Rules of Engagement (RoE) provide a vital framework that aligns the penetration testing processes with business priorities, protects essential assets, and ensures results are both meaningful and actionable while minimizing unnecessary risks.
Without clear rules of engagement, penetration testing can disrupt critical operations, compromise sensitive data, and expose your organization to legal risks. Conducting security assessments without well-defined and mutually agreed boundaries often leads to confusion, unintended outages, and compliance issues.
This blog walks through penetration testing ROE in detail, why it matters, its core components, and best practices.
Key Reasons Why Penetration Testing ROE Matters
For any process to succeed, the framework and rules should be clearly defined. It provides a clearly defined roadmap. Penetration testing ROE is no exception, as it establishes boundaries, scopes, and communication protocols that ensure every test is controlled, transparent, and aligned with business objectives.
Before defining the rules, it’s important to grasp the process itself, learn about Penetration testing and its approaches methods and stages in detail.
Here are some of the reasons it matters:
- Legal Protection: A penetration test without written permission is illegal, no matter how good your intentions are. Legal agreements are binding, shield everyone involved, and ensure tests don’t cross beyond defined limits to avoid lawsuits, fines, or worse.
- Shared Understanding: RoE ensures every stakeholder—from executives to IT staff—understands what’s being tested, when it will happen, and what methods are being employed. There should not be any scope for assumptions or miscommunications.
- Protection from Business Disruption: A test that doesn’t go as intended can cause damage like an actual breach. It can halt operations, modify or delete data, or trigger alerts that send your incident response team into overdrive. RoE can prevent such scenarios by scheduling tests at safe times and avoiding risky methodologies.
- Meaningful Results: When testers know what’s allowed and what isn’t, they can dig deep without wasting time. As a result, you get actionable findings, not a mess to clean up.
Core Components of the Penetration Testing Rules of Engagement
Here is a list of key components of penetration testing ROE:
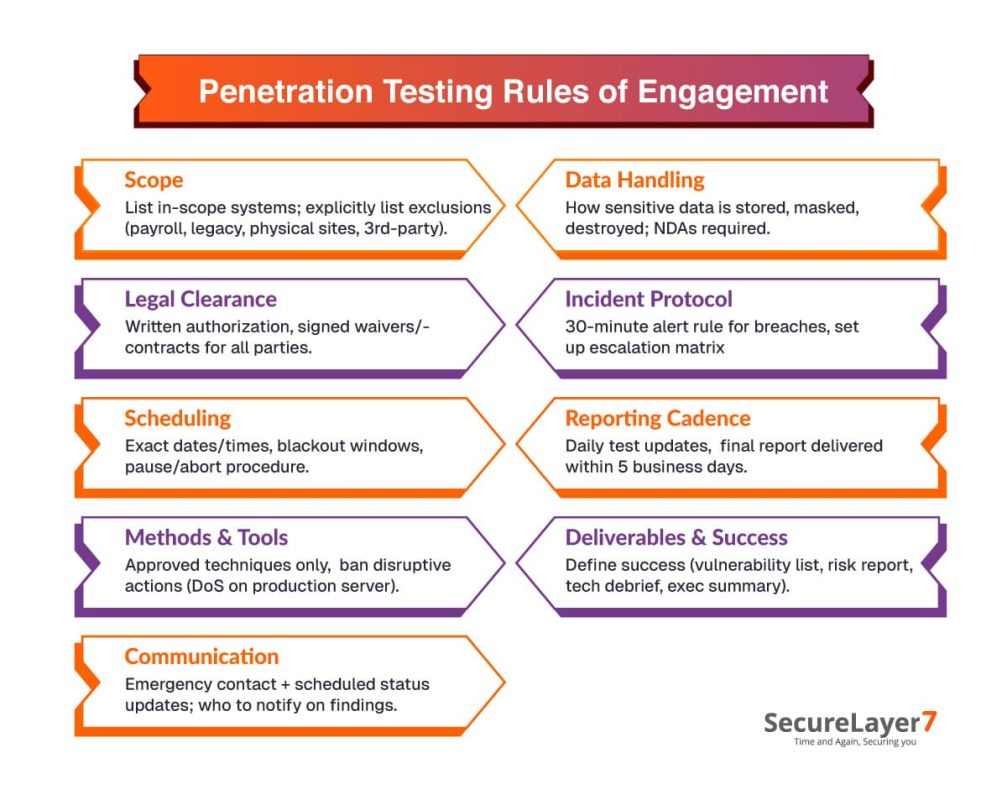
Scope
- List every system, app, or cloud service on the test menu.
- Make it clear what’s off-limits (e.g., payroll systems, customer data, legacy gear).
- Don’t forget physical locations or third-party integrations.
Legal Clearance
- Get written authorization from decision-makers.
- Ensure all waivers and contracts are signed. This covers both your team and the consultants.
Scheduling
- Define exact testing windows that include dates, hours, and blackout periods.
