Organizations spend serious time and money trying to protect their most important systems. Firewalls are in place. Tools are deployed. Playbooks are written. And yet, breaches keep happening—not always because defenses are missing, but because attackers find paths no one was actively watching.
That gap is hard to ignore. It’s not that teams don’t care about security. It’s that many defenses are tested in isolation, under ideal conditions. They rarely show what happens once an attacker gets a foothold and starts moving quietly through the environment. That’s where blind spots tend to live.
Red team assessments exist to surface those blind spots. They go beyond traditional penetration testing by simulating how real attackers operate over time, not just how vulnerabilities look on paper.
This guide looks at red team assessments from the ground up: what they are, why they matter, how they differ from purple team exercises, how they work in practice, the phases involved, real-world examples, and what to consider when choosing the right red team partner.
What is Red Team Assessment?
A red team assessment is designed to test more than individual security controls. It evaluates how well an organization’s people, processes, and technology hold up under sustained, real-world attack conditions. Instead of reviewing policies in isolation or scanning for known weaknesses, red teams actively challenge an organization’s security posture as a determined adversary would.
Red teams are made up of ethical hackers who think and operate like real attackers. They design attack scenarios that reflect how modern threats unfold—moving laterally, abusing trust relationships, and quietly bypassing defenses rather than triggering obvious alarms.
The goal is not simply to gain access, but to observe how security teams detect, respond, and contain a credible threat over time. This approach often exposes gaps in visibility, coordination, and incident response that traditional testing fails to surface.
While red teaming is often compared to penetration testing, the two serve different purposes. Penetration tests focus on identifying and validating specific vulnerabilities. Red team assessments take a broader view, examining whether an organization can withstand a full attack lifecycle.
The tools and techniques may overlap, but red teaming is structured to reflect how attackers actually operate in today’s environments.
Modern red team exercises are also shaped by frameworks such as MITRE ATT&CK, which map attacker behaviors across tactics and techniques. While elements like lateral movement and defense evasion have existed for years, these frameworks bring consistency, realism, and strategic depth to red team operations.
As a result, red teaming has become a more effective way to measure real-world security readiness—not just technical weaknesses, but an organization’s ability to recognize and respond to them.
How Does a Red Team Assessment Work?
A Red Team assessment is an offensive security testing methodology that mimics hackers tactics to test defenses. They use similar adversary tools and emulate their methodology of sending phishing emails to breach networks or systems. Red team experts identify gaps before malicious actors could exploit them.
Based on the outcome of the attack, detailed reports follow that provide actionable insights and remediation measures to strengthen security. .
A red team assessment follows a systematic and structured process running into various phases to simulate a real-world cyber threat scenario.
Red Teaming vs. Other Security Assessments
A. Red Teaming vs. Penetration Testing:
Though red teaming and penetration testing are often used interchangeably, the approach and methodology differ.
Penetration testing, or PT, is a tool-assisted manual assessment that evaluates how far a malicious attacker will penetrate an organization’s IT network by exploiting vulnerabilities. Pentests typically involve testing, systems, web apps, mobile devices, etc.
Unlike red teaming, pen testing is not a stealthy process. The organization and security teams are aware of the testing. Plus, pen testers’ approach is to find as many security vulnerabilities as possible.
A red team assessment is a stealthy way of conducting tests. Red teamers employ a team of ethical hackers who work silently and secretly for an extended period. This approach aims to understand target systems and gain an in-depth understanding of the people, technology, and environment.
They adopt numerous techniques, such as malicious file payloads, RFID (Radio Frequency Identification) cloners, and hardware trojans. Red teamers may use social engineering or plant hardware trojans. In short, they can adopt any methodology to intrude into the system and exploit opportunities.
| Parameters | Penetration Testing | Red Teaming |
| Time | Typically shorter, ranging from days to a few weeks | May last up to over a month |
| Objective | Identifying exploitable vulnerabilities and risks | Testing detection, response, and security culture |
| Tactics | Uses tailored methodologies for different scopes and targets | Real-world tactics, social engineering, and data exfiltration |
| Outcome | Identification of vulnerabilities with remediation advice | Insights into overall security posture with recommendations |
| Cost | Generally cheaper due to limited testing time. | Often more expensive due to longer duration and techniques |
| Nature | Non stealthy | Stealthy, like a real-world attack scenario |
B. Red Team vs Blue Team vs Purple Team
In offensive security testing, these three specialized teams work together to improve organization’s cyber defense capabilities:
Red Team simulates attackers’ mindset and tactics. It conducts penetration tests whose scope is authorized to identify vulnerabilities. They mimic real adversaries to test defenses without causing any damage. Their purpose is to detect weaknesses before malicious actors exploit them.
