Data validation plays a critical role in preventing some of the most devastating cyberattacks. OWASP M4, categorized under the OWASP Mobile Top 10 risks, highlights the danger of Insufficient Input/Output Validation – a vulnerability that arises when applications fail to properly check, sanitize, or encode user-supplied data. This oversight can lead to a variety of exploits including SQL injection, cross-site scripting (XSS), command injection, and buffer overflows, putting both user data and system integrity at risk.
This vulnerability arises when applications fail to validate or sanitize incoming and outgoing data properly. The same goes for output data: it can become a vehicle for exploits if it isn’t correctly encoded before rendering.
OWASP and the Mobile Top 10 security risks
The Open Web Application Security Project (OWASP) is a globally recognised nonprofit organisation dedicated to improving software security. OWASP publishes the “Mobile Top 10,” highlighting the most critical security risks affecting mobile applications. This list helps developers, security professionals, and organisations prioritise and address vulnerabilities that could lead to data breaches, unauthorised access, and other severe security incidents in mobile apps.
Insufficient Input/Output Validation (OWASP M4)
Insufficient Input/Output Validation, identified as M4 in the OWASP Mobile Top 10 2024, occurs when a mobile application fails to properly validate and sanitise data it receives (input) or sends out (output). The app does not thoroughly check user inputs or output data for malicious content or unexpected formats. Such lapses enable attackers to inject harmful code or manipulate data, leading to attacks like SQL injection, cross-site scripting (XSS), command injection, and path traversal.
Why this vulnerability poses a critical risk in modern applications
This vulnerability is critical because it opens the door to severe technical and business consequences:
- Technical Risks: Attackers can execute unauthorised code, gain access to sensitive data, compromise backend systems, disrupt application functionality, and cause data corruption or crashes.
- Business Risks: Exploitation can lead to data breaches, loss of customer trust, reputational damage, legal liabilities, regulatory penalties, and operational disruptions.
What is Input/Output Validation?
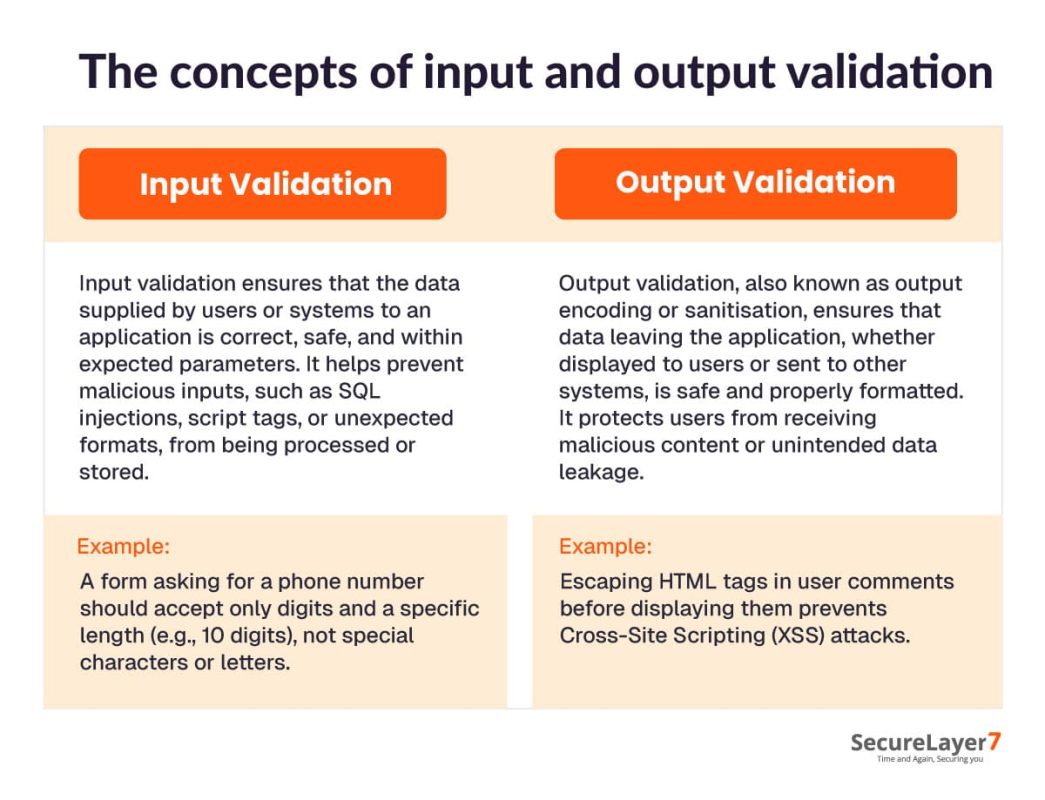
Every mobile and web application in the contemporary digital world is integrated with user-generated content through forms, APIS, or other external sources. Input/Output (I/O) validation ensures that the data being captured and processed is secure, reliable, and managed properly. Inadequate validation procedures can lead to serious risks, including data exposure, Dos (Denial-of-Service) attacks, or total system takeovers. The concepts of fundamental input and output validation underscore their significance concerning improperly executed events.
