The hyper-connected business environment has made cyber threats a daily reality. Data breaches, ransomware attacks, phishing campaigns, and insider threats can strike without warning, causing severe operational disruption, financial losses, and reputational harm. It provides organizations with a systematic process to detect, contain, investigate, and recover from cybersecurity incidents while minimizing damage and restoring normal operations as swiftly as possible.
A well-structured Incident Response Plan is more than a checklist – it is a strategic framework that aligns people, processes, and technology to ensure readiness when incidents occur. It outlines the steps security teams should follow, from initial detection to post-incident analysis, and is reinforced by organizational controls that maintain consistency, accountability, and compliance.
Definition of Incident Response In Cybersecurity
Incident Response (IR) in cybersecurity is the structured process organizations follow to identify, contain, eliminate, and recover from security incidents such as data breaches, malware infections, or insider threats. It involves a coordinated set of actions by security teams, IT staff, and other stakeholders to address threats quickly, limit their impact, and restore normal operations. Unlike ad-hoc reactions, incident response is proactive and pre-defined, supported by documented procedures, trained personnel, and monitoring systems to ensure a consistent and effective approach.
A well-designed incident response framework is typically aligned with industry standards such as NIST, ISO 27035, or SANS, and outlines specific roles, responsibilities, and workflows. It not only focuses on immediate containment but also incorporates lessons learned, enabling organizations to improve their defenses and reduce the likelihood of future incidents.
Learn more about the core purpose of incident response in our detailed guide on Improving Incident Response with Real-Time Threat Monitoring and Analysis.
Why Incident Response is Critical For Organizations Today
Cyberattacks are becoming more sophisticated, frequent, and costly, leaving organizations with little room for error. A single security breach can lead to data loss, regulatory penalties, customer distrust, and operational downtime – sometimes within hours of the attack. Without an effective incident response strategy, businesses risk prolonged recovery times, higher financial damages, and reputational harm that can take years to repair.
Regulatory frameworks such as GDPR, HIPAA, and PCI DSS require organizations to have documented procedures for responding to security incidents. Failure to comply can lead to legal consequences and fines. In this high-risk environment, incident response is not optional – it is a critical component of any organization’s cybersecurity posture, enabling faster decision-making, coordinated actions, and minimal disruption during a crisis.
How It Helps Minimize Damage and Speed Up Recovery
Incident response helps organizations limit damage and recover faster by enabling a rapid, coordinated, and informed reaction to security threats. The process starts with early detection – often through continuous monitoring and threat intelligence – which allows teams to identify suspicious activity before it escalates. Immediate containment measures, such as isolating affected systems, stop the spread of the attack and protect unaffected assets.
Once the threat is neutralized, recovery efforts restore operations, repair affected systems, and validate that vulnerabilities have been addressed. Post-incident reviews identify gaps in defenses and improve security policies for the future. This end-to-end approach not only shortens downtime but also reduces financial losses, safeguards customer trust, and strengthens resilience against future cyberattacks.
What is an Incident Response Plan
An Incident Response Plan (IRP) is a documented, strategic framework that guides organizations in detecting, responding to, and recovering from cybersecurity incidents. It outlines specific roles, responsibilities, communication channels, and technical steps to be taken when a security breach, data compromise, or system outage occurs. The goal is to ensure that responses are swift, organized, and effective – minimizing damage and reducing recovery time.
An IRP is not a one-time document; it is a living framework that evolves alongside emerging threats, changes in technology, and lessons learned from past incidents. By standardizing response actions, it helps organizations maintain business continuity, comply with regulations, and build stakeholder confidence during a security crisis.
Definition and purpose
An Incident Response Plan is a formalized set of instructions and procedures designed to help an organization prepare for, detect, contain, eradicate, and recover from cybersecurity incidents.
The primary purpose of an IRP is to:
- Minimize impact on operations, finances, and reputation.
- Ensure a rapid and coordinated response by clearly defining responsibilities.
- Maintain compliance with laws, regulations, and contractual obligations.
- Improve organizational resilience by learning from incidents and strengthening defenses.
Core components of an incident response plan
A robust IRP typically includes the following key components:
- Preparation: Policies, training, and tools in place before an incident occurs.
