You’re about to wrap up work when suddenly an email pops up from someone in your team. The subject line reads, “Need credentials ASAP to resolve system outage.”
It feels urgent, and because the sender’s name looks familiar, you respond without second-guessing. Minutes later, you’ve unknowingly handed over sensitive login details, not to your colleague, but to an attacker impersonating them.
That’s the essence of social engineering. It doesn’t rely on breaking encryption or bypassing firewalls; it exploits trust and predictable routines.
Attackers trick people into giving away passwords, financial data, or other critical information, often opening the door to much larger breaches like ransomware or network compromise. Data also confirms the gravity of the issue: 59% of organizations globally experienced a ransomware attack in 2024.
This blog walks through various social engineering tactics, its types, and best practices for prevention.
What is Social Engineering?
Social engineering refers to a kind of cyber threat that involves psychologically manipulating employees in an organization to reveal sensitive information, or perform specific actions, such as disclosing passwords or providing system access.
The attacker, through various means, gains the trust of people so that they lower the guard, and then encourages them to take actions, such as clicking on web links or opening a malicious attachment.
Social engineering is not a cyber attack in the true sense. It’s more about the psychology of persuasion.
Types of Social Engineering Attacks
Social engineering attacks are of several types, including:
Phishing
Phishing is a type of cyber attack where scammers impersonate trusted organizations or individuals, such as banks, employers, or well-known companies to trick people into revealing sensitive information like passwords, credit card numbers, or login credentials.
For example, someone receives an email pretending to be from their bank, asking them to verify their account by entering their password on a fake website.
Smishing
Smishing is a type of phishing scam that is delivered through SMS messages to trick individuals into clicking malicious links or sharing confidential details. It happens when people get texts claiming urgent banking issues or deliveries, prompting action via a harmful link.
For example, someone gets a text saying their bank account is locked with a link to a fake website asking for their login credentials.
Whaling
Whaling is a more sophisticated kind of phishing attack that targets high-level executives, such as CEO, CFO, CTO, within organizations. Attackers conduct thorough research and contact company leaders with personalized, authentic-looking messages to steal data or authorize transactions.
For example, a CFO might get a convincing email from someone posing as the CEO, directing them to transfer funds to a fraudulent account.
Baiting
Baiting is a social engineering scheme that tempts users with free offers or physical items to inject malware in their system. It occurs when users download free software or plug-in containing malicious code.
Baiting can occur via physical dropped USB drives labeled with enticing terms like “Employee Benefits” or “Confidential,” which when plugged into a computer automatically install harmful software.
Diversion Theft
Diversion theft involves intercepting goods, funds, or information by altering delivery or payment details. It occurs when hackers impersonate suppliers or clients to convince staff to send shipments or payments to the wrong address.
For example, a company receives a last-minute email update on shipping instructions, leading them to send a package to an unintended person instead of the authorized recipient.
Business Email Compromise (BEC)
Business Email Compromise (BEC) is a type of social engineering scam where attackers use spoofed business emails to manipulate employees into sending money or data.
For example, an employee receives an email that appears to be from the company MD instructing them to quickly wire funds to a vendor’s new bank account controlled by the attacker.
Quid Pro Quo
Quid pro quo is a scam offering services or rewards in exchange for sensitive information. It occurs when attackers pose as IT support or contest organizers offering help or prizes to extract credentials.
For example, a scammer pretends to be tech support, offers to fix a non-existent computer issue, and asks the victim to share their password.
Pretexting
Pretexting is a social engineering attack where a hacker creates a genuine looking scenario to manipulate the target person into disclosing private information. It happens when attackers pose as colleagues, auditors, or officials and gradually build trust to request sensitive data.
For example, an attacker impersonates an HR rep and convinces an employee to reveal their Social Security number for “payroll verification.”
Watering Hole
Watering hole attacks target specific websites or online platforms frequently visited by the intended victims. Attackers compromise these websites, injecting malicious code or links that infect the visitors’ devices.
