
Smart Contract Audits: Ensuring Trust and Security in Blockchain
August 4, 2023
A Guide To Web3 Penetration Testing
August 17, 2023
In an increasingly connected world, the online presence of businesses and individuals heavily relies on websites.
WordPress, a widely embraced content management system (CMS), empowers millions of websites with its versatility and user-friendly interface.
However, with great popularity comes a heightened risk of cyber threats, making it imperative to prioritize the security of your WordPress site.
Enter vulnerability assessment and penetration testing – the dynamic duo of website protection.
In this blog, we will embark on a journey to uncover the essential practices of securing your WordPress website through these powerful techniques.
Whether you’re a website owner, developer, or security enthusiast, understanding and implementing these strategies will fortify your digital fortress against potential vulnerabilities.
By following this concise guide, you will acquire a deeper understanding of WordPress vulnerabilities, learn to assess your site’s security and deploy the necessary measures to shield it from potential threats.
With a proactive approach to security, you can instill confidence in your visitors and safeguard the long-term success of your WordPress website.
The Importance of Understanding WordPress Vulnerabilities
WordPress vulnerabilities can be likened to hidden entry points that cybercriminals can exploit to gain unauthorized access to your website.
Understanding these vulnerabilities is essential because it empowers you to proactively protect your site and its sensitive data. Here’s why comprehending these vulnerabilities is vital:

1. Risk Mitigation
Identifying vulnerabilities in your WordPress site plays a critical role in maintaining its security. It empowers you to take the necessary steps to mitigate potential risks before they are exploited by malicious actors.
By staying informed about the latest vulnerabilities and security best practices, you can proactively implement preventive measures that significantly reduce the likelihood of a successful attack.
When you identify vulnerabilities in your WordPress site, you gain valuable insights into potential weak points that attackers could exploit.
This knowledge allows you to take swift action to address these vulnerabilities before they are leveraged for malicious purposes. By conducting regular vulnerability assessments and staying up-to-date with the latest security information, you can stay one step ahead of cyber threats.
Staying informed about the latest vulnerabilities and security best practices is crucial for effective risk mitigation.
Security researchers and the WordPress community continually discover and disclose vulnerabilities, along with recommended solutions.
By actively monitoring these developments, you can access patches, updates, and guidelines that address emerging threats.
Implementing these preventive measures, such as promptly applying software updates and configuring robust access controls, enhances the security posture of your WordPress site.
2. Understanding Potential Risks
Once vulnerabilities are identified in your WordPress site, it is crucial to comprehend the potential risks they present.
This involves conducting a comprehensive assessment of the impact that successful exploitation of each vulnerability could have on your website, data, and users.
By understanding these risks, you gain valuable insights that allow you to prioritize your mitigation efforts and allocate resources effectively.
Understanding the potential risks associated with each vulnerability helps you gauge the severity of the potential consequences.
For example, a vulnerability that allows unauthorized access to sensitive user data can lead to privacy breaches and damage to your reputation.
On the other hand, a vulnerability that results in a denial-of-service attack could lead to extended periods of downtime and loss of revenue.
By comprehending these risks, you can make informed decisions on how to address them based on their potential impact.
Once you have assessed the risks, you can prioritize your mitigation efforts accordingly. High-risk vulnerabilities that have severe consequences require immediate attention and remediation.
This may involve applying patches, updating software versions, or implementing additional security measures.
Medium-risk vulnerabilities may require action in the near future, while low-risk vulnerabilities can be addressed over time.
By prioritizing your efforts, you can focus on the vulnerabilities that pose the greatest risk to your WordPress site and allocate your resources effectively to mitigate these risks.
3. Security Best Practices
Security researchers and the WordPress community consistently release updates, patches, and guidelines that specifically target emerging threats.
By actively staying up-to-date, you can gain valuable insights into recommended security measures and implement them effectively, thereby reducing the attack surface and fortifying your site’s defenses.
Keeping abreast of the latest vulnerabilities allows you to stay one step ahead of potential attackers.
Security researchers continuously discover and disclose vulnerabilities, helping you understand the evolving threat landscape.
The WordPress community, known for its commitment to security, promptly responds to these discoveries by issuing updates and patches.
