
Mobile App Security Testing: Safeguarding User Data
November 23, 2023
Ensuring Web Server Security: Protecting Your Online Presence
November 29, 2023
In the ever-evolving battlefield of cybersecurity, the threats that lurk within your organization’s own walls are just as dreadful as those from the outside. This is where Internal Penetration Testing comes into play. It’s your secret weapon against vulnerabilities hiding within your networks, systems, and workforce.
Imagine this scenario: Your external defenses are solid, and you think your organization is secure. But unknown to you, a weak link exists within your internal infrastructure.
It’s a ticking time bomb, waiting for the right moment to explode into a full-blown security breach. This is precisely why internal penetration testing is not just important – it’s essential.
The Critical Role of Internal Penetration Testing
In this blog, we’re diving headfirst into the world of Internal Penetration Testing. We’ll explore what it is, why it matters, and how it can save your organization from costly breaches and reputational damage.
So, if you’re ready to discover the secrets of safeguarding your digital fortress from within, keep reading. We’re about to unlock the power of Internal Penetration Testing and show you how to turn your vulnerabilities into strengths.
Benefits of Internal Penetration Testing
Now that we understand the essence of Internal Penetration Testing, let’s uncover the numerous advantages it brings to the table for organizations, while also shedding light on the risks and consequences of overlooking internal security.
Advantages of Internal Penetration Testing:
Uncover Hidden Vulnerabilities: Internal Penetration Testing goes beyond the surface to unearth vulnerabilities that may be invisible to traditional security measures. It reveals the weaknesses an attacker could exploit from within.
Protection from Insider Threats: As mentioned earlier, insider threats are a significant concern. This testing helps in identifying and mitigating risks associated with employees, contractors, or anyone with access to your internal systems.
Risk Reduction: By identifying and addressing vulnerabilities proactively, you reduce the risk of a costly data breach. Prevention is always more cost-effective than remediation.
Enhanced Security Awareness: Internal testing educates your staff about potential threats and security best practices. This heightened awareness can lead to a more security-conscious organizational culture.
Compliance and Regulatory Alignment: For many industries, compliance with data protection and security standards is non-negotiable. Internal Penetration Testing ensures your organization meets these requirements.
Improved Incident Response: In the event of a security incident, having a clear understanding of your internal systems gained through testing can expedite incident response efforts.
Risks and Consequences of Neglecting Internal Security:

Data Breaches: Neglecting internal security can lead to data breaches. This can result in the theft of sensitive customer data, intellectual property, or financial information, causing reputational damage and financial losses.
Operational Disruption: An internal breach can disrupt your day-to-day operations, leading to downtime, loss of productivity, and increased recovery costs.
Legal Consequences: Depending on your location and industry, data breaches may lead to legal consequences, fines, and lawsuits if customer data is compromised due to internal vulnerabilities.
Reputation Damage: Public perception matters. A security incident stemming from internal weaknesses can harm your organization’s reputation and erode trust among customers and partners.
Loss of Competitive Edge: In today’s competitive landscape, the ability to protect sensitive information is a selling point. A security breach resulting from negligence can undermine your competitive edge.
Financial Impact: Dealing with the aftermath of a security breach can be financially crippling, including costs associated with investigations, remediation, and potential fines.
Preparing for an Internal Penetration Test
Before diving headfirst into an Internal Penetration Test, organizations must take several crucial preparatory steps to ensure the process is effective, efficient, and aligned with their security objectives.
In this section, we’ll outline the initial steps that organizations should take before conducting an internal penetration test, emphasizing the importance of scoping, defining goals, and obtaining proper authorization.
