
The Cybersecurity Due Diligence Checklist Made Easy For VCs
May 25, 2023
Mastering the OWASP Top 10: A Comprehensive Guide
May 31, 2023
The global penetration testing market, projected to reach USD$2.7 billion by 2027 from USD$1.4 billion in 2022, shows how increasingly committed global businesses are to safeguarding their data and digital assets.
It begs the question, what has changed to drive this demand?
As remote or hybrid working environments emerge as the new normal, most businesses must facilitate secure remote access to off-site employees without increasing their risk exposure. Unfortunately, with unsupervised remote access comes a world of unknown, unmanageable, and damaging security exposures that put the organization and its data at immense risk.
Luckily, as bleak as it sounds, penetration testing programs are an excellent means to eliminate such underlying vulnerabilities and increase the overall security posture of your infrastructure, data, and other digital assets.
This guide to creating your own comprehensive penetration testing program will cover the following:
- The purpose of a penetration testing program
- What is a good pentest program?
- Anatomy of a pentest
- How to build your pentest program
- Factors to consider when creating a penetration testing program
- Get comprehensive penetration testing from SecureLayer7
This article will explore why pentesting programs are important, their anatomy, and a recommended approach to building your own robust penetration testing platform.
The Purpose of a Penetration Testing Program
As the list of exposures continues to grow, the primary purpose of any penetration testing program must be to continuously improve its threat detection and response to address potent vulnerabilities.
Additionally, it must serve as a tool that enables your organization to reduce its attack surface and weak spots such that it becomes a less likely target amongst attackers.
What is a Good Pentest Program?
A good penetration testing program should have well-established success requirements. It should be able to comprehensively assess and gather information on your organizational assets under its coverage to identify vulnerabilities. Once uncovering the vulnerabilities, it should be able to perform asset classification and threat modeling to identify the most pressing issues.
Upon exploitation, the tester should be able to pivot the pentest program to perform exploits on multiple layers of the organization’s systems. It should provide actionable business reports with multi-layered recommendations to address issues effectively.
If a breach occurs, the program’s detection, response, and remediation should be quick and effective so that organizations face minimal damages, downtimes, and data theft.
Anatomy of a Pentest
The best penetration tests follow a well-planned methodology that allows testers to strategically plan and implement tests to achieve the best outcomes.
When you skip steps and proceed to target a system without a strategic approach, you are most likely to suffer from publicized breaches that can subject you to diminished productivity, expensive fines, public scrutiny, and reputational damage.
Here are the basic steps any pentester must follow as a planned and practical approach to penetration testing:
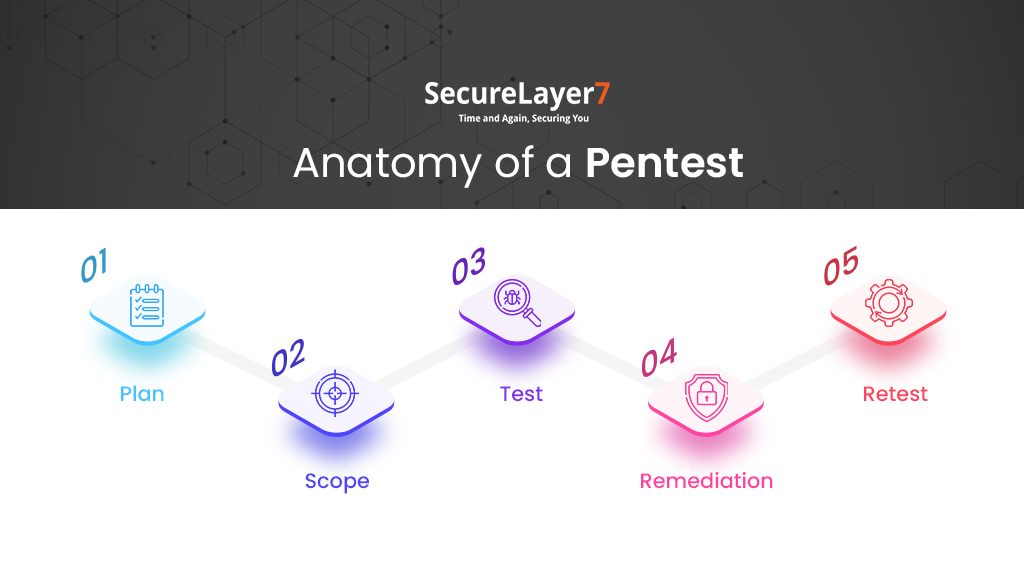
Stage 1: Plan
In the first planning stage, you map out all the assets, including software, devices, and networks you plan to test. You also set realistic timeframes for your penetration test to ensure its completion is within a prescribed time window.