- Detection & Identification: Processes for monitoring, logging, and verifying incidents.
- Containment: Short-term and long-term actions to limit the spread of the incident.
- Eradication: Removing malware, vulnerabilities, or malicious actors from systems.
- Recovery: Restoring systems, applications, and data to normal operations.
Examples of common cybersecurity incidents covered
An Incident Response Plan typically addresses a wide range of threats, including but not limited to:
- Ransomware attacks: Malicious encryption of files demanding payment for decryption.
- Phishing and spear-phishing: Social engineering emails designed to steal credentials or deliver malware.
- Distributed Denial of Service (DDoS): Overwhelming systems or networks to cause downtime.
- Insider threats: Malicious or negligent actions by employees or contractors.
- Data breaches: Unauthorized access, theft, or exposure of sensitive data.
Key Steps in The Incident Response Process
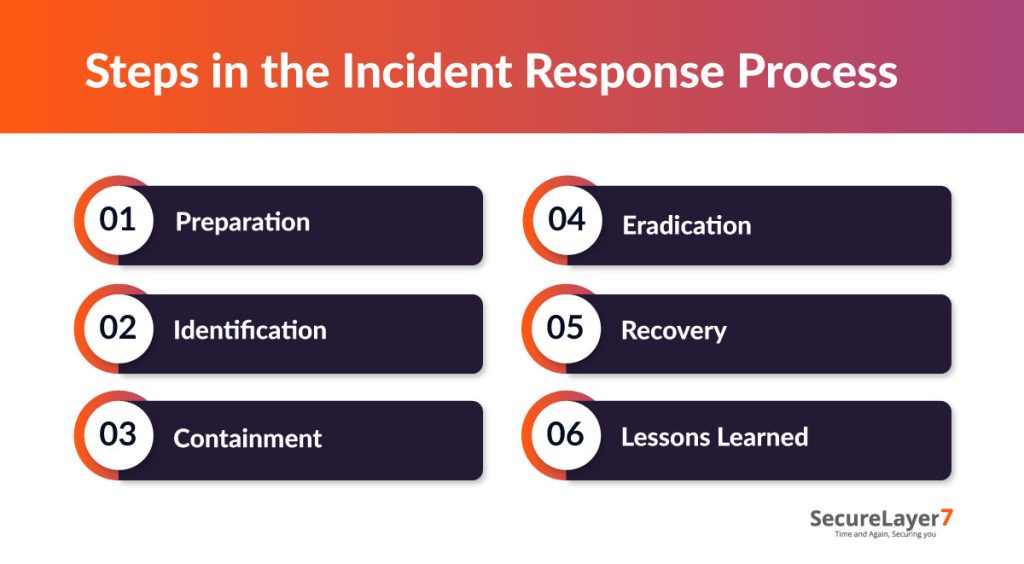
An effective incident response process follows a structured sequence of actions to detect, contain, and recover from security incidents while minimizing disruption. A clear framework ensures that every team member knows their role, enabling swift, coordinated action during high-pressure situations.
Following the below steps not only streamlines technical response but also strengthens communication, decision-making, and regulatory compliance.
Step 1: Preparation
Preparation is the most critical phase of the incident response lifecycle. It involves building the necessary infrastructure, processes, and team readiness to respond effectively to any cybersecurity incident. Without solid preparation, even the most advanced tools and skilled personnel may struggle to contain and remediate a threat in time. The following step is proactive, focusing on prevention and readiness rather than reaction.
Setting up policies, communication channels, and training
A strong preparation phase begins with clear security policies that define how incidents should be reported, investigated, and resolved. These policies should align with industry standards and compliance requirements such as NIST, ISO 27035, GDPR, HIPAA, or PCI DSS, depending on the organization’s sector.
Equally important are communication channels – both internal and external. Internally, security teams, IT staff, and executives should have dedicated, secure channels (e.g., encrypted messaging, incident hotlines) to coordinate during an incident.
Defining roles and responsibilities
Clearly defined roles and responsibilities ensure that during a security incident, there is no confusion about who should take action. An effective incident response team (IRT) typically includes:
- Incident Response Manager: Oversees the entire process, makes high-level decisions, and ensures proper escalation.