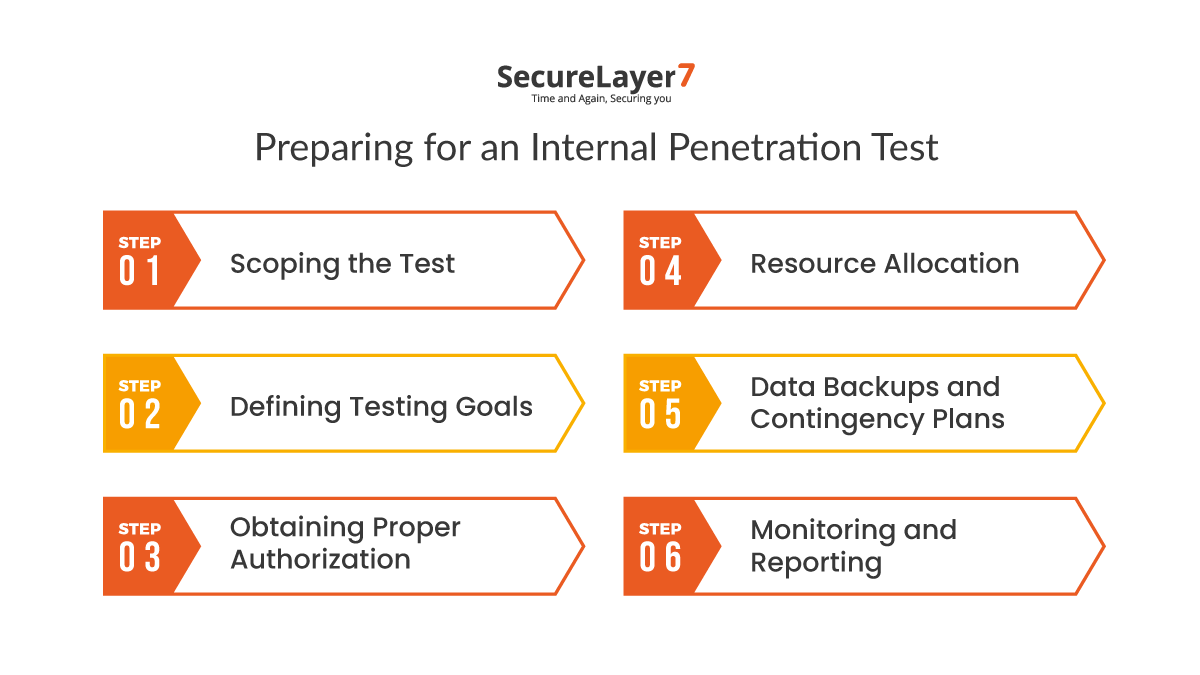
1. Scoping the Test:
Identify Targets: Determine what specific components of your internal infrastructure will be subjected to testing. This could include servers, databases, workstations, IoT devices, etc.
Establish Boundaries: Define the scope by specifying the areas, networks, or systems that are in and out of bounds for the test. This ensures that the testing remains controlled and minimizes any unintended disruptions.
Set Rules of Engagement: Clearly articulate the rules of engagement for the testing team. This should cover what actions are permitted, communication protocols, and any constraints to ensure a safe and productive testing environment.
2. Defining Testing Goals:
Identify Objectives: Clearly state the objectives of the penetration test. Are you looking to identify specific vulnerabilities, assess the effectiveness of incident response procedures, or gauge the resilience of your defenses as a whole?
Prioritize Targets: Based on the criticality of systems and data, prioritize targets for testing. Not all assets may be equally important, so allocate resources accordingly.
3. Obtaining Proper Authorization:
Legal and Ethical Considerations: Ensure that you comply with all legal and ethical considerations. Penetration testing without proper authorization can lead to legal consequences.
Stakeholder Communication: Communicate the testing plan to all relevant stakeholders, including IT teams, security personnel, and senior management. Transparency in this phase is essential.
Get Sign-off: Obtain formal authorization from senior management or the relevant decision-makers. This sign-off demonstrates commitment to the testing process and underscores its importance.
4. Resource Allocation:
Assemble the Testing Team: Select a team of skilled penetration testers who have the expertise to simulate real-world attacks. They should be familiar with your organization’s systems and technologies.
Tools and Equipment: Ensure that the testing team has access to the necessary tools, equipment, and resources required to execute the test effectively.
5. Data Backups and Contingency Plans:
Backup Critical Data: Before the test begins, ensure that all critical data is backed up securely. This safeguards against accidental data loss during the testing process.
Incident Response Plan: Develop and communicate an incident response plan that outlines the steps to be taken in the event of a real security incident being triggered during testing.