Blue Team acts as defenders whose primary task is to monitor systems, identify intrusion and respond to security systems. They do so by implementing security controls, analyzing logs, and creating an incident response plan.
The purple team’s role is to bridge the gap between red and blue teams. They collaborate with both the red team and blue team. Their objective is to interact with both teams to create a feedback loop to strengthen the organization’s defenses.
Different Phases of Red Team Assessment
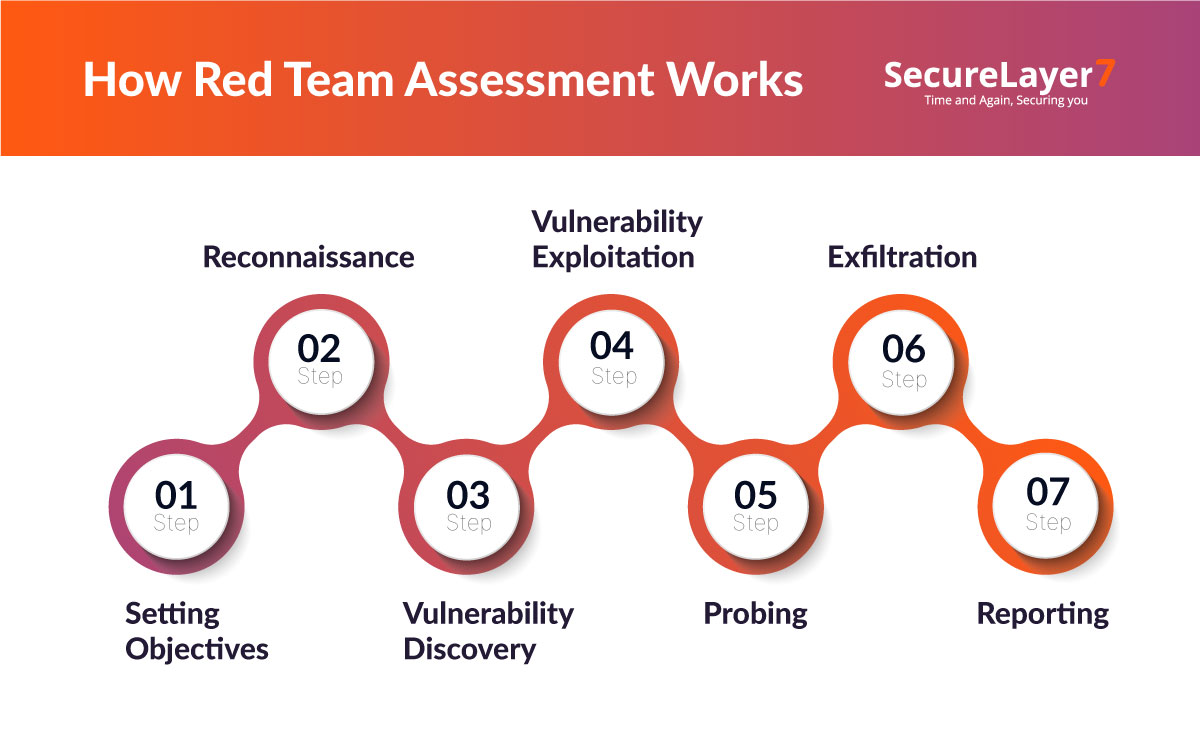
1. Establish Scope And Objective: The initial phase includes planning and goal mapping. It ensures all stakeholders align on the process’s rules and goals.