Honey Trap
Honey trap attacks exploit human vulnerabilities, particularly in romantic or personal relationships. Attackers create fictitious online personas to establish trust over time, often engaging in extended conversations or emotional manipulation before attempting to extract sensitive information or gain unauthorized access.
These attacks can be highly targeted, focusing on individuals with access to valuable data or systems.
Tailgating
Tailgating occurs when an unauthorized individual gains physical access to restricted areas by following an authorized person through controlled entry points without proper authorization.
Often, the attacker relies on social cues like politeness or distraction, making the victim less likely to question their presence. This tactic bypasses electronic access controls entirely, leaving physical security systems ineffective.
Rogue Security Software
Rogue security software deceives users into downloading or purchasing fake programs that claim to protect their systems but instead introduce malware or expose vulnerabilities.
These scams often use alarming pop-up warnings, fake virus detections, or urgent prompts to pressure the user into immediate action. Once installed, the software can steal data, damage files, or demand payment for “removal.”
Dumpster Diving
Dumpster diving involves attackers physically searching through trash or discarded materials to find valuable information, such as documents containing passwords, account numbers, or sensitive business data.
Discarded storage devices, printouts, or handwritten notes can also be targeted. This low-tech method is surprisingly effective when organizations fail to properly destroy confidential materials before disposal.
Pharming
Manipulating DNS (Domain Name System) settings or injecting malicious code into compromised websites, redirecting users to fraudulent sites that mimic legitimate ones, is known as pharming.
Targeted victims believe they are visiting trusted domains, but instead, their sensitive information is captured by attackers. Unlike phishing, pharming does not always require user interaction and can affect multiple users simultaneously.
Scareware
One such attack that plays on individuals’ fears by presenting false alerts or warnings about malware infections on their devices is known as Scareware. The attackers can urge victims to download malicious software disguised as security tools.
The Lifecycle of a Social Engineering Attack
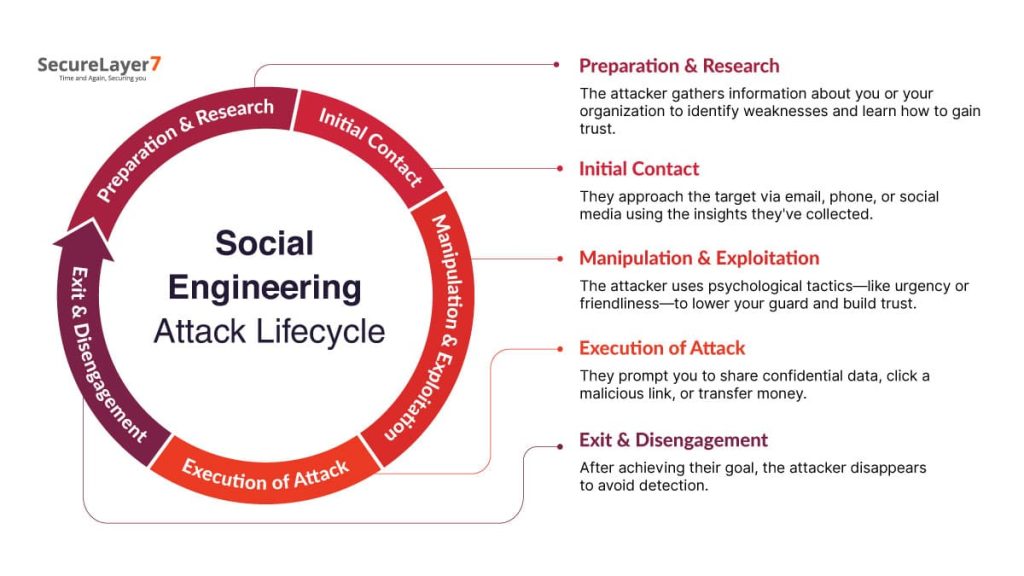
- Preparation & Research
In the first stage, the hacker tries to understand your psychology to learn about you and your organization. They study anything that may help them understand your psychology to win trust or spot a weakness. - Initial Contact
Now, when the initial homework is done, they reach their target through email, phone, or a direct social media message. These contacts are designed to seem trustworthy and relevant. The goal is to establish a connection and set the stage for further engagement.
