Privacy risks in mobile apps have evolved into a serious security threat as our reliance on smartphones deepens. Many apps don’t just collect basic user data; they track user behavior, store personal information, and often use it for commercial gain without explicit consent. But for most users, privacy concerns seem limited to tapping “Allow” during installation, but the real problem runs deeper.
In reality, mobile apps often gather and retain far more data than they legitimately need. Over time, this unchecked collection quietly erodes user privacy, sometimes leading to exposure of sensitive data without any hacking involved. OWASP Inadequate Privacy Control Risks underscore how poor data handling practices in mobile apps can expose users to significant privacy violations.
This blog explains inadequate privacy controls risk mean, how it occurs, and the best practices developers can follow to protect user privacy and build trust in mobile applications.
What Does “Inadequate Privacy Controls” Mean in Mobile Apps?
In the OWASP TOP 10 mobile app security risks list, inadequate privacy controls refer to poor or insufficient mechanisms for managing user data, how it’s collected, stored, shared, and secured.
You can check the OWASP Mobile Top 10 Risks, 2024 to gain in-depth insights into various mobile app related risks and guidance for mitigation strategies.
When mobile apps gather personally identifiable information (PII), such as names, email addresses, location data, or device identifiers without explicit user consent, they violate basic data protection principles.
Often, this information is stored in unencrypted form, leaving it vulnerable to theft if the device or app is compromised.
Collecting personal data without a legitimate business purpose adds another layer of privacy risk for users. For example, some apps continue tracking a user’s location even when the app is inactive. This raises serious transparency and ethical concerns.
A major contributor to these issues is the use of third-party SDKs that may not follow strong security or privacy standards. Weak API configurations or insecure data transmissions within these SDKs can expose sensitive data to unauthorized access.
Such lapses not only endanger users’ privacy, but also create regulatory compliance risks under laws like GDPR and CCPA.
Eventually, mobile app privacy isn’t just about asking for permissions, it’s about responsible data handling. Developers must ensure every data point collected serves a clear purpose, is securely stored, and is shared only with trusted entities.
Causes of Inadequate Privacy Control Risks
As the mobile ecosystem expands and third-party integrations grow, maintaining consistent privacy standards becomes even harder. Understanding these root causes is key to protecting both user trust and regulatory compliance.
- Many privacy related risks begin with legacy security configurations or unpatched systems. Apps may still rely on older encryption methods or weak access controls, making user data more vulnerable to exposure.
- Some apps request broad permissions without stating a clear purpose. When users are not told why their data is needed or how it will be used, it leads to unnecessary data access and compliance risks.
- Using third-party SDKs without evaluating their data-handling behavior is a common cause of privacy lapses.
- Poorly secured SDKs can introduce tracking scripts or unsafe API calls, leaking sensitive user information.
- When privacy policies lack clarity or aren’t followed in practice, compliance with laws like GDPR and CCPA becomes unreliable. This increases the likelihood of both legal penalties and reputational harm.
- Development teams often prioritize speed and new features over security and privacy testing. Without proper visibility into data flows or automated privacy checks, breaches often go unnoticed until damage has already occurred.
Case Studies of Inadequate Privacy Controls Risk
The following case studies illustrate how inadequate privacy controls in mobile apps can lead to serious data exposure, regulatory violations, and user mistrust:
Scenario #1 Mobile health app leaking geolocation and fitness patterns
A health app leaks users’ health data and other medical conditions to third party servers without their explicit consent. Users on the other hand believed the app does it for personal tracking. But, they gathered and stored many other sensitive health info.
It exposes users to privacy risks and highlights what can happen when privacy controls are ignored.
Scenario # 2 Syncing app uploading phone books to foreign servers
A contact management app captures and stores entire phonebook data of users located in countries with weak data protection laws. The application does this without taking explicit consent and permission of users. Such incidents underscores the importance of transparency, consent, and data residency.
Common privacy control security risks in mobile apps
There are several privacy control related security risks in mobile phones, including:
1. Not using permissions responsibly
Most mobile apps only take broad permissions for gathering data related to location, camera, contacts during installation or runtime. But they are not used for the purpose appropriately. It exposes users to privacy risks.
For instance, an app requests permissions to access a user’s contact data without specifically mentioning what feature requires it. This enables silent data harvesting. Such type of unauthorized data collection directly or through third-party SDKs can expose PIIs to risks.
2. Poor granularity of access control mechanism
Most apps lack granular access control features. For example, an image sharing app may request access to the entire Google photo library instead of individual images.Broad level data access expands the attack surface and may compromise privacy level. It can even expose data to third party tracking libraries.