By regularly monitoring these developments and promptly applying relevant security updates, you can mitigate the risk of your site being exploited through known vulnerabilities.
In addition to updates and patches, security best practices provide essential guidance for strengthening your WordPress site’s defenses.
These practices encompass a wide range of areas, such as user authentication, access controls, secure coding practices, and data encryption.
By adhering to these best practices, you minimize potential vulnerabilities and create layers of protection for your site.
Implementing measures like strong passwords, utilizing two-factor authentication (2FA), restricting user privileges, and regularly backing up your site’s data contribute significantly to its overall security posture.
4. Preventive Measures:
Armed with knowledge about vulnerabilities and security best practices, you can take preventive measures to mitigate risks. This may involve actions such as:
- Applying software updates and security patches promptly to fix known vulnerabilities.
- Configuring secure access controls, including strong passwords and two-factor authentication (2FA).
- Utilizing secure coding practices to minimize the chances of introducing vulnerabilities during development.
- Regularly backing up your site’s data to minimize data loss in case of an attack.
- Implementing web application firewalls (WAFs) or security plugins to add an extra layer of protection against common attack vectors.
By proactively implementing these preventive measures based on vulnerability identification and risk assessment, you significantly reduce the likelihood of a successful attack on your WordPress site.
Remember, security is an ongoing process, and regular vulnerability assessments, coupled with continuous monitoring and updates, are vital for maintaining a secure website.
Preparing for a WordPress Penetration Test
Ensuring a thorough and effective WordPress security audit is essential before conducting a penetration test. Here are two crucial steps to consider during the preparation phase:
Install Kali Linux for Your WordPress Security Audit:
When preparing for a WordPress security audit, it is highly recommended to install Kali Linux on your testing environment. Kali Linux is an operating system purpose-built for penetration testing and security assessments.
By installing Kali Linux, you gain access to a wide range of powerful tools and resources specifically designed for assessing the security of your WordPress site. These tools include vulnerability scanners, network analysis utilities, password crackers, and exploitation frameworks.
With Kali Linux, you can perform a variety of tests and simulations to evaluate the security of your WordPress installation. For instance, you can conduct vulnerability scans to identify potential weaknesses in your site’s software versions, plugins, or configurations.
Additionally, you can simulate attacks such as SQL injections, cross-site scripting (XSS), or brute-force attacks to uncover vulnerabilities and assess the effectiveness of your defenses.
Kali Linux’s comprehensive suite of security tools and resources empowers you to conduct a thorough assessment of your WordPress site’s security posture.
By utilizing these specialized tools, you can proactively identify potential vulnerabilities and weaknesses, enabling you to take appropriate measures to mitigate risks and enhance the overall security of your WordPress installation. It is important to note that Kali Linux should be used responsibly and only on systems that you have proper authorization to test.
Get consent for your WordPress pentest
Obtaining consent is an integral part of conducting a WordPress penetration test responsibly and ethically.
Before initiating any security assessment, it is crucial to seek explicit permission from the website owner or administrator.
Conducting unauthorized testing without consent not only raises legal concerns but can also disrupt services and harm the reputation of both the tester and the website owner.
By obtaining proper consent, you ensure a transparent and collaborative approach that fosters trust and cooperation.
Seeking permission for a WordPress penetration test demonstrates your commitment to professionalism and ethical conduct. It allows the website owner or administrator to be aware of the testing activities and understand the purpose behind them.
This open communication establishes a collaborative environment where you can work together to identify and address potential security issues.
Moreover, obtaining consent provides legal protection for both parties, ensuring that the test is conducted within the boundaries of applicable laws and regulations.
By obtaining explicit consent, you establish a framework of trust and cooperation with the website owner or administrator.
Three steps in a WordPress penetration test
WordPress penetration testing typically involves three key steps: mapping, discovery, and exploitation.
Let’s delve into each step, discussing their significance and highlighting some tools commonly used in the process.
1. Mapping – The first step of WordPress penetration testing
The mapping phase involves gathering information about the WordPress site, its infrastructure, and its potential entry points for exploitation.
