OWASP Top 10 : Cross-Site Scripting #3 Bad JavaScript Imports
August 28, 2017Pacemakers prone to getting hacked
September 5, 2017
Hi Readers,
This article is about Burp Suite Macros which helps us in automating efforts of manual input payload fuzzing.
While it may be known to many testers, this article is written for those who are yet to harness the power of burp suite’s macro automation.
In my penetration testing career so far, while performing fuzzing of parameters and page fields in web applications, I did encounter some challenges relating to session handling.
In multiple cases, the application used to terminate the session being used for testing, this either happened due to some security countermeasures ( for example: getting unsafe input, the session used to get logged out) or in other cases, the say the burp spider/ crawler used to fuzz the logout page parameters and terminate the session.
In such cases, further scans, probes and requests becomes unproductive. Since you have to perform a re login and establish the session of the application.
I used to do this manually and it was a bit of cumbersome. While trying to find a workaround, I was going through the Burp Suite functions and based on my curiosity, I noticed Burp’s session handling functionality.
After probing around the options, I came to the idea backed by some on line research that Burp takes care of the above challenges with some rule based macros.
In simple words, say if fuzzing parameters leads to termination of session, Burp can auto login the app with the credentials, and continue scanning and crawling itself.
Things needed:
1 I used burp’s free version (1.7.21 free)
2 Any website which has session handling ( I am showing using the classic demo.testfire.net)
Step 1:
This is the website I am showing which has a login feature:
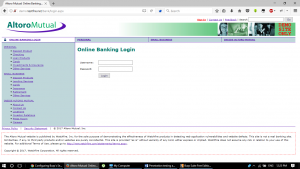
Vulnerable Website
Step 2:
At this point, I am simply keeping the interception off in burp suite and putting the credentials here to perform a login.
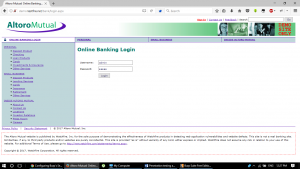
Login Page
Step 3:
Here we enter the logged in page of the website:
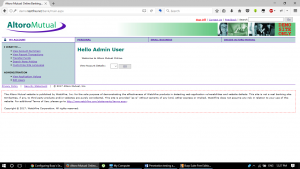
Login field values
Step 4:
Now in order to test the session handling, we can send this page request to burp’s repeater tab and by removing the cookies have a look if the session is terminated due to session breaking.
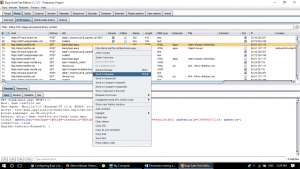
Request using repeater
Step 5:
We can see that the page session is working since we have a proper session. Let’s try to remove the cookies and test again
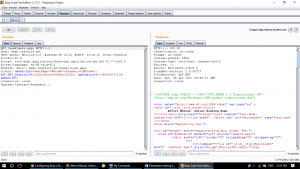
Repeater Tab
Step 6:
As we can see, the session gets logged out and we need to login back again to continue testing.
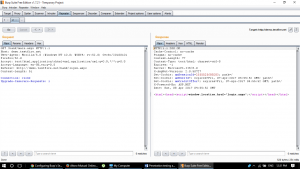
Session Terminated
Step 7:
Now comes to the rescue- Burp Macros.
Navigate to : Project Options -> Sessions -> Session Handling Rules
Setting up Macro
Step 8:
Here we can see that there is a default rule – Use cookies from Burp’s cookie jar.
