
Web Application Penetration Testing Methodology
January 23, 2023
The 10 Best Web Application Penetration Testing Tools In 2023
January 30, 2023
A Gartner report suggesting that the global application security expenditure is estimated to increase from US$5 billion in 2022 to US$7.5 billion in 2023 clearly demonstrates how businesses worldwide are more invested than ever to keep their web applications safeguarded against cyber intrusions.
As the defacto face of your company, these applications are typically data-driven client-server software that helps businesses establish a dominant online presence, provide stellar customer service, and achieve a competitive edge over their market rivals. Web apps accomplish this by leveraging the information they collect through the large volume of user interactions with the application.
This is why regularly assessing their cybersecurity posture should be a business’s utmost priority to protect sensitive information such as their users’ personal, medical, and credit card information. But how does penetration testing come into the picture, and what does web application penetration testing have to do with it? Well, keep reading to gain an in-depth understanding of how cybersecurity plays an important role in uplifting businesses globally.
This article aims to provide SMEs that frequently encounter challenges in detecting vulnerabilities and flaws in their web applications with an in-depth guide on penetration testing, how it’s conducted, and its irrefutable benefits.
Through this informative read, we will walk businesses through a proactive, comprehensive security assessment process that will be instrumental in detecting and mitigating system compromises before cybercriminals can exploit them.
What is Web Application Pentesting
Web apps are programs stored on a remote server and provided to customers through an internet browser’s interface. They are vital for businesses to achieve industry standards, operate efficiently, and enhance customer service. The sensitive data they collect, manage, and stow makes them a favored target amongst cyber criminals looking to achieve a quick payday.
Penetration tests or pen tests are a widely used security assessment technique where a cyber security professional performs a self-inflicted simulated attack on an application’s internal and external networks to weed out underlying flaws, threats, and vulnerabilities. Its primary purpose is to uncover and exploit these vulnerabilities to steal sensitive company data using the same tactics a cybercriminal would.
By doing so, businesses can apply remediation efforts to strengthen the client’s security posture before allowing malicious actors to discover and exploit the exposures themselves.
Regular penetration testing is also helpful in fixing misconfigurations, bugs, and flaws present early in their web application development cycle before a public launch. These assessments are essential to proactively combat emerging attack vectors and threats that the increasingly sophisticated cybercriminal’s may employ to target your business.
Web Application Penetration Testing Methodology
Now that we have covered penetration testing, let us look at its methodologies, security frameworks, and use cases.
1. Security Frameworks
Security frameworks are guidelines detailing documented vulnerabilities, policies, and procedures that testers can leverage to maintain security controls, reduce exposures, and manage risk. Testers must select the right frameworks for their web app pentest methodology, as it affects its outcome and success.
Let us take a look at some of the most effective and widely used security frameworks:

Open Web Application Security Project (OWASP)
The Open Web Application Security Project (OWASP) is one of the most popular security frameworks for web app penetration testing. It is an open-source security testing methodology focusing on cybersecurity awareness and web application security. OWASP offers distinct types of standards targeting web application security.
– OWASP Top 10
The OWASP Top 10 is a published document that provides awareness for developers and web application security of the most commonly exploited security vulnerabilities. It serves as an essential standard for most developers to practice safe coding.
– OWASP Code Review
It is a technical book containing the best code review practices for software developers, management, and security professionals to promote a secure product development lifecycle.
– OWASP Developer Guide
The OWASP Developer Guide is a well-documented guide detailing the best practices, recommendations, and roadmaps to ensure secure coding.
Open-Source Security Testing Methodology Manual (OSSTMM)
Created by the Institute for Security and Open Methodologies (ISECOM), The Open-Source Security Testing Methodology Manual (OSSTMM) is a means for implementing and documenting penetration tests.
OSSTMM helps guide SMEs with the essential cybersecurity best practices, what vulnerabilities to look for , and how to interpret the results.
As a customizable and adaptable framework, businesses should adjust the OSSTMM framework to suit a web application’s unique security requirements to stay optimally protected from data theft and cyberattacks.
It is worth noting that OSSTMM 3.0 is the latest version, with all prior versions deemed obsolete, so ensure you use its latest iteration.
PCI Data Security Standard (PCI DSS)
Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards devised for e-commerce organizations that receive, process, store, or transmit sensitive credit card data to do so securely. PCI DSS helps testers determine how attackers can gain unauthorized access to a target application’s files, logs, and payment data.
For a web application to achieve PCI DSS compliance, a tester must audit its security posture to determine if it upholds the PCI DSS requirements for scope, vulnerability management, methodologies, and segmentation.
