
Cyber Security Webinar 2021 – The Emergence of CyberThreat Evaluation
July 13, 2021
What is Data Lake? Understanding Data Lake Building Security
July 29, 2021
This article will take you through each step that essentially contributes to the whole process of AWS vulnerability scanning.
Before delving deep into all the methods and remedies one can run to prevent AWS vulnerability, let us reflect on the significance of keeping it secure and why you as an individual or as an enterprise need to be alert.
Limitations of AWS and the security it provides
It is essential to understand that not all cloud platforms like AWS provide vulnerability management.
Thus, all vulnerabilities and their management are extended.
Here are some of the limitations of AWS security.
The Shared-Responsibility Model
AWS has the framework of a shared-responsibility model which means that the client is responsible for securing data that is deployed on the cloud.
Furthermore, the shared-responsibility model in a nutshell can be understood as AWS taking care of its various cloud platforms by keeping a check on their weaknesses.
However, the data that has been deployed on the platform through the customer’s end has to be taken care of by the customers themselves.
This sometimes results in negligence on the security of the data from the customer’s end. Had AWS taken care of the part, there would have been less concern about data breaches.
Multi-Factor Authentication
A significant number of AWS services lack multi-factor authentication, do not use network segmentation (through AWS security groups), and give an excessive number of rights. In big cloud deployments, it might be challenging to locate these assets and determine their value.
Compliances to go along with
Apart from this, many organizations are bound to comply with standards like HIPAA, SOX, PCI DSS, etc. To ensure that the requirements of these standards are being fulfilled, the cloud has to be free of all weaknesses.
What is AWS vulnerability scanning?
The process of automatically finding and reporting possible security gaps or vulnerabilities in Amazon Web Services (AWS) infrastructure, such as network settings, operating systems, applications, and other resources, is referred to as AWS Vulnerability Scanning.
This assists in the identification of possible threats and enables companies to take preventive actions to reduce security risks, secure sensitive data, and maintain compliance with security requirements.
How do you conduct an AWS vulnerability scan?
Here are a few ground rules to follow before you go ahead with the AWS vulnerability scan.
- Determine what will be tested by outlining the specific devices, software, and infrastructure that will be put through their paces. This ensures that the testing is focused on the areas that matter most to the company and that the findings are useful.
- Start with a quick check. Before diving into an in-depth investigation, it’s a good idea to find any obvious security flaws using a vulnerability scanner like AWS Inspector or Astra’s vulnerability scanner. This will serve as a starting point for assessing the security level and determining where to focus improvement efforts.
- Define the test. Decide if a network penetration test, an application penetration test or a hybrid of the two will be performed. Insights gained from this will be used to choose adequate testing methods.
- Spell out what is expected of everyone involved in the test, from stakeholders to the penetration testing firm (if the test is being outsourced).
- Develop a schedule for the technical evaluation to make sure testing is completed in a timely manner.
- Establish breach protocols. Plan for what to do if the test finds that security has been compromised. This will guarantee a faster reaction and lessen the damage from any breach.
- To make sure a penetration test is done legally and ethically, it is important to have formal permission from all relevant parties beforehand.
Companies can make sure their AWS penetration tests are well-planned, efficient, and up to par with their security standards if they adhere to these guidelines.
Conducting an AWS vulnerability scan
Conducting an AWS vulnerability scan involves several steps, including the following.
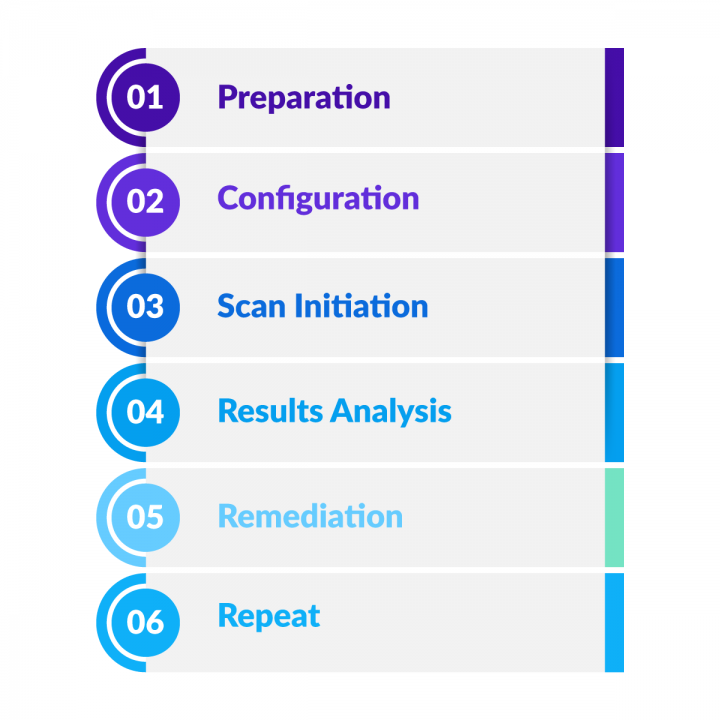
- Preparation: Gather information about the AWS environment, including the assets and components that will be included in the scan.