Stage 2: Scope
The scope defines the areas of the target business that will be subject to penetration testing. As companies handle a substantial volume of sensitive data, intellectual property, and trade secrets, they may not want to compromise through an intrusive test.
This is where your organization decides the critical assets that will be pentested and those that won’t. It also gives the penetration tester clear direction into the depth and resources they will need for the test.
Stage 3: Test
Now is when the actual testing begins, where the pen testers typically perform automated scanning to scale the target systems to weed out Common Vulnerabilities and Exposures (CVEs). Automated testing helps testers gain a better understanding of the current security posture of the target systems.
It also provides insights into the most obvious weak spots and what direction to take for the penetration test.
Simultaneously, the penetration testing team conduct manual testing to uncover more complex business logic vulnerabilities that an automated scanner may miss. It is worth noting that if you want to maximize the effectiveness of your penetration test, it is best to employ a professional pentester with critical expertise and experience in the field.
Once the tester uncovers all vulnerabilities, they map out their attack strategy, devise the payload, launch their exploits, observe the results, and document the findings through a detailed business report. This report will prove vital for the target business to understand the implications of each risk and how to remediate them.
Stage 4: Remediation
Remediation is the most critical stage where the testers fulfill the objectives of the penetration test. The penetration testing team leverages the documented vulnerability information to devise a mitigation strategy that addresses all the uncovered weak spots and vulnerabilities.
Stage 5: Retest
Achieving the best results from penetration testing can be an iterative process. Sometimes, inaccurate patchwork may cause additional problems or fail to address all vulnerabilities. Retesting the patched areas can help identify and mitigate such errors. Adjust your retesting focus on smaller areas to double-check if you successfully solved the issues.
There are limitations to how many times you should perform retesting. Ideally, it stops when the tester is satisfied with the target’s system’s new security posture.
How to build your pentest program
Building a penetration testing program for your organization can be challenging and requires a finetuned methodical approach.
We have simplified the process to a few simple steps to make creating your own penetration testing programs easier.

Step 1: Set Objectives
For your first program, it is better to define realistic objectives you hope to achieve with your program and only include what your organization can handle. They help you devise penetration testing programs that address your unique requirements and enhance your security stance.
Carefully consider them, as they will define how you proceed with your program design.
For instance, let’s assume your organization wants to address suspected vulnerabilities in a few critical components and subsequently acquire PCI-DSS compliance. Here, the realistic objectives drive your program design, such that it addresses all problems within your essential assets to accomplish PCI-DSS compliance.
Step 2: Identify Critical Assets
Every organization has a different outlook as to what are their critical assets. What you consider an asset vital to your organization may differ from another, so dive deep, assess, and determine the assets that might cause you the most harm if exploited.
Once you know the answer, you can build your pentest program to comprehensively cover every aspect of your assets that can potentially cause you harm. You can still include testing of lower priority assets into the coverage at a diminished priority and frequency.
Step 3: Determine Asset Updation Cycles
System changes and updates don’t always produce the desired results. Often, the very updates designed to address a weak spot in a critical asset can increase the exposure of another.
Your penetration testing program should be able to continuously monitor, track, and spot vulnerabilities in your assets every time you make a system change or update.
Step 4: Check for Major Infrastructure Changes Over the Course of the Test
Every time a significant infrastructure is made, such as cloud migration or major hardware upgradation, the odds are that it may come with its own set of new security exposures due to human error.
If not mitigated quickly, such vulnerabilities can give way to severe breaches. Your program must have comprehensive coverage of such assets undergoing significant changes.
Try and include tests with a smaller area of focus to quickly check if problems persist without needing a complete system scan. Also, schedule your programs to run tests before and after every significant infrastructure change.
Remember, the higher the pentesting frequency, the more effectively you can train and perfect your program’s effectiveness in addressing emerging vulnerabilities.
Step 5: Plan Logistics
Decide how and what approach your program will take to uncover vulnerabilities. For instance, you can decide whether your program will conduct black or grey box testing. You may have limited time to conduct tests and address vulnerabilities in specific scenarios.
In such instances, it makes sense to conduct grey box testing. Other times when you have ample time and resources to comprehensively conduct tests, you can take a black box approach.