6. Monitoring and Reporting:
Continuous Monitoring: Set up a system for continuous monitoring of the test to ensure it remains within the predefined scope and doesn’t adversely affect the organization’s operations.
Reporting Procedures: Establish clear reporting procedures for the testing team to document their findings, including vulnerabilities, potential impacts, and recommended remediation steps.
Conducting the Internal Penetration Test
Internal penetration testing is a crucial component of a comprehensive cybersecurity strategy. It involves assessing the security of an organization’s internal network, systems, and applications to identify vulnerabilities that could be exploited by malicious actors.
In this section, we will outline the various methodologies and techniques used during an internal penetration test, explain the role of penetration testers and the tools they employ, and provide examples of common attack scenarios and vulnerabilities targeted during the test.
Methodologies and Techniques
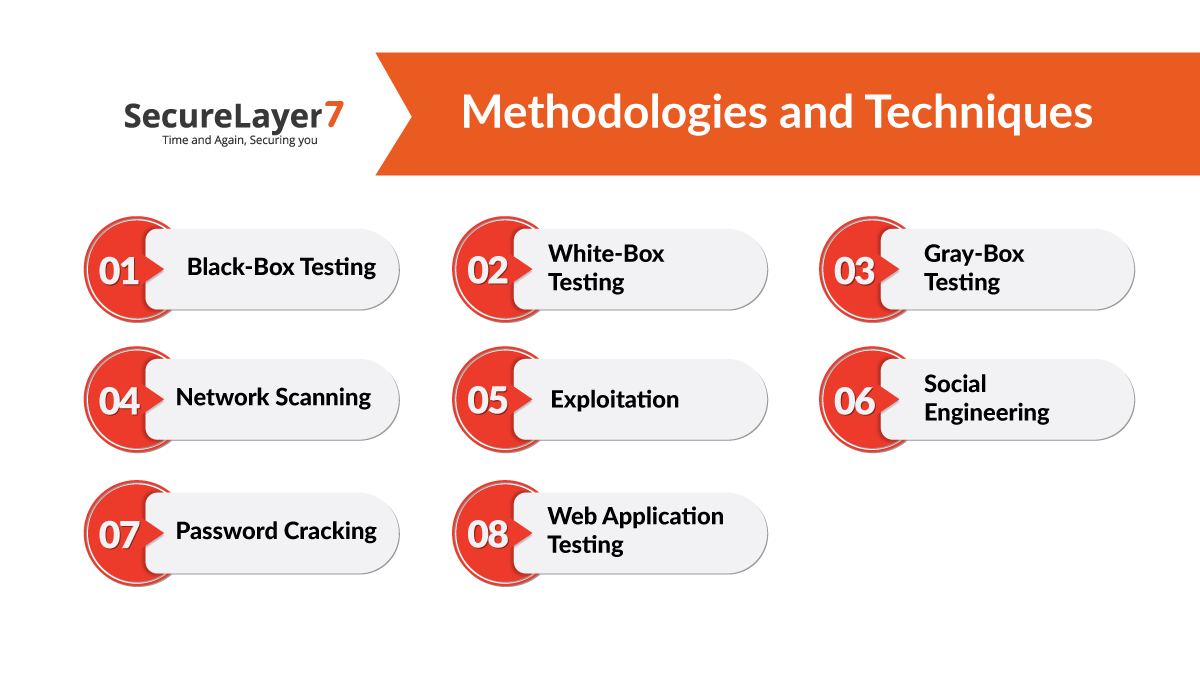
1. Black-Box Testing
In black-box testing, the penetration tester has limited knowledge about the internal systems and network. This simulates the perspective of an external attacker.
2. White-Box Testing:
White-box testing involves a thorough understanding of the internal infrastructure. Testers have access to network diagrams, source code, and system documentation.
3. Gray-Box Testing:
Gray-box testing falls between black-box and white-box testing. Testers have some knowledge of the internal systems but lack full access.
4. Network Scanning:
Scanning tools like Nmap and Nessus are used to identify open ports, services, and vulnerabilities on the network.
5. Exploitation:
Penetration testers attempt to exploit vulnerabilities discovered during scanning. This may include gaining unauthorized access to systems, escalating privileges, or executing malicious code.