- Security Analysts: Monitor systems, investigate alerts, and perform technical containment and eradication.
Step 2: Identification
The Identification phase is a critical step in the incident response process where an organization detects and confirms whether a security incident has occurred, and understands its scope and impact. This phase lays the foundation for an effective response by ensuring incidents are promptly identified and accurately evaluated.
Detecting and confirming security incidents
Detection involves continuously monitoring systems, networks, and security tools (such as SIEM, endpoint detection, and firewalls) to spot suspicious or anomalous activities that could indicate a security event. Alerts may come from automated systems, user reports, or external threat intelligence.
The incident response team must confirm whether it is a genuine incident rather than a false positive. This confirmation process includes analyzing logs, alerts, network traffic, and other forensic data to verify the threat.
Understanding the scope and impact
After confirming an incident, the team assesses the scope and impact to comprehend how widespread and severe the incident is. This involves:
- Identifying affected systems, data, and users.
- Determining the attack vectors and methods used by the attacker.
- Measuring the potential damage to operations, data integrity, confidentiality, and availability.
Step 3: Containment
Containment is a critical phase in the incident response process focused on limiting the spread and impact of a cybersecurity incident once it has been identified. The goal is to prevent further damage, stabilize the situation, and prepare for the next steps of eradication and recovery. Containment strategies are divided into short-term and long-term approaches, each with distinct goals and actions.
Short-term containment to limit immediate damage
Short-term containment involves urgent, immediate actions designed to quickly halt the progression of the incident and stop the attack from spreading further. These measures are disruptive but necessary to protect the organization from escalating harm. Key short-term containment actions include:
- Isolating affected systems: Disconnect infected devices or systems from the network to prevent lateral movement of malware or attackers.
- Disabling compromised accounts or credentials: Lock down accounts suspected of being used by attackers to contain unauthorized access.
- Temporary network segmentation: Segment networks to contain the incident to a limited environment.
Long-term containment strategies
After stabilizing the immediate threat, long-term containment focuses on ensuring the attacker cannot regain access and on strengthening defenses to prevent recurrence. This phase is more controlled and deliberate, aiming to restore business operations safely while cleaning up vulnerabilities that were exploited. Typical long-term containment strategies include:
- Applying patches and software updates: Fix vulnerabilities that were exploited in the attack.
- Reconfiguring network segmentation: Enhance network controls to restrict future lateral movement.
- Revoking and replacing credentials: Change passwords and revoke access permissions compromised during the incident.
Step 4: Eradication
After containing the incident to prevent further damage, the next step is Eradication – completely removing the root cause of the incident and eliminating any malicious components from the environment. This phase ensures that attackers cannot re-establish their presence through the same vulnerabilities, misconfigurations, or compromised accounts.
Removing the root cause and malicious components
The eradication process starts with a thorough investigation to identify how the incident began and what weaknesses were exploited. Once identified, teams take targeted actions to remove both the cause and the effects of the attack. This may include:
- Deleting malware or malicious scripts from infected systems.
- Disabling and removing compromised user accounts or service credentials.
- Patching vulnerabilities in operating systems, applications, or network devices.
Step 5: Recovery
Recovery is the phase following eradication, focused on restoring affected systems, services, and operations back to normal and verifying their secure and stable functioning. The goal is to bring the organization back to full operational capacity while ensuring that no threats remain and that systems are resilient against future incidents.
Restoring systems and verifying normal operations
The recovery process involves carefully reintroducing systems into production after they have been cleaned, patched, and tested. Key actions include:
- Restoring data and systems from clean backups to ensure integrity and eliminate any lingering malicious code.
- Rebuilding or reimaging affected servers and endpoints in a secure environment.
- Monitoring network traffic and system logs closely to detect any signs of residual threats or re-compromise.
Step 6: Lessons Learned
The final phase of the incident response process is Lessons Learned – an often-overlooked step that is crucial for strengthening an organization’s security posture. Once the incident is fully contained, eradicated, and systems are recovered, teams should take the time to reflect, document, and analyze the event in detail.
Documenting findings and improving future response
A post-incident review (sometimes called a “post-mortem” or “after-action report”) should be conducted with all relevant stakeholders, including incident responders, IT teams, management, and, when necessary, legal or compliance officers. Key actions include:
- Documenting the full timeline of the incident – from detection to resolution.