- Make a plan for how to pause or stop the test if something unexpected happens.
Methods and Tools
- Approve only those attack techniques and tools that won’t disrupt key operations.
- Prohibit anything likely to cause service loss, such as Denial-of-Service (DoS) attacks on production.
Communication
- Establish a direct line for urgent communication during the test, as well as scheduled updates.
- Set up a clear protocol for who gets notified if a real vulnerability is discovered or something breaks.
Data Handling
- Write out how any sensitive data found during the process will be treated, stored, and destroyed.
- Use non-disclosure agreements to ensure confidentiality.
Incident Protocol
- Establish a clear alerting process for critical incidents. For example, if a tester discovers a breach exposing sensitive customer data, they must call and email the security team within 30 minutes.
- Set up a structured escalation matrix or a defined chain of command to ensure incidents are reported to the right people in the right order. For example, if the Security Manager is unavailable, the tester contacts the CTO next.
Reporting Cadence
- Prepare a pre-established reporting cadence to ensure relevant stakeholders receive timely updates.
- Send daily email updates during testing and deliver the final detailed findings report within five business days after completion.
Deliverables and Success Criteria
- Clearly specify what counts as a win: a list of critical vulnerabilities, a risk report, technical debriefs, or executive summaries.
- Align deliverables with clear business and risk focus.
Key Stakeholders Involved in Drafting ROE
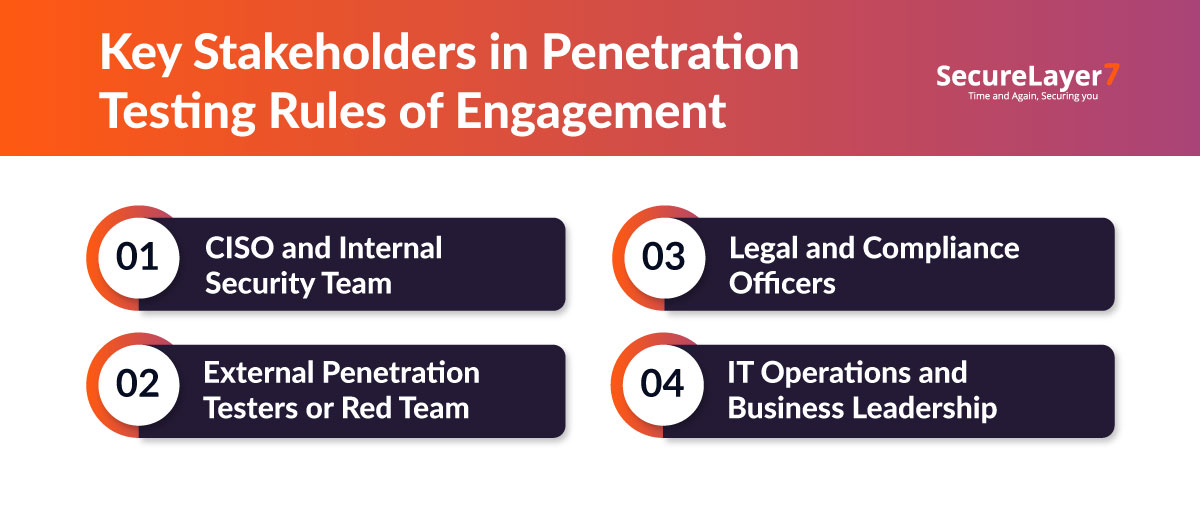
Drafting rules of engagement involves key stakeholders to ensure tests align with security, legal compliance, technical risks, and business continuity goals.
- CISO and Internal Security Team: The CISO and security team set security priorities and ensure the engagement aligns with overall business security objectives, addressing the organization’s most critical assets.
- External Penetration Testers or Red Team: External testers bring specialized expertise, design tailored attack scenarios, and advise on technical feasibility.
- Legal and Compliance Officers: Legal and compliance stakeholders review testing plans to ensure activities comply with laws and regulations.
- IT Operations and Business Leadership: Involvement of IT operations and business leaders ensures testing serves business objectives and minimizes risks to ongoing operations.
Common Mistakes in ROE Creation (and Consequences)
Setting clear Rules of Engagement (ROE) is crucial for effective and safe penetration testing. Overlooking common mistakes can expose organizations to security, legal, and communication risks.
Failing to clearly define which systems are in scope may result in testing unintended or sensitive assets, leading to outages, business disruption, or breaches of trust and confidentiality.
For example, if testers are unclear about the scope of production server testing, it can cause a temporary outage and customer complaints.
Not involving legal experts can create serious compliance issues, as testers might violate laws or regulatory requirements, exposing the organization to fines, lawsuits, or regulatory actions. For example, if personal data is accessed without consent, it may result in a regulatory investigation.
Without a predefined escalation plan, critical incidents may be detected but not promptly communicated to responsible teams, delaying response and potentially worsening security incidents or business impacts.