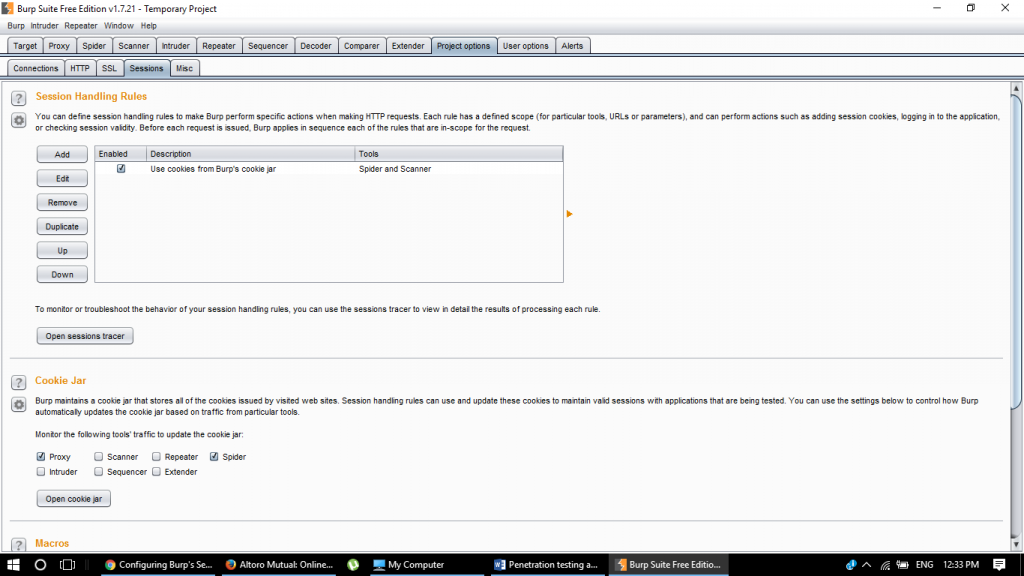
Burp Cookie Jar
Step 9:
Click add button to create a new rule.
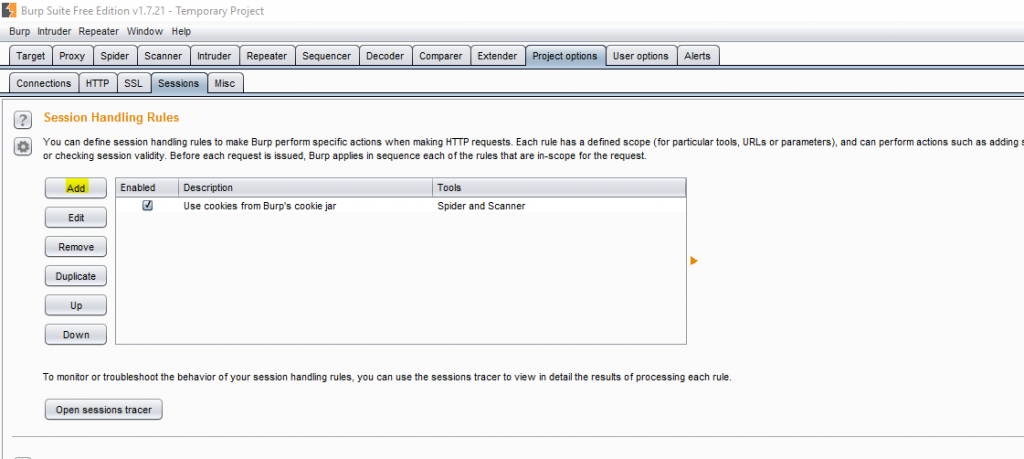
Adding rule for macro
Step 10:
Put a rule description which suits you and under rule actions, select “Check session is valid”
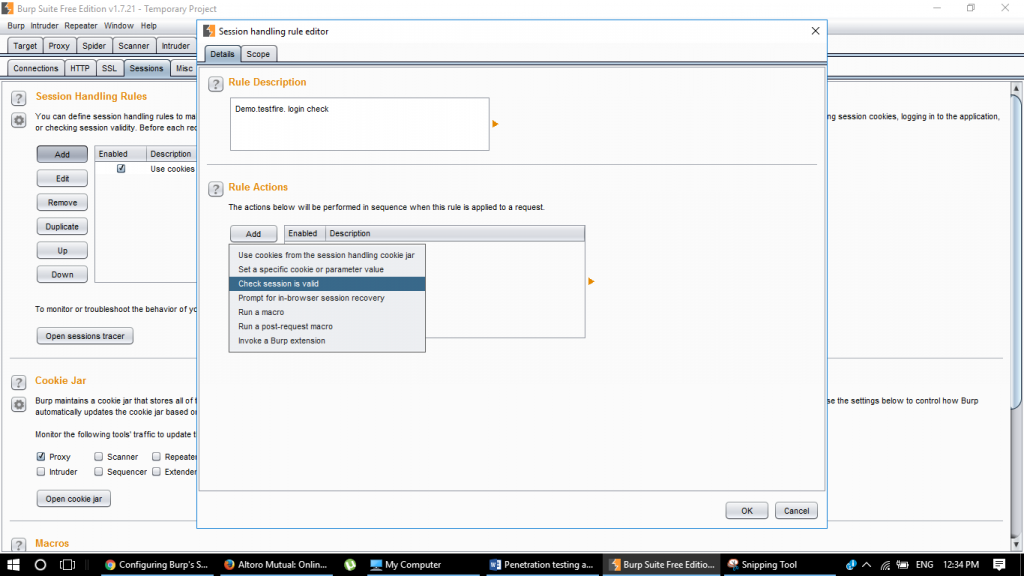
Setting burp rule description
Step 11:
Once you click OK, the session handling editor will fire up which will show the default: Issue current request. Leave as it is and scroll down to “if session is invalid, perform the following action”