- Identifying the root cause and any contributing factors.
- Evaluating the effectiveness of each step in the response process.
Incident Response in Cybersecurity Strategy
Incident Response (IR) is not an isolated function – it is a critical pillar of a broader cybersecurity strategy. When integrated effectively, it works alongside preventive controls, threat intelligence, and governance measures to create a layered defense that can withstand both anticipated and unforeseen attacks.
By embedding IR into the overarching cybersecurity strategy, organizations ensure that the right people, processes, and technologies are ready to take action. This integration not only improves resilience but also builds trust among customers, regulators, and partners who expect swift, effective handling of security threats.
For a deeper dive into how offensive and defensive approaches complement each other, see Offensive Security vs Defensive Security: Cybersecurity 101.
How it Integrates into Broader Cybersecurity Frameworks
Incident response is woven into comprehensive cybersecurity frameworks – such as NIST Cybersecurity Framework, ISO/IEC 27001, and CIS Controls – by aligning with their core functions: Identify, Protect, Detect, Respond, and Recover. IR focuses especially on the Respond and Recover functions but is coordinated with others to ensure:
- Continuous monitoring detects threats early.
- Protective measures limit attack surfaces.
- Established response plans mobilize teams to act promptly when incidents occur.
- Recovery procedures restore normal operations with minimized disruption.
- Lessons learned feedback improves policies and defenses.
Role in Compliance (e.g., PCI DSS, HIPAA, GDPR)
Incident response plays a critical role in achieving and maintaining compliance with major regulatory standards and frameworks designed to protect data and privacy.
- PCI DSS (Payment Card Industry Data Security Standard): Requires organizations handling payment card data to have an incident response plan that includes procedures for immediate containment, investigation, and reporting of data breaches involving cardholder information.
- HIPAA (Health Insurance Portability and Accountability Act): Mandates health organizations to implement policies and procedures for identifying and responding to security incidents that affect electronic protected health information (ePHI).
- GDPR (General Data Protection Regulation): Obligates organizations processing EU citizens’ data to detect personal data breaches promptly, notify authorities within 72 hours, and mitigate damage through effective incident response.
Collaboration Between Security Teams, IT, and Stakeholders
Effective incident response depends on strong collaboration across the organization. This multidisciplinary cooperation typically involves:
- Security Teams: Lead detection, analysis, containment, and eradication efforts using their technical expertise and tools.
- IT Teams: Support system recovery, patching, and infrastructure changes to restore secure operations.
- Management and Business Units: Provide guidance on business impact, prioritize critical assets, and coordinate communication internally and externally.
- Legal and Compliance: Ensure regulatory requirements are met and advise on risk and notification obligations.
Organizational Controls for Incident Response
Organizational controls are the policies, processes, and safeguards that provide the structure for effective incident response. They ensure that when a cybersecurity event occurs, actions are consistent, coordinated, and compliant with industry standards and legal requirements.
When implemented together as part of a layered defense strategy, these controls create a resilient environment where threats can be detected, contained, and resolved efficiently. Regular audits and updates to these controls ensure they remain effective against evolving cyber risks, helping organizations maintain readiness and reduce the impact of security incidents.
Administrative Controls: Policies, Compliance Requirements, Training, Incident Reporting Protocols
Administrative controls establish the policies, procedures, and human factors that govern incident response. Key elements include:
- Policies: Documented incident response policies define the expected behavior, roles, responsibilities, and procedures for managing security incidents. These policies ensure a consistent and compliant approach across the organization.
- Compliance Requirements: Adherence to regulatory and industry standards (such as PCI DSS, HIPAA, GDPR) mandates specific incident response controls, reporting timelines, and accountability mechanisms.
- Training: Regular training and awareness programs equip staff with the knowledge to recognize potential incidents, understand their roles in response, and follow established protocols effectively.
- Incident Reporting Protocols: Clear channels and procedures for timely reporting of suspected security events by employees and external parties enable early detection and rapid response.
Technical Controls: Access management, Network Segmentation, Encryption, System Monitoring
Technical controls provide the technological mechanisms to prevent, detect, and contain incidents. Important technical controls include:
- Access Management: Strict control of user permissions and authentication, including the use of multi-factor authentication (MFA), limits unauthorized access to systems and sensitive data.