Step 6: Define the Scope
Finally, it’s time to decide the scope of what assets you will include in your penetration testing program. A good practice is to limit the focus area to cover only the most essential assets. This way, your program can conduct extensive tests and uncover vulnerabilities without taking too much time.
Factors to Consider When Building a Penetration Testing Program
Let us look at some critical factors to consider when building your penetration testing program:
1. Complexity
Gauge the volume of your organization’s data, the risks you face in light of a breach, the likelihood of you being a target, and the access levels issues that increase your risk exposure.
By doing so, you can include the assets necessary for penetration testing while excluding those with confidential business data you don’t want to be included in the testing scope. It decreases the program’s complexity while making it more usable and manageable for its users.
2. Spend vs Risk
A good piece of advice is to base your program expenditure proportionate to the organizational risk you face. When your risk is low and expenditure is high, it indicates that your program expenditure and complexity are too high and disproportionate to the low level of risk your organization faces.
Likewise, when your risk is high and program expenditure is low, it indicates that your program spending and complexity are too low and disproportionate to the high level of organizational risk.
Your goal should be to match your program spending such that the complexity and expenditure justify the data breach risk that you face.
3. Pentest Objective
The main focus areas for your penetration testing program should include validating attack vectors, identifying application vulnerabilities, and optimizing access control.
For your program to validate attack vectors, it must make sure to include vulnerability exploitation, input validation, authentication & authorization testing, lateral movement, and data exfiltration.
Form logic, input validation, authentication, authorization, and third-party vendor security are some of the most commonly vulnerable areas in applications. Make sure your program tests and uncover vulnerabilities in such fields.
Finally, your program must test the strength of your access control tools, processes, standards, and clearance levels to identify weak spots.
Types of Pentests
There are numerous types of Penetration Tests to include in your application, such as:
- Application Penetration Testing
- Mobile Application Security
- Thick Client Application Security
- VoIP Penetration Testing
- On-Demand Penetration Testing
- Cloud Infrastructure Penetration Testing
Depending on your objectives, you must decide what type of penetration tests you will include in your program.
The approach your testers will be undertaking should also influence how you build your program. Let us look at some of the approaches to penetration testing.
- Grey Box Pentest
If your need for results is immediate, your program can facilitate grey box pentest. In a grey box test, you provide the testers with information on the covered assets, login credentials, permissions, and weak spots, excluding the source code prior to the testing.
- Black Box Pentest
A more realistic alternative approach is Black Box Pentests, where you provide the tester with no prior knowledge of the organization’s functions or login credentials. Like a real-world attack scenario, the tester must perform their reconnaissance, scale the target systems, gather information, and launch their exploits from scratch.
- White Box Pentest
A white box test is where you provide your pentester with all system and network information, including source codes, network credentials, and network maps. It is the quickest way to perform a penetration test.
Get Comprehensive Penetration Testing from SecureLayer7
SecureLayer7’s continuous penetration tests help customers to spot high-risk vulnerabilities such as SQL injection, Cross-Site Scripting, server-side request forgery, components with known vulnerabilities, broken access control, weak identification & authentication, security misconfigurations, sensitive data exposures, XML external entities, insecure deserialization, and insufficient logging & monitoring which may result in severe attacks.
Our robust services include the following:
- Application Penetration Testing
- Mobile App Penetration Testing
- Thick Client Penetration Testing
- VOIP Penetration Testing
- On-Demand Penetration Testing
- Cloud Penetration Testing
We are renowned amongst SMEs and large organizations that use our penetration testing services to perform and act on the vulnerabilities and insights uncovered from our continuous pen tests.
Do you suspect the presence of vulnerabilities in your AWS, Azure, and Kubernetes cloud infrastructure? Don’t fret. We additionally help businesses securely maintain their cloud infrastructure by detecting and quarantining vulnerabilities in the most renowned platforms at a reasonable cost. Our services reduce your exposure to exploits while maintaining compliance with industry standards and regulations.
Our developers have designed our penetration tests to address every aspect of your business and the unique threats facing them. Contact us to find out how we identify and mitigate all your organization’s network vulnerabilities.
============================
Summary:
With the increasing global commitment businesses are placing to safeguard their data, infrastructure, and digital assets to combat emerging threats, it may be time for you to start prioritizing your own. There is no better way to optimally secure your organization than creating your own penetration testing program. However, creating and tailoring a penetration testing program to address an organization’s unique security requirements may be a tricky process that needs certain crucial considerations. Click here to learn how to overcome such challenges and create a winning penetration testing program that keeps your sensitive data and critical assets safeguarded at all times.


