BlueBorne- the lethal attack to take over your devices
September 13, 2017
OWASP TOP 10: #4 | Insecure Direct Object Reference Vulnerability
September 20, 2017Reverse Engineering is an fascinating art of playing with low level code.
In this article, we will see a hands-on tutorial for patching an exe file to accept any serial key!
Tool for use:
● Ollydbg (http://www.ollydbg.de/)
● A crack-me for demonstration. You can download loads of crack-mes for hands-on practice from http://crackmes.de/
A crack-me is a small program designed to test a programmer’s reverse engineering skills. They are programmed by other reversers as a legal way to “crack” software.
Let me show you how a simple crack-me exercise, which has a particular serial key (obviously unknown to me) can be patched for making it accept any serial key)
Any application can be patched/ cracked in multiple ways. Some of the situations I have worked on in the past included:
1) Application logic patched to accept any serial key
2) Use breakpoint-analysis to step through the application and find a serial key from inside the debugger windows
3) Decipher the serial-key generation and create a key-generator to produce infinite product keys
As you can see here is a sample crack-me, “passwordapp.exe”. Upon clicking the application, it shows us to enter a password for access.
Sample crackme
Entering random password: 1111, we try to test the app
Random key
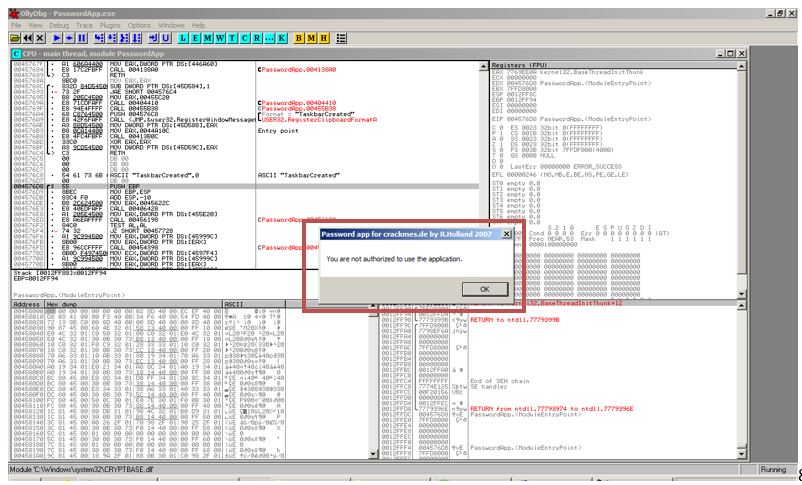
As normally expected, we will get a warning due to wrong password: Not authorized.
Now to patch this exe, we open “Ollydbg” to fire up the same app inside the debugger to analyze it.
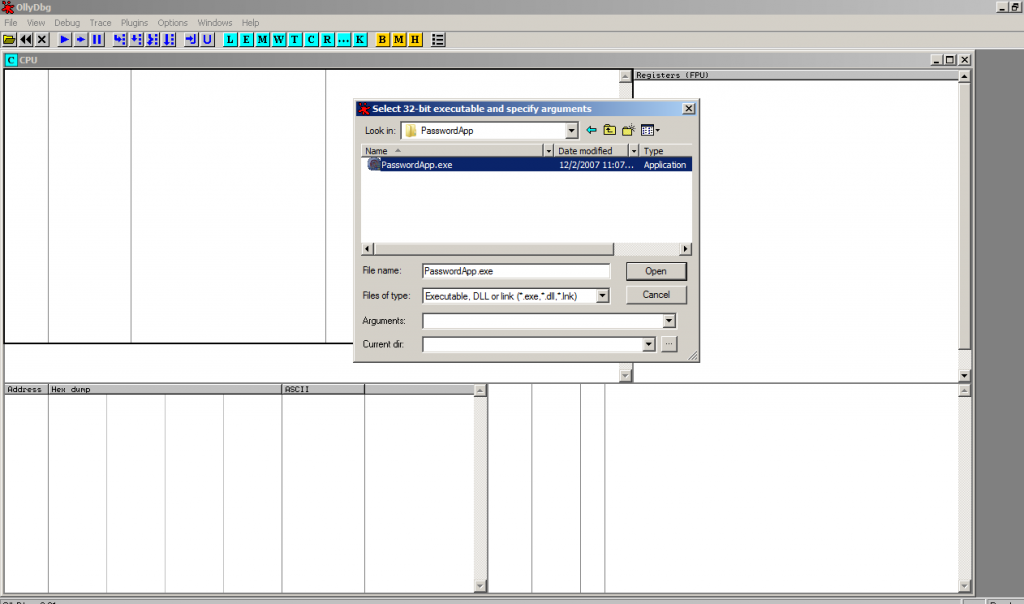
Ollydbg initial screen
For beginners, here is a short intro to ollydbg, to help you get familiar with it. 4
1) CPU Window : The most frequent workplace where we will be working on as a step by step flow for code analysis
2) Registers: The part of the window which contains the 32bit/ 64bit registers, and flag informations
3) Hex Dump: Simply said, it shows the hex representation of data
4) Memory Stack: The stack display pane showing comments, and the address of memory.
Click File /Open and the above box will pop up, select the appropriate directory and launch the app inside the debugger.
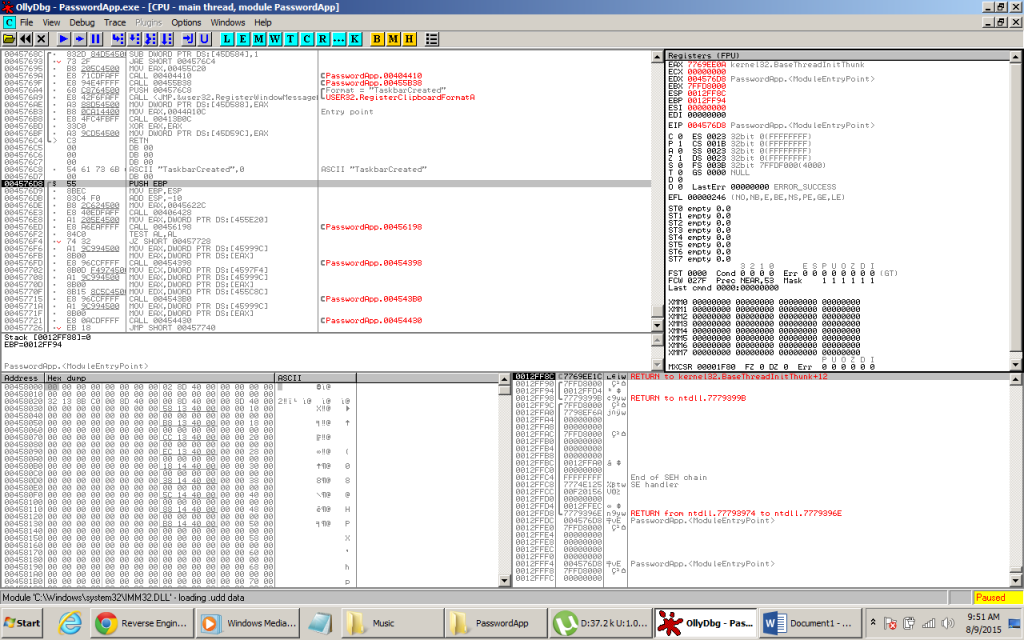
Parts of Olly
Once the application loads inside the debugger, we can the app inside the windows with all the assembly instructions visible.