- Network Segmentation: Dividing the network into zones restricts attacker movement within the environment, containing potential breaches to limited areas.
- Encryption: Protecting data at rest and in transit using strong encryption ensures confidentiality and integrity even if data is intercepted or accessed illicitly.
- System Monitoring: Continuous monitoring through security information and event management (SIEM) systems, intrusion detection/prevention systems (IDS/IPS), and endpoint detection technologies enables early detection of suspicious activities.
Physical Controls: Data center security, Restricted access areas, Environmental safeguards
Physical controls safeguard the tangible infrastructure and assets critical to IT and data security. These controls typically encompass:
- Data Center Security: Access to data centers should be tightly controlled with authentication measures such as key cards, biometric scans, and surveillance.
- Restricted Access Areas: Sensitive areas where critical infrastructure or data is stored are secured to prevent unauthorized physical entry.
- Environmental Safeguards: Protections against fire, flooding, power failures, and other environmental risks include fire suppression systems, uninterruptible power supplies (UPS), and climate controls to maintain operational stability.
Importance of layered Defense and Regular Control Audits
A layered defense approach, often termed “defense in depth,” combines these administrative, technical, and physical controls to create multiple barriers against threats. This redundancy drastically reduces the risk that a single control failure will lead to a successful attack.
Regular audits and assessments of these controls are essential to:
- Verify their proper implementation and effectiveness.
- Identify gaps or weaknesses that could be exploited.
- Ensure ongoing compliance with evolving regulatory requirements.
- Adapt to new threats and technological changes.
Challenges in Building and Executing an Incident Response Plan
Creating an Incident Response Plan (IRP) is essential for cybersecurity readiness, but building and executing it effectively can be challenging. Many organizations struggle with resource limitations, unclear processes, and changing threat landscapes that demand constant adaptation.
Common challenges include insufficient staffing or budget, communication breakdowns during high-pressure situations, and a lack of regular testing or updates to keep the plan relevant. Recognizing these issues early allows organizations to take corrective measures, ensuring their IRP remains practical, responsive, and capable of minimizing the impact of security incidents.
Resource Constraints
Limited resources often pose a significant challenge in building and sustaining a robust IRP. This includes:
- Staffing shortages: Insufficient qualified cybersecurity personnel to form and maintain an incident response team or to manage incidents promptly.
- Budget limitations: Restricted financial resources to invest in specialized tools, training, and technology crucial for effective incident detection and response.
- Time constraints: Difficulty dedicating enough time for plan development, employee training, and conducting incident response exercises amid competing business priorities.
- Tool limitations: Lack of adequate monitoring, forensic, and automation tools to enable quick detection, analysis, and containment.
Communication Breakdowns
Incident response requires clear, timely, and effective communication among different teams and stakeholders. Communication breakdowns can severely impair incident handling by causing:
- Delayed incident reporting: Employees or external parties may be unsure how, when, or whom to notify, leading to late detection and response.
- Misaligned roles and responsibilities: Ambiguity in communication channels can cause confusion about who is accountable for specific tasks.
- Poor coordination among teams: Lack of proper communication frameworks limits collaboration between IT, security, legal, management, and external parties.
- Inconsistent messaging: Inadequate communication planning may generate conflicting or unclear messages internally and externally, damaging trust and compliance.
Lack of Regular Testing or Updates
An incident response plan is not a one-time effort – it requires continuous maintenance and improvement. Many organizations struggle with:
- Failure to conduct regular drills and simulations: Without testing, teams cannot practice coordinated responses or identify weaknesses in plans and processes.
- Outdated plans and policies: IRPs can become obsolete due to evolving threats, changes in technology, or organizational shifts, diminishing their effectiveness during real incidents.
- Neglecting lessons learned: Without incorporating feedback from past incidents or exercises, recurring issues remain unaddressed.
- Compliance risks: Regulatory frameworks often mandate regular testing and updates, and failure to comply may lead to penalties.