The concepts of input and output validation
Difference between client-side and server-side validation
- Client-side validation occurs in the user’s browser, providing instant feedback (e.g., flagging invalid email formats) and reducing server load. It’s vulnerable to bypassing via disabled JavaScript or HTML manipulation.
- Server-side validation happens on the server after data submission, offering robust security against tampering and validating hidden/encrypted data. It’s slower but essential for comprehensive protection.
Real-world examples of common validation failures
- E-commerce price tampering: Attackers manipulate API inputs (e.g., altering product prices) due to missing server-side checks.
- SQL injection: Unvalidated user inputs in login fields allow attackers to execute malicious database queries.
- Cross-site scripting (XSS): Improper output sanitisation lets attackers inject scripts into web pages, stealing session cookies.
- Denial of Service (Dos): Malicious inputs (e.g., oversized files) crash systems lacking input size validation.
Understanding OWASP M4
Web applications rely heavily on data exchange between users and systems, making validating input and output data a critical component of secure software design. OWASP M4: Insufficient Input/Output Validation is a key category in the OWASP Mobile Top 10 risks, highlighting the dangers of neglecting proper data validation.
This vulnerability or risk will occur if systems do not guarantee consistent verification of the supplied input through any interface, including systems and users to which the information output is directed. As a result of these lapses, many exploits, including code injection, leakage of crucial data, non-operability of fundamental features, and bypassing security measures, can happen.
OWASP M4 in the context of mobile apps/web systems
OWASP M4, or Insufficient Input/Output Validation, refers to a security vulnerability where mobile or web applications fail to properly validate and sanitise data received from external sources (input) or sent out (output). This lack of rigorous validation allows malicious data to enter or exit the system unchecked, leading to potential exploitation. It is a common and easily detectable weakness that can compromise application integrity, data confidentiality, and system security.
Examples of attacks exploiting insufficient validation (e.g., SQL Injection, XSS, buffer overflows)
- SQL Injection: Attackers inject malicious SQL commands through unvalidated input fields, enabling unauthorized database access or data manipulation.
- Cross-Site Scripting (XSS): Malicious scripts are injected into output content that has not been sanitized correctly, allowing attackers to steal user sessions or manipulate webpage content.
- Buffer Overflows: Excessive input data overwrites memory buffers, causing erratic behaviour or enabling arbitrary code execution.
- Command Injection: Unsensitized inputs are used in system commands, allowing attackers to execute arbitrary commands on the host system.
How unvalidated input/output can be manipulated by attackers
When input validation is insufficient, attackers can craft specially formed inputs containing unexpected or malicious characters, scripts, or code. For example, they might insert SQL commands into form fields or script tags into output data. Without proper checks, these inputs bypass security controls and execute unauthorised actions such as data theft, remote code execution, or system compromise.
Unvalidated output can allow malicious scripts to run on client devices, leading to session hijacking or defacement. This manipulation exploits the system’s trust in input/output data, turning it into an attack vector.
Real-World Impact
Input and output validation flaws are not theoretical threats; they have been at the centre of some of the most damaging cyberattacks in recent history. When applications fail to validate the data they receive or output properly, attackers can manipulate inputs to execute code, access unauthorised data, or cause systems to crash.
Understanding the real-world impact of insufficient I/O validation helps developers and organizations recognize the urgency of secure coding practices and the importance of validating and sanitizing every piece of data that flows through their systems.
Case studies or data breaches caused by poor input/output validation
The 2013 Target breach attack is a telling example of attackers exploiting a lack of validation and control in vendor-facing web applications by uploading malicious scripts (web shells). This enabled remote control, privilege escalation, and the theft of personal and credit card data for 70 million customers. Many mobile apps suffer from unorchestrated data leaks due to faulty validation of input and output streams.