PCI DSS mandates that penetration tests must be conducted through manual and automated scanning at least once a year or when the business makes significant security changes. It requires testers to attempt to exploit or bypass the security features of system components.
Upon completion, PCI DSS compliance requires comprehensive documentation and reporting of all results to the client. A PCI DSS report must contain information on all verified vulnerabilities and accompanying details on their risk and exposure levels.
2. Test Cases
Web application penetration testing helps identify and mitigate a broad range of attacks. Here are some of the most common use cases of web app pen tests:
Password Cracking
This is a commonly used technique where a cybercriminal illegally obtains sensitive passwords using an application, an algorithm, or several other methods to steal sensitive data, including company resources, credentials, and credit card information.
SQL Injection
SQLi is a web application vulnerability where an attacker injects malicious SQL queries into a data-driven target application to gain unauthorized access to its database to download, modify, and delete sensitive data.
The SQL injection can also lead to denial-of-service attacks or compromise the back-end infrastructure.
Cross-site Scripting (XSS)
Cross-site Scripting is a technique where attackers inject malicious scripts onto a target web application to hack or infect the systems of unsuspecting users who interact with it.
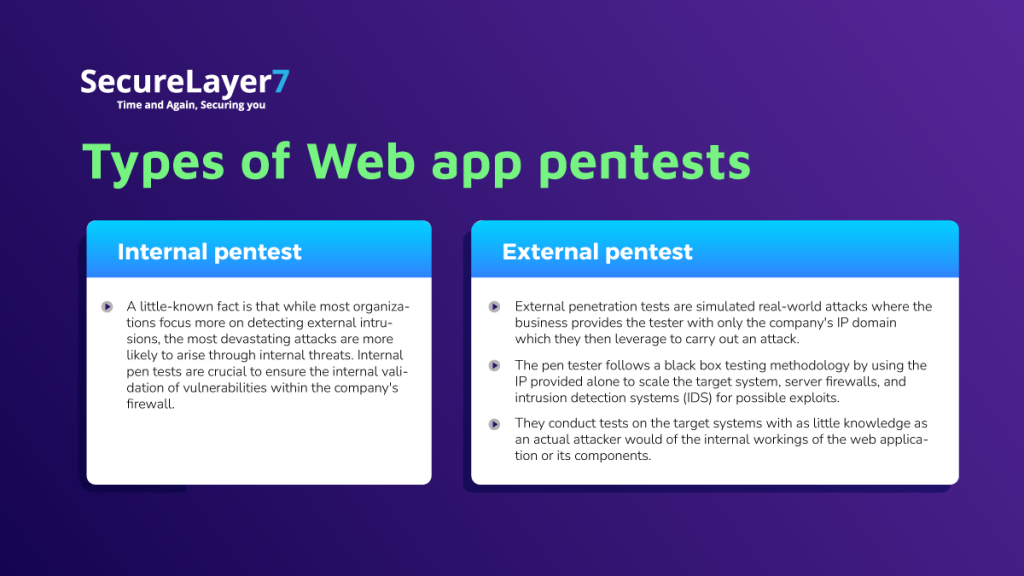
Types of Web App Pentests
There are two ways in which a tester conducts penetration tests. They are:
Benefits of Web Application Penetration Testing
The primary benefits of regular web application penetration testing are:
Ensure Compliance
Penetration tests enable your business’s transactions, processes, and functions to stay compliant and up-to-date with the constantly changing data privacy laws and regulations.
They allow companies to pinpoint and remediate functions that are non-compliant with the current industry standards and apply strong security measures that protect sensitive information.
Interestingly, some industries require businesses to perform penetration tests on their web applications to achieve compliance.
Assess Risks
When launching your web applications, it is common to have security flaws, technical problems, misconfigured firewalls & DNS servers, UX issues, and other weaknesses. Before launching the defective product to the public, developers can leverage penetration tests to identify and mitigate all weaknesses and security concerns in the target application’s infrastructure.
This practice ensures businesses release an ironclad version with minimal security or data leak concerns that is less likely to be attacked.
Safeguarding Sensitive Data
The dark web is a significant marketplace where bad actors use cryptocurrency to buy and sell stolen data. This illegal data marketplace is the primary motivation behind attacks purportedly targeting web-based data-driven applications that hold invaluable information about businesses and their users.
Another top motive that drives attackers to steal web application data is its value to a business’s competitors. Subjecting your web application to a comprehensive penetration test is crucial to managing and curbing data leak risks that could affect the company and its reputation. Doing so reduces the application’s attack surface and safeguards its valuable data.
Additionally, the enhanced safety provided by periodic pen tests upholds the company’s reputation as one that values the security of its users data.
The Steps of Web Penetration Testing
Now that we understand the undeniable benefits of web application penetration testing, let us study the various steps a tester typically follows to implement one successfully.