2. Reconnaissance: In this phase, red teamers gather information about the organization’s IT network, its technology, infrastructure, and employees. For example, red teamers utilize social engineering tactics to scrap employees’ email addresses from LinkedIn. Then, they create phishing emails to test the organization’s email security.
3. Vulnerability Discovery: Based on the reconnaissance stage findings, now red teamers identify vulnerabilities and potential attack paths through active testing. For example, after reconnaissance, security teams find that the company’s system has an outdated version of Apache Struts on their web servers. Based on this finding, the red team might design a test for CVE-2017-5638 vulnerability that involves using specially crafted HTTP headers.
4. Vulnerability Exploitation: After identifying vulnerabilities, the red team attempts to exploit them to gain access to the target’s systems using safe exploitation techniques to bypass security restrictions.
5. Privilege Escalation: At this stage, the red team analyzes how far they can move laterally within the network. The objective is to understand the network’s depth and identify further opportunities to achieve their objectives.
6. Exfiltration: In this phase, the red team attempts to extract sensitive information from the target environment while avoiding detection. For example, once a red team gains access to finance department networks, red teamers may encrypt customer financial records and slowly transfer them via DNS tunneling technique.
7. Reporting: This is the last stage. Now, the red team prepares a detailed attack narrative, executive summary report and a comprehensive summary report. Besides, the report also includes vulnerabilities discovered, how they were exploited, and actionable recommendations to strengthen the incident response capabilities.
Methodologies Used in Red Teaming
A. Social Engineering Attacks
Red teams craft convincing communications that manipulate trust to gain unauthorized access to systems or information through deception rather than technical exploits.
Example: A red teamer wearing contractor attire and carrying maintenance tools convinced front desk staff to provide temporary access to a restricted floor, where they photographed sensitive documents left on desks after hours.
B. Network Exploitation
Techniques that bypass network security controls or intercept communications between legitimate systems to capture sensitive data.
Example: Red teamers deployed a rogue device on an internal network segment that intercepted unencrypted traffic between legacy systems, capturing administrator credentials that were transmitted during routine maintenance procedures.
C. Web Application Attacks
Inserting malicious code or commands into application inputs to manipulate backend systems into performing unintended operations.
Example: A red teamer inserted JavaScript code into a customer support ticket that executed when viewed by administrators, capturing their session cookies and granting the team access to the support portal’s admin functions.
D. Cloud & Identity Attacks
Targeting weaknesses in cloud environments to access hosted applications, data, or administrative capabilities.
Let’s understand this with an example: Example: Red teamers identified unsecured storage buckets through automated scanning, discovering database backups containing unencrypted credentials that provided access to the organization’s payment processing environment.
Industries That Benefit Most from Red Teaming
A. Financial Institutions
Financial institutions managing trillions of dollars in assets often require comprehensive and robust testing for security. Red teaming will test transaction systems for vulnerabilities, help to minimize risk of fraud, identify compliance issues, and establish customer trust against increasingly more sophisticated transactions in digital banking.
B. Government And Defense
Government entities find themselves being targeted by nation-state attackers for exclusive access and classified information. Red teaming can evaluate defense against and resilience to advanced persistent threats, associated with detecting and protecting secure communication channels, and validating protection of critical infrastructure in the conduct of operations that are a matter of national security.
C. Healthcare And Critical Infrastructure
Healthcare providers must protect sensitive patient data and life-critical systems. Red teaming will facilitate protection of parts or systems which are designated as critical, necessary continuity in essential services, protections against ransomware attacks on medical devices, compliance and adherence to standards, fortification of attacks on public access and associated security, while ensuring reestablishing services and continuity in essential public infrastructure.
D. Technology And SaaS Companies
Technology companies protect valuable intellectual property and customer data. Red teaming will test vulnerabilities before releasing products, validate security in vulnerable cloud infrastructures, and evaluate defense against supply chain attacks on widely-used software programs.
Benefits of Red Team Assessments
In-depth analysis of security posture : Red team assessment allows organizations to identify hidden weaknesses in their technology, people, and processes. Based on the evaluation, CISOs can take a fresh look at the internal security scenario and find practical solutions to the problems.