Best Practices for an Effective Incident Response Program
A well-designed Incident Response Program goes beyond having a documented plan – it requires continuous improvement, team coordination, and the right blend of people, processes, and technology. The most effective programs are proactive, ensuring teams are trained, systems are tested, and procedures are ready to be executed the moment a threat is detected.
By following proven best practices such as regular simulations, cross-functional collaboration, up-to-date documentation, and leveraging AI and automation, organizations can respond to incidents faster and with greater precision.
Regular Testing and Simulations
- Conduct frequent exercises: Regularly test the incident response plan through tabletop exercises, simulations, and real-world scenario drills. This practice helps identify weaknesses or gaps in the plan and strengthens team coordination.
- Validate roles and procedures: Testing allows team members to rehearse their responsibilities, ensuring clarity and confidence during an actual incident.
- Update based on feedback: Use test results to refine and improve incident response processes, adapting to emerging threats and changes in organizational infrastructure.
- Increase readiness and reduce downtime: Regular practice leads to faster, confident responses, minimizing business disruption and recovery time.
Creating a Cross-functional Incident Response Team
- Diverse expertise: Assemble a team comprising cybersecurity professionals, IT personnel, legal, communications, and business stakeholders to cover all aspects of incident handling.
- Clear roles and responsibilities: Define each member’s duties explicitly, establishing escalation paths and decision authority to avoid confusion and delays.
- Foster collaboration: Encourage open communication and joint training to enhance coordination, maximize resource utilization, and enable holistic incident management.
- Benefits: Faster response times, comprehensive problem-solving, improved decision-making, and greater organizational resilience.
Keeping Documentation up to Date
- Maintain comprehensive incident response plans: Ensure the plan is well-documented, clear, and tailored to the organization’s specific risks and operational context.
- Update regularly: Review and revise documentation at least annually, or whenever significant changes occur in technology, threat landscape, or organizational structure.
- Include detailed playbooks: Develop scenario-specific playbooks with step-by-step actions for common incident types like ransomware, phishing, or data breaches.
- Record lessons learned: Document insights from each incident to refine procedures and prevent recurrence.
Integrating AI and Automation
- Speed and accuracy: Leverage AI-powered tools to automatically detect threats in real-time, prioritize alerts, and initiate containment actions faster than manual methods.
- Reduce human error and workload: Automation minimizes routine, repetitive tasks and allows security teams to focus on complex analysis and strategic response.
- Scalability and proactive defense: AI can handle large volumes of data and adapt to evolving threats, enhancing incident prediction and prevention capabilities.
- Continuous learning: AI systems evolve by learning from new incidents, improving detection accuracy and response efficiency over time.
- Examples of automation: Automated threat triage, incident ticketing, alert correlation, containment workflows, and resource mobilization.
Conclusion
A structured incident response approach is essential for minimizing the impact of cyber threats and ensuring swift recovery. By following a defined process – supported by clear policies, technical safeguards, and cross-functional collaboration – organizations can respond effectively, protect critical assets, and maintain business continuity.
Regularly reviewing and updating incident response plans and organizational controls keeps defenses aligned with evolving threats, while adherence to industry frameworks such as NIST, ISO 27035, and SANS ensures a resilient and compliant security posture.
Partnering with experienced cybersecurity experts can make all the difference in readiness and execution. SecureLayer7 offers specialized incident response and security services to help organizations detect, contain, and recover from cyber incidents with confidence.
Get in touch with SecureLayer7 to strengthen your defenses and ensure your business is prepared for whatever comes next.
Frequently Asked Questions (FAQs)
Incident response in cybersecurity is the structured process of identifying, containing, eliminating, and recovering from security incidents such as data breaches, malware attacks, or insider threats. Its goal is to minimize damage, restore normal operations, and prevent future occurrences.
An incident response plan provides a clear framework for responding to security incidents quickly and effectively. It ensures all stakeholders know their roles, reduces decision-making delays, limits financial and reputational damage, and helps maintain compliance with regulatory requirements.
Organizations should test their incident response plan at least once a year through simulations or tabletop exercises. Frequent testing may be necessary after major system changes, security incidents, or regulatory updates.
Incident response is typically led by an Incident Response Team (IRT) that includes security analysts, IT staff, legal and compliance officers, communications representatives, and executive sponsors. While the security team plays a central role, effective response requires collaboration across departments.