6. Social Engineering:
Testers use social engineering techniques to manipulate employees into revealing sensitive information or taking actions that compromise security.
7. Password Cracking:
Brute force attacks, dictionary attacks, and password spraying are used to crack weak or easily guessable passwords.
8. Web Application Testing:
Testers assess the security of web applications by identifying vulnerabilities like SQL injection, cross-site scripting (XSS), and CSRF.
Role of Penetration Testers
Penetration testers play a critical role in internal security assessments:
Planning: They plan and scope the test, defining objectives and rules of engagement.
Testing: They use various tools and techniques to simulate attacks and identify vulnerabilities.
Analysis: Testers analyze the results, prioritize findings, and provide detailed reports to stakeholders.
Recommendations: They suggest remediation strategies to fix vulnerabilities and improve security.
Continuous Improvement: Testers assist in ongoing security improvement efforts by providing feedback and retesting as needed.
Tools Employed by Penetration Testers
Penetration testers rely on a wide range of tools, both commercial and open source, to conduct assessments. Some commonly used tools include:
Metasploit: A powerful framework for developing, testing, and executing exploits.
Wireshark: A network protocol analyzer for capturing and inspecting data on the network.
Burp Suite: A tool for web application security testing, including scanning for vulnerabilities and intercepting web traffic.
Nessus: A vulnerability scanner that identifies security issues in networks and systems.
Hydra and John the Ripper: Tools for password cracking.
Social Engineering Toolkit (SET): A toolkit for simulating social engineering attacks.
Common Attack Scenarios and Vulnerabilities
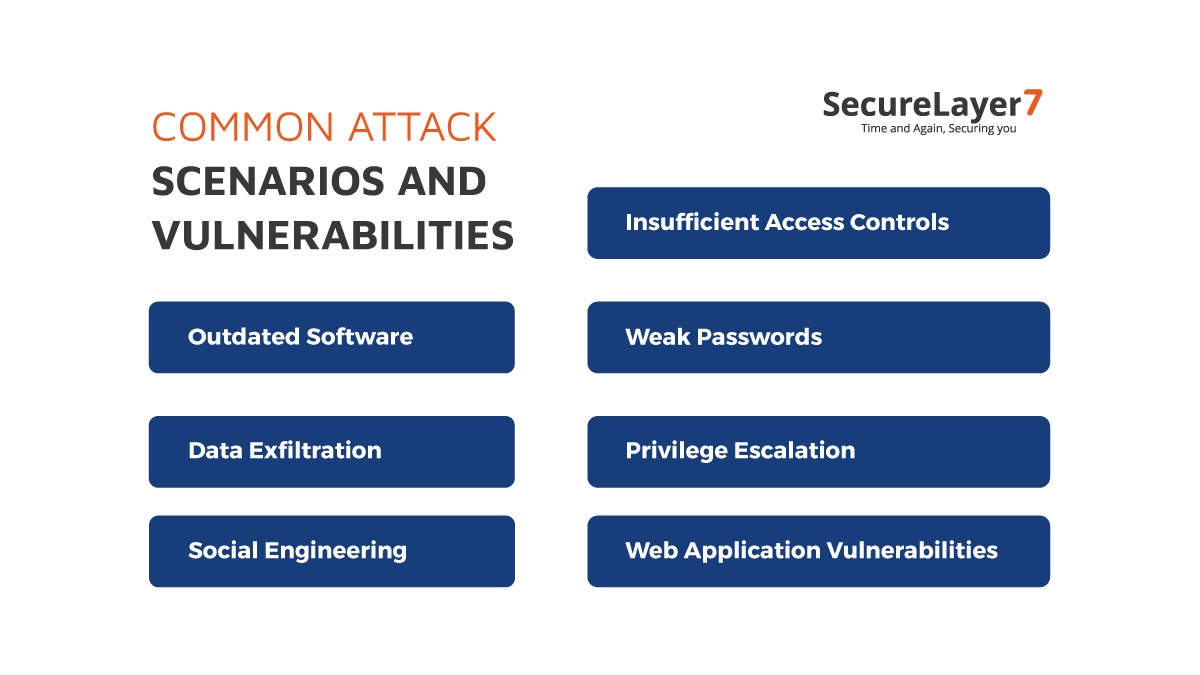
During internal penetration tests, testers simulate various attack scenarios targeting common vulnerabilities, such as:
Insufficient Access Controls: Testing for unauthorized access to sensitive data or systems.