- Enhanced security:Red teams comprise cybersecurity experts who are equipped with the expertise to handle the most modern and sophisticated threats. This enables you to bolster security preparedness and eliminate the chance of costly breaches.
- Increased ROI: It maximizes the return on the investment made in securing an organization by analyzing how well-equipped the security system is, helping to avoid millions of dollars of losses after a breach.
- Efficient prioritization: Red team tactics can help prioritize vulnerability remediation, cybersecurity measure implementation, and security expenses.
- Improved compliance: Red team analysis allows companies to view weaknesses critical to regulatory compliance and fix them as soon as possible.
- Identifying security gaps: Red teaming simulates real-world attacks to uncover hidden vulnerabilities. It allows organizations to plug security gaps before they are exploited by attackers.
- Strengthening incident response:Red team exercises evaluate and enhance incident response capabilities by simulating attacks. It improves detection times and response strategies. It optimizes cybersecurity resilience and readiness.
- Improving security awareness: Red teaming increases employee awareness of potential threats, reducing human error and enhancing overall security posture through training and simulations, fostering a culture of vigilance and security.
Different Phases of a Red Teaming Assessment
Every red team engagement is different by design. A fixed methodology or reused playbook cannot reflect the realities of distinct business models, technical environments, or threat profiles. For this reason, the approach must be adapted to the organisation’s context and the outcomes it actually cares about.
This level of customisation ensures attack scenarios mirror credible, real-world threats rather than hypothetical risks. It also ensures that findings are usable—grounded in how systems, processes, and teams behave under pressure, not how they are expected to behave in theory.
1. Planning and coordination
The planning phase determines whether a Red Team exercise delivers insight or simply activity. Most failures in Red Teaming can be traced back to weak alignment at this stage.
This phase involves two primary groups: the Control Team and the Threat Intelligence Team. The engagement begins with a pre-launch meeting between the provider’s sales team and the client’s designated stakeholders.
The objective is practical alignment, not formal onboarding:
- Understand the organisation’s risk drivers, regulatory exposure, and recent security concerns.
- Define scope precisely, including exclusions that protect critical operations.
- Agree on timelines, duration, escalation thresholds, and safe-guards.
- Establish the Rules of Engagement (ROE), covering legal approvals, incident handling, and stop conditions.
In the days following this meeting, the client formally nominates its Control Team and shares operational details needed to maintain continuity during the assessment. This typically includes emergency contacts, blackout periods, and systems that must not be disrupted.
A kick-off meeting is then held to align technical and operational expectations. This session has two specific goals:
- Infrastructure and environment briefing: The Control Team provides a clear, working overview of the environment—identity systems, authentication flows, network segmentation, SaaS dependencies, internal tooling, and third-party integrations. The intent here is to eliminate assumptions, not document everything.
- Definition of attack objectives: The Threat Intelligence Team translates business risk into explicit attacker goals, such as:
- Gain access to proprietary source code repositories used in active development pipelines
- Compromise executive or board-level email accounts to simulate targeted espionage or fraud
- Exfiltrate sensitive documents related to R&D, pricing, or strategic planning
- Achieve domain-level privileges within Active Directory to assess blast-radius and lateral movement controls.
This preparation phase ensures the assessment is anchored in outcomes the organisation actually needs to test.
2. Threat Intelligence and risk modelling
This phase connects context to execution. It involves the Control Team, Threat Intelligence Team, and Red Team, and focuses on transforming organisational knowledge into realistic attack paths.
Using information provided during planning, the threat intelligence team creates a structured report that typically includes:
- Identification of high-value assets: Critical business functions, sensitive data stores, core applications, and supporting infrastructure whose compromise would cause measurable operational, financial, or reputational damage.
- Initial exposure and weakness analysis: Early identification of potential attack surfaces based on architecture choices, identity models, integration patterns, and technology stacks,highlighting areas where attackers are most likely to succeed.
- Threat actor modelling: Selection of attacker profiles relevant to the organisation, including ransomware operators, data-theft groups, or financially motivated actors, along with their common entry points, dwell time patterns, and objectives.