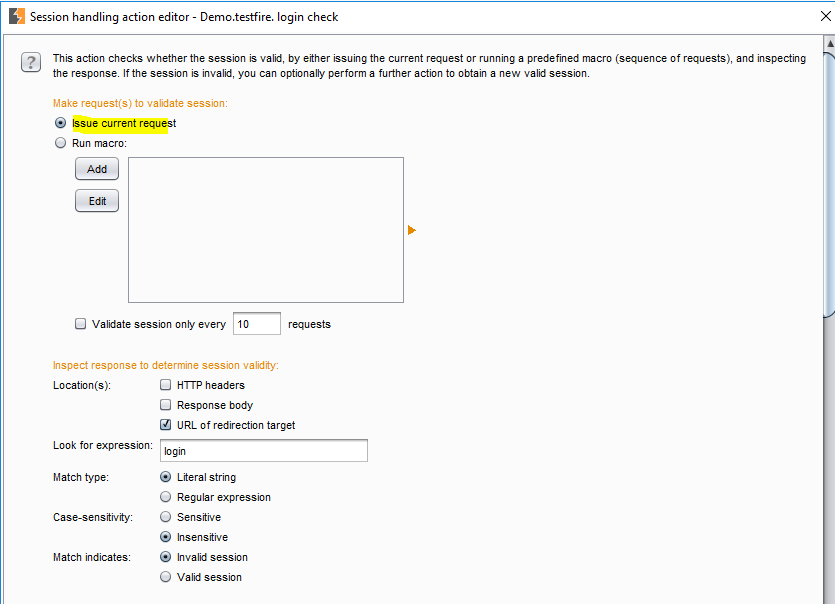
Rule Configuration
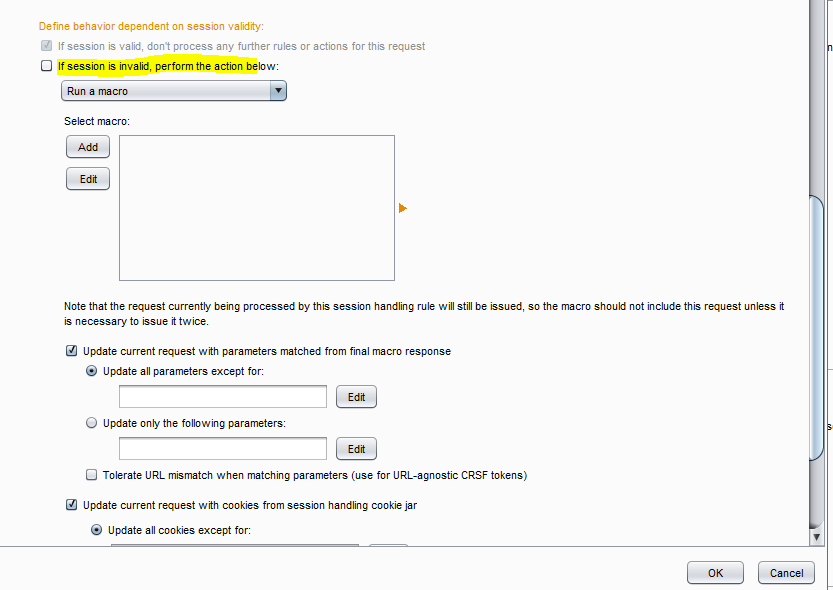
Rule Configuration Setting
Step 12:
Tick the if session invalid and click on add macro. At this point, you will get a Macro Recorder which has all the proxy history. Click and select the page which has the login credentials and performs a login. Click ok
Step 13:
Once you click ok, the Macro editor will fire up and you can name it with a custom name, as well as have options to simulate the macro, re-record, re-analyze.