3. Failing to revoke permissions after use
Permission to collect data is not for an indefinite time period. It’s for a specific task. For example, a scanner app may continue to gather image data even if it’s no longer required. Access level permissions require re-evaluation regularly to avoid misuse of collected data.
4. Storing sensitive data in logs or cache
Often sensitive data like authentication tokens, personal identifiers, or financial information are stored in plaintext in system logs or local caches for convenience of debugging. Such storage locations are unsafe and can easily expose data to other apps or malicious actors, resulting in severe privacy breaches.
5. No user-facing control over shared data
Some apps share user data with third parties, such as advertisers, analytics platforms without explicit permission of users. They use vague and broad level consent for the same. Lack of transparency and user control over such activities undermines user trust and it can result in unauthorized data distribution, violating GDPR, CCPA.
6. Lack of audit trail for sensitive data use
Apps often do not maintain logs or records of when and how sensitive data (like location or microphone access) is accessed, or by whom. The lack of audit trail makes it difficult for security experts to trace potential misuse and detect non-compliance with privacy standards.
Why It’s Hard to spot inadequate privacy risk
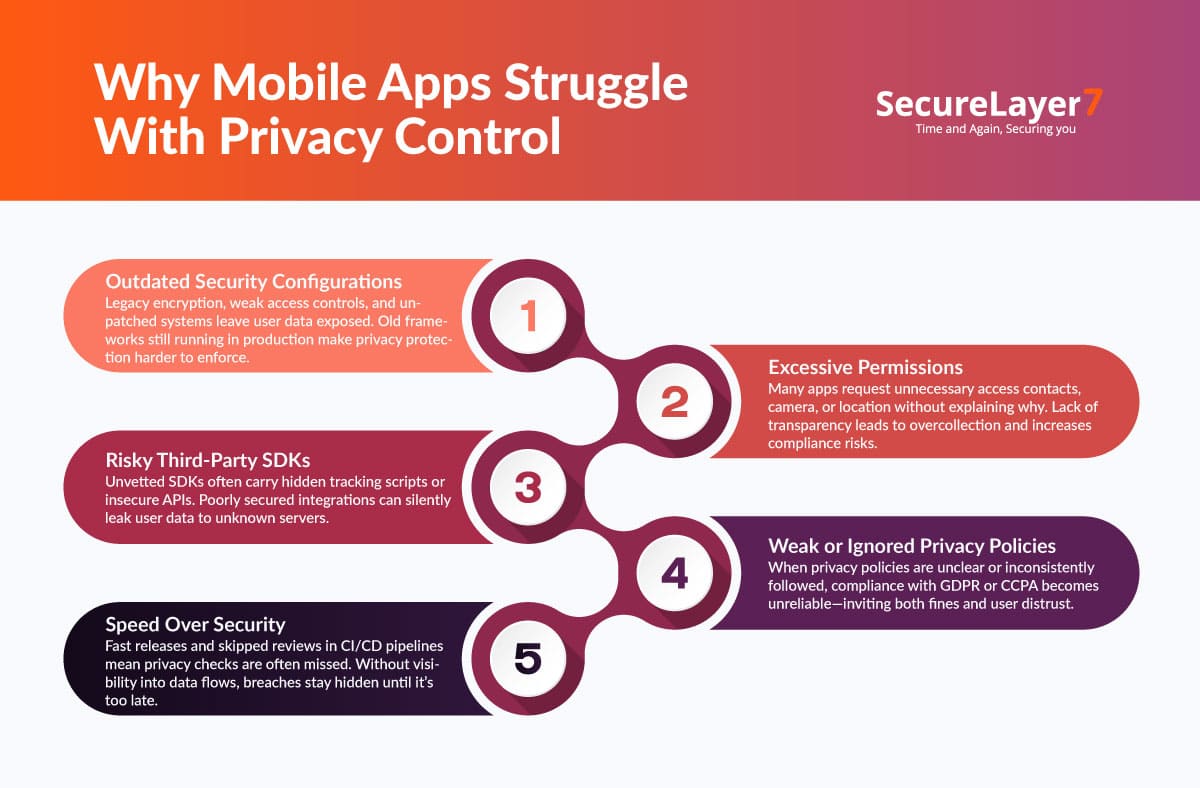
Detecting inadequate privacy control risks in mobile apps is not as simple as scanning for vulnerabilities. Many of these risks operate silently within app ecosystems, hidden behind SDKs, permissions, and fragmented testing practices. Below are some core reasons why privacy risks often remain undetected.