- MITRE ATT&CK alignment: Mapping anticipated techniques, tactics, and procedures across the attack lifecycle, clearly linking each phase to specific objectives such as persistence, lateral movement, privilege escalation, or data exfiltration.
3. Validation and refinement of scenarios
An interim review meeting is held to challenge and refine the proposed scenarios. During this session:
- Unrealistic assumptions are removed
- Environmental constraints are factored in
- Attack paths are adjusted to reflect operational realities
The report serves as the authoritative reference for the Red Team during execution and ensures scenarios reflect plausible adversary behaviour.
4. Red Team test execution
This phase is where planning is tested against reality. The Red Team executes the attacks, while the Control Team ensures adherence to the ROE and operational safety.
Before testing begins, the red team prepares a detailed Red Team Plan, which includes:
- Attack scenarios and execution flow
A chronological breakdown of each scenario, including decision points, dependencies, fallback paths, and clearly defined success criteria tied to business objectives. - Leg-ups and contingency paths
Pre-approved mechanisms that allow progress when tests stall due to time limits, defensive controls, or environmental constraints—ensuring learning continues without violating scope.
This plan is reviewed with the Control Team to confirm alignment with objectives, timelines, and escalation procedures before execution begins.
Once approved, the Red Team conducts the attacks as defined, adapting tactics where necessary to maintain realism. Throughout this phase:
- Key milestones are communicated to the Control Team
- Operational risks are escalated immediately
- Every action, outcome, and workaround is recorded
Both successful and failed attempts are documented, as failures often reveal the most valuable defensive insights.
At the conclusion of testing, the Red Team produces an interim report detailing:
- Actions attempted and their outcomes
- Access achieved across systems and identities
- Objectives met, partially met, or blocked
This report is reviewed with the Control Team before moving into joint analysis.
5. Closure phase: final report and recommendations
The closure phase focuses on translating activity into improvement. All teams—the Red Team, Blue Team, and Control Team—are involved.
Following test completion, the Blue Team is informed and asked to produce a Blue Team Report outlining:
- Attacks detected or missed
- Alerts generated and response actions taken
- Incidents successfully contained or mitigated
This report provides a direct insight into the effectiveness of existing detection and response capabilities.
Replay Workshop
Now, a collaborative Replay Workshop is then conducted to:
- Compare Red Team actions with Blue Team detections and responses.
- Identify gaps where techniques bypassed controls.
- Understand why specific alerts failed or arrived too late.
The workshop continues iteratively until Red Team techniques are consistently detected or neutralised.
Final reporting and feedback
The final Red Team Report consolidates:
- Initial weaknesses identified
- Defensive improvements achieved during collaboration
- Prioritised, actionable recommendations covering tooling, processes, and detection logic
This report is presented in a feedback session with all stakeholders to ensure shared understanding and ownership of remediation actions.
Red Teaming: Challenges And Limitations
Red teaming offers a realistic view of how attackers operate, but it is not without constraints. While these exercises are effective at testing detection and response under real-world conditions, they also come with practical, operational, and strategic limitations that organizations need to understand before relying on them as a primary security measure.
Here are some of the key challenges organizations commonly encounter:
- Scope & rules of engagement constraints:Certain areas are not under scope in the red team assessments as they have sensitive data, or may be critical to maintain compliance, and prevent potential disruptions. These constraints are put in place through the Rules of Engagement (RoE) to ensure testing aligns as per organizational policies.
- Costs involved:Red teaming is costlier than traditional security as they require more resources to carry out tests. It demands more skilled professionals, sophisticated tools, and extensive planning. The complexity of attacks requires more time and effort than standard vulnerability assessments.
- Potential for disruptions: Operational impact can be minimized during red team assessment by establishing clear communication channels and predefined protocols. The operation should be monitored in real-time so that disruptions are quickly addressed.
Case Study: Red Team Assessment
A. Defending Network Defenses
A large global bank engaged a red team to test the defense of its network perimeter. The team defined the scope and they exploited physical security gaps and cloned employee badges to breach the internal network. Then, the team used escalation privileges to gain domain admin access and exfiltrated 1 million customer records.