This step aims to create a comprehensive understanding of the target’s architecture and identify areas that may be susceptible to attacks. Here is the list of several tools which can assist in this process:

NMAP
NMAP (Network Mapper) is a versatile network scanning tool that helps discover hosts, services, and open ports on a network.
It can be used to identify the IP addresses associated with the WordPress site, as well as the services running on those IP addresses.
By conducting various scan types, NMAP provides valuable insights into the network infrastructure supporting the WordPress site, helping testers create an accurate network map.
Zenmap
Zenmap is the graphical user interface (GUI) version of NMAP. It offers a user-friendly interface for network scanning and mapping, providing visual representations of the network topology.
Zenmap allows testers to explore and analyze the discovered hosts, open ports, and services in an intuitive manner, making it easier to identify potential vulnerabilities and weaknesses in the WordPress site’s network infrastructure.
ReconDog
ReconDog is an all-in-one reconnaissance tool that automates information gathering during the mapping phase.
It performs various scans to collect data about the target site, such as IP addresses, subdomains, DNS information, open ports, and more.
ReconDog aggregates this information into a comprehensive report, aiding testers in mapping the WordPress site’s infrastructure and identifying potential attack vectors.
Open Source Intelligence (OSINT)
Open Source Intelligence refers to the collection and analysis of information from publicly available sources.
During the mapping phase, OSINT tools and techniques can be employed to gather information about the WordPress site, its owner, and associated entities.
OSINT tools utilize search engines, social media platforms, online databases, and other sources to extract valuable data that can contribute to the mapping process.
WPintel Chrome Plugin
WPintel is a Chrome plugin specifically designed for WordPress intelligence gathering. It provides insights and information about WordPress sites, such as the themes and plugins being used, their versions, and other metadata.
WPintel helps testers quickly identify key WordPress-related information directly from within their web browser, aiding in the mapping phase by providing valuable insights into the target WordPress site.
DirBuster
DirBuster is a tool utilized for brute-forcing directories and files on web servers. During the mapping phase, DirBuster assists in the discovery of hidden or unprotected directories and files within the WordPress site.
By exhaustively scanning directories, DirBuster can reveal potentially sensitive areas or misconfigurations, enabling testers to identify potential vulnerabilities and weaknesses in the site’s file structure.
WPScan
WPScan is a widely recognized vulnerability scanner specifically designed for WordPress. It helps identify security vulnerabilities, misconfigurations, and outdated plugins or themes within the WordPress site.
WPScan’s extensive vulnerability database and continuous updates make it a go-to tool for security audits in the WordPress ecosystem.
During the mapping phase, WPScan assists in identifying potential weaknesses, and guiding testers in prioritizing their efforts for subsequent stages of the penetration testing process.
2. What’s next in WordPress penetration testing: Discovery Phase
During the discovery phase of WordPress penetration testing, our main goal is to uncover vulnerabilities and potential security weaknesses within the WordPress site.
This phase requires a comprehensive examination and assessment of various components, including themes, plugins, configurations, and user inputs.
In order to accomplish this task, we rely on a range of valuable tools, with WPScan being one of the key players. Let’s explore this further.
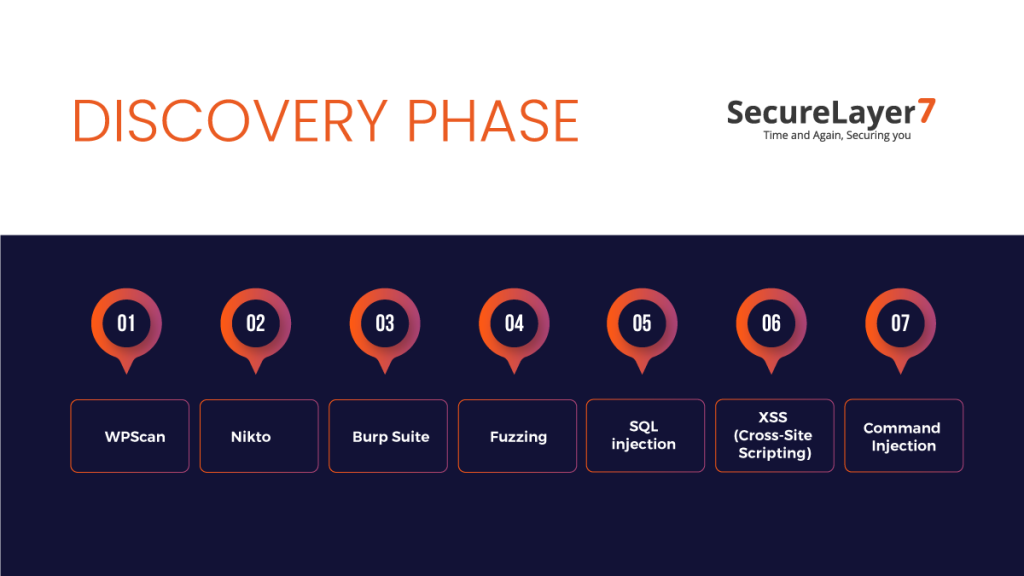
Let us get to know these in detail
WPScan
WPScan is widely recognized as a highly regarded vulnerability scanner that has been specifically developed for WordPress.