For example, a tester may discover active malware but, if unaware of the escalation matrix, could email non-relevant stakeholders instead of the incident response team, delaying containment efforts.
Inadequate instructions for interim and final reporting can lead to missed findings and confusion among stakeholders.
Consequences of the Lack of Penetration Testing Rules of Engagement
Rules of engagement don’t just help avoid risks; they play a critical role in forging trust and collaboration between the penetration testing team and the organization’s IT and security teams. By explicitly communicating what is authorized, when tests will occur, and how findings will be shared, ROE brings transparency to the entire process.
For example, an organization allowing pentesting without a well-defined ROE may create confusion among employees when unexpected scanning triggers firewalls or when testers attempt social engineering attacks.
As a result, the IT team may choose to block testers mid-engagement or leadership may question the value of testing altogether.
Real-World Example of ROE Success and Failure
A major financial institution hired a penetration testing partner to assess its internet and mobile banking applications. The RoE precisely defined scope, permissions, and testing times, escalation steps, reporting, data handling, communication channels, executive approvals, and scheduled off-peak hours.
Testers discovered and helped address critical vulnerabilities—such as flaws risking unauthorized access without disrupting business or violating legal boundaries.
Lesson Learned: Clear, comprehensive RoE empowers testers to operate confidently, helps organizations avoid legal or operational pitfalls, and ensures findings translate into concrete security improvements.
Best Practices: Penetration Testing Rules of Engagement
Below is a list of best practices for creating penetration testing ROE:
Clearly Define the Scope and Permissions
- Establish a detailed list of all assets, such as applications, networks, and physical locations.
- Explicitly state what testing methods are allowed or prohibited.=
- Document special items such as sensitive data handling or emergency shutoff procedures.
- Clearly specify restrictions on testing, if any.
- Identify any third-party systems that may be indirectly affected.
- Make a list of acceptable testing tools and techniques to avoid unintended disruptions.
Obtain Formal Written Authorization and Approvals
- Obtain signed approval from senior management and legal departments before testing starts.
- Confirm that all permissions cover both technical and physical testing activities (if applicable).
- Maintain copies of authorization as legal protection for both testers and the organization.
- Ensure external testers acknowledge and accept these terms formally.
- Clearly specify the timeframe for which the approval is valid.
Establish Comprehensive Communication
- Define primary communication channels (email, phone, messaging platforms) for routine updates and urgent alerts.
- Create a detailed escalation matrix listing personnel roles, contact info, and step-by-step escalation order for incidents.
- Incorporate procedures for handling emergencies such as unintended outages or data leaks.
- Document all communications to maintain an audit trail.
Schedule and Document Testing Windows and Constraints
- Agree upon specific testing dates and timeframes.
- Add contingency plans for pauses, rescheduling, or emergencies.
- Clearly communicate testing schedules to all affected parties (IT, business units, legal).
- Confirm test duration limits to prevent prolonged exposure or unintended persistence.
- Consider time zone differences if teams or systems are geographically dispersed.
Define Data Handling, Privacy, and Reporting Requirements
- Outline how sensitive data accessed during tests will be protected, stored, and destroyed post-engagement.
Detail what data can be included in reports, ensuring compliance with privacy regulations like GDPR. - Specify reporting frequency (interim and final), report formats, and distribution lists to guarantee transparency and actionability.
- Establish confidentiality agreements and nondisclosure clauses for testers and stakeholders.
Plan for Risk Management and Business Continuity
- Identify potential risks inherent in testing activities and set mitigation steps to minimize business impact.
- Prepare clear instructions on how to handle situations if critical systems are affected during testing.
- Coordinate with business continuity and disaster recovery teams to ensure alignment.
- Define escalation steps based on risk thresholds.
- Include insurance or liability considerations.
Conclusion
Penetration testing rules of engagement serves as a basic manual for security teams. Ignoring it may put the process at risk, as it may become directionless. RoE protects the interests of all parties involved in the process. When security teams have a clear roadmap, they don’t wait for attacks to happen—they proactively handle vulnerabilities.
Ready to launch penetration testing? Avoid confusion and gain clarity from the start. Contact us today to schedule a 30-minute discovery call.
FAQs
The RoE must be formally approved by senior leadership (e.g., CEO, CISO) at the client organization before testing begins, and both parties (client and service provider) should sign off to confirm agreement.
The RoE must be explicit and comprehensive, covering scope (in/out of scope assets), timing, methods, contacts, communication protocols, incident response, data handling, and legal authorization—sufficient to prevent ambiguity and operational risk.
No action outside the approved RoE is permitted without prior, explicit client approval. Testers must pause and request authorization, as unauthorized activities risk legal and operational consequences.
The RoE should be reviewed and updated for each new engagement or whenever major changes occur in systems, compliance, or business objectives—typically annually or after significant system/process changes.