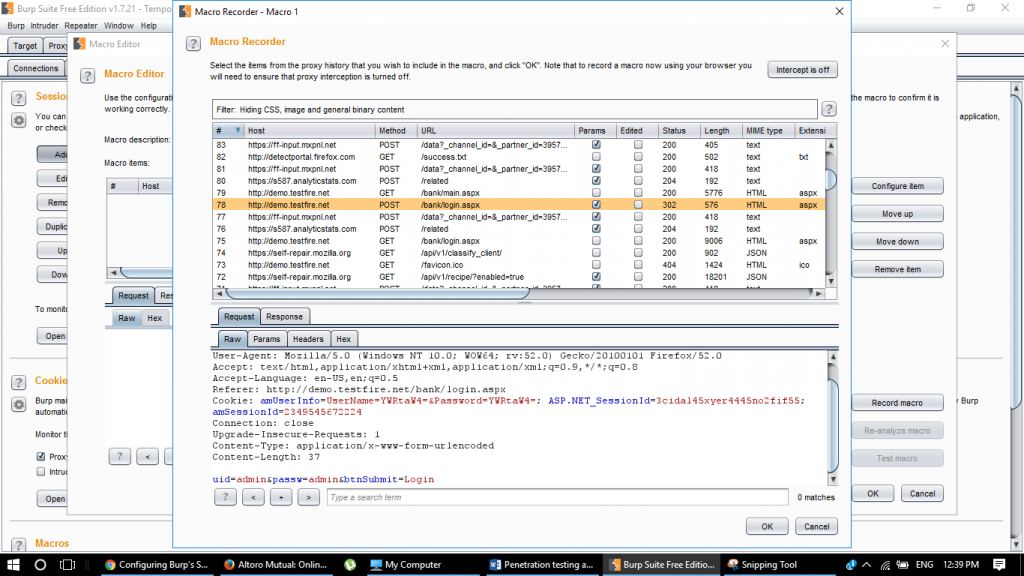
Macro Recorder
Step 14:
Before to running a test, configure the parameters to identify if burp has captured the test parameters correctly.
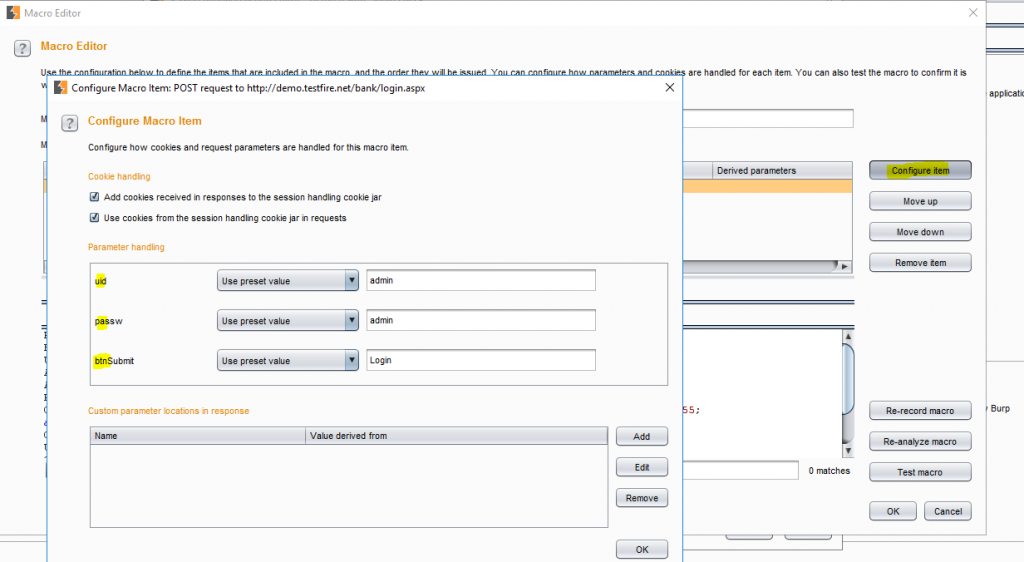
Macro Recorder Parameter Check
Step 15:
Since here all is set, we can perform a run of test macro post click ok.
Step 16:
Now click on final scope and set the URL Scope to all urls / suite scope/ custom scope to guide the macro where to run.