Weak Passwords: Assessing the strength of passwords and their susceptibility to cracking.
Outdated Software: Identifying systems with outdated software and known vulnerabilities.
Privilege Escalation: Attempting to escalate user privileges to gain unauthorized access.
Data Exfiltration: Testing the organization’s ability to detect and prevent data theft.
Web Application Vulnerabilities: Finding vulnerabilities like SQL injection, XSS, and CSRF in web applications.
Social Engineering: Evaluating the susceptibility of employees to phishing, pretexting, or other social engineering attacks.
Conducting an internal penetration test is essential for identifying and mitigating security risks within an organization’s infrastructure. It helps organizations proactively strengthen their security posture, protect sensitive data, and defend against potential threats.
Analyzing Test Results
After the completion of a penetration test, the post-testing phase is critical for making sense of the findings and taking appropriate actions to improve the organization’s security posture.
This phase involves data analysis and report generation, prioritizing identified vulnerabilities, and providing clear and actionable reports.
Data Analysis
Data Collection: Penetration testers gather a vast amount of data during the test, including vulnerability scans, logs, and notes on their actions.
Identification of Vulnerabilities: The collected data is reviewed to identify vulnerabilities, weaknesses, and security issues that were discovered during the test.
Severity Assessment: Each vulnerability is assessed for its severity and potential impact on the organization’s security.
Contextual Analysis: Testers provide context for vulnerabilities, explaining how they were exploited, if applicable, and the potential implications of a successful attack.
Prioritization and Remediation
Once vulnerabilities are identified and assessed, organizations need to prioritize and remediate them effectively:
Risk Assessment: Assess the risk associated with each vulnerability by considering factors like the potential impact on operations, data, and compliance.
Prioritization: Prioritize vulnerabilities based on their severity, risk, and the ease of exploitation. Some vulnerabilities may pose a higher risk due to their potential for significant harm or because they are easy targets for attackers.
Remediation Planning: Develop a remediation plan that outlines the steps and timeline for addressing each vulnerability. Consider short-term mitigations to reduce immediate risk and long-term solutions for comprehensive security improvements.
Resource Allocation: Allocate resources, including personnel and budget, to address high-priority vulnerabilities promptly.
Patch Management: Ensure that software and systems are kept up-to-date with security patches to address known vulnerabilities.
Security Awareness Training: Educate employees about security best practices to reduce the risk of human error and social engineering attacks.
Importance of Clear and Actionable Reports

Clear and actionable reports are a crucial outcome of a penetration test, as they guide organizations in improving their security posture and addressing vulnerabilities effectively:
Detailed Findings: The report should provide detailed information about each vulnerability, including how it was discovered, its potential impact, and technical specifics.
Severity Ratings: Assign severity ratings or risk scores to vulnerabilities to help organizations prioritize remediation efforts.
Recommendations: Include clear and specific recommendations for mitigating each vulnerability. Recommendations should be practical and actionable, with step-by-step guidance where needed.
Timelines: Specify timelines for addressing vulnerabilities. This helps organizations understand the urgency of remediation.
Executive Summary: Provide an executive summary that highlights the overall state of security, key findings, and high-priority vulnerabilities for leadership and non-technical stakeholders.
Supporting Evidence: Include evidence, such as screenshots or log entries, to demonstrate the existence of vulnerabilities and make it easier for IT teams to reproduce and fix them.
Mitigation Verification: After remediation, penetration testers can perform a retest to verify that vulnerabilities have been successfully addressed.
Feedback Loop: Establish a feedback loop to ensure that findings are reviewed, and actions are taken promptly. Encourage communication between security teams and the rest of the organization.
