Password Reset OTP Bypass Critical Vulnerability in YesBank Banking Application
October 20, 2016
OWASP TOP 10 Cross-Site Request Forgery #8 – About CSRF Vulnerability and Fix
November 22, 2016
On Tuesday Joomla announced the security for the critical Joomla vulnerability which allows attackers to create account CVE-2016-8870 and escalate the privilege CVE-2016-8869 due to inadequate checks on the registration code. We have mentioned below the cause of the exploit and fix of the issue along with the demonstration of the proof of concept for the exploit.
Understanding the Joomla Security Patch
Upon analyzing the patch, I found that it was easy to spot the fix provided by the Joomla developers. They just removed the register function in the user class. There were two register functions in vulnerable Joomla versions, namely registration.register and user.register. The fix removed the user.register function.
The registration.register function has the code to check whether the user registration is enabled or disabled, whereas user.register does not perform the check.
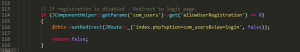
This allowed the creation of an account when user registration is disabled by calling the user.register function with appropriate parameters.
Analyzing the user.register function :
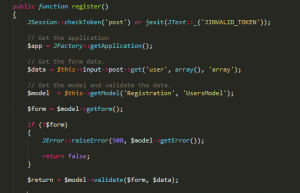
This function takes the user input data in the form of an array i.e user[key] = Value, the whole array is stored in $data variable. Then it performs validation of user-supplied data against the form variables.
In order to exploit the first vulnerability, the user.register function should be called with user associated array.
Proof of concept for Creating a Joomla Exploit user account
The exploit consists of two things. First, calling the user.register function, and second, passing all the variables in user[key] = value array.
A call to the user.register :
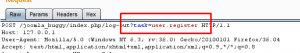
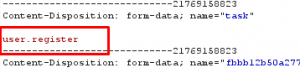
The parameters to be stored in the database are passed as an array of users.
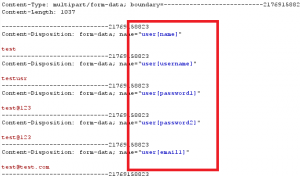
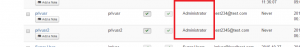
Upon successful joomla exploitation, a new account is created .
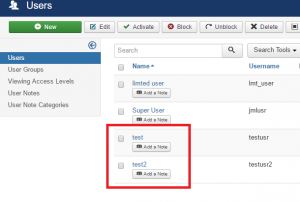
Proof of concept for Elevated Privileges of Joomla user account
The validate method in the user.register does not validate or filter input data against the form properly so any number of extra parameters can be passed and they get processed and stored in the user’s database.
privilege escalation can be achieved by passing extra parameters with the previous exploit as shown below :
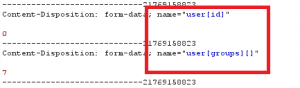
The group id 7 sets the user in the administrator group upon creation.
Uploading PHP Backdoors Using Joomla Extensions
After the creation of the user account with elevated privileges, the attacker can use the existing features of Joomla to upload the PHP backdoors. Joomla allows admin users to install the extension packages on the Joomla website. An attacker could use this feature to upload the PHP backdoors on the website and gain access to the server. Further, an attacker could also try to elevate the limited Linux user to gain full access to the system.
Conclusion
To keep your Joomla website secure, you will have to update the Joomla version to the latest one. You can download the latest version from here. If you’re seeking help to Patch this vulnerability, you can always contact at info[at]securelayer7.net.
Reference:
[1] https://www.joomla.org/announcements/release-news/5678-joomla-3-6-4-released.html