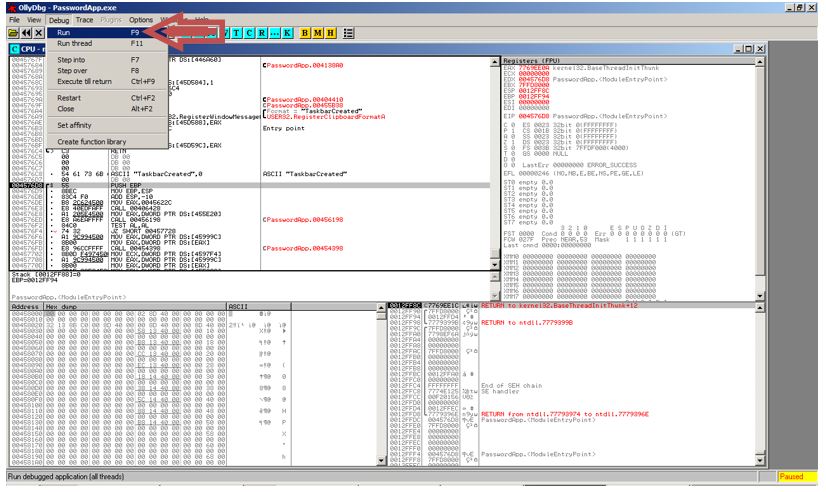
Setting Debug
As a part of our inspection, we need to run the application again, but this time inside the debugger to inspect and analyze its responses. Go to debug menu -> and Click on Run. The application will again run inside Ollydbg. As usual the application is waiting for the user input for password.
To test the application logic, we will again enter a random password as input.
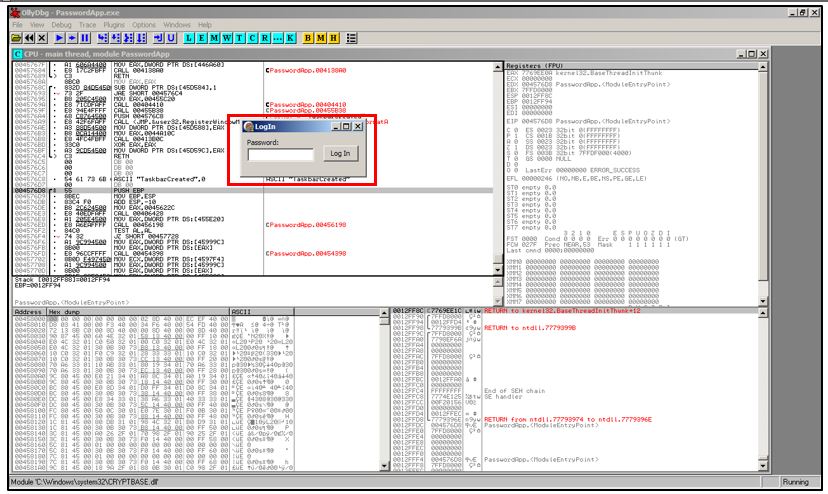
Loadup exe in olly
Loadup exe in olly
As soon as we again enter a random password, we are greeted with the same error as before.
In simple applications such as these, often THE KEY TO REVERSING IS FINDING THE ERROR MESSAGE!
Here just note the error message, which says we are unauthorized to use the application. Once we close the error message, just right click inside the console window and Right click -> Search for-> All referenced strings. Following this step is the reason, since now we will be hunting the error message, which we just encountered.