Compliance and Regulatory Considerations
When it comes to cybersecurity, compliance with industry-specific regulations and standards is non-negotiable. Internal Penetration Testing plays a pivotal role in meeting these requirements. Here’s a brief look at its relevance in the context of compliance:
Meeting Regulatory Demands:
HIPAA (Health Insurance Portability and Accountability Act): Healthcare organizations handling sensitive patient data are required to conduct internal security assessments, making internal testing critical.
PCI DSS (Payment Card Industry Data Security Standard): Payment processors and merchants must regularly assess their internal networks to safeguard cardholder data.
Data Protection Frameworks:
GDPR (General Data Protection Regulation): GDPR mandates that organizations protect the personal data of EU citizens. Internal Penetration Testing helps ensure data security.
ISO 27001: This internationally recognized standard for information security management systems emphasizes the importance of regular internal assessments.
Industry-Specific Requirements:
Financial Services: Banks and financial institutions often face stringent regulations. Internal Penetration Testing helps identify vulnerabilities in financial systems.
Critical Infrastructure: Organizations managing critical infrastructure must assess internal security to protect against potential cyberattacks.
Challenges and Best Practices
Internal penetration tests come with their share of challenges, but these best practices can help organizations conduct successful and effective testing:
Challenges:
Scope Creep: Define clear boundaries to prevent testing from straying into unintended areas.
Resource Constraints: Allocate skilled testers and necessary tools for comprehensive assessments.
Operational Impact: Minimize disruptions by monitoring the test closely and having an incident response plan.
Best Practices:
- Clear Objectives: Define specific testing goals to focus efforts on critical areas.
- Communication: Maintain open communication with stakeholders to ensure transparency.
- Continuous Improvement: Learn from each test to enhance security over time.
By addressing these challenges and implementing best practices, organizations can navigate internal penetration testing successfully, enhancing their security posture.
Summing Up
As we wrap up our exploration, let’s recap the key takeaways from this blog and emphasize the crucial role of internal penetration testing in today’s cybersecurity landscape.
Key Takeaways:
Internal Vulnerabilities Matter: While external threats often grab headlines, internal vulnerabilities can be just as devastating.
Proactive Defense: Internal Penetration Testing is a proactive approach to identifying and mitigating risks within your organization’s infrastructure.
Compliance and Regulations: It’s not just a security practice; it’s a compliance necessity in many industries.
Risk Reduction: Conducting internal tests helps reduce the risk of data breaches and operational disruptions.
Continuous Improvement: Learn from each test to continually enhance your security posture.
The Crucial Role of Internal Penetration Testing:
So, as you navigate the ever-shifting landscape of cybersecurity, remember that safeguarding your organization from within is not an option; it’s a necessity.
Internal Penetration Testing is your ally in this ongoing battle, helping you stay one step ahead of the threats lurking within your digital walls.
SecureLayer7: Your Trusted Partner in Internal Penetration Testing
In the relentless world of cybersecurity, where threats can come from all directions, safeguarding your organization is not just an option – it’s a mission-critical imperative.
At SecureLayer7, we understand the ever-evolving nature of cyber risks and the urgent need to bolster your defenses from within.
We are your trusted partner in Internal Penetration Testing, and here’s why you should choose us:
Expertise and Experience:
With years of hands-on experience, our elite team of penetration testers is well-equipped to simulate real-world attacks, uncover vulnerabilities, and safeguard your internal infrastructure.
Compliance Assurance:
We understand the complex web of regulations and compliance standards that govern different industries. Our Internal Penetration Testing services ensure that you not only meet but exceed these requirements, keeping you on the right side of the law.
Customized Solutions:
We don’t believe in a one-size-fits-all approach. Our experts work closely with you to tailor testing to your unique needs, whether you’re in healthcare, finance, or critical infrastructure.
Continuous Improvement:
Cyber threats are ever-evolving, and so are our methodologies. We help you learn from each test to strengthen your defenses continuously.
Proactive Defense:
With SecureLayer7 by your side, you don’t just react to threats; you proactively defend against them, ensuring your organization remains resilient and secure.
Choose SecureLayer7 as your partner in Internal Penetration Testing, and together, we’ll fortify your digital fortress, leaving no room for vulnerabilities to hide. Your security is our mission, and we stand ready to defend it.