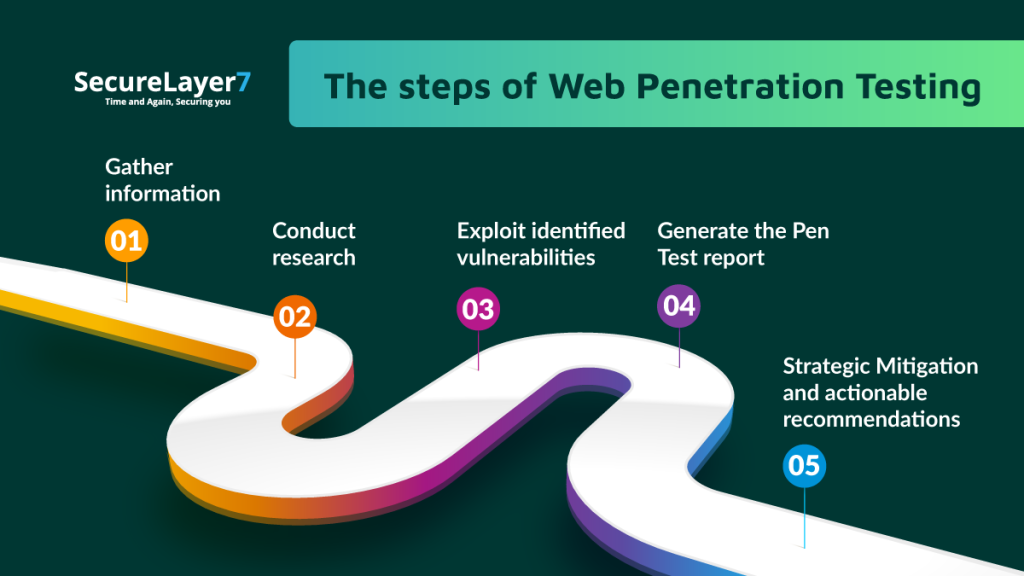
Step 1 – Gather Information
The first step towards a successful pen test is conducting reconnaissance to collect information. Irrespective of the tester’s technique, the end goal should be to derive as much information as possible from the target web application to pinpoint vulnerabilities.
A tester can interact with two sources to gather information and map the network connected to the web application. The actionable information collected from either of the two sources should provide the tester with enough knowledge to formulate their attack strategy and carry out their exploits.
Active Reconnaissance
This type of reconnaissance involves gathering information by interacting directly with the target system through tactics such as network fingerprinting, Nmap web server scanning, Shoden network scanners, or DNS forwarding.
Passive Reconnaissance
When engaging in passive reconnaissance, the tester does not directly interact with the target web application; instead, they comb through internet search engines such as Google to find any relevant information about your business and its web applications.
Nmap, Maltego, TruffleHog, Sublist3r, SpiderFoot, theHarvester, and Wappalyzerand are some of the popular tools used for reconnaissance.
Step 2 – Conduct Research
The raw data from the reconnaissance phase alone is insufficient to carry out a penetration test. The next step is to conduct thorough research on the information gathered in the previous step.
Once completed, the tester should have sufficient details indicating potential security weaknesses, misconfigurations, problematic code, and other threats.
This research allows testers to devise an attack strategy, including how they will leverage the uncovered vulnerabilities and carry out their exploit.
Step 3 – Exploit Identified Vulnerabilities
Once completing the research, it is time to infiltrate and exploit the target web application to steal data the same way an attacker would. After this orchestrated attack, the tester can perform practical risk assessments of each vulnerability.
Several popular pen testing tools are available that effortlessly carry out automated attacks to reveal the presence of common vulnerabilities and weaknesses.
Once the tester selects their preferred tool, they move on to the next step and launch an automated attack on the web application. While the automated penetration test occurs, the tester can simultaneously prepare, plan, and implement more sophisticated manual attacks to show complex security exposures that the automated tools cannot detect.
Such a combination of automated and manual attacks is an effective strategy for conducting comprehensive penetration tests.
Step 4 – Generate the Pen Test Report
For the pen test to be productive, it must be well-documented with supporting evidence and screenshots detailing all results, however minor they may be. This documentation will give the business a comprehensive understanding of the remediation requirements they must fulfill to strengthen their security posture.
This report must include the executive summary, pen test scope & method, vulnerability report, and remediation report. While documenting the technical findings is essential, the tester must make it understandable to business stakeholders with inadequate technical knowledge.
Most professional penetration testers provide a business-oriented report that can be understood by all levels of management and the IT security department to ensure all stakeholders understand the nature of each vulnerability and the mitigation actions required to eliminate it.
