
7 Best Penetration Testing Service Companies In India
May 5, 2023
The 6 Steps In The Penetration Testing Process
May 15, 2023
On March 29th, 2023, the cybersecurity world was alerted to a troubling issue – the 3CXDesktopApp had been compromised. The implications of this supply chain campaign are significant, given the global distribution of various Trojanized versions of their VOIP software. This attack has impacted Windows and macOS clients, with growing concerns surrounding the safety and security of VOIP use on a large scale. Although some users had already reported alerts by the middle of March, many assumed they were false positives. As individuals and companies alike depend on these VOIP technologies for communication, the need for heightened cybersecurity measures has never been more apparent.
What is the 3CXDesktopApp?
The 3CXDesktopApp is a legitimate voice and video conferencing software offering call, video, and live chat over the internet. It was developed by 3CX, a business communications software company founded in 2005 when Voice over Internet Protocol (VOIP) was still an emerging technology. According to the company website, 3CX has approximately 600,000+ customer companies, with over 12 million daily users in 190 countries.
The software-based PBX phone system is currently available on Windows, Linux, Android, and iOS, as well as a Chrome extension and a Progressive Web App (PWA) browser-based version of the client. The 3CX website lists customer organizations in sectors including:
- Manufacturing and Automotive
- Food and Beverage
- Hospitality
- Managed Information Technology Service Providers (MSPs)
Campaign Overview
The 3CX Phone Management System can be implemented on-premises. We also came across a Reddit post where a user reported suspicious activity after updating the 3CX desktop on March 24, 2023. According to the user, the 3cxdesktopapp.exe program accessed browser caches, as revealed by EDR file history data.
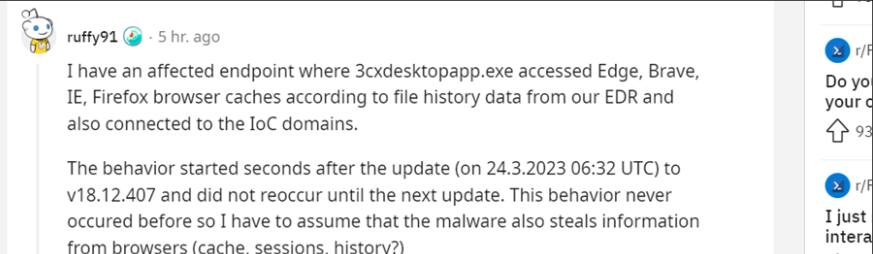
Figure: Reddit Post
According to 3CX, the recent attack resulted from infected bundled libraries that were compiled into the Windows Electron App through GIT. The vendor has also stated, “Electron Windows App shipped in Update 7, version numbers 18.12.407 & 18.12.416, includes a security issue.
Anti-Virus vendors have flagged the executable 3CXDesktopApp.exe and, in many cases, uninstalled it from the system. Electron Mac App version numbers 18.11.1213, 18.12.402, 18.12.407 & 18.12.416 are also affected.
The .msi file, when executed, drops two malicious files – “ffmpeg.dll” and “d3dcompiler_47.dll” – in the location C:\Users\[user_name]\AppData\Local\Programs\3CXDesktopApp\app.
The infection begins when the application file “3CXDesktopApp.exe” loads “ffmpeg.dll”. Then, “ffmpeg.dll” decrypts the encrypted code from “d3dcompiler_47.dll”, which seems to be a shellcode to gain access to the compromised system.
This shellcode loads another DLL file that tries to access the IconStorages GitHub page to find an .ico file that contains the encrypted shellcode for interacting with the Command-and-Control (C&C) server. After locating the C&C server, the backdoor establishes a connection to retrieve the potential final payload.
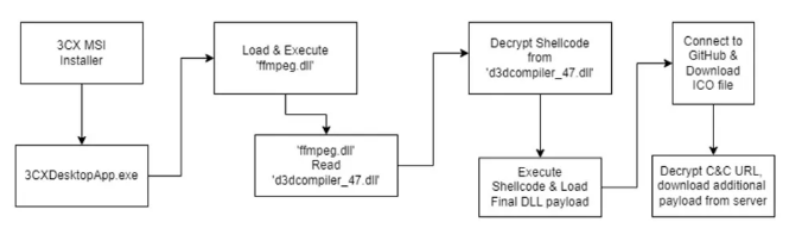
Figure: Infection Chain
3CX confirms software is compromised
3CX CEO Nick Galea confirmed on Thursday, 30th March 2023 morning in a forum post that the 3CX Desktop application was compromised to include malware. As a result, Galea is recommending all customers uninstall the desktop app and switch to the PWA client instead.
“As many of you have noticed, the 3CX DesktopApp has malware. It affects the Windows Electron client for customers running update 7. It was reported to us yesterday night, and we are working on an update to the DesktopApp, which we will release in the coming hours,” Galea shared in the 3CX forums on 29th March 2023.
MITRE ATT &CK Techniques
| Tactic | Technique ID | Technique Name |
| Initial Access | T1195 | Supply Chain Compromise |
| Execution | T1204.002 | User Execution: Malicious File |
| Defense Evasion | T1140 T1027 T1574.002 T1497.003 | Deobfuscate/Decode Files or Information Obfuscated Files or Information Hijack Execution Flow: DLL Side-Loading Virtualization/Sandbox Evasion: Time-Based Evasion |
| Credential Access | T1555 T1539 | Credentials from Password Stores Steal Web Session Cookie |
| Command and Control | T1071 | Application Layer Protocol |
What you should do?
If you run the 3CX compromised versions, we highly recommend you check that:
- No detection exception is configured for the 3CX applications in your security solutions (EDR, AV, etc.).
- All detection tools are updated with appropriate rules and Indicators of Compromise (IoC).
- Your 3CX apps are upgraded to the latest clean version (18.12.422) or uninstalled in favor of the PWA web-only solution.
The best way to go about this is to uninstall the app (if you are running Windows Defender, it’s going to do this automatically for you, unfortunately) and then install it again.
Conclusion
The potential damage caused by the 3CXDesktopApp supply chain attack is significant, including the theft of sensitive user data.
Organizations affected by this attack should immediately take steps to prevent it from causing widespread harm. The current investigation suggests that the threat actor behind this attack is skilled and persistent.
The consequences of such an attack, such as financial loss, reputational impact, and the loss of customer trust, are severe.
Organizations must remain vigilant and take proactive measures to secure their supply chains to prevent similar attacks in the future.
To prevent the compromission of systems from third-party applications, it is recommended to use updated application versions, always use EDR, Antivirus with updated signature database, and follow the principle of least privileged to avoid complete system compromission.
Always follow and keep updated about the security information of installed applications through their security update page or security advisories. For more information on how to get started connecting to SecureLayer7.