Its primary purpose is to identify a range of security vulnerabilities, including outdated themes or plugins, misconfigurations, and weak passwords.
What makes WPScan truly powerful is its utilization of an extensive and continuously updated database of known vulnerabilities.
By leveraging this database, WPScan thoroughly scans the WordPress site, meticulously searching for potential weaknesses.
Once the scan is complete, it generates detailed reports that highlight the identified issues, empowering testers to take appropriate remedial actions to address the vulnerabilities effectively.
With WPScan in our toolkit, we can confidently uncover and address security concerns within the WordPress site, ultimately fortifying its defenses against potential threats.
Nikto
Nikto is an invaluable web server scanner that plays a crucial role during the discovery phase of WordPress penetration testing.
Its purpose is to thoroughly examine the web server that hosts the WordPress site, enabling us to identify common misconfigurations and potential security risks.
By performing comprehensive tests, Nikto meticulously checks for various vulnerabilities and issues that could compromise the security of the server and, consequently, the WordPress site.
One of the key features of Nikto is its ability to detect outdated server software. It carefully analyzes the server’s software versions and compares them against known vulnerabilities and patches.
This helps us pinpoint any outdated software that could be susceptible to exploitation by attackers.
Additionally, Nikto assesses files and permissions configuration to ensure they are appropriately set, minimizing the risk of unauthorized access or unintended exposure of sensitive information.
Furthermore, Nikto looks for potential vulnerabilities within the server, including misconfigured server options or weak security configurations.
It searches for common security loopholes that could be leveraged by malicious actors to gain unauthorized access or perform unauthorized actions on the server. By uncovering these server-side security risks, Nikto provides valuable insights that allow us to proactively address them, thereby strengthening the overall security of the WordPress site.
Burp Suite
Burp Suite is an incredibly powerful and versatile web application security testing tool that proves invaluable during the discovery phase of WordPress penetration testing.
It offers a range of modules designed to assist testers in uncovering potential vulnerabilities within the WordPress site and ensuring its robust security.
The proxy module is a standout feature of Burp Suite. It allows testers to intercept and analyze web requests and responses between the browser and the WordPress site.
By intercepting the traffic, testers gain visibility into the data being exchanged and can identify potential security vulnerabilities. This module serves as a vital tool for understanding how the WordPress site interacts with the user’s input and how it handles various types of requests.
Another essential module within Burp Suite is the scanner module. This module automates the scanning process, enabling testers to identify common vulnerabilities present in the WordPress site.
It leverages a comprehensive database of known vulnerabilities and security issues to analyze the site’s components, such as themes, plugins, and configurations.
The scanner module effectively highlights potential weaknesses, giving testers a clear picture of the security landscape and enabling them to focus their efforts on mitigating these vulnerabilities.
Fuzzing
Fuzzing is an effective technique employed during the discovery phase of WordPress penetration testing to uncover vulnerabilities by injecting unexpected or malformed data into a system.
By inputting this unconventional data, testers aim to trigger unexpected behavior and identify potential security weaknesses within the WordPress site.
Fuzzing is particularly useful for detecting input validation issues, buffer overflows, and various other types of vulnerabilities that may have otherwise gone unnoticed.