1. SDK behavior post-installation is not transparent
Once an app is installed, neither the operating system nor the user can fully track what third-party SDKs are doing inside the app. They may silently collect personal data, communicate with remote servers, or store sensitive information insecurely. Because such activities occur behind the scenes, privacy violations often go unnoticed until a breach is discovered.
2. Mobile CI/CD pipelines bypass privacy reviews
Modern mobile app development favors speed and automation. Continuous Integration and Continuous Deployment (CI/CD) pipelines help release updates quickly—but they also tend to skip manual privacy or security reviews. As a result, SDK updates or new app features may be pushed to production without verifying how they handle or transmit user data.
3. Users grant permissions they don’t understand
Most users consent to permissions without reading or understanding what data the app will access. A single tap on “Allow” may grant access to contacts, camera, location, and more—giving apps excessive control over personal data. This behavior, while convenient, creates an environment where privacy risks thrive unnoticed.
4. Platform Differences: iOS vs. Android Behavior
iOS and Android handle privacy and data permissions differently. What’s secure on iOS may be less controlled on Android, and vice versa. These differences complicate privacy assessments, especially for cross-platform apps where identical features can behave differently depending on the operating system.
5. Testing security gaps in privacy validation
Automated and dynamic testing tools often monitor how an app behaves during normal use, but they can miss privacy issues that occur under specific conditions—such as login, configuration changes, or location-based triggers. When these edge cases aren’t tested, hidden data leaks or unencrypted transmissions remain undetected.
Attack vectors in inadequate privacy control risks
Mobile privacy risks often emerge from hidden SDKs, insecure communication channels, or weak permission enforcement. Below are some of the most common and high-impact risks developers and security teams must be aware of.
1. Malicious SDKs harvesting data silently
Some mobile apps unknowingly include malicious third-party SDKs that collect sensitive information in the background without user consent or proper permissions.
For instance, a compromised SDK might embed itself within a legitimate framework, such as Facebook’s SDK, to intercept session tokens or authentication data. Since this activity occurs behind the scenes, users remain unaware of the data being siphoned from their devices.
2. Rogue apps sniffing shared data between apps
Certain rogue apps exploit shared storage or inter-app communication channels to access confidential data, such as login credentials or personal identifiers. A common tactic involves overlaying fake login or payment screens to trick users into entering sensitive details.
These attacks can lead to financial fraud or identity theft, especially on devices lacking app isolation safeguards.
3. Reverse engineering app logic to bypass runtime permission checks
Attackers may reverse engineer an app’s source or binary code to identify how runtime permissions are handled. Using tools like Frida, they can manipulate permission checks or patch the app to bypass security controls entirely.
This allows unauthorized access to restricted features or stored data, undermining the app’s entire privacy model.
4. Exfiltrating data via third-party advertising networks
Advertising SDKs are among the most common sources of unintentional data exposure. Many ad networks collect and transmit user data, such as location, device identifiers, and browsing activity to external servers under the guise of targeted advertising.
Without clear consent or disclosure, these SDKs create compliance and reputational risks for developers, especially when sensitive personal data is involved.
How to Prevent Inadequate Privacy Control Risks
Privacy control related risks can be minimized if certain practices are followed. Using the following ways can help:
Minimize data collection
- Only collect the necessary data required for specific service to avoid privacy risks.
- Always verify the user data coming from third parties.
- Periodically audit data collection process to remove outdated, or legacy data.
Data reduction and anonymization
- Use data masking, data redaction to protect sensitive information.
- Carry out data discovery and classification to identify all personally identifiable information (PII).
- Use pseudonymization to enhance privacy and regulatory compliance.
Data lifecycle management
- Set up a detailed data lifecycle management strategy including data creation, storage, usage, sharing, archiving, and timely deletion.
- Establish data retention policies and data detention policy to minimize risk.
- Use role-based access controls (RBAC) and multi-factor authentication (MFA) to restrict data access levels. ecycle.
Secure transmission and storage
- Encrypt data-in- transit and data-at-rest using AES-256 encryption standard.
- Remove unused services and devices.
User consent and transparency
- Obtain explicit, informed, and unambiguous consent from users before collecting or processing their data.
- Clearly explain what data is collected, why, and how it will be used.
- Maintain transparency by communicating data practices openly.
Backup securely
- Store backups securely using encryption and restrict access to authorized personnel only.
- Maintain offsite and onsite backups to ensure redundancy and quick recovery in case of disaster.
Privacy threat modeling
- Visualize how sensitive data moves through the mobile app to pinpoint where privacy risks may arise.
- Apply frameworks like STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege.
- Assess potential impact of each identified threat to focus mitigation efforts on the highest risks.