Business and technical impact of these vulnerabilities
Technically, insufficient input/output validation can lead to unauthorised code execution, data breaches, system crashes, and complete system compromise. From a business perspective, these vulnerabilities cause severe consequences such as privacy violations, regulatory penalties (e.g., PCI compliance failures), reputational damage, fraud, and operational disruptions. The financial and trust losses from such breaches often far exceed the cost of preventive security measures.
Consequences such as data leaks, system crashes, or privilege escalation
Poor validation can result in:
- Data leaks: Sensitive information exposed through insecure data storage or injection attacks.
- System crashes: Malformed inputs causing buffer overflows or application instability.
- Privilege escalation: Attackers leveraging injected code or stolen credentials to gain administrative control, as seen in the Target breach, where “pass-the-hash” techniques were used to escalate privileges.
How to Identify M4 Vulnerabilities
Identifying OWASP M4 vulnerabilities, Insufficient Input/Output Validation, is critical for securing modern web and mobile applications. These vulnerabilities occur when user-supplied data is not properly validated before being processed or output, leading to a wide range of attacks, including XSS, SQL injection, path traversal, and remote code execution.
Since validation failures often hide in plain sight, developers, testers, and security professionals must implement proactive detection strategies throughout the software development lifecycle.
Manual code review and penetration testing
Manual code reviews involve scrutinizing source code to detect improper validation of inputs and outputs. Look for:
- Missing or improper input sanitization.
- Hardcoded trust assumptions.
- Inconsistent encoding of output.
Penetration testing simulates real-world attacks to discover exploitable flaws. A penetration tester may:
- Attempt SQL injection or XSS using crafted payloads.
- Exploit mis-validated headers or file formats.
- Probe input endpoints using fuzzing techniques.
Static and dynamic analysis tools
Static Application Security Testing (SAST) tools analyse source code or binaries without running the program, detecting patterns linked to insufficient validation, such as concatenated SQL queries or missing sanitisation functions. Examples include Android Studio Lint for mobile apps and tools like SonarQube for Code. Dynamic Application Security Testing (DAST) tools test running applications by sending crafted inputs to detect vulnerabilities such as cross-site scripting (XSS) or injection flaws.
Integrating automated security scanners into CI/CD pipelines
Integrating automated security scans into Continuous Integration/Continuous Deployment (CI/CD) pipelines guarantees early and persistent detection of M4 vulnerabilities. During code commits and pull requests, static analysis tools check for insecure input/output handling, and dynamic scanners test for runtime flaws in the deployed builds. With Jenkins, GitLab, or GitHub Actions, deep integration allows for seamless developer feedback, which helps avoid code production in vulnerable states, thus ensuring secure delivery cycles.
This approach combines manual review with automated analysis and contains CI/CD integration, creating a comprehensive shield against OWASP M4: Insufficient Input/Output Validation and web and mobile application vulnerabilities, exposing them to severe risks.
Best Practices to Prevent Insufficient I/O Validation
Input and output validation are fundamental security measures that help protect applications from malicious data injection, cross-site scripting (XSS), data leakage, and system compromise. When an application fails to validate or sanitise incoming or outgoing data correctly, it becomes vulnerable to various attack vectors, potentially exposing sensitive information or enabling attackers to manipulate the application’s behaviour.
Insufficient I/O validation is listed under OWASP M4 as a critical security risk. It typically stems from a lack of strict rules around what data an application accepts or returns. Without enforcing constraints and proper encoding, applications may inadvertently trust user-supplied data, leading to serious consequences like corruption, and unauthorized access.
Enforce strong validation rules (whitelisting, type checking)
Implement strict input validation using allowlisting- accept only known good data patterns, types, lengths, and formats. For example, validate that a phone number contains only digits and has a fixed length. Avoid relying on blocklist (denylist) approaches, which attackers can easily bypass. Before validation, inputs (e.g., decode URL-encoded data) should always be canonicalized to prevent evasion.
Sanitize and encode outputs
Before sending data back to users or other systems, sanitise and encode outputs to prevent injection attacks like Cross-Site Scripting (XSS). Use context-specific encoding (HTML, URL, JSON) to neutralise potentially harmful characters. Secure coding frameworks often provide built-in output encoding functions; leverage these to avoid manual errors.
Use secure coding libraries and frameworks
Utilise well-maintained validation libraries and frameworks (e.g., Django Validators, Apache Commons Validators, JSON Schema validators) to enforce consistent and tested validation rules. These tools reduce human error and improve security posture. For database interactions, always use parameterised queries or prepared statements instead of concatenating user inputs to prevent SQL injection.