Step 17:
I leave it include all URLs here. Let’s now head over to repeater again to test our macro.
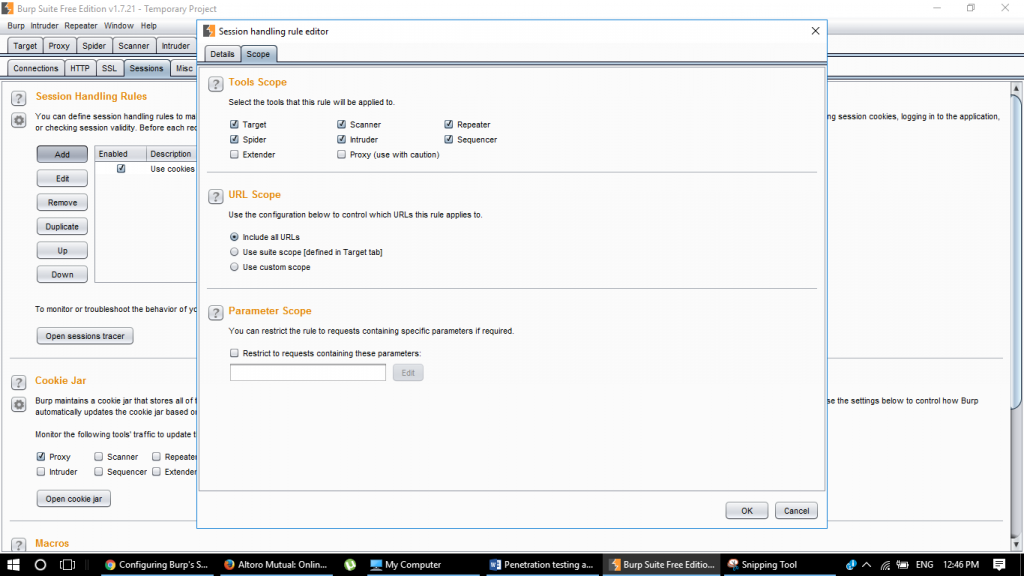
Scope setting for macro
Step 18:
Take a look, we are trying to access the main page without cookies in repeater tab:
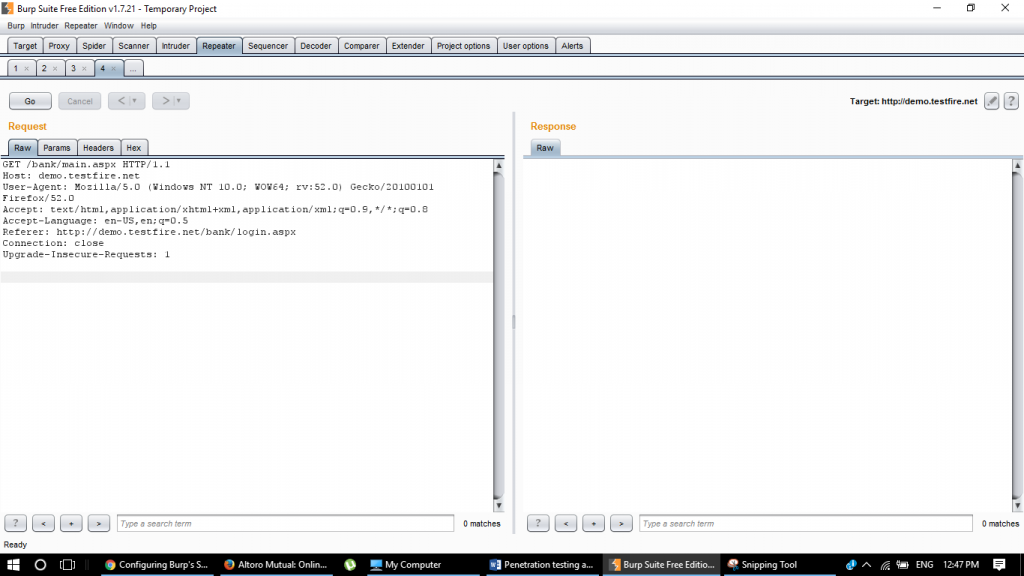
Step 19:
Once we hit go, the cookies will automatically get added to the request and the page will load up!
