What are IoT Security Challenges?
September 4, 2019
A run-time approach for pen-testing iOS applications Part-II (Objection in Action)
October 7, 2019
Hello everybody,
This article will cover dynamic run-time penetration testing of iOS applications or iOS pentesting, making use of the Objection framework or systems.
An iOS penetration test is performed to distinguish the two vulnerabilities including the potential for unapproved personnel to access the systems and data, as well as strengths, enabling a full danger appraisal or risk management as we know it to be finished
Objection is a run-time mobile exploration toolkit, powered by Frida. Objection injects make use of Frida to inject the objects into application run-time in order to execute certain tasks in the security context. Objection framework enables the pentester to interact with the application’s behavior in real time as well as monitor application’s content, files, key-chains, .plist files, etc. It is also possible to download those files directly into the pc if you have read access for those files as well as we can upload our manipulated files whenever write access has been granted to those files.
Pre-requisite:
Let us have a look at some of prerequisites for the iOS pentesting.
1. Python version 3.4+
Download latest python version from here:
https://www.python.org/downloads/
2. pip or pip3
PIP is a package management system for Python, Once Python has been installed, install pip from this awesome guide.
https://github.com/BurntSushi/nfldb/wiki/Python-&-pip-Windows-installation
3. Jailbroken iOS device:
For easy setup and installation, a jailbroken iOS device is recommended with Cydia installed. We will use iPad with 12.4 iOS version.
Installation:
1. Install Frida and Objection modules in python:
pip install -U objection
pip install -U frida2. virtualenv version 15+:
We will need virtual environment greater than 15. To install virtualenv:
pip install virtualenv3. Check current virtualenv version
virtualenv --version4. Upgrade if virtualenv version is less than 15
pip install virtualenv --upgrade5. Install Frida in iOS device:
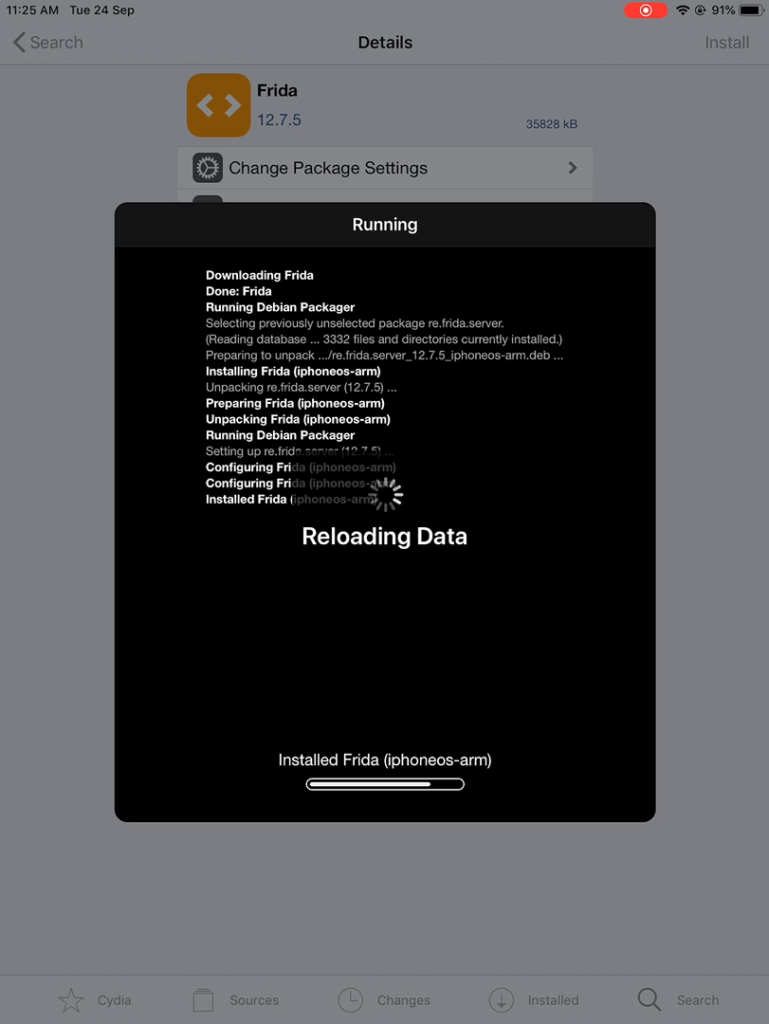
We need to install the Frida scripts package into the iOS device. This package contains the Frida server and the scripts to be injected for the further iOS pentesting. This Frida server will act as a middleware for communicating the commands and the applications.
i. Start cydia in iOS device and goto “Sources”
ii. Click on edit and add following URL:
https://build.frida.reiii. After this, goto search and search for “Frida”
iv. Click on install and frida will get install in device.
6. After all installation we will do small smoke test
i. Connect device via usb to pc
ii. Run powershell or command prompt in Administrator mode and run following command:
frida-ps -U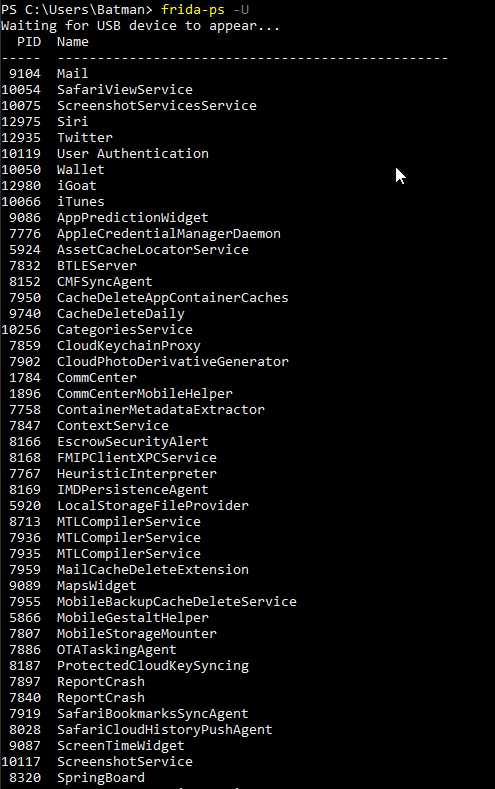
iii. This will list all running services and application is our iOS device
iv. If the target application is not getting listed in this list, open that application and again run the command above.
Objection in action continued in next part…..
Cybersecurity frequently may turn out to be an incorrect observation on the off chance that in the event that we don’t have the foggiest idea how the frameworks or systems were created or developed just as if the iOS pentesting is performed or not.