To streamline the fuzzing process, testers can leverage specialized fuzzing tools such as AFL (American Fuzzy Lop) or OWASP ZAP.
These tools automate the generation and submission of a large number of inputs to the WordPress site, targeting different components like forms, URLs, or parameters.
By systematically injecting diverse and potentially malicious inputs, fuzzing tools help identify how the site responds to different scenarios and unveil any vulnerabilities or weaknesses in its handling of such inputs.
One key advantage of fuzzing is its ability to uncover previously unknown or unexpected security flaws.
It goes beyond traditional testing methods by exploring edge cases and unanticipated scenarios that could potentially lead to vulnerabilities.
Fuzzing enables testers to simulate real-world attack scenarios and evaluate how the WordPress site reacts under stress or with non-standard inputs.
For specific vulnerability types:
SQL injection
Tools like SQLMap and Havij are widely utilized during the discovery phase of WordPress penetration testing to detect and exploit SQL injection vulnerabilities.
SQL injection is a severe security flaw that occurs when an attacker is able to manipulate the site’s database queries by injecting malicious SQL code.
These tools automate the process of identifying and exploiting such vulnerabilities, enabling testers to comprehensively assess the security posture of the WordPress site.
SQLMap and Havij possess advanced capabilities that allow testers to efficiently scan the WordPress site for potential SQL injection vulnerabilities.
These tools analyze the site’s inputs, such as form fields or URL parameters, and attempt to inject malicious SQL statements. By doing so, they aim to provoke unexpected behavior or retrieve sensitive information from the site’s database.
Once an SQL injection vulnerability is detected, these tools offer features to exploit the flaw further.
They enable testers to execute arbitrary SQL commands, extract database information, modify data, or even gain unauthorized access to the site’s backend systems.
By demonstrating the potential impact of an SQL injection vulnerability, testers can emphasize the urgency of addressing and mitigating such security risks.
XSS (Cross-Site Scripting)
Tools like XSSer and OWASP ZAP are valuable resources during the discovery phase of WordPress penetration testing, specifically for identifying and exploiting cross-site scripting (XSS) vulnerabilities.
XSS vulnerabilities occur when untrusted user input is improperly handled, allowing malicious scripts to be injected into the site’s pages and executed by unsuspecting users. These tools automate the process of identifying and exploiting XSS vulnerabilities, enabling testers to comprehensively assess the security of the WordPress site.
When using tools like XSSer and OWASP ZAP, testers can analyze various input fields and parameters within the WordPress site to identify potential XSS vulnerabilities. These tools simulate different attack scenarios by injecting specially crafted payloads into the site’s inputs, such as form fields or URL parameters.
By monitoring the site’s responses and analyzing the injected payloads, testers can identify instances where the injected scripts are successfully executed or displayed on the site’s pages.
Once an XSS vulnerability is detected, these tools provide options for exploiting the flaw further. They allow testers to inject malicious scripts and evaluate the potential impact on the site and its users.
By demonstrating the ability to execute arbitrary code within the context of the site, testers can illustrate the risks associated with XSS vulnerabilities and the potential consequences if left unaddressed.
Command Injection
Tools like Commix and OWASP ZAP are invaluable during the discovery phase of WordPress penetration testing as they assist in identifying and exploiting command injection vulnerabilities.
Command injection vulnerabilities pose a significant threat when user inputs are not properly sanitized and are directly passed to a command interpreter.
This allows attackers to execute malicious commands on the server hosting the WordPress site. By automating the detection and verification process, these tools support testers in securing the WordPress site against potential command injection attacks.
During testing, tools like Commix and OWASP ZAP carefully examine user inputs within the WordPress site to uncover potential command injection vulnerabilities.
They meticulously inject specially crafted payloads into input fields, URLs, or other parameters, closely observing the response from the server.
By analyzing any unexpected behavior in the response, testers can determine if the site is susceptible to command injection attacks, where an attacker could potentially exploit the vulnerability.
Once a command injection vulnerability is discovered, these tools provide options for further exploration and exploitation.
Testers can simulate the execution of arbitrary commands on the server, showcasing the potential impact an attacker could have if they gained unauthorized access.
By demonstrating the ability to execute commands, testers can effectively communicate the severity of command injection vulnerabilities and emphasize the need for their prompt remediation.
