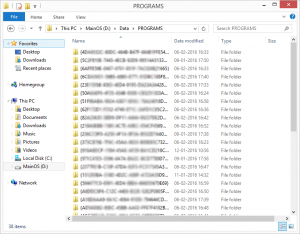
For instance, an example of directories from the target application can be seen below:
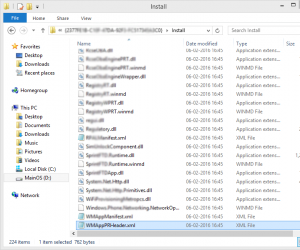
Now, we will have to dump the files from the directory by copying them to your local system for further analysis. This is where the interesting part begins!!
In the phone directory, you will find the WMAppManifest.xml. This file is one of the important parts of the application, which provides the IPC mechanism to the applications. Also, this file mentions what native code is used by the application.
Example of WMAppManifest.XML:
<Deployment xmlns=”http://schemas.microsoft.com/windowsphone/2009/deployment” AppPlatformVersion=”7.1″>
<App xmlns=”” Title=”BANK” RuntimeType=”Silverlight” Version=”1.2.8″ Description=”Sample description” BitsPerPixel=”32″ ProductID=”{174t3210-j331-245y-64vc-12222452d32a}” Genre=”apps.normal” IsBeta=”false” Author=”Bank Application” Publisher=”Bank Application”>
Alright, now that we have all the Windows application files with us, what should be our next step?
De-compiling application files
Windows application is typically developed using .NET framework by writing C# assemblies and C++/WinRT executable. So we do have following reverse engineering tools with us.
- ILSpy
- JustDecompile from Telerik
- .Net Reflector
- IDA Pro
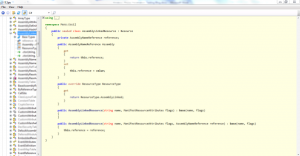
Now, in this example, I’m using the ILSpy application to reverse the target application. In the following image, you can find the reversed code.
How will it be useful for the further research ? When I was performing pentest on a windows application I tried to find the following:
- Authentication tokens
- Account credentials
- Any data revealing users sensitive information
- Weak Encryption standards
- Hardcoded keys
The above checklist is just an example checklist, which I felt can be shared with my blog readers.
Takeaway from this post:
- How to unlock the windows application
- Obfuscating the application.
In the next blog post, I’m preparing to cover Web Browser Control, SQL Injection, XAML Injection, Javascript Bridge Security , Push notification, Application Logging, Registry access, File System Access.
Special thanks to XDA forums for sharing the resources on the windows phone.
References
-
Interop Unlock For WP8 by GoodDayToDie: http://forum.xda-developers.com/showthread.php?t=2435697