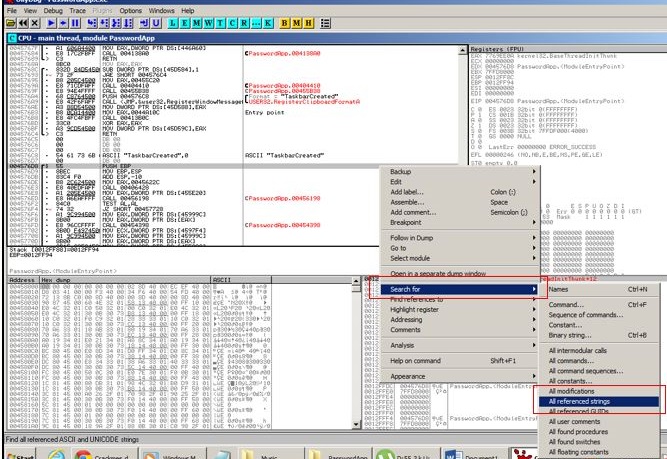
Searching for Error String_1
Searching for Error String_2
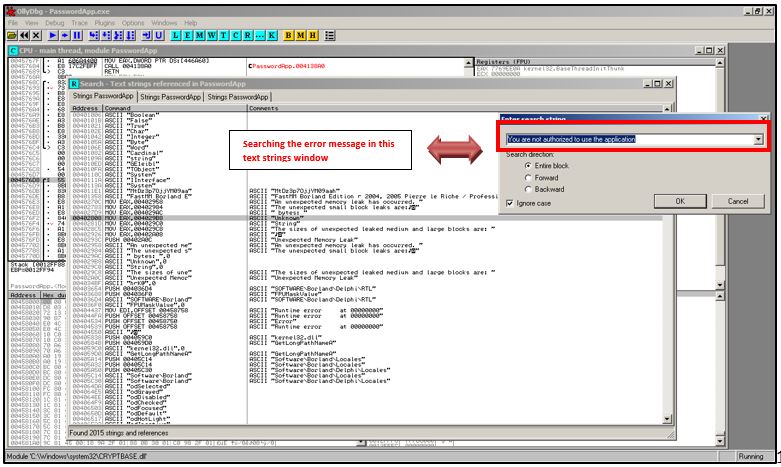
On clicking all reference strings, we will get a text box, where we will type the error message.
Once done, we get a window where all the ASCII strings of the application are present.
Once we double click on message finding the window, we will be taken back to the main console. Observing closely, go a little above the line of the error message looking for a jump instruction.
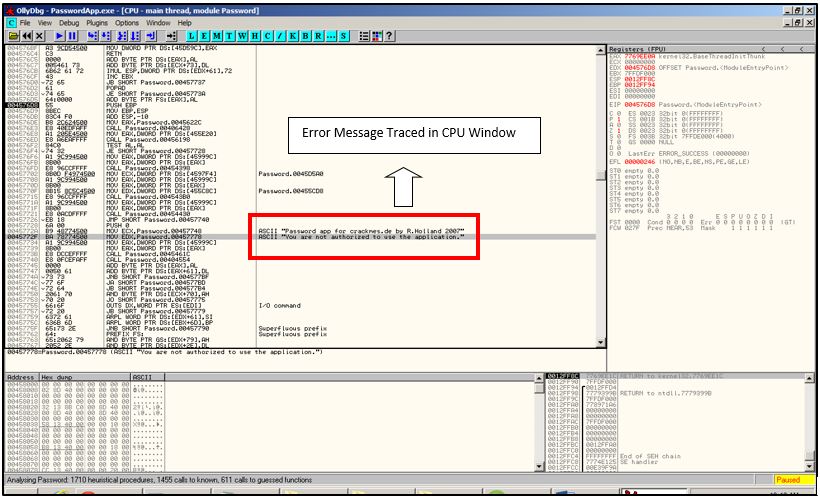
Error Message
Here you can find the following instruction: “JE SHORT Password.00457728”
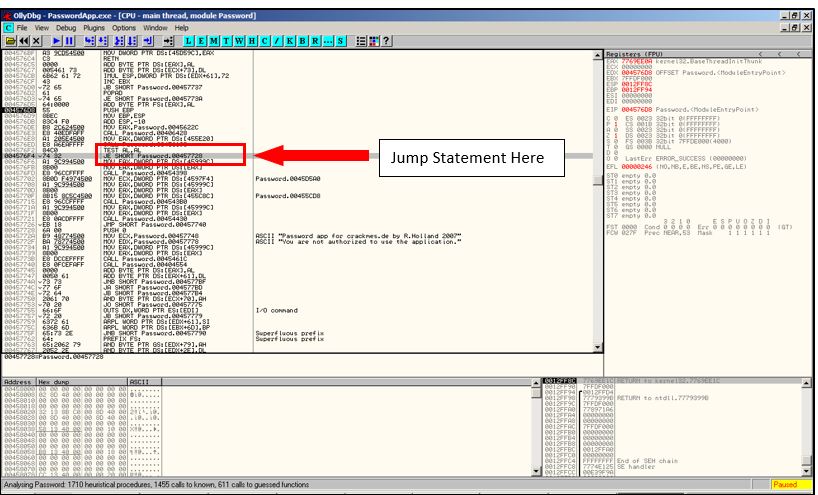
Jump Statement
JE is a conditional jump which means that if the condition is right then it will jump to 00457728,which leaves us to the message “You are not authorized to use the application” and if the condition is not satisfied it just continues reading the code
Now we finally can remove this message, our approach being:
•Fill it with NOP’s(No Operation) and make this conditional jump not work
•Change JE SHORT Password.00457728 to JNE SHORT Password.00457728, JNE(Jump If Not Equal) means that if the password is correct it will give you the bad message and if the password is incorrect it will give you the correct message.