Exploitation – The final stage of WordPress penetration testing
Exploitation is a critical phase in WordPress penetration testing where the objective is to leverage identified vulnerabilities to gain unauthorized access or control over the target system.
This phase allows testers to assess the potential impact of successful attacks and provides insights into the effectiveness of existing security measures.
During the exploitation phase, testers utilize various techniques and tools to exploit vulnerabilities discovered in the WordPress site. While the specific methods employed may vary depending on the vulnerabilities present, common approaches include:
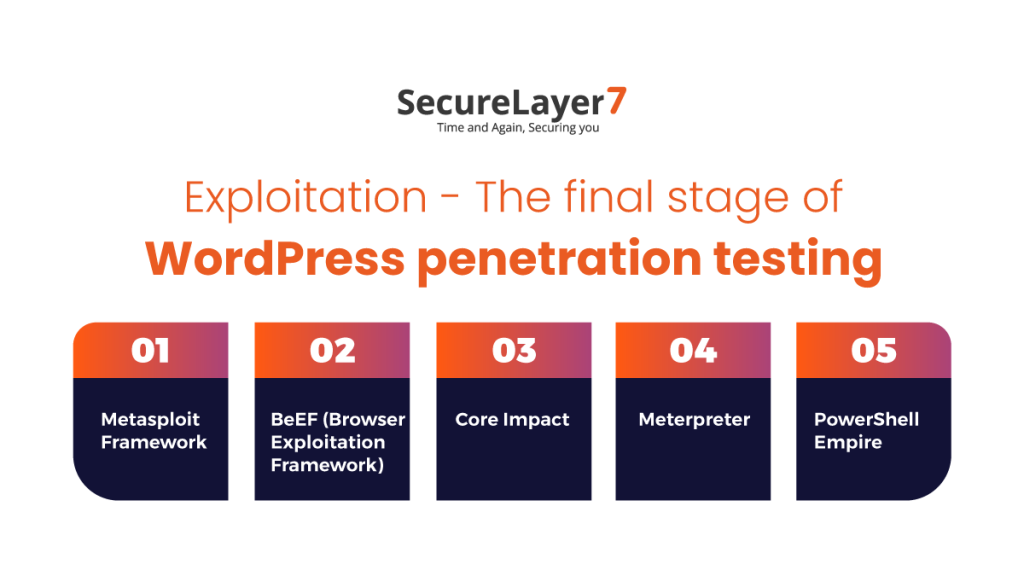
Metasploit Framework
The Metasploit Framework is a powerful and widely-used exploitation tool that offers a comprehensive set of tools for identifying and exploiting vulnerabilities.
It provides a vast array of exploits, payloads, and auxiliary modules that can be used to gain unauthorized access to the WordPress site.
With Metasploit, testers can automate the process of finding and exploiting vulnerabilities, making it an essential tool in a penetration tester’s arsenal.
BeEF (Browser Exploitation Framework)
BeEF is a specialized framework designed for targeting web browsers. It enables testers to exploit client-side vulnerabilities, such as cross-site scripting (XSS) or HTML injection.
By leveraging BeEF, testers can take control of user browsers interacting with the WordPress site. This allows them to manipulate the browser’s behavior, launch attacks, and gather valuable information from the compromised browsers.
Core Impact
Core Impact is a commercial penetration testing tool that offers a wide range of exploits for various platforms and applications, including WordPress.
It provides a comprehensive set of features for automating the identification and exploitation of vulnerabilities. Core Impact enables testers to perform in-depth assessments, generate detailed reports, and gain a comprehensive understanding of the site’s security posture.
Meterpreter
Meterpreter is a powerful payload that is part of the Metasploit Framework. It provides an interactive shell that allows testers to maintain control over a compromised system.
With Meterpreter, testers can perform post-exploitation activities, such as exploring the compromised WordPress site, extracting valuable information, and maintaining persistence on the compromised system.
PowerShell Empire
PowerShell Empire is a post-exploitation framework that leverages PowerShell, a scripting language built into Windows, to gain control over compromised systems.
It offers a wide range of modules and capabilities for maintaining persistence, lateral movement, and data exfiltration from the compromised WordPress site.