This red team exercise revealed the loopholes in the perimeter security and weak internal monitoring and poor access controls.
B. Social Engineering Attack Against a Corporate Network
A financial firm’s red team carried out a smishing campaign using phishing links via SMS. They obtained unauthorized access to credentials and bypassed MFA during the login process. This exercise exposed employee susceptibility to social engineering.
C. Cloud Security Red Team Assessment
An ecommerce company leveraged red team assessment to uncover misconfigured storage buckets and weak access controls. The red team exploited these gaps to conduct data exfiltration. This exercise exposed risks like unsecured APIs.
How to Choose the Right Red Team Provider
Red team assessment is a sophisticated, critical, and expensive task. The room for error is very narrow. You need to consider several factors before selecting the right red team company:
A. Certifications and credentials
Skill of red teaming professionals should be high to carry out red team assessment. You need to partner with a company who has a highly qualified team. A way to judge the quality of the team is to look for recognized certifications like Certified Red Team Operator (CRTOP) or Offensive Security Certified Professional (OSCP). Such credentials validate the quality of professionals.
B. Experience and track record
Reputation matters in any business. You should evaluate the provider’s history by reviewing their completed projects. Ask for client’s references. If they have a proven track record of working with enterprise grade clients and in diverse industries, it indicates their capability to handle various security challenges effectively.
C. Methodologies and tools
Ensure that the provider employs up-to-date methodologies, such as the MITRE ATT&CK framework, which guides their assessment processes. The use of contemporary tools is crucial for simulating advanced threats accurately.
These factors collectively contribute to a provider’s ability to deliver comprehensive and reliable red team assessments.
Key questions to ask
Red team assessment solutions are tailored to meet various organizational needs. But it’s important to ask specific questions from stakeholders before the upcoming assessment:
- What are the red teaming exercise’s critical goals and objectives you want to achieve?
- Who will be involved in the exercise, and what roles will they play?
- What are the events that can cause severe damage to an organization’s brand reputation if something goes wrong?
- What are critical IT infrastructures organizations rely on, including hardware and software?
- What are the possible consequences of compromising the organization’s critical assets?
Best Practices For Red Team Assessment
Effective red team assessments help organizations identify vulnerabilities and strengthen defenses. Here’s how to prepare, implement findings, and ensure ongoing improvements.
Preparing for a Red Team Engagement
- Define goals and focus areas for the exercise.
- Select a skilled red team with industry-relevant experience.
- Outline scope, tools, and timelines clearly.
- Formalize rules of engagement to avoid conflicts.
Post-Assessment Security Enhancements
- Compile key vulnerabilities and recommendations.
- Prioritize remediation based on risk severity.
- Share insights to drive collaboration on fixes.
Continuous Testing & Purple Teaming Approaches
- Schedule frequent assessments to stay ahead of threats.
- Use purple teaming to align offensive and defensive efforts.
- Improve security by learning from past exercises.
Conclusion
Red teams hack, but they do it to protect organizations’ computing infrastructure and networks. This is an advanced and effective method of assessing the robustness of security systems. Hackers have become smarter and they are using sophisticated systems and tools for attack. That’s why organizations need to think and act like them to protect their assets.
Looking for a proven red team partner that helps your organizations test real attack paths, uncover blind spots, and validate whether security programs hold up under real-world pressure. Contact us now to schedule a call!
Frequently Asked Questions (FAQs)
Typically 1 week for small organizations and up to a month for larger ones, depending on scope, budget, and locations tested.
To simulate real-world attacks, test detection/response capabilities, evaluate security culture, and identify hidden vulnerabilities in people, processes, and technology.
Often too costly for small businesses unless handling sensitive data or facing high-risk threats; penetration testing is usually a more practical alternative.
By securing backups, restricting access to sensitive data, and strictly adhering to pre-approved rules of engagement to prevent accidental breaches.
Annually or biannually, with continuous purple teaming for real-time collaboration between offensive and defensive teams.
Penetration testing, social engineering, threat intelligence, communication, and physical infiltration tactics (if applicable) to mimic advanced adversaries.