Here, I am changing the JE to JNE by double clicking on the instruction line.
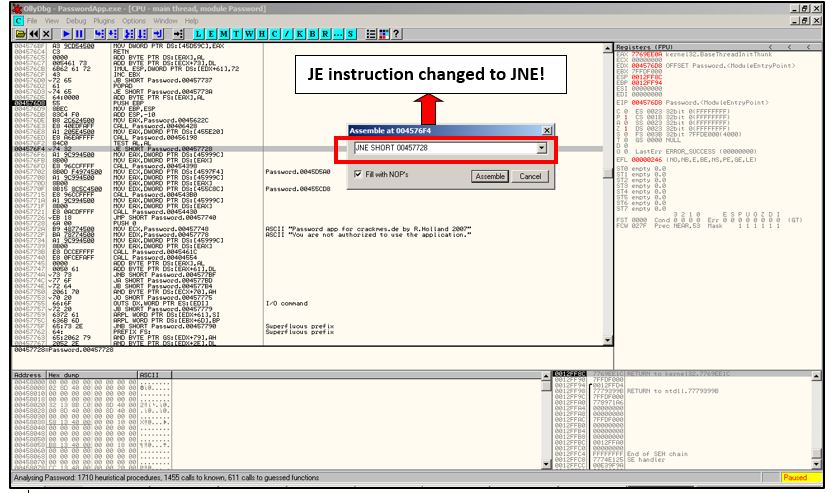
Set Jump Instruction
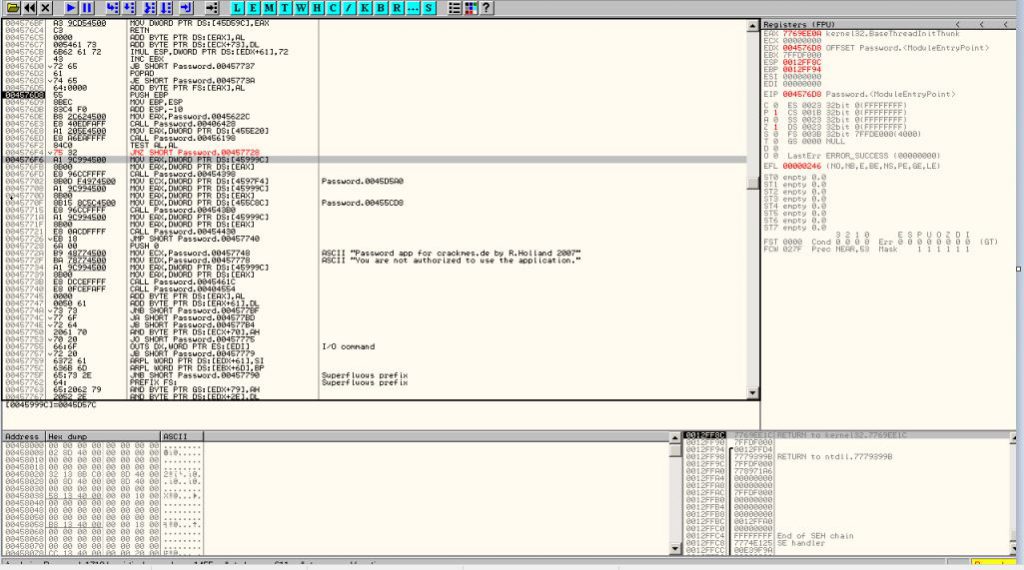
Finding Jump Instruction
Again the application will ask us to enter the password, but this time the 1111 password which was wrong, will be ignored by the application about its authenticity thus it will directly jump to the “you are authorized” section demonstrating successful patching of the app. Hit assemble and re-run the app.