- Manipulation & Exploitation
While crafting the message, they play with emotions like creating a sense of urgency. They may start with a friendly conversation to gain your trust. The overall motive is to influence you to lower your guard.
- Execution of Attack
Once trust is established, the attacker makes their final move. They trick you into sharing confidential info, clicking a harmful link, or transferring money to achieve their goal. - Exit & Disengagement
After the objective is accomplished, the attacker erases evidence, sever communication channels, and disappear from all contact points. This cautious exit prevents tracing.
Common Warning Signs
- Unexpected email with Attachments or Links: If you receive an email or text with an urgent tone, emotional prompts, or security warnings asking you to click. Take a pause and verify before clicking.
- Unusual Requests: Be alert on receiving unexpected payment instructions or odd attachment from a colleague or executive. If you smell something suspicious, confirm it from the sender directly.
- Urgent Demands: Never been in a hurry to click an offer link that claims to expire soon.
- Too-Good-To-Be-True Offers: Be skeptical of offers involving money, prizes, or rewards for sharing personal or company information. If it sounds too good to be true, it’s probably a scam.
Examples of Social Engineering Attacks
The following real-world social engineering attack cases show common tactics employed by cybercriminals, how the incidents happened, and impacts:
Example #1: Barbara Corcoran (Shark Tank), 2020
Attackers created a spoofed email, identical to Barbara Corcoran’s assistant’s address, to trick her bookkeeper to conduct a wire transfer of nearly $400,000 for a fake real estate invoice.
The incident came to light in February 2020, after the bookkeeper noticed some minor inconsistencies in the transaction process.
- How it Happened: The bookkeeper, believing the request came from a trusted assistant, processed the fraudulent payment. However, the scam was exposed when the real assistant denied sending the mail.
- Impact: According to some media reports, almost $400,000 was lost in the scam.
Example #2: Toyota Boshoku Corporation, 2019
Cyber criminals used email to convince a finance executive to change legitimate vendor bank account details, resulting in a fraudulent payment transfer.
This attack happened in August, 2019, in a series of days. It was identified a few days later after officials reviewed irregularities in the transaction.
- How it Happened: Attackers impersonated a trusted party and prompted an urgent change to banking details. Without independent verification, $37 million was transferred to an account controlled by scammers.
- Impact: Toyota Boshoku lost $37 million, significantly impacting their financial situation. It’s not clear if any of the funds were recovered.
Example #3: Cabarrus County, 2018
Hackers impersonated a trusted vendor using email and fake documentation to fraudulently update payment account details. The scam went undetected for several weeks.
The payments were made between November and early December 2018, but the fraud came into notice in December.
- How it Happened: Officials processed a bank account change and transferred $2.5 million intended to a vendor, of which $1.7 million was never recovered.
- Impact: $1.7 million was lost, resulting in operational and budget challenges for the county.
Best Practices for Preventing Social Engineering Attacks
Employee Training and Awareness
- Train employees to identify fake help desk calls, deepfake voices, and urgent executive-style scams.
- Encourage teams to share suspicious activity and support each other in staying alert.
Multi-Factor Authentication Enhancements
- Implement MFA across critical systems to block attackers even if passwords are stolen.
- Adopt stronger MFA methods like security keys or push notifications instead of SMS codes.
- Mandate MFA usage for sensitive workflows to reduce account takeover risks.
Network Security Controls
- Isolate critical networks to limit breaches and prevent attackers from moving laterally.
- Restrict user access strictly to what is required for their role.
- Deploy anomaly detection and decoy systems to quickly identify and trap intruders.
Technical Controls
- Monitor for unauthorized use of legitimate remote tools such as AnyDesk or Splashtop.
- Apply application whitelisting, DNS filtering, and strict email filtering to block malicious activity.