Input validation for APIs and mobile endpoints
Treat all data from APIS and mobile endpoints as untrusted. Implement rigorous server-side validation, including schema validation (e.g., JSON Schema) for structured data, and validate all headers, parameters, and request bodies. Do not rely solely on client-side validation, which can be bypassed. Enforce strict validation rules on the backend to prevent injection, manipulation, and unauthorized data access through API calls or mobile app inputs.
Developer and Organization Checklist
Ensuring application security is a shared responsibility between developers and organisations. Security vulnerabilities like insufficient input/output validation or insecure authentication can lead to data breaches, financial losses, and reputational damage.
It covers essential validation points, coding practices, deployment protocols, and ongoing monitoring recommendations, empowering teams to identify gaps, reinforce security controls, and build resilient applications aligned with OWASP and industry best practices.
Pre-deployment validation rules testing
- Define Clear Validation Requirements: Establish comprehensive validation rules for all inputs and outputs, covering data types, lengths, formats, and allowed characters.
- Automated Testing: Integrate unit and integration tests, verifying input validation logic against valid and malicious inputs. Use fuzz testing to uncover unexpected edge cases.
- Manual Code Review: Conduct thorough code reviews on input/output handling to identify missing or weak validation.
- Penetration Testing: To validate defences, perform security testing simulating real-world attacks such as SQL injection, XSS, and command injection.
- Use Static and Dynamic Analysis Tools: Employ SAST and DAST tools to detect validation weaknesses before release.
Post-deployment monitoring and logging
- Implement Detailed Logging: Log all input validation failures and suspicious activities with sufficient context to facilitate incident investigation.
- Real-Time Monitoring: Use security information and event management (SIEM) systems to detect anomalies or repeated validation errors that may indicate attacks.
- Alerting Mechanisms: Set alerts for critical validation failures or unusual patterns to enable rapid response.
- User Feedback Loop: Monitor user reports for potential validation-related issues or unexpected behaviours.
Periodic security audits and updates
- Regular Security Audits: Schedule periodic audits of validation logic and security controls to identify new vulnerabilities or regressions.
- Update Validation Rules: Continuously refine validation rules based on emerging threats, attack patterns, and application changes.
- Patch and Upgrade Dependencies: Keep libraries, frameworks, and tools up to date to take advantage of security improvements and fixes.
- Training and Awareness: Educate developers and stakeholders about secure coding practices and the importance of input/output validation.
Conclusion
Insufficient Input/Output Validation, listed as OWASP M4, is a foundational security risk that continues to impact both mobile and web applications. By failing to validate and sanitize data at every entry and exit point, organizations open themselves up to a range of severe threats – SQL injection, cross-site scripting (XSS), buffer overflows, command injection, and more.
To safeguard digital assets and ensure application resilience, developers must adopt a defense-in-depth strategy – one that includes strong input/output validation rules, secure coding libraries, regular penetration testing, and CI/CD-integrated security scans. Input and output should never be assumed safe, regardless of source or context.
Need help assessing and securing your application against OWASP M4 and other critical vulnerabilities?
Connect with SecureLayer7 – a global offensive security firm that specializes in vulnerability assessment, penetration testing, and application security solutions. Empower your development lifecycle with expert-led security audits and continuous protection.
Frequently Asked Questions (FAQs)
OWASP M4 refers to a security risk where applications fail to properly validate user input or sanitize output. This vulnerability can lead to attacks such as SQL injection, cross-site scripting (XSS), command injection, and data leakage. M4 emphasizes the importance of both validating incoming data and securely handling outgoing data to prevent exploitation.
Input validation ensures that only correctly formatted and expected data is processed by the application. Without it, attackers can inject malicious inputs that manipulate system behavior, access unauthorized data, or compromise application integrity. Strong validation is a fundamental defense against many common vulnerabilities, including those listed in the OWASP Top 10.
Input validation filters and restricts incoming data to match expected formats and values, blocking invalid or malicious input. Output encoding transforms outgoing data so that it’s treated as plain text, not executable code especially when rendering in browsers or transmitting over APIs.
Yes. APIs, especially REST and GraphQL endpoints, are prime targets if input validation is missing or inconsistent. Mobile apps can also be reverse-engineered to send malicious data to backend services, making server-side validation and schema enforcement critical for mobile security as well.
Schema validation ensures that data submitted to an API matches a predefined structure, including:
• Required fields
• Data types (e.g., string, number, boolean)
• Pattern matching (e.g., email format)
• Length and boundary constraints