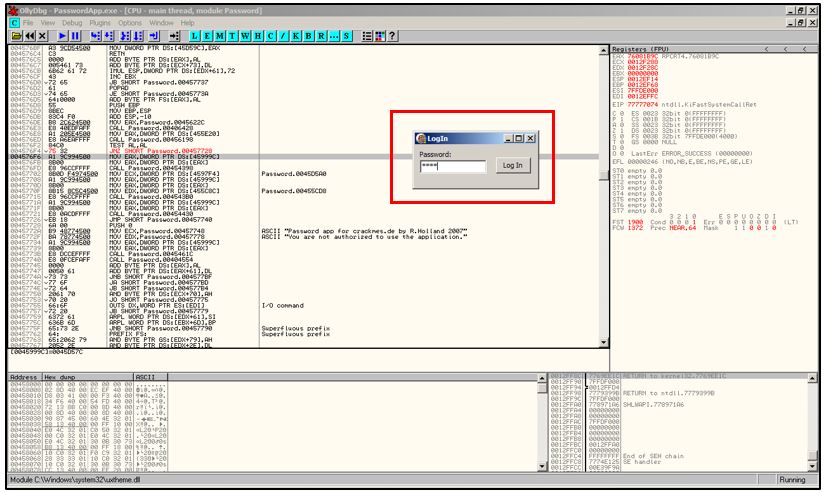
Testing Random Serial
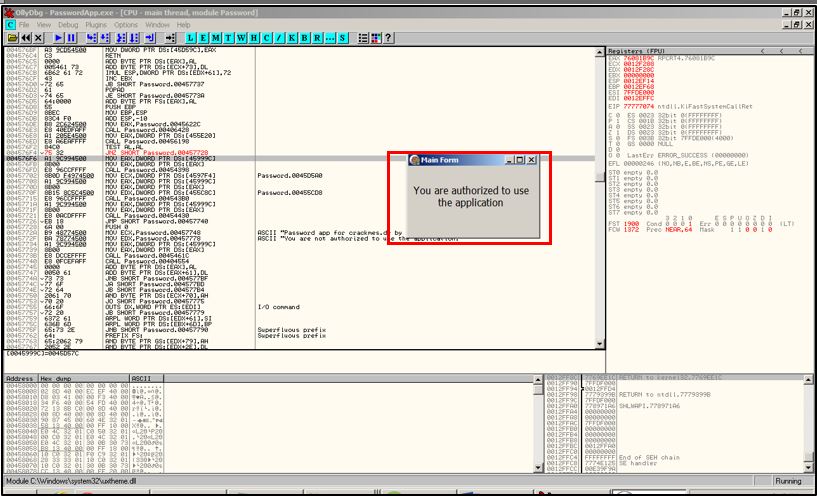
Successful Patching of crackme
Now to permanently modify the app to accept any password, simply save the modified exe.
Right click on code window-> “copy to executable” -> “All modifications” -> Copy all-> “Save file”.
So that’s it, we have patched a simple application.