Tampering cookie value to check session
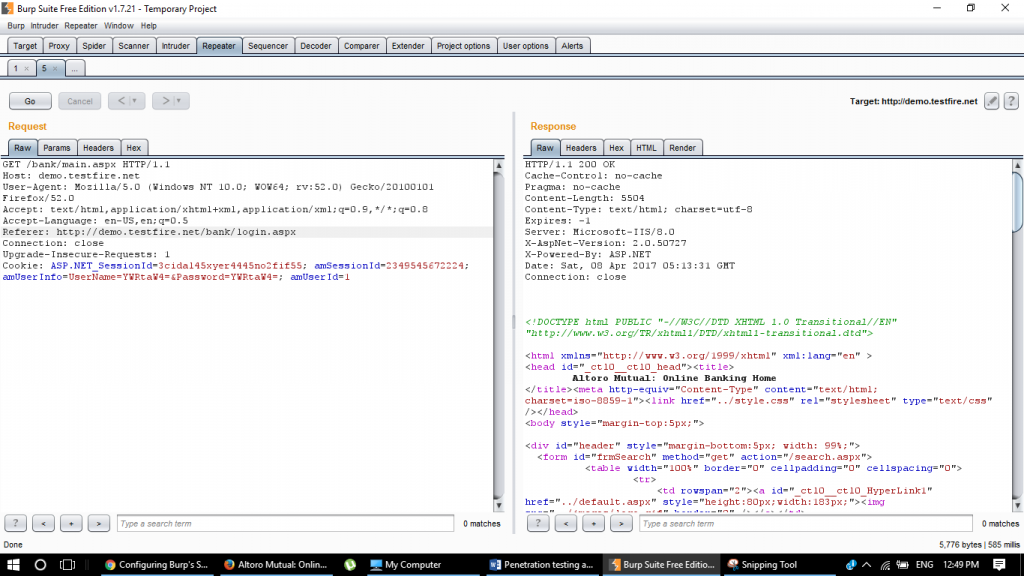
Macro executed
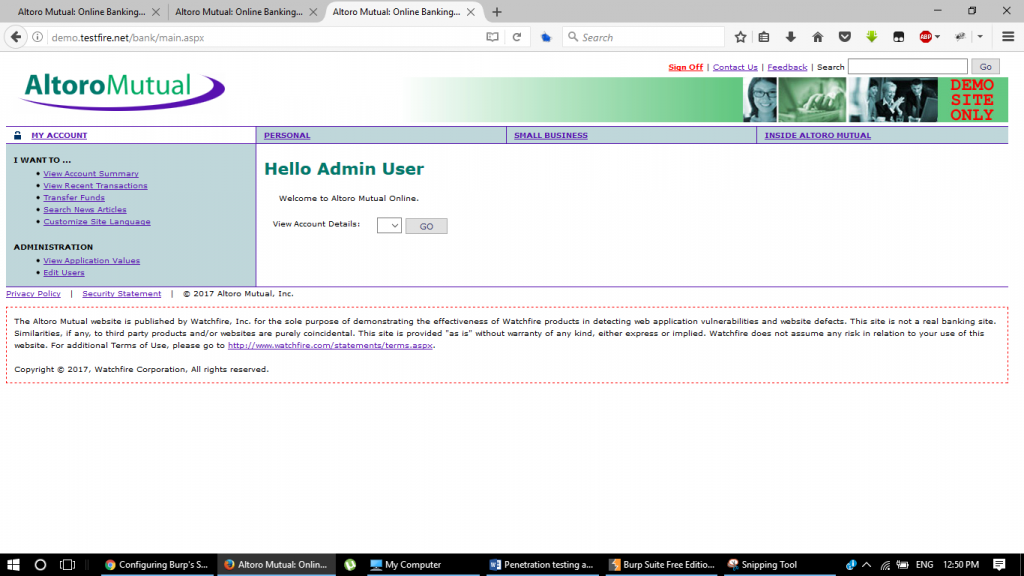
Macro executed with cookie added
So that’s it. It’s a sweet and simple way to show how burp is useful for creating session based rules and macros.
We can simply fuzz the input fields with our test payloads to check for vulnerabilities such as XSS, SQLi, IDOR etc. Even if the application gets timed out due to intermediate inactivity or protects session against junk inputs while automated scanning or manual testing, such macros will help you execute the recorded action and log you back inside the app!
You can explore it further to use cookie jar/ burp extender and lots of other option! Happy experimenting!