PowerShell Empire allows testers to execute PowerShell scripts remotely, enabling them to perform various actions and extract sensitive data from the compromised system.
Common WordPress security issues and how to solve them
Here are some common WordPress security issues and solutions to address them:
Weak Passwords
- Issue: Weak passwords make it easier for attackers to gain unauthorized access to your WordPress site.
- Solution: Encourage users to create strong, unique passwords. Implement password policies that require a combination of uppercase and lowercase letters, numbers, and special characters. Consider using a password manager to generate and store complex passwords securely.
Outdated WordPress Core, Themes, and Plugins:
- Issue: Outdated software versions may contain known vulnerabilities that can be exploited by attackers.
- Solution: Regularly update your WordPress core, themes, and plugins to the latest versions. Enable automatic updates whenever possible or set up notifications for available updates. Remove or replace unsupported or abandoned plugins/themes with actively maintained alternatives.
Insufficient User Permissions:
- Issue: Giving users excessive administrative privileges can increase the risk of unauthorized access or accidental damage.
- Solution: Assign user roles and permissions based on their specific needs. Limit administrative access to trusted individuals. Regularly review and revoke unnecessary privileges for users who no longer require them.
Inadequate Backup and Recovery:
- Issue: Without proper backups, you may risk losing your website data in the event of a security incident or system failure.
- Solution: Implement regular backup procedures for your WordPress site, including both files and databases. Store backups securely on remote servers or cloud storage platforms. Test the restoration process periodically to ensure backups are working effectively.
Cross-Site Scripting (XSS) Attacks:
- Issue: XSS attacks occur when malicious scripts are injected into web pages, potentially compromising users’ data or spreading malware.
- Solution: Use security plugins or web application firewalls (WAFs) that can help detect and prevent XSS attacks. Sanitize and validate user inputs to prevent script injection. Regularly update themes and plugins, as developers often release patches to address XSS vulnerabilities.
SQL Injection Attacks:
- Issue: SQL injection occurs when malicious SQL queries are injected into web forms or database queries, potentially granting unauthorized access to the database.
- Solution: Use prepared statements or parameterized queries in your WordPress code to prevent SQL injection. Avoid using user inputs directly in database queries. Regularly update and sanitize user inputs to ensure they meet the expected format and don’t contain malicious code.
Brute Force Attacks:
- Issue: Brute force attacks involve automated attempts to guess user passwords, potentially leading to unauthorized access.
- Solution: Enforce strong passwords and implement login attempt limitations or lockout mechanisms. Consider using two-factor authentication (2FA) to add an extra layer of security. Use security plugins that offer features specifically designed to protect against brute force attacks.
File Upload Vulnerabilities:
- Issue: Insecure file upload mechanisms can allow attackers to upload malicious files to your server, leading to potential compromises.
- Solution: Implement file upload restrictions, such as limiting file types and sizes. Use security plugins that scan uploaded files for malware or suspicious content. Store uploaded files outside the web root directory to prevent direct access.
Lack of SSL/TLS Encryption:
- Issue: Without proper encryption, sensitive data transmitted between users and your website can be intercepted by attackers.
- Solution: Install an SSL/TLS certificate on your website to enable HTTPS encryption. Ensure that all login and user data transactions are encrypted. Update your WordPress site’s settings to force HTTPS connections.
Get a comprehensive vulnerability assessment of your WordPress environment with SecureLayer7
Experience peace of mind with SecureLayer7’s comprehensive vulnerability assessment service for your WordPress environment.
Our team of expert security professionals will thoroughly analyze your WordPress site, plugins, themes, configurations, and user inputs to identify potential vulnerabilities and security weaknesses.
By leveraging our state-of-the-art tools and methodologies, we ensure that your WordPress site is protected against potential threats.
Take the proactive approach to secure your WordPress environment today.
Contact SecureLayer7 and schedule your vulnerability assessment. Safeguard your website, protect your valuable data, and stay one step ahead of malicious actors.
Don’t wait for a security breach to happen. Let us fortify your WordPress site and provide you with actionable insights to enhance your overall security posture.
Trust SecureLayer7 for a comprehensive vulnerability assessment tailored to your specific needs.