- Disable unused remote access services or secure them with MFA and strong passwords.
Security Monitoring and Analytics
- Enable continuous monitoring to detect threats at any hour.
- Track unusual login times, location anomalies, and other behavioral red flags.
- Establish baselines of normal activity to detect deviations quickly.
Incident Response Planning
- Educate staff on how to report suspicious emails or calls without fear of blame.
- Prepare communication plans and backups to stay operational during crises.
- Define clear roles for responding to incidents and rehearse them regularly.
Robust Identity and Access Management
- Apply Zero Trust principles by verifying every user and device, internal or external.
- Audit access rights frequently and remove permissions that are no longer needed.
- Grant elevated privileges only temporarily and revoke them after use.
Response Readiness
- Develop simple playbooks tailored to scenarios like impersonation or SIM swap attacks.
- Conduct regular drills to build muscle memory and speed in response actions.
- Reinforce readiness so teams act decisively during real-world incidents.
Third-Party Risk Management
- Evaluate vendors carefully and enforce high security standards before granting access.
- Limit third-party access to the minimum necessary for their function.
- Review vendor permissions frequently and revoke outdated ones immediately.
Defensive Password and Reset Strategy
- Verify identities rigorously during password resets using callbacks or extra checks.
- Promote passphrases that are long and complex instead of predictable “strong” passwords.
- Test employees regularly with simulated attacks to reinforce password hygiene.
Use a Layered Defense
- Combine training, processes, and technology into overlapping security layers.
- Reinforce vigilance by making cybersecurity an ongoing habit, not a one-time effort.
- Integrate people, tools, and workflows to create resilience against evolving threats.
Verify the Source
- Confirm the authenticity of any request for sensitive information by contacting the organization directly through verified details.
- Avoid clicking links or downloading attachments from unsolicited emails, messages, or websites.
Strengthen Passwords
- Use strong, unique passwords for each account and avoid predictable information like birthdates.
- Avoid using easily guessable information such as birthdates or common words.
- Enable two-factor authentication to add an extra layer of protection.
Be Cautious with Personal Information
- Share personal or sensitive details only with trusted entities.
- Only provide such information to trusted entities and avoid disclosing it on public platforms or in response to unsolicited requests.
Keep Software Updated
- Regularly update operating systems, apps, and security tools to patch known vulnerabilities. Outdated software can be exploited by attackers.
Use Spam Filters
- Enable spam filters to detect and block suspicious or malicious emails.
- This reduces the risk of phishing and spear phishing attempts.
Use Secure Wi-Fi Networks
- Connect only to secure and trusted networks, especially in public places.
- Avoid unsecured networks that could be used for eavesdropping or data theft.
Implement Security Policies
- Create and enforce clear guidelines for information sharing, password use, and reporting suspicious activity.
- Address social engineering risks directly in these policies.
Regularly Back Up Data
- Maintain secure, encrypted backups on external storage or cloud services.
- Backups help restore data quickly after an attack and reduce impact.
Stay Updated on Security Threats
- Verify identities rigorously during password resets with callbacks or extra checks.
- Encourage use of long, complex passphrases.
- Run simulated attacks to train employees on password hygiene.
Conclusion
Social engineering attacks exploit trust rather than technical vulnerability that makes it harder to detect and prevent. Organizations can reduce social engineering risks through regular employee training, layered defenses, and clear response plans, and vigilant monitoring.
At SecureLayer7, we know how security awareness training and education programs can help prevent such attacks. Our experts know how to prevent the most sophisticated attacks. Contact us now to learn more.
FAQ’s
Threat actors mimic trusted contacts, company branding, such as logo, images, and reference real projects or colleagues. This lowers the suspicion and tricks employees into believing it quickly to perform the requested action.
Some of the signs include urgent payment demands, unusual sender addresses, spelling and grammar inconsistencies. These are common red flags for social engineering and employees should confirm and double-check before performing any action.
Yes. This is because attackers use human psychology to bypass cybersecurity restrictions.