Step 5 – Strategic Mitigation and Actionable Recommendations
Once the business has a complete overview of all the findings, it is time to implement the remediation plan. While some threats may have delayed risks, others may immediately threaten application security.
Strategic mitigation allows businesses to address security concerns based on their propensity to cause immediate danger to the web application and its data. By such means, your business can first address the most pressing issues before moving on to others with a comparatively lower priority.
A good recommendation is to conduct retests and function-specific penetration tests to ensure that all loopholes, threats, misconfigurations, and vulnerabilities were, in fact, permanently addressed.
Retesting is crucial because, occasionally, the tester may mistakenly apply incorrect fixes that subsequently lead to the creation of new threats. Retesting can spot and address such instances.
Only when the results of the retests and remediation indicate successful mitigation of all issues or vulnerabilities can the business declare that its data and web application are optimally protected.
However, it is worth noting here that cybercriminals are constantly devising new attack strategies and exploiting unknown vectors to infiltrate unsuspecting web applications. In such a landscape, penetration tests must be conducted as an ongoing practice at regular intervals for businesses and their web applications to remain safeguarded.
Common Tools Used in WAPT
Kali Linux and Parrot Security are ideal and effective operating systems (OS) for web application penetration testing. Some popular tools used are OWASP ZAP, Arachni, Burp Site, Nessus, Nikto, and WPScan testers for dynamic application security testing(DAST), and Snyk Code, Semgrep, SonarQube, and Fortify Static Code Analyzer for static application security testing (SAST).
Finding security vulnerabilities in your dependencies while developing and testing your applications requires tools such as OWASP Dependency Check and Snyk io.
It is worth noting that while automated tools are excellent means to scan and identify the most common vulnerabilities quickly, they have their limitations and are prone to generating false positives.
Only through manual testing can you help find more complex business logic vulnerabilities. Manual testing is also an efficient way to reduce false positives and verify actual vulnerabilities.
To summarize, while automated tools significantly improve the process, an experienced tester employs both methodologies for the best results.
Provide Comprehensive Protection For Your Web Applications With SecureLayer7
SecureLayer7 helps customers spot high-risk web application vulnerabilities such as using components with known vulnerabilities, SQL Injection, Cross-Site Scripting, Broken Access Control, Broken Identification & Authentication, Security Misconfigurations, Sensitive Data Exposures, XML External Entities, Insecure Deserialization, Server-Side Request Forgery, and Insufficient Logging & Monitoring, which may result in severe data breaches within your web applications.
We are renowned amongst SMEs that leverage our penetration testing application to perform and act on continuous pen tests. We additionally help businesses securely maintain their cloud infrastructure by detecting and quarantining vulnerabilities in AWS, Azure, and Kubernetes systems at a reasonable cost.
Our network security service ensures that your corporate infrastructure complies with industry regulations and follows the best network security practices reducing the risk of attacks on devices and servers.
SL7 provides full security service to your web application with automated and manual testing to identify and remediate all risks challenging your application security. Contact us to find out how we identify and mitigate all your web app vulnerabilities.
Summary
Web apps and the sensitive data they operate on are vital for businesses to achieve industry standards, operate efficiently, and enhance customer service. In recent years, these applications have made them a moving target amongst sophisticated cyber criminals looking to achieve a quick payday. This informative read aims to provide readers with an in-depth guide to penetration tests, how they work, the tools involved, and how businesses leverage them to identify vulnerabilities and strengthen the security of their web applications.
FAQ
What is a web application penetration test?
A web application penetration test is a type of security testing where an authorized tester simulates real-world attacks on a web application to identify vulnerabilities and weaknesses that could be exploited by malicious hackers.
What are the five stages of web penetration testing?
The five stages of web penetration testing typically include reconnaissance, scanning, gaining access, maintaining access, and covering tracks. These stages involve systematically probing and testing the web application’s security measures to identify potential vulnerabilities and weaknesses.
What are the three types of penetration tests?
The three types of penetration tests are black box testing, white box testing, and grey box testing. Black box testing involves testing without any prior knowledge of the web application, white box testing involves testing with full knowledge of the web application’s architecture and code, and grey box testing involves testing with partial knowledge of the web application.
What are the different penetration testing tools?
There are various penetration testing tools available, such as Metasploit, Burp Suite, Nmap, Nessus, and OWASP ZAP, that are commonly used by security testers for identifying and exploiting vulnerabilities in web applications.
What are the types of web security testing?
The types of web security testing include vulnerability scanning, security code review, access control testing, authentication and authorization testing, session management testing, error handling testing, and input validation testing. These tests help identify potential security loopholes in web applications and ensure their overall security posture.