Conduct privacy impact assessments on SDK updates
- Assess how updated SDKs collect, store, or share user data.
- Record identified privacy risks from SDK update.
- Implement controls or alternatives to minimize exposure.
Embed privacy linting/checks into CI/CD pipelines
- Integrate privacy-focused static code analysis tools to detect insecure data handling.
- Configure CI/CD pipelines to block deployments if privacy checks fail.
Train product owners on regulatory and reputational risk
- Provide regular training on relevant regulations such as GDPR, CCPA, HIPAA.
- Empower product owners to balance features with privacy compliance.
Establish policy on what types of data can be accessed by apps
- Categorize data types into personal, sensitive, anonymized.
- Ensure apps only access the minimum necessary data. .
- Regularly update data access policies as per regulatory requirements.
Continuous privacy testing
- Leverage tool-generated reports to prioritize and remediate privacy risks before app release.
- Use tools like MobSF(Mobile Security Framework) for static code analysis and Ostorlab for dynamic testing to identify privacy vulnerabilities continuously.
- Schedule privacy scans as part of the build and deployment process to catch issues early.
Best Practices to Avoid User Privacy Control Risks
Here is the list of the best practices to avoid privacy control risks in mobile applications:
Strong cryptography
- Use hash passwords with strong, collision-resistant algorithms.
- Enforce strict access controls for cryptographic keys.
Support HTTP Strict Transport Security (HSTS)
- Use HSTS headers to ensure browsers only connect via secure HTTPS, preventing downgrade attacks.
- Configure browsers to refuse connections with invalid or untrusted TLS certificates.
- If forcing HSTS for all users is impractical, provide an option to enable it for privacy-conscious users.
Digital certificate pinning
- Hardcode or store hashes of valid certificates in clients to prevent man-in-the-middle attacks, especially in hostile environments.
- Protect against attackers issuing fraudulent certificates by pinning expected certificates.
- Avoid reliance on users to correctly handle certificate warnings by enforcing pinning in apps.
Panic modes
- Allow users under threat to activate modes that hide or delete sensitive data without alerting adversaries.
- Enable fake accounts or inboxes that appear normal but protect real data.
- Panic modes should be hard to detect and allow normal operations to continue to avoid suspicion.
Remote Session Invalidation
- Provide interfaces for users to see all logged-in devices and sessions.
- Users should be able to remotely log out or invalidate sessions, especially for lost or stolen devices.
- Invalidate suspicious sessions promptly to reduce risk from stolen cookies or tokens.
Allow connections from anonymous networks
- Enable users to access services via anonymity networks to bypass censorship and protect privacy.
- Reconsider policies that restrict access from Tor or VPNs to avoid harming users in restrictive regions.
- Facilitate easy use of SOCKS proxies or libraries (e.g., OnionKit) to improve user anonymity.
Prevent IP address leakage
- Prevent loading of external images or resources that can reveal user IP addresses.
- Provide options to block or allow third-party content to protect user privacy.
Conclusion
Poor privacy control means poor security and eventually it erodes the trust of users. Also, CISOs need to understand that privacy is deeply embedded in mobile app’s architecture and it’s not a superficial thing like UI. Ignoring it can be risky for businesses and, therefore, they should treat privacy violations as security breach incidents.
Privacy control related risks can have serious consequences if ignored. Our offensive security team can help deal with such risks with ease. Contact us now to learn more.
FAQs on inadequate privacy control risks
You can start by taking a close look at the app’s permissions, how it collects data, and the behavior of any SDKs it uses. Using automated tools can help you audit data flows and check them against privacy laws like GDPR or CCPA, ensuring everything is compliant and that there’s no unauthorized access to data.
You can use tools like AppSweep, Ostorlab, and MobSF, which can be seamlessly integrated into your CI/CD pipeline. These tools scan your apps for any privacy violations, spotting unsafe data flows, insecure permissions, and problematic SDK behaviors before you deploy, helping you maintain ongoing privacy compliance.
Yes, third-party SDKs may introduce inherent privacy risk. They can access user data through the permissions granted to the app. If there’s a lack of strict control or transparency, these SDKs can pose a significant privacy threat, especially if their behavior changes after integration due to updates.
User consent means you need to get clear permission from users before collecting their personal data. On the other hand, legitimate business interest allows you to use data without explicit consent, but only when it’s necessary and doesn’t significantly impact user rights, as outlined by privacy regulations.
Use proxy-based tools like mitmproxy, Proxyman, or Charles Proxy with SSL interception. Combine these with instrumentation frameworks or debug builds to monitor network traffic and internal data handling securely.