- Configuration: Configure the vulnerability scanner with the necessary settings, including the target systems, scan options, and authentication credentials.
- Scan initiation: Launch the scan and allow the scanner to run and collect information about the AWS environment.
- Results analysis: Review the scan results to identify potential vulnerabilities and security weaknesses. The results should be organized by severity and prioritized for remediation based on the risk they pose to the environment.
- Remediation: Address the identified vulnerabilities and security weaknesses by implementing appropriate remediation actions, such as applying patches, configuring security settings, or updating security policies.
- Repeat: Repeat the scan process to verify that the remediation actions were effective and that the environment remains secure.
It is important to keep in mind that AWS vulnerability scanning is just one aspect of a comprehensive security strategy. Organizations should also implement other security measures, such as firewalls, intrusion detection systems, and access controls, to protect their AWS environment.
Picking the right tool
Picking up the right tool is the most significant part of the process as different tools allow you to work with different resources, and with the right tool, you will be able to diagnose the weaker areas efficiently.
Here is the list of tools that can and should be used when conducting an AWS vulnerability scan.
AWS Config
AWS Config is a service offered by Amazon Web Services (AWS) that enables you to assess, track, and evaluate the configurations of your AWS resources.
With AWS Config, you can automate the assessment of resource configurations, monitor changes in configurations, and evaluate configurations against desired settings.
AWS Config also provides detailed resource configuration history, making it easier for you to understand changes made to your resources over time and quickly troubleshoot issues. Additionally, you can use AWS Config to set up compliance checks and ensure that your resources are aligned with industry or organizational standards.
AWS Config integrates with other AWS services and supports a variety of resource types, including EC2 instances, VPCs, RDS databases, and more. The service can be accessed through the AWS Management Console, the AWS CLI, and APIs.
Astra
Astra is a web application penetration testing software that is used by security researchers and penetration testers to identify vulnerabilities in web applications. It has a modern user interface and is equipped with a comprehensive set of tools and features that make it easier to conduct security assessments.
Some of the key features of Astra include:
- Vulnerability Scanning – Astra automates the process of discovering security vulnerabilities in web applications.
- Manual Testing – Astra provides manual testing tools and techniques to give testers the flexibility to test and verify vulnerabilities that may have been missed by automated scans.
- Reporting – Astra generates detailed reports that highlight the findings and recommendations for remediation.
- Collaboration – Astra enables collaboration between teams and integrates with other security tools to streamline the penetration testing process.
Astra is designed to be user-friendly and accessible to both experienced and novice testers, and it is regularly updated with the latest vulnerabilities and attack techniques.
Intruder
To prevent expensive data breaches, you may use Intruder, an online vulnerability scanner, to discover where your digital infrastructure is vulnerable.
Cloud Custodian
Cloud Custodian is a rules engine for controlling resources in the public cloud. It lets people set rules that make it possible to have a safe, cost-effective cloud architecture.
It’s a simple, adaptable platform that brings together a company’s disparate ad hoc scripts under a single roof, complete with standardized metrics and reporting.
With the help of policies, Cloud Custodian checks the status of your cloud infrastructure against your ideal configuration.
Analyze and Fix Vulnerabilities – The Final Step
Delivering a report with findings and suggestions is the last stage of a penetration test. After the test is complete, all of the data acquired must be compiled, including details about the vulnerabilities found, the exploitation techniques utilized, and the results of the attacks.
The report must include a comprehensive evaluation of the target’s overall security posture and suggestions for shoring up the target’s defenses.
Both technical and non-technical stakeholders should be able to comprehend the report after reading it, thus, its writing and presentation should be clear and succinct.
The report should also provide a risk assessment that ranks the vulnerabilities according to the severity and frequency with which they might be exploited.
There should be a debriefing session between the penetration tester and the customer when the findings of the test are presented.
This meeting is an opportunity for the tester to go through the test findings with the client and provide advice on how to strengthen security.
Verification and follow-up are the last phases of a penetration test. This includes checking to see whether the security flaws have been patched and the suggestions made.
This is a crucial stage because it verifies that the company has enhanced its security by taking measures to counteract the threats that have been identified.
Get complete coverage with comprehensive penetration testing from SecureLayer7
SecureLayer7 is the solution that can solve all your pen testing issues. With a broad range of services like Application Penetration Testing, Mobile Application Security, Thick Client Application Security, VoIP penetration testing, On Demand Penetration Testing, you can secure all your assets with one tool.
Explore pen testing with one of the best players in the realm of cybersecurity. Check out SecureLayer